|
Document Classification
Document classification or document categorization is a problem in library science, information science and computer science. The task is to assign a document to one or more Class (philosophy), classes or Categorization, categories. This may be done "manually" (or "intellectually") or algorithmically. The intellectual classification of documents has mostly been the province of library science, while the algorithmic classification of documents is mainly in information science and computer science. The problems are overlapping, however, and there is therefore interdisciplinary research on document classification. The documents to be classified may be texts, images, music, etc. Each kind of document possesses its special classification problems. When not otherwise specified, text classification is implied. Documents may be classified according to their Subject (documents), subjects or according to other attributes (such as document type, author, printing year etc.). In the rest of th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Library Science
Library and information science (LIS)Library and Information Sciences is the name used in the Dewey Decimal Classification for class 20 from the 18th edition (1971) to the 22nd edition (2003). are two interconnected disciplines that deal with information management. This includes organization, access, collection, and regulation of information, both in physical and digital forms.Coleman, A. (2002)Interdisciplinarity: The Road Ahead for Education in Digital Libraries D-Lib Magazine, 8:8/9 (July/August). Library science and information science are two original disciplines; however, they are within the same field of study. Library science is applied information science. Library science is both an application and a subfield of information science. Due to the strong connection, sometimes the two terms are used synonymously. Definition Library science (previously termed library studies and library economy) is an interdisciplinary or multidisciplinary field that applies the practices, per ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Expectation Maximization
Expectation, or expectations, as well as expectancy or expectancies, may refer to: Science * Expectancy effect, including observer-expectancy effects and subject-expectancy effects such as the placebo effect * Expectancy theory of motivation * Expectation (philosophy) * Expected value, in mathematical probability theory * Expectation value (quantum mechanics) * Expectation–maximization algorithm, in statistics Music * ''Expectation'' (album), a 2013 album by Girl's Day * ''Expectation'', a 2006 album by Matt Harding * ''Expectations'' (Keith Jarrett album), 1971 * ''Expectations'' (Dance Exponents album), 1985 * ''Expectations'' (Hayley Kiyoko album), 2018, or Expectations/Overture", a song from the album * ''Expectations'' (Bebe Rexha album), 2018 * ''Expectations'' (Katie Pruitt album), 2020, or the title song * "Expectation" (waltz), a 1980 waltz composed by Ilya Herold Lavrentievich Kittler * "Expectation" (song), a 2010 song by Tame Impala * "Expectations" (song ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Routing
Routing is the process of selecting a path for traffic in a Network theory, network or between or across multiple networks. Broadly, routing is performed in many types of networks, including circuit-switched networks, such as the public switched telephone network (PSTN), and computer networks, such as the Internet. In packet switching networks, routing is the higher-level decision making that directs network packets from their source toward their destination through intermediate network nodes by specific packet forwarding mechanisms. Packet forwarding is the transit of network packets from one Network interface controller, network interface to another. Intermediate nodes are typically network hardware devices such as Router (computing), routers, gateway (telecommunications), gateways, Firewall (computing), firewalls, or network switch, switches. General-purpose computers also forward packets and perform routing, although they have no specially optimized hardware for the task. T ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
E-mail Spam
Email spam, also referred to as junk email, spam mail, or simply spam, refers to unsolicited messages sent in bulk via email. The term originates from a Monty Python sketch, where the name of a canned meat product, "Spam," is used repetitively, mirroring the intrusive nature of unwanted emails. Since the early 1990s, spam has grown significantly, with estimates suggesting that by 2014, it comprised around 90% of all global email traffic. Spam is primarily a financial burden for the recipient, who may be required to manage, filter, or delete these unwanted messages. Since the expense of spam is mostly borne by the recipient, it is effectively a form of " postage due" advertising, where the recipient bears the cost of unsolicited messages. This cost imposed on recipients, without compensation from the sender, makes spam an example of a " negative externality" (a side effect of an activity that affects others who are not involved in the decision). The legal definition and status of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Spam Filter
Email filtering is the processing of email to organize it according to specified criteria. The term can apply to the intervention of human intelligence, but most often refers to the automatic processing of messages at an SMTP server, possibly applying anti-spam techniques. Filtering can be applied to incoming emails as well as to outgoing ones. Depending on the calling environment, email filtering software can reject an item at the initial SMTP connection stage or pass it through unchanged for delivery to the user's mailbox. It is also possible to redirect the message for delivery elsewhere, quarantine it for further checking, modify it or 'tag' it in any other way. Motivation Common uses for mail filters include organizing incoming email and removal of spam and computer viruses. Mailbox providers filter outgoing email to promptly react to spam surges that may result from compromised accounts. A less common use is to inspect outgoing email at some companies to ensure that em ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
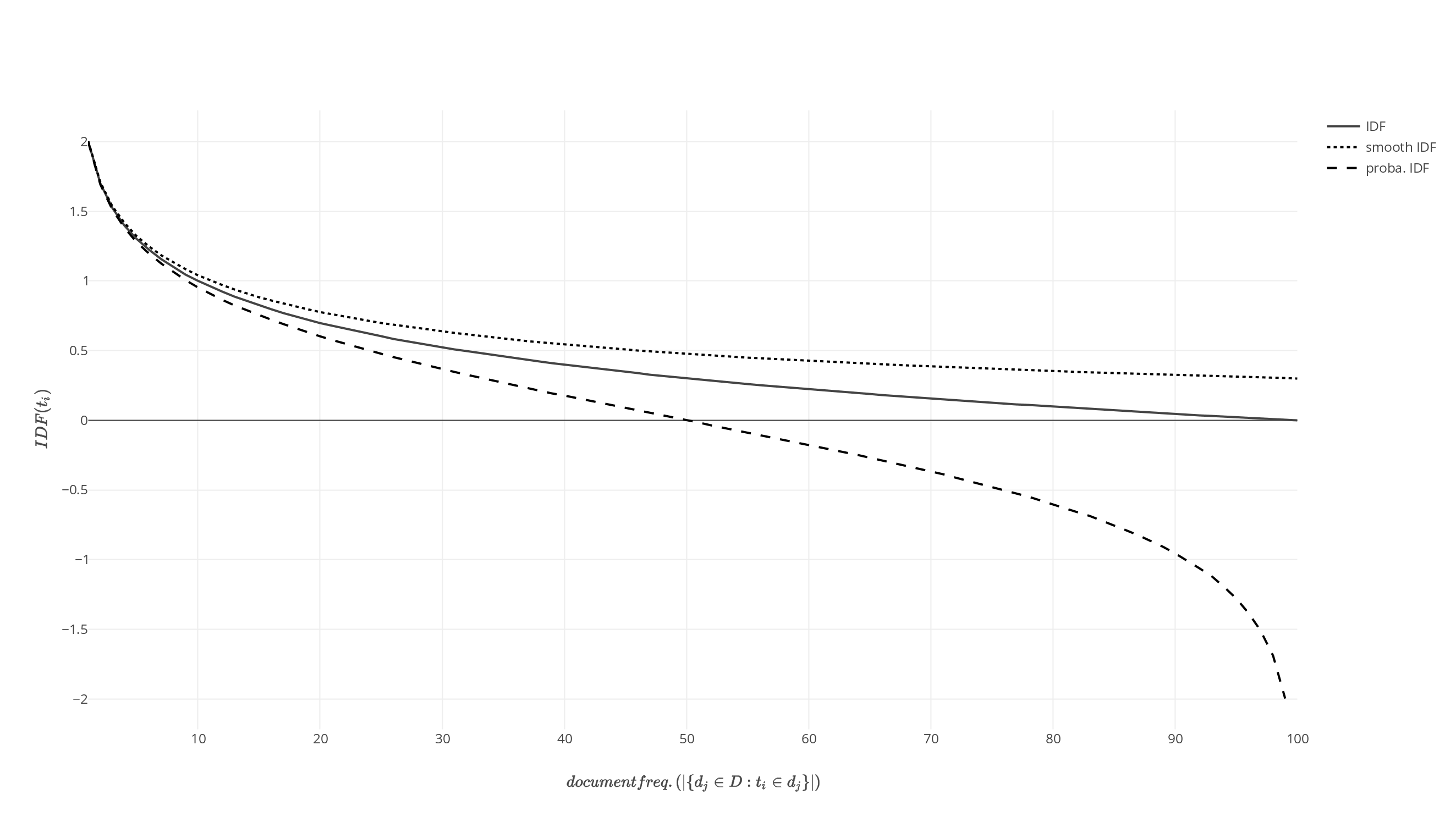
Tf–idf
In information retrieval, tf–idf (term frequency–inverse document frequency, TF*IDF, TFIDF, TF–IDF, or Tf–idf) is a measure of importance of a word to a document in a collection or Text corpus, corpus, adjusted for the fact that some words appear more frequently in general. Like the bag-of-words model, it models a document as a multiset of words, without word order. It is a refinement over the simple bag-of-words model, by allowing the weight of words to depend on the rest of the corpus. It was often used as a weighting factor in searches of information retrieval, text mining, and user modeling. A survey conducted in 2015 showed that 83% of text-based recommender systems in digital libraries used tf–idf. Variations of the tf–idf weighting scheme were often used by search engines as a central tool in scoring and ranking a document's Relevance (information retrieval), relevance given a user Information retrieval, query. One of the simplest ranking functions is computed b ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
K-nearest Neighbor Algorithm
In statistics, the ''k''-nearest neighbors algorithm (''k''-NN) is a non-parametric supervised learning method. It was first developed by Evelyn Fix and Joseph Hodges in 1951, and later expanded by Thomas Cover. Most often, it is used for classification, as a ''k''-NN classifier, the output of which is a class membership. An object is classified by a plurality vote of its neighbors, with the object being assigned to the class most common among its ''k'' nearest neighbors (''k'' is a positive integer, typically small). If ''k'' = 1, then the object is simply assigned to the class of that single nearest neighbor. The ''k''-NN algorithm can also be generalized for regression. In ''-NN regression'', also known as '' nearest neighbor smoothing'', the output is the property value for the object. This value is the average of the values of ''k'' nearest neighbors. If ''k'' = 1, then the output is simply assigned to the value of that single nearest neighbor, also known as ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Support Vector Machines
In machine learning, support vector machines (SVMs, also support vector networks) are supervised max-margin models with associated learning algorithms that analyze data for classification and regression analysis. Developed at AT&T Bell Laboratories, SVMs are one of the most studied models, being based on statistical learning frameworks of VC theory proposed by Vapnik (1982, 1995) and Chervonenkis (1974). In addition to performing linear classification, SVMs can efficiently perform non-linear classification using the ''kernel trick'', representing the data only through a set of pairwise similarity comparisons between the original data points using a kernel function, which transforms them into coordinates in a higher-dimensional feature space. Thus, SVMs use the kernel trick to implicitly map their inputs into high-dimensional feature spaces, where linear classification can be performed. Being max-margin models, SVMs are resilient to noisy data (e.g., misclassified examples). ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Soft Set
Soft set theory is a generalization of fuzzy set theory, that was proposed by Molodtsov in 1999 to deal with uncertainty in a parametric manner. A soft set is a parameterised family of sets - intuitively, this is "soft" because the boundary of the set depends on the parameters. Formally, a soft set, over a universal set X and set of parameters E is a pair (''f'', ''A'') where ''A'' is a subset In mathematics, a Set (mathematics), set ''A'' is a subset of a set ''B'' if all Element (mathematics), elements of ''A'' are also elements of ''B''; ''B'' is then a superset of ''A''. It is possible for ''A'' and ''B'' to be equal; if they a ... of E, and ''f'' is a function from ''A'' to the power set of X. For each ''e'' in ''A'', the set ''f''(''e'') is called the value set of ''e'' in (''f'', ''A''). A systematic literature review on soft set theory was published in the journal Neural Computing and Applications in February 2024. One of the most important steps for the new ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Rough Set
In computer science, a rough set, first described by Polish computer scientist Zdzisław I. Pawlak, is a formal approximation of a crisp set (i.e., conventional set) in terms of a pair of sets which give the ''lower'' and the ''upper'' approximation of the original set. In the standard version of rough set theory described in Pawlak (1991), the lower- and upper-approximation sets are crisp sets, but in other variations, the approximating sets may be fuzzy sets. Definitions The following section contains an overview of the basic framework of rough set theory, as originally proposed by Zdzisław I. Pawlak, along with some of the key definitions. More formal properties and boundaries of rough sets can be found in and cited references. The initial and basic theory of rough sets is sometimes referred to as ''"Pawlak Rough Sets"'' or ''"classical rough sets"'', as a means to distinguish it from more recent extensions and generalizations. Information system framework Let I = (\mathb ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Natural Language Processing
Natural language processing (NLP) is a subfield of computer science and especially artificial intelligence. It is primarily concerned with providing computers with the ability to process data encoded in natural language and is thus closely related to information retrieval, knowledge representation and computational linguistics, a subfield of linguistics. Major tasks in natural language processing are speech recognition, text classification, natural-language understanding, natural language understanding, and natural language generation. History Natural language processing has its roots in the 1950s. Already in 1950, Alan Turing published an article titled "Computing Machinery and Intelligence" which proposed what is now called the Turing test as a criterion of intelligence, though at the time that was not articulated as a problem separate from artificial intelligence. The proposed test includes a task that involves the automated interpretation and generation of natural language ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Naive Bayes Classifier
In statistics, naive (sometimes simple or idiot's) Bayes classifiers are a family of " probabilistic classifiers" which assumes that the features are conditionally independent, given the target class. In other words, a naive Bayes model assumes the information about the class provided by each variable is unrelated to the information from the others, with no information shared between the predictors. The highly unrealistic nature of this assumption, called the naive independence assumption, is what gives the classifier its name. These classifiers are some of the simplest Bayesian network models. Naive Bayes classifiers generally perform worse than more advanced models like logistic regressions, especially at quantifying uncertainty (with naive Bayes models often producing wildly overconfident probabilities). However, they are highly scalable, requiring only one parameter for each feature or predictor in a learning problem. Maximum-likelihood training can be done by evaluating a c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |