|
YubiKey Neo And Nano
The YubiKey is a hardware authentication device manufactured by Yubico to protect access to computers, networks, and online services that supports one-time passwords (OTP), public-key cryptography, and authentication, and the Universal 2nd Factor (U2F) and FIDO2 protocols developed by the FIDO Alliance. It allows users to securely log into their accounts by emitting one-time passwords or using a FIDO-based public/private key pair generated by the device. YubiKey also allows for storing static passwords for use at sites that do not support one-time passwords. Google, Amazon, Microsoft, Twitter, and Facebook use YubiKey devices to secure employee accounts as well as end user accounts. Some password managers support YubiKey. Yubico also manufactures the Security Key, a similar lower cost device with only FIDO2/WebAuthn and FIDO/U2F support. The YubiKey implements the HMAC-based One-time Password Algorithm (HOTP) and the Time-based One-time Password Algorithm (TOTP), and identifie ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Palo Alto, California
Palo Alto (; Spanish language, Spanish for "tall stick") is a charter city in the northwestern corner of Santa Clara County, California, United States, in the San Francisco Bay Area, named after a Sequoia sempervirens, coastal redwood tree known as El Palo Alto. The city was established in 1894 by the American industrialist Leland Stanford when he founded Stanford University in memory of his son, Leland Stanford Jr. Palo Alto includes portions of Stanford University and borders East Palo Alto, California, East Palo Alto, Mountain View, California, Mountain View, Los Altos, California, Los Altos, Los Altos Hills, California, Los Altos Hills, Stanford, California, Stanford, Portola Valley, California, Portola Valley, and Menlo Park, California, Menlo Park. At the 2010 United States Census, 2020 census, the population was 68,572. Palo Alto is one of the most expensive cities in the United States in which to live, and its residents are among the most educated in the country. Howeve ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Elliptic Curve Cryptography (ECC)
Elliptic-curve cryptography (ECC) is an approach to public-key cryptography based on the algebraic structure of elliptic curves over finite fields. ECC allows smaller keys compared to non-EC cryptography (based on plain Galois fields) to provide equivalent security.Commercial National Security Algorithm Suite and Quantum Computing FAQ U.S. National Security Agency, January 2016. Elliptic curves are applicable for , s, [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Radio-frequency Identification
Radio-frequency identification (RFID) uses electromagnetic fields to automatically identify and track tags attached to objects. An RFID system consists of a tiny radio transponder, a radio receiver and transmitter. When triggered by an electromagnetic interrogation pulse from a nearby RFID reader device, the tag transmits digital data, usually an identifying inventory number, back to the reader. This number can be used to track inventory goods. Passive tags are powered by energy from the RFID reader's interrogating radio waves. Active tags are powered by a battery and thus can be read at a greater range from the RFID reader, up to hundreds of meters. Unlike a barcode, the tag does not need to be within the line of sight of the reader, so it may be embedded in the tracked object. RFID is one method of automatic identification and data capture (AIDC). RFID tags are used in many industries. For example, an RFID tag attached to an automobile during production can be used to track ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
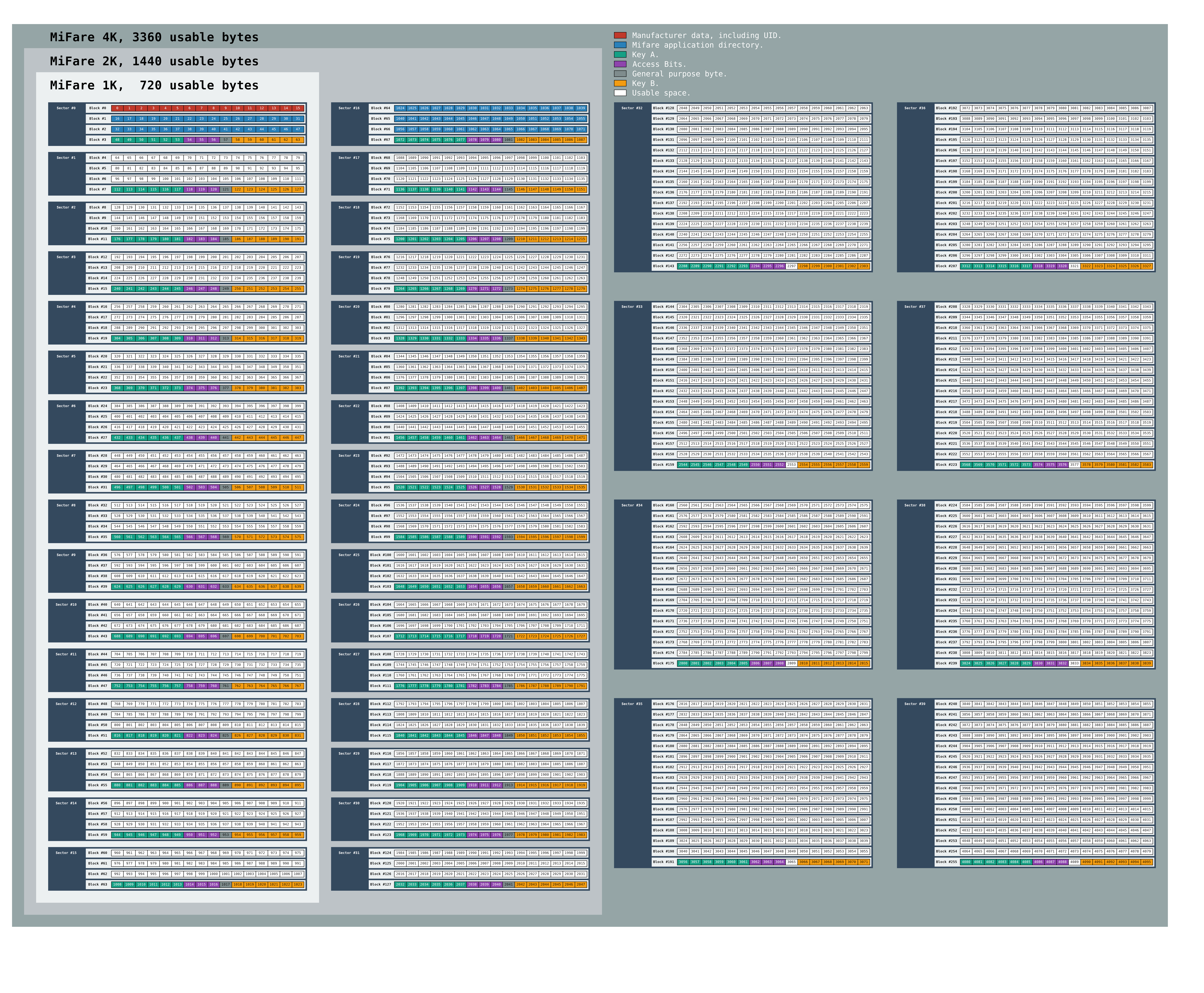
MIFARE
MIFARE is the NXP Semiconductors-owned trademark of a series of integrated circuit (IC) chips used in contactless smart cards and proximity cards. The brand name covers proprietary solutions based upon various levels of the ISO/IEC 14443 Type A 13.56 MHz contactless smart card standard. It uses AES and DES/Triple-DES encryption standards, as well as an older proprietary encryption algorithm, Crypto-1. According to NXP, 10 billion of their smart card chips and over 150 million reader modules have been sold. MIFARE is owned by NXP Semiconductors, which was spun off from Philips Electronics in 2006. Variants MIFARE products are embedded in contactless and contact smart cards, smart paper tickets, wearables and phones. The MIFARE brand name (derived from the term MIKRON FARE Collection and created by the company Mikron) covers four families of contactless cards: ; MIFARE Classic: Employs a proprietary protocol compliant to parts 1–3 of ISO/IEC 14443 Type A, with an NXP ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Initiative For Open Authentication
Initiative for Open Authentication (OATH) is an industry-wide collaboration to develop an open reference architecture using open standards to promote the adoption of strong authentication. It has close to thirty coordinating and contributing members and is proposing standards for a variety of authentication technologies, with the aim of lowering costs and simplifying their functions. Terminology The name ''OATH'' is an acronym from the phrase "open authentication", and is pronounced as the English word "oath". OATH is not related to OAuth, an open standard for authorization. See also * HOTP: An HMAC-Based One-Time Password Algorithm (RFC 4226) * TOTP: Time-Based One-Time Password Algorithm (RFC 6238) *OCRA: OATH Challenge-Response Algorithm (RFC 6287) *Portable Symmetric Key Container (PSKC) (RFC 6030) *Dynamic Symmetric Key Provisioning Protocol (DSKPP) (RFC 6063) *FIDO Alliance The FIDO ("Fast IDentity Online") Alliance is an open industry association launched in Febr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Advanced Encryption Standard
The Advanced Encryption Standard (AES), also known by its original name Rijndael (), is a specification for the encryption of electronic data established by the U.S. National Institute of Standards and Technology (NIST) in 2001. AES is a variant of the Rijndael block cipher developed by two Belgian cryptographers, Joan Daemen and Vincent Rijmen, who submitted a proposal to NIST during the AES selection process. Rijndael is a family of ciphers with different key and block sizes. For AES, NIST selected three members of the Rijndael family, each with a block size of 128 bits, but three different key lengths: 128, 192 and 256 bits. AES has been adopted by the U.S. government. It supersedes the Data Encryption Standard (DES), which was published in 1977. The algorithm described by AES is a symmetric-key algorithm, meaning the same key is used for both encrypting and decrypting the data. In the United States, AES was announced by the NIST as U.S. FIPS PUB 197 (FIPS 197) on Novemb ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Stockholm
Stockholm () is the Capital city, capital and List of urban areas in Sweden by population, largest city of Sweden as well as the List of urban areas in the Nordic countries, largest urban area in Scandinavia. Approximately 980,000 people live in the Stockholm Municipality, municipality, with 1.6 million in the Stockholm urban area, urban area, and 2.4 million in the Metropolitan Stockholm, metropolitan area. The city stretches across fourteen islands where Mälaren, Lake Mälaren flows into the Baltic Sea. Outside the city to the east, and along the coast, is the island chain of the Stockholm archipelago. The area has been settled since the Stone Age, in the 6th millennium BC, and was founded as a city in 1252 by Swedish statesman Birger Jarl. It is also the county seat of Stockholm County. For several hundred years, Stockholm was the capital of Finland as well (), which then was a part of Sweden. The population of the municipality of Stockholm is expected to reach o ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Seattle
Seattle ( ) is a seaport city on the West Coast of the United States. It is the seat of King County, Washington. With a 2020 population of 737,015, it is the largest city in both the state of Washington and the Pacific Northwest region of North America. The Seattle metropolitan area's population is 4.02 million, making it the 15th-largest in the United States. Its growth rate of 21.1% between 2010 and 2020 makes it one of the nation's fastest-growing large cities. Seattle is situated on an isthmus between Puget Sound (an inlet of the Pacific Ocean) and Lake Washington. It is the northernmost major city in the United States, located about south of the Canadian border. A major gateway for trade with East Asia, Seattle is the fourth-largest port in North America in terms of container handling . The Seattle area was inhabited by Native Americans for at least 4,000 years before the first permanent European settlers. Arthur A. Denny and his group of travelers, subsequ ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Palo Alto
Palo Alto (; Spanish for "tall stick") is a charter city in the northwestern corner of Santa Clara County, California, United States, in the San Francisco Bay Area, named after a coastal redwood tree known as El Palo Alto. The city was established in 1894 by the American industrialist Leland Stanford when he founded Stanford University in memory of his son, Leland Stanford Jr. Palo Alto includes portions of Stanford University and borders East Palo Alto, Mountain View, Los Altos, Los Altos Hills, Stanford, Portola Valley, and Menlo Park. At the 2020 census, the population was 68,572. Palo Alto is one of the most expensive cities in the United States in which to live, and its residents are among the most educated in the country. However, it also has a youth suicide rate four times higher than the national average, often attributed to academic pressure. As one of the principal cities of Silicon Valley, Palo Alto is headquarters to a number of high-tech companies, includi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Secure Shell
The Secure Shell Protocol (SSH) is a cryptographic network protocol for operating network services securely over an unsecured network. Its most notable applications are remote login and command-line execution. SSH applications are based on a client–server architecture, connecting an SSH client instance with an SSH server. SSH operates as a layered protocol suite comprising three principal hierarchical components: the ''transport layer'' provides server authentication, confidentiality, and integrity; the ''user authentication protocol'' validates the user to the server; and the ''connection protocol'' multiplexes the encrypted tunnel into multiple logical communication channels. SSH was designed on Unix-like operating systems, as a replacement for Telnet and for unsecured remote Unix shell protocols, such as the Berkeley Remote Shell (rsh) and the related rlogin and rexec protocols, which all use insecure, plaintext transmission of authentication tokens. SSH was first de ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Active Directory
Active Directory (AD) is a directory service developed by Microsoft for Windows domain networks. It is included in most Windows Server operating systems as a set of processes and services. Initially, Active Directory was used only for centralized domain management. However, Active Directory eventually became an umbrella title for a broad range of directory-based identity-related services. A server running the Active Directory Domain Service (AD DS) role is called a domain controller. It authenticates and authorizes all users and computers in a Windows domain type network, assigning and enforcing security policies for all computers, and installing or updating software. For example, when a user logs into a computer that is part of a Windows domain, Active Directory checks the submitted username and password and determines whether the user is a system administrator or normal user. Also, it allows management and storage of information, provides authentication and authorization mec ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Docker (software)
Docker is a set of platform as a service (PaaS) products that use OS-level virtualization to deliver software in packages called ''containers''. The service has both free and premium tiers. The software that hosts the containers is called Docker Engine. It was first started in 2013 and is developed by Docker, Inc. Background Containers are isolated from one another and bundle their own software, libraries and configuration files; they can communicate with each other through well-defined channels. Because all of the containers share the services of a single operating system kernel, they use fewer resources than virtual machines. Operation Docker can package an application and its dependencies in a virtual container that can run on any Linux, Windows, or macOS computer. This enables the application to run in a variety of locations, such as on-premises, in public (see decentralized computing, distributed computing, and cloud computing) or private cloud. When running on Linux, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |



_Round_Function.png)




