|
Multi Theft Auto
''Multi Theft Auto'' (''MTA'') is a multiplayer modification for the Microsoft Windows version of Rockstar North games '' Grand Theft Auto III'', '' Grand Theft Auto: Vice City'' and '' Grand Theft Auto: San Andreas'' that adds online multiplayer functionality. For ''Grand Theft Auto: San Andreas'', the mod also serves as a derivative engine to Rockstar's interpretation of RenderWare. History Background The release of ''Grand Theft Auto III'', a critically acclaimed sandbox-style action-adventure computer and video game developed by DMA Design (now Rockstar North) represented the first 3D title in the ''Grand Theft Auto'' (''GTA'') series. Despite its success, it was the first ''Grand Theft Auto'' game to ship without the network multiplayer gameplay features that were present in earlier titles, which allowed players to connect through a computer network and play the game with others. The first version of ''Multi Theft Auto'', dubbed ''Grand Theft Auto III: Alternati ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
GitHub
GitHub, Inc. () is an Internet hosting service for software development and version control using Git. It provides the distributed version control of Git plus access control, bug tracking, software feature requests, task management, continuous integration, and wikis for every project. Headquartered in California, it has been a subsidiary of Microsoft since 2018. It is commonly used to host open source software development projects. As of June 2022, GitHub reported having over 83 million developers and more than 200 million repositories, including at least 28 million public repositories. It is the largest source code host . History GitHub.com Development of the GitHub.com platform began on October 19, 2007. The site was launched in April 2008 by Tom Preston-Werner, Chris Wanstrath, P. J. Hyett and Scott Chacon after it had been made available for a few months prior as a beta release. GitHub has an annual keynote called GitHub Universe. Organizational ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Video Game
Video games, also known as computer games, are electronic games that involves interaction with a user interface or input device such as a joystick, controller, keyboard, or motion sensing device to generate visual feedback. This feedback mostly commonly is shown on a video display device, such as a TV set, monitor, touchscreen, or virtual reality headset. Some computer games do not always depend on a graphics display, for example text adventure games and computer chess can be played through teletype printers. Video games are often augmented with audio feedback delivered through speakers or headphones, and sometimes with other types of feedback, including haptic technology. Video games are defined based on their platform, which include arcade video games, console games, and personal computer (PC) games. More recently, the industry has expanded onto mobile gaming through smartphones and tablet computers, virtual and augmented reality systems, and remote c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Code Injection
Code injection is the exploitation of a computer bug that is caused by processing invalid data. The injection is used by an attacker to introduce (or "inject") code into a vulnerable computer program and change the course of execution. The result of successful code injection can be disastrous, for example, by allowing computer viruses or computer worms to propagate. Code injection vulnerabilities occur when an application sends untrusted data to an interpreter. Injection flaws are most often found in SQL, LDAP, XPath, NoSQL queries, OS commands, XML parsers, SMTP headers, program arguments, etc. Injection flaws tend to be easier to discover when examining source code than via testing. Scanners and fuzzers can help find injection flaws. Injection can result in data loss or corruption, lack of accountability, or denial of access. Injection can sometimes lead to complete host takeover. Certain types of code injection are errors in interpretation, giving special meaning to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Slashdot
''Slashdot'' (sometimes abbreviated as ''/.'') is a social news website that originally advertised itself as "News for Nerds. Stuff that Matters". It features news stories concerning science, technology, and politics that are submitted and evaluated by site users and editors. Each story has a comments section attached to it where users can add online comments. The website was founded in 1997 by Hope College students Rob Malda, also known as "CmdrTaco", and classmate Jeff Bates, also known as "Hemos". In 2012, they sold it to DHI Group, Inc. (i.e., Dice Holdings International, which created the Dice.com website for tech job seekers). In January 2016, BIZX acquired both slashdot.org and SourceForge. In December 2019, BIZX rebranded to Slashdot Media. Summaries of stories and hyperlinks to news articles are submitted by Slashdot's own users, and each story becomes the topic of a threaded discussion among users. Discussion is moderated by a user-based moderation system. Randomly sele ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
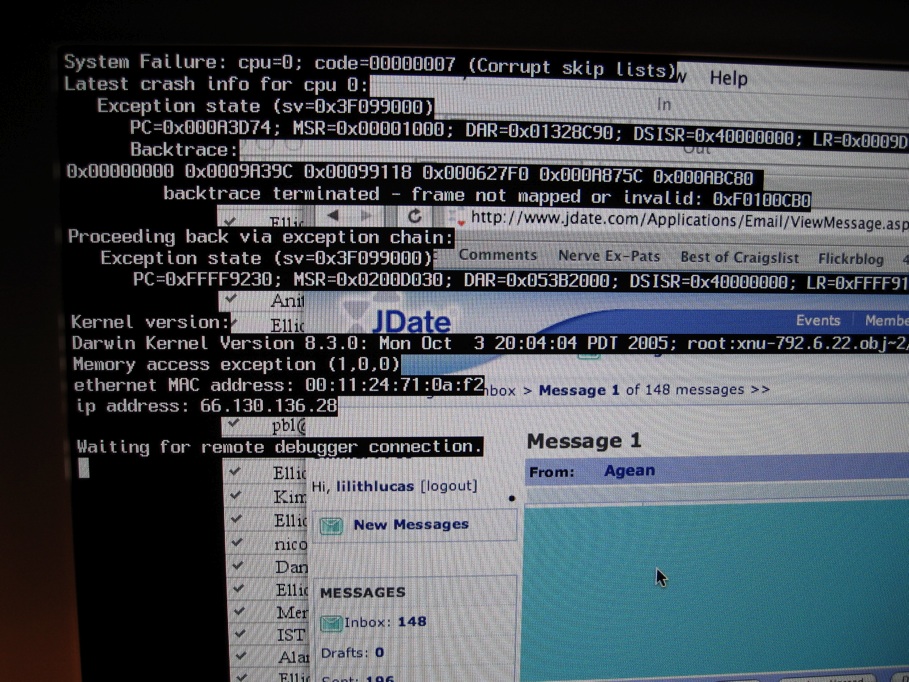
Crash (computing)
In computing, a crash, or system crash, occurs when a computer program such as a software application or an operating system stops functioning properly and exits. On some operating systems or individual applications, a crash reporting service will report the crash and any details relating to it (or give the user the option to do so), usually to the developer(s) of the application. If the program is a critical part of the operating system, the entire system may crash or hang, often resulting in a kernel panic or fatal system error. Most crashes are the result of a software bug. Typical causes include accessing invalid memory addresses, incorrect address values in the program counter, buffer overflow, overwriting a portion of the affected program code due to an earlier bug, executing invalid machine instructions (an illegal opcode), or triggering an unhandled exception. The original software bug that started this chain of events is typically considered to be the cause of the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Gamespy
GameSpy was an American provider of online multiplayer and matchmaking middleware for video games founded in 1996 by Mark Surfas. After the release of a multiplayer server browser for the game, QSpy, Surfas licensed the software under the GameSpy brand to other video game publishers through a newly established company, GameSpy Industries, which also incorporated his Planet Network of video game news and information websites, and GameSpy.com. GameSpy merged with IGN in 2004; by 2014, its services had been used by over 800 video game publishers and developers since its launch. In August 2012, the GameSpy Industries division (which remained responsible for the GameSpy service) was acquired by mobile video game developer Glu Mobile. IGN (then owned by News Corporation) retained ownership of the GameSpy.com website. In February 2013, IGN's new owner, Ziff Davis, shut down IGN's "secondary" sites, including GameSpy's network. This was followed by the announcement in April 2014 that G ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Software Framework
In computer programming, a software framework is an abstraction in which software, providing generic functionality, can be selectively changed by additional user-written code, thus providing application-specific software. It provides a standard way to build and deploy applications and is a universal, reusable software environment that provides particular functionality as part of a larger software platform to facilitate the development of software applications, products and solutions. Software frameworks may include support programs, compilers, code libraries, toolsets, and application programming interfaces (APIs) that bring together all the different components to enable development of a project or system. Frameworks have key distinguishing features that separate them from normal libraries: * ''inversion of control'': In a framework, unlike in libraries or in standard user applications, the overall program's flow of control is not dictated by the caller, but by the frame ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
XBAND
XBAND (stylized as XBⱯND) was one of the first competitive online console gaming networks and was available for the Genesis and Super NES. It was produced by Catapult Entertainment in Cupertino, California. It is the only modem released in America to have been officially licensed by Nintendo. It debuted in various areas of the United States in late 1994 and 1995. History The Genesis version of the XBAND was released in November 1994, with the Super NES version following in June 1995, and the Super Famicom version in April 1996. The Genesis version also works with the Genesis Nomad. In Brazil the Mega Drive service was released as the Mega Net 2, named after the Sega Meganet. In 1995, Catapult Entertainment signed a deal with General Instrument, producers of the Sega Channel, which stipulated that the XBAND modem would henceforth be built into new Sega Channel adapters, and that the top 5 to 10 games offered by Sega Channel each month would be playable over XBAND. Initially, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Proof Of Concept
Proof of concept (POC or PoC), also known as proof of principle, is a realization of a certain method or idea in order to demonstrate its feasibility, or a demonstration in principle with the aim of verifying that some concept or theory has practical potential. A proof of concept is usually small and may or may not be complete. These collaborative trials aim to test feasibility of business concepts and proposals to solve business problems and accelerate business innovation goals. A proof of value (PoV) is sometimes used along proof of concept, and differs by focusing more on demonstrating the potential customers use case and value, and is usually less in-depth than a proof of concept. Usage history The term has been in use since 1967. In a 1969 hearing of the Committee on Science and Astronautics, Subcommittee on Advanced Research and Technology, ''proof of concept'' was defined as following: One definition of the term "proof of concept" was by Bruce Carsten in the context o ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cheating (video Games)
Cheating in video games involves a video game player using various methods to create an advantage beyond normal gameplay, usually in order to make the game easier. Cheats may be activated from within the game itself (a cheat code implemented by the original game developers), or created by third-party software (a game trainer or debugger) or hardware (a cheat cartridge). They can also be realized by exploiting software bugs; this may or may not be considered cheating based on whether the bug is considered common knowledge. History Cheating in video games has existed for almost their entire history. The first cheat codes were put in place for play testing purposes. Playtesters had to rigorously test the mechanics of a game and introduced cheat codes to make this process easier. An early cheat code can be found in ''Manic Miner'', where typing "6031769" (based on Matthew Smith's driving license) enables the cheat mode. Within months of '' Wizardry: Proving Grounds of the Mad O ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Network
A computer network is a set of computers sharing resources located on or provided by network nodes. The computers use common communication protocols over digital interconnections to communicate with each other. These interconnections are made up of telecommunication network technologies, based on physically wired, optical, and wireless radio-frequency methods that may be arranged in a variety of network topologies. The nodes of a computer network can include personal computers, servers, networking hardware, or other specialised or general-purpose hosts. They are identified by network addresses, and may have hostnames. Hostnames serve as memorable labels for the nodes, rarely changed after initial assignment. Network addresses serve for locating and identifying the nodes by communication protocols such as the Internet Protocol. Computer networks may be classified by many criteria, including the transmission medium used to carry signals, bandwidth, communications pro ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |