|
Crib (cryptanalysis)
The known-plaintext attack (KPA) is an attack model for cryptanalysis where the attacker has access to both the plaintext (called a crib), and its encrypted version (ciphertext). These can be used to reveal further secret information such as secret keys and code books. The term "crib" originated at Bletchley Park, the British World War II decryption operation, where it was defined as: History The usage "crib" was adapted from a slang term referring to cheating (e.g., "I cribbed my answer from your test paper"). A "crib" originally was a literal or interlinear translation of a foreign-language text—usually a Latin or Greek text—that students might be assigned to translate from the original language. The idea behind a crib is that cryptologists were looking at incomprehensible ciphertext, but if they had a clue about some word or phrase that might be expected to be in the ciphertext, they would have a "wedge," a test to break into it. If their otherwise random attacks on the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Attack Model
In cryptanalysis, attack models or attack types are a classification of cryptographic attacks specifying the kind of access a cryptanalyst has to a system under attack when attempting to "break" an encrypted message (also known as ''ciphertext'') generated by the system. The greater the access the cryptanalyst has to the system, the more useful information they can get to utilize for breaking the cypher. In cryptography, a sending party uses a cipher to encrypt (transform) a secret ''plaintext'' into a ''ciphertext'', which is sent over an insecure communication channel to the receiving party. The receiving party uses an inverse cipher to decrypt the ciphertext to obtain the plaintext. A secret knowledge is required to apply the inverse cipher to the ciphertext. This secret knowledge is usually a short number or string called a ''key''. In a cryptographic attack a third party cryptanalyst analyzes the ciphertext to try to "break" the cipher, to read the plaintext and obtain the k ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
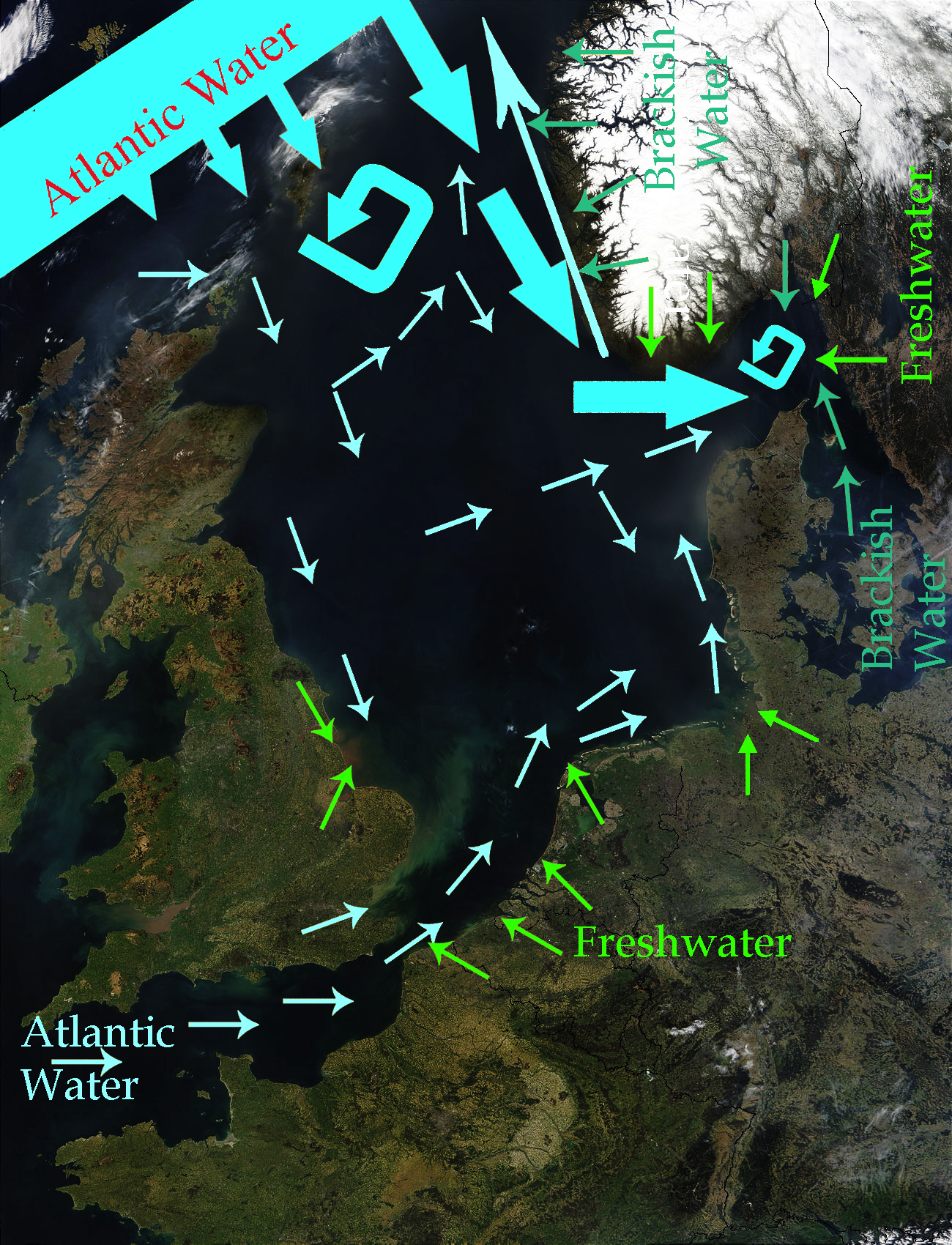
North Sea
The North Sea lies between Great Britain, Norway, Denmark, Germany, the Netherlands and Belgium. An epeiric sea on the European continental shelf, it connects to the Atlantic Ocean through the English Channel in the south and the Norwegian Sea in the north. It is more than long and wide, covering . It hosts key north European shipping lanes and is a major fishery. The coast is a popular destination for recreation and tourism in bordering countries, and a rich source of energy resources, including wind and wave power. The North Sea has featured prominently in geopolitical and military affairs, particularly in Northern Europe, from the Middle Ages to the modern era. It was also important globally through the power northern Europeans projected worldwide during much of the Middle Ages and into the modern era. The North Sea was the centre of the Vikings' rise. The Hanseatic League, the Dutch Republic, and the British each sought to gain command of the North Sea and access ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
William Halsey Jr
William Frederick "Bull" Halsey Jr. (October 30, 1882 – August 16, 1959) was an American Navy admiral during World War II. He is one of four officers to have attained the rank of five-star fleet admiral of the United States Navy, the others being William Leahy, Ernest King, and Chester W. Nimitz. Born in Elizabeth, New Jersey, Halsey graduated from the United States Naval Academy in 1904. He served in the Great White Fleet and, during World War I, commanded the destroyer . He took command of the aircraft carrier in 1935 after completing a course in naval aviation, and was promoted to the rank of rear admiral in 1938. At the start of the War in the Pacific (1941–1945), Halsey commanded the task force centered on the carrier in a series of raids against Japanese-held targets. Halsey was made commander of the South Pacific Area, and led the Allied forces over the course of the Battle for Guadalcanal (1942–1943) and the fighting up the Solomon chain (1942–1945). ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Russian Copulation
In cryptography, Russian copulation is a method of rearranging plaintext before encryption so as to conceal stereotyped headers, salutations, introductions, endings, signatures, etc. This obscures clues for a cryptanalyst, and can be used to increase cryptanalytic difficulty in naive cryptographic schemes (however, most modern schemes contain more rigorous defences; see ciphertext indistinguishability). This is of course desirable for those sending messages and wishing them to remain confidential. Padding is another technique for obscuring such clues. The technique is to break the starting plaintext message into two parts and then to invert the order of the parts (similar to circular shift In combinatorial mathematics, a circular shift is the operation of rearranging the entries in a tuple, either by moving the final entry to the first position, while shifting all other entries to the next position, or by performing the inverse op ...). This puts all endings and beginnings (pr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
5-UCO
The 5-UCO (5-Unit Controlled)Ralph Erskine, "The 1944 Naval BRUSA Agreement and its Aftermath", ''Cryptologia'' 30(1), January 2006 pp14–15 was an on-line one-time tape Vernam cipher encryption system developed by the UK during World War II for use on teleprinter circuits. During the 1950s, it was used by the UK and US for liaison on cryptanalysis. 5-UCO was fully synchronous, and therefore could be electrically regenerated on tandem high frequency (HF) radio links (i.e. one link connected to the next). It could operate directly with commercial circuits. The system also provided traffic-flow security (TFS). Another feature of the 5-UCO was that the receiving operator could maintain synchronisation if the path delay suddenly changed by "walking up and down" the key tape (one character at a time or one bit at a time). This procedure avoided the cumbersome task of a restart.Melville Klein, "Securing Record Communications: The TSEC/KW-26", 2003, NSA brochure, p. 4(PDF)/ref> ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
One-time Tape
In cryptography, the one-time pad (OTP) is an encryption technique that cannot be cracked, but requires the use of a single-use pre-shared key that is not smaller than the message being sent. In this technique, a plaintext is paired with a random secret key (also referred to as ''a one-time pad''). Then, each bit or character of the plaintext is encrypted by combining it with the corresponding bit or character from the pad using modular addition. The resulting ciphertext will be impossible to decrypt or break if the following four conditions are met: #The key must be at least as long as the plaintext. #The key must be random ( uniformly distributed in the set of all possible keys and independent of the plaintext), entirely sampled from a non-algorithmic, chaotic source such as a hardware random number generator. It is not sufficient for OTP keys to pass statistical randomness tests as such tests cannot measure entropy, and the number of bits of entropy must be at least e ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Władysław Kozaczuk
Władysław Kozaczuk (23 December 1923 – 26 September 2003) was a Polish Army colonel and a military and intelligence historian. Life Born in the village of Babiki near Sokółka, Kozaczuk joined the army in 1944, during World War II, at Białystok. In 1945 he became a Polish Army second lieutenant, and spent the first 5 years of his service commanding operational units of the Internal Security Corps, fighting the Polish anticommunist underground and then the Ukrainian Insurgent Army. In 1950 he was transferred to the Internal Security Corps Staff in Warsaw. In 1954–55, following the Korean War, Kozaczuk carried out armistice-related duties in Korea. In 1955–58 he served in the Polish Ministry of Internal Affairs ('). In 1957–58 he saw duty with the International Control Commission in Vietnam. In 1958–69 he served in Polish military counter-intelligence (''Wojskowa Służba Wewnętrzna''). According to his family, he found conditions there uncongenial ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Marian Rejewski
Marian Adam Rejewski (; 16 August 1905 – 13 February 1980) was a Polish mathematician and cryptography, cryptologist who in late 1932 reconstructed the sight-unseen German military Enigma machine, Enigma cipher machine, aided by limited documents obtained by French military intelligence. Over the next nearly seven years, Rejewski and fellow mathematician-cryptologists Jerzy Różycki and Henryk Zygalski developed and used techniques and equipment to decrypt the German machine ciphers, even as the Germans introduced modifications to their equipment and encryption procedures. Five weeks before the outbreak of World War II the Poles, at a conference in Warsaw, shared their achievements with the French and British, thus enabling Britain to begin reading German Enigma-encrypted messages, seven years after Rejewski's original reconstruction of the machine. The intelligence that was gained by the British from Enigma decrypts formed part of what was code-named Ultra (cryptography), Ul ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Biuro Szyfrów
The Cipher Bureau, in Polish: ''Biuro Szyfrów'' (), was the interwar Polish General Staff's Second Department's unit charged with SIGINT and both cryptography (the ''use'' of ciphers and codes) and cryptanalysis (the ''study'' of ciphers and codes, for the purpose of "breaking" them). The precursor of the agency that would become the Cipher Bureau was created in May 1919, during the Polish-Soviet War (1919–21), and played a vital role in securing Poland's survival and victory in that war. In mid-1931, the Cipher Bureau was formed by the merger of pre-existing agencies. In December 1932, the Bureau began breaking Germany's Enigma ciphers. Over the next seven years, Polish cryptologists overcame the growing structural and operating complexities of the plugboard-equipped Enigma. The Bureau also broke Soviet cryptography. Five weeks before the outbreak of World War II, on 25 July 1939, in Warsaw, the Polish Cipher Bureau revealed its Enigma-decryption techniques and equipme ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Benford's Law
Benford's law, also known as the Newcomb–Benford law, the law of anomalous numbers, or the first-digit law, is an observation that in many real-life sets of numerical data, the leading digit is likely to be small.Arno Berger and Theodore P. HillBenford's Law Strikes Back: No Simple Explanation in Sight for Mathematical Gem 2011. In sets that obey the law, the number 1 appears as the leading significant digit about 30% of the time, while 9 appears as the leading significant digit less than 5% of the time. If the digits were distributed uniformly, they would each occur about 11.1% of the time. Benford's law also makes predictions about the distribution of second digits, third digits, digit combinations, and so on. The graph to the right shows Benford's law for base 10, one of infinitely many cases of a generalized law regarding numbers expressed in arbitrary (integer) bases, which rules out the possibility that the phenomenon might be an artifact of the base-10 number system ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Alan Turing
Alan Mathison Turing (; 23 June 1912 – 7 June 1954) was an English mathematician, computer scientist, logician, cryptanalyst, philosopher, and theoretical biologist. Turing was highly influential in the development of theoretical computer science, providing a formalisation of the concepts of algorithm and computation with the Turing machine, which can be considered a model of a general-purpose computer. He is widely considered to be the father of theoretical computer science and artificial intelligence. Born in Maida Vale, London, Turing was raised in southern England. He graduated at King's College, Cambridge, with a degree in mathematics. Whilst he was a fellow at Cambridge, he published a proof demonstrating that some purely mathematical yes–no questions can never be answered by computation and defined a Turing machine, and went on to prove that the halting problem for Turing machines is undecidable. In 1938, he obtained his PhD from the Department of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Double-Cross System
The Double-Cross System or XX System was a World War II counter-espionage and deception operation of the British Security Service (a civilian organisation usually referred to by its cover title MI5). Nazi agents in Britain – real and false – were captured, turned themselves in or simply announced themselves, and were then used by the British to broadcast mainly disinformation to their Nazi controllers. Its operations were overseen by the Twenty Committee under the chairmanship of John Cecil Masterman; the name of the committee comes from the number 20 in Roman numerals: "XX" (i.e. a double cross). The policy of MI5 during the war was initially to use the system for counter-espionage. It was only later that its potential for deception purposes was realised. Of the agents from the German intelligence services, ''Abwehr'' and ''Sicherheitsdienst'' (SD), some were apprehended, while many of the agents who reached British shores turned themselves in to the authorities; others wer ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |