|
Attack Model
In cryptanalysis, attack models or attack types are a classification of cryptographic attacks specifying the kind of access a Cryptanalysis, cryptanalyst has to a system under attack when attempting to "break" an Encryption, encrypted message (also known as ''ciphertext'') generated by the system. The greater the access the cryptanalyst has to the system, the more useful information they can get to utilize for breaking the cypher. In cryptography, a sending party uses a cipher to encryption, encrypt (transform) a secret ''plaintext'' into a ''ciphertext'', which is sent over an insecure communication channel to the receiving party. The receiving party uses an inverse cipher to decryption, decrypt the ciphertext to obtain the plaintext. A secret knowledge is required to apply the inverse cipher to the ciphertext. This secret knowledge is usually a short number or string called a ''cryptographic key, key''. In a cryptographic attack a third party cryptanalyst analyzes the ciphertex ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Cryptanalysis
Cryptanalysis (from the Greek ''kryptós'', "hidden", and ''analýein'', "to analyze") refers to the process of analyzing information systems in order to understand hidden aspects of the systems. Cryptanalysis is used to breach cryptographic security systems and gain access to the contents of encrypted messages, even if the cryptographic key is unknown. In addition to mathematical analysis of cryptographic algorithms, cryptanalysis includes the study of side-channel attacks that do not target weaknesses in the cryptographic algorithms themselves, but instead exploit weaknesses in their implementation. Even though the goal has been the same, the methods and techniques of cryptanalysis have changed drastically through the history of cryptography, adapting to increasing cryptographic complexity, ranging from the pen-and-paper methods of the past, through machines like the British Bombes and Colossus computers at Bletchley Park in World War II, to the mathematically advanced ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
One Time Pad
The one-time pad (OTP) is an encryption technique that cannot be cracked in cryptography. It requires the use of a single-use pre-shared key that is larger than or equal to the size of the message being sent. In this technique, a plaintext is paired with a random secret key (also referred to as a ''one-time pad''). Then, each bit or character of the plaintext is encrypted by combining it with the corresponding bit or character from the pad using modular addition. The resulting ciphertext is impossible to decrypt or break if the following four conditions are met: # The key must be at least as long as the plaintext. # The key must be truly random. # The key must never be reused in whole or in part. # The key must be kept completely secret by the communicating parties. These requirements make the OTP the only known encryption system that is mathematically proven to be unbreakable under the principles of information theory. Digital versions of one-time pad ciphers have been ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Lunchtime Attack
A chosen-ciphertext attack (CCA) is an attack model for cryptanalysis where the cryptanalyst can gather information by obtaining the decryptions of chosen ciphertexts. From these pieces of information the adversary can attempt to recover the secret key used for decryption. For formal definitions of security against chosen-ciphertext attacks, see for example: Michael Luby and Mihir Bellare et al. Introduction A number of otherwise secure schemes can be defeated under chosen-ciphertext attack. For example, the El Gamal cryptosystem is semantically secure under chosen-plaintext attack, but this semantic security can be trivially defeated under a chosen-ciphertext attack. Early versions of RSA padding used in the SSL protocol were vulnerable to a sophisticated adaptive chosen-ciphertext attack which revealed SSL session keys. Chosen-ciphertext attacks have implications for some self-synchronizing stream ciphers as well. Designers of tamper-resistant cryptographic smart cards m ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Chosen-ciphertext Attack
A chosen-ciphertext attack (CCA) is an attack model for cryptanalysis where the cryptanalyst can gather information by obtaining the decryptions of chosen ciphertexts. From these pieces of information the adversary can attempt to recover the secret key used for decryption. For formal definitions of security against chosen-ciphertext attacks, see for example: Michael Luby and Mihir Bellare et al. Introduction A number of otherwise secure schemes can be defeated under chosen-ciphertext attack. For example, the El Gamal cryptosystem is semantically secure under chosen-plaintext attack, but this semantic security can be trivially defeated under a chosen-ciphertext attack. Early versions of RSA padding used in the SSL protocol were vulnerable to a sophisticated adaptive chosen-ciphertext attack which revealed SSL session keys. Chosen-ciphertext attacks have implications for some self-synchronizing stream ciphers as well. Designers of tamper-resistant cryptographic smart ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Adaptive Chosen-plaintext Attack
A chosen-plaintext attack (CPA) is an attack model for cryptanalysis which presumes that the attacker can obtain the ciphertexts for arbitrary plaintexts.Ross Anderson, ''Security Engineering: A Guide to Building Dependable Distributed Systems''. The first edition (2001): http://www.cl.cam.ac.uk/~rja14/book.html The goal of the attack is to gain information that reduces the security of the encryption scheme. Modern ciphers aim to provide semantic security, also known as ''ciphertext indistinguishability under chosen-plaintext attack'', and they are therefore, by design, generally immune to chosen-plaintext attacks if correctly implemented. Introduction In a chosen-plaintext attack the adversary can (possibly adaptively) ask for the ciphertexts of arbitrary plaintext messages. This is formalized by allowing the adversary to interact with an encryption oracle, viewed as a black box. The attacker’s goal is to reveal all or a part of the secret encryption key. It may seem infeasib ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Public-key Cryptosystem
Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a public key and a corresponding private key. Key pairs are generated with cryptographic algorithms based on mathematical problems termed one-way functions. Security of public-key cryptography depends on keeping the private key secret; the public key can be openly distributed without compromising security. There are many kinds of public-key cryptosystems, with different security goals, including digital signature, Diffie–Hellman key exchange, public-key key encapsulation, and public-key encryption. Public key algorithms are fundamental security primitives in modern cryptosystems, including applications and protocols that offer assurance of the confidentiality and authenticity of electronic communications and data storage. They underpin numerous Internet standards, such as Transport Layer Security (TLS), SSH, S/MIME, a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
State Space
In computer science, a state space is a discrete space representing the set of all possible configurations of a system. It is a useful abstraction for reasoning about the behavior of a given system and is widely used in the fields of artificial intelligence and game theory. For instance, the toy problem Vacuum World has a discrete finite state space in which there are a limited set of configurations that the vacuum and dirt can be in. A "counter" system, where states are the natural numbers starting at 1 and are incremented over time has an infinite discrete state space. The angular position of an undamped pendulum is a continuous (and therefore infinite) state space. Definition State spaces are useful in computer science as a simple model of machines. Formally, a state space can be defined as a tuple [''N'', ''A'', ''S'', ''G''] where: * ''N'' is a Set (mathematics), set of states * ''A'' is a set of arcs connecting the states * ''S'' is a nonempty subset of ''N ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Chosen-plaintext Attack
A chosen-plaintext attack (CPA) is an attack model for cryptanalysis which presumes that the attacker can obtain the ciphertexts for arbitrary plaintexts.Ross Anderson, ''Security Engineering: A Guide to Building Dependable Distributed Systems''. The first edition (2001): http://www.cl.cam.ac.uk/~rja14/book.html The goal of the attack is to gain information that reduces the security of the encryption scheme. Modern ciphers aim to provide semantic security, also known as ''ciphertext indistinguishability under chosen-plaintext attack'', and they are therefore, by design, generally immune to chosen-plaintext attacks if correctly implemented. Introduction In a chosen-plaintext attack the adversary can (possibly adaptively) ask for the ciphertexts of arbitrary plaintext messages. This is formalized by allowing the adversary to interact with an encryption oracle, viewed as a black box. The attacker’s goal is to reveal all or a part of the secret encryption key. It may seem infe ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Gordon Welchman
William Gordon Welchman OBE (15 June 1906 – 8 October 1985) was an English mathematician. During World War II, he worked at Britain's secret decryption centre at Bletchley Park, where he was one of the most important contributors. In 1948, after the war, he moved to the US and later worked on the design of military communications systems. Early life, education and career Gordon Welchman was born, the youngest of three children, at Fishponds in Bristol, to William Welchman (1866–1954) and Elizabeth Marshall Griffith. William was a Church of England priest who had been a missionary overseas before returning to England as a country vicar, eventually becoming archdeacon of Bristol. Elizabeth was the daughter of another priest, the Revd Edward Moule Griffith. Welchman was educated at Marlborough College and then studied mathematics at Trinity College, Cambridge, from 1925 to 1928. In 1929, he became a Research Fellow in Mathematics at Sidney Sussex College, Cambridge. He be ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Bletchley Park
Bletchley Park is an English country house and Bletchley Park estate, estate in Bletchley, Milton Keynes (Buckinghamshire), that became the principal centre of Allies of World War II, Allied World War II cryptography, code-breaking during the Second World War. During World War II, the estate housed the Government Code and Cypher School (GC&CS), which regularly penetrated the secret communications of the Axis Powers most importantly the German Enigma machine, Enigma and Lorenz cipher, Lorenz ciphers. The GC&CS team of codebreakers included John Tiltman, Dilwyn Knox, Alan Turing, Harry Golombek, Gordon Welchman, Conel Hugh O'Donel Alexander, Hugh Alexander, Donald Michie, W. T. Tutte, Bill Tutte and Stuart Milner-Barry. The team at Bletchley Park devised automatic machinery to help with decryption, culminating in the development of Colossus computer, Colossus, the world's first programmable digital electronic computer. Codebreaking operations at Bletchley Park ended in 1946 and al ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Crib (cryptanalysis)
The known-plaintext attack (KPA) is an attack model for cryptanalysis where the attacker has access to both the plaintext (called a crib) and its encrypted version (ciphertext). These can be used to reveal secret keys and code books. The term "crib" originated at Bletchley Park, the British World War II decryption operation, where it was defined as: History The usage "crib" was adapted from a slang term referring to cheating (e.g., "I cribbed my answer from your test paper"). A "crib" originally was a literal or interlinear translation of a foreign-language text—usually a Latin or Greek text—that students might be assigned to translate from the original language. The idea behind a crib is that cryptologists were looking at incomprehensible ciphertext, but if they had a clue about some word or phrase that might be expected to be in the ciphertext, they would have a "wedge," a test to break into it. If their otherwise random attacks on the cipher managed to sometimes produce th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
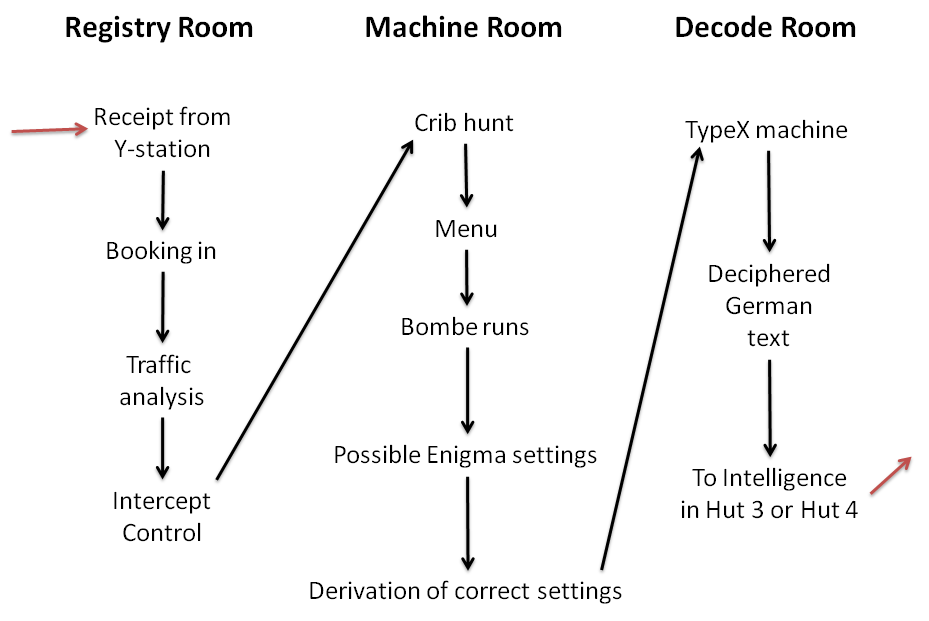
Cryptanalysis Of The Enigma
Cryptanalysis of the Enigma ciphering system enabled the western Allies of World War II, Allies in World War II to read substantial amounts of Morse code, Morse-coded radio communications of the Axis powers that had been enciphered using Enigma machines. This yielded military intelligence which, along with that from other decrypted Axis radio and teleprinter transmissions, was given the codename ''Ultra (cryptography), Ultra''. The Enigma machines were a family of portable cipher machines with rotor machine, rotor scramblers. Good operating procedures, properly enforced, would have made the plugboard Enigma machine unbreakable to the Allies at that time. The German plugboard-equipped Enigma became the principal cryptography, crypto-system of the Third Reich, German Reich and later of other Axis powers. In December 1932 it was broken by mathematician Marian Rejewski at the Polish General Staff's Cipher Bureau (Poland), Cipher Bureau, using mathematical permutation group theory ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |