|
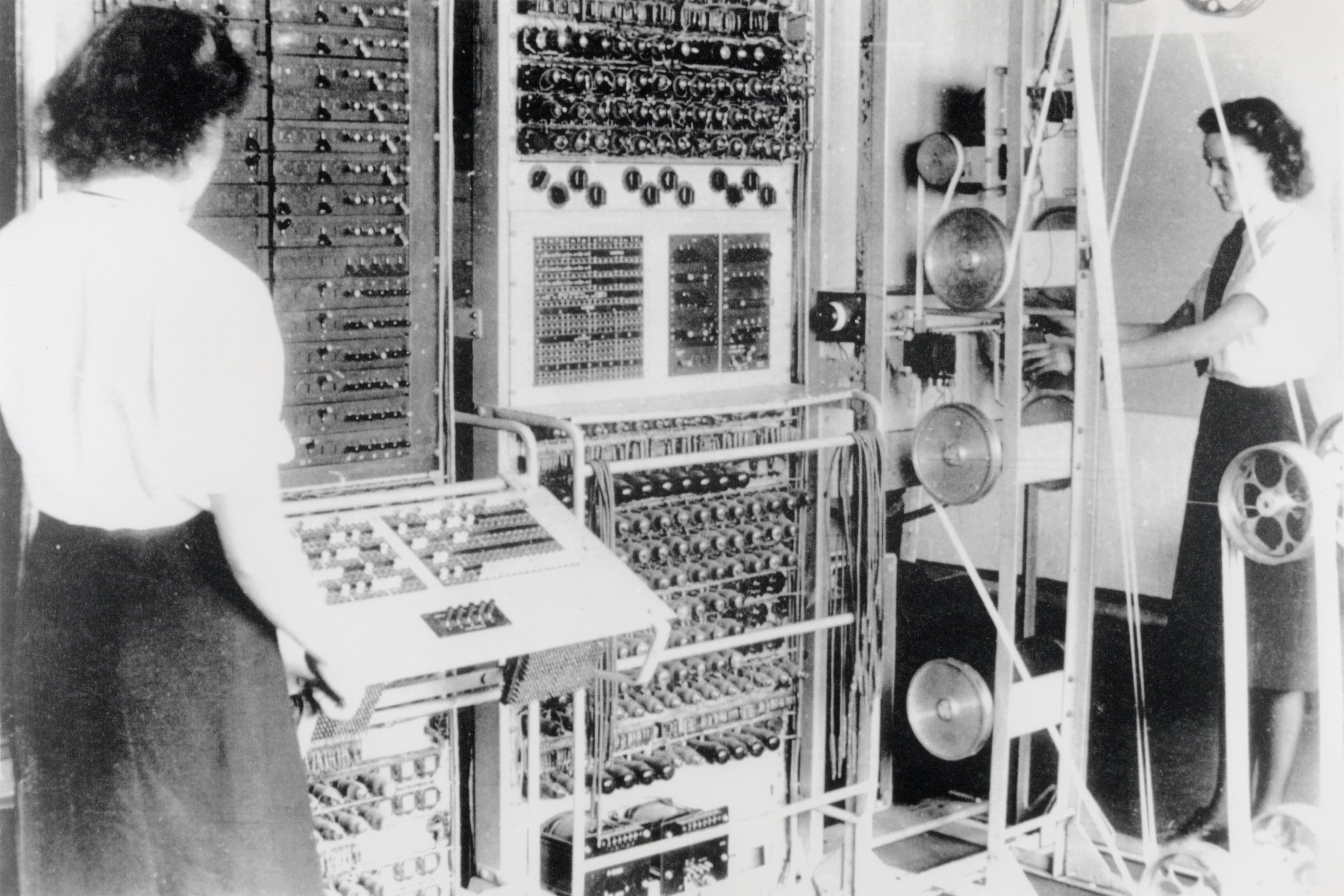
Cryptanalytic Computer
A cryptanalytic computer is a computer designed to be used for cryptanalysis, which nowadays involves massive statistical analysis and multiple trial decryptions that since before World War II are possible only with automated equipment. Polish cryptanalysts designed and built automated aids in their work on Enigma traffic. Arguably, the first modern computer (digital, electronic, and somewhat programmable) was built for cryptanalytic work at Bletchley Park (the Colossus) during the war. More modern computers were important after World War II, and some machines (like the Cray-1) are reported to have had machine instructions hardwired in at the request of NSA. Computers continue to be important in cryptanalysis well into the 21st century. NSA, in fact, is said to have the largest number of installed computers on the planet. Whether this is true in an age of Google computer farms and such is doubtful but remains publicly unknown. See also * Bomba (cryptography) * Bombe * Colossu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
UNIVAC 1101 "Atlas" Cryptanalytic Installation
UNIVAC (Universal Automatic Computer) was a line of electronic digital stored-program computers starting with the products of the Eckert–Mauchly Computer Corporation. Later the name was applied to a division of the Remington Rand company and successor organizations. The BINAC, built by the Eckert–Mauchly Computer Corporation, was the first general-purpose computer for commercial use, but it was not a success. The last UNIVAC-badged computer was produced in 1986. History and structure J. Presper Eckert and John Mauchly built the ENIAC (Electronic Numerical Integrator and Computer) at the University of Pennsylvania's Moore School of Electrical Engineering between 1943 and 1946. A 1946 patent rights dispute with the university led Eckert and Mauchly to depart the Moore School to form the Electronic Control Company, later renamed Eckert–Mauchly Computer Corporation (EMCC), based in Philadelphia, Pennsylvania. That company first built a computer called BINAC (BINary Automat ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer
A computer is a machine that can be programmed to Execution (computing), carry out sequences of arithmetic or logical operations (computation) automatically. Modern digital electronic computers can perform generic sets of operations known as Computer program, programs. These programs enable computers to perform a wide range of tasks. A computer system is a nominally complete computer that includes the Computer hardware, hardware, operating system (main software), and peripheral equipment needed and used for full operation. This term may also refer to a group of computers that are linked and function together, such as a computer network or computer cluster. A broad range of Programmable logic controller, industrial and Consumer electronics, consumer products use computers as control systems. Simple special-purpose devices like microwave ovens and remote controls are included, as are factory devices like industrial robots and computer-aided design, as well as general-purpose devi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptanalysis
Cryptanalysis (from the Greek ''kryptós'', "hidden", and ''analýein'', "to analyze") refers to the process of analyzing information systems in order to understand hidden aspects of the systems. Cryptanalysis is used to breach cryptographic security systems and gain access to the contents of encrypted messages, even if the cryptographic key is unknown. In addition to mathematical analysis of cryptographic algorithms, cryptanalysis includes the study of side-channel attacks that do not target weaknesses in the cryptographic algorithms themselves, but instead exploit weaknesses in their implementation. Even though the goal has been the same, the methods and techniques of cryptanalysis have changed drastically through the history of cryptography, adapting to increasing cryptographic complexity, ranging from the pen-and-paper methods of the past, through machines like the British Bombes and Colossus computers at Bletchley Park in World War II, to the mathematically advanced comput ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
World War II
World War II or the Second World War, often abbreviated as WWII or WW2, was a world war that lasted from 1939 to 1945. It involved the vast majority of the world's countries—including all of the great powers—forming two opposing military alliances: the Allies and the Axis powers. World War II was a total war that directly involved more than 100 million personnel from more than 30 countries. The major participants in the war threw their entire economic, industrial, and scientific capabilities behind the war effort, blurring the distinction between civilian and military resources. Aircraft played a major role in the conflict, enabling the strategic bombing of population centres and deploying the only two nuclear weapons ever used in war. World War II was by far the deadliest conflict in human history; it resulted in 70 to 85 million fatalities, mostly among civilians. Tens of millions died due to genocides (including the Holocaust), starvation, ma ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Bletchley Park
Bletchley Park is an English country house and estate in Bletchley, Milton Keynes ( Buckinghamshire) that became the principal centre of Allied code-breaking during the Second World War. The mansion was constructed during the years following 1883 for the financier and politician Sir Herbert Leon in the Victorian Gothic, Tudor, and Dutch Baroque styles, on the site of older buildings of the same name. During World War II, the estate housed the Government Code and Cypher School (GC&CS), which regularly penetrated the secret communications of the Axis Powersmost importantly the German Enigma and Lorenz ciphers. The GC&CS team of codebreakers included Alan Turing, Gordon Welchman, Hugh Alexander, Bill Tutte, and Stuart Milner-Barry. The nature of the work at Bletchley remained secret until many years after the war. According to the official historian of British Intelligence, the "Ultra" intelligence produced at Bletchley shortened the war by two to four years, and without it th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Colossus Computer
Colossus was a set of computers developed by British codebreakers in the years 1943–1945 to help in the cryptanalysis of the Lorenz cipher. Colossus used thermionic valves (vacuum tubes) to perform Boolean and counting operations. Colossus is thus regarded as the world's first programmable, electronic, digital computer, although it was programmed by switches and plugs and not by a stored program. Colossus was designed by General Post Office (GPO) research telephone engineer Tommy Flowers to solve a problem posed by mathematician Max Newman at the Government Code and Cypher School (GC&CS) at Bletchley Park. Alan Turing's use of probability in cryptanalysis (see Banburismus) contributed to its design. It has sometimes been erroneously stated that Turing designed Colossus to aid the cryptanalysis of the Enigma. (Turing's machine that helped decode Enigma was the electromechanical Bombe, not Colossus.) The prototype, Colossus Mark 1, was shown to be working in December 1943 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cray-1
The Cray-1 was a supercomputer designed, manufactured and marketed by Cray Research. Announced in 1975, the first Cray-1 system was installed at Los Alamos National Laboratory in 1976. Eventually, over 100 Cray-1s were sold, making it one of the most successful supercomputers in history. It is perhaps best known for its unique shape, a relatively small C-shaped cabinet with a ring of benches around the outside covering the power supplies and the cooling system. The Cray-1 was the first supercomputer to successfully implement the vector processor design. These systems improve the performance of math operations by arranging memory and registers to quickly perform a single operation on a large set of data. Previous systems like the CDC STAR-100 and ASC had implemented these concepts but did so in a way that seriously limited their performance. The Cray-1 addressed these problems and produced a machine that ran several times faster than any similar design. The Cray-1's architect w ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Google
Google LLC () is an American multinational technology company focusing on search engine technology, online advertising, cloud computing, computer software, quantum computing, e-commerce, artificial intelligence, and consumer electronics. It has been referred to as "the most powerful company in the world" and one of the world's most valuable brands due to its market dominance, data collection, and technological advantages in the area of artificial intelligence. Its parent company Alphabet is considered one of the Big Five American information technology companies, alongside Amazon, Apple, Meta, and Microsoft. Google was founded on September 4, 1998, by Larry Page and Sergey Brin while they were PhD students at Stanford University in California. Together they own about 14% of its publicly listed shares and control 56% of its stockholder voting power through super-voting stock. The company went public via an initial public offering (IPO) in 2004. In 2015, Google was reor ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Bomba (cryptography)
The ''bomba'', or ''bomba kryptologiczna'' (Polish for "bomb" or "cryptologic bomb"), was a special-purpose machine designed around October 1938 by Polish Cipher Bureau cryptologist Marian Rejewski to break German Enigma-machine ciphers. Etymology How the machine came to be called a "bomb" has been an object of fascination and speculation. One theory, most likely apocryphal, originated with Polish engineer and army officer Tadeusz Lisicki (who knew Rejewski and his colleague Henryk Zygalski in wartime Britain but was never associated with the Cipher Bureau). He claimed that Jerzy Różycki (the youngest of the three Enigma cryptologists, and who had died in a Mediterranean passenger-ship sinking in January 1942) named the "bomb" after an ice-cream dessert of that name. This story seems implausible, since Lisicki had not known Różycki. Rejewski himself stated that the device had been dubbed a "bomb" "for lack of a better idea". Perhaps the most credible explanation is given ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Bombe
The bombe () was an electro-mechanical device used by British cryptologists to help decipher German Enigma-machine-encrypted secret messages during World War II. The US Navy and US Army later produced their own machines to the same functional specification, albeit engineered differently both from each other and from Polish and British bombes. The British bombe was developed from a device known as the " bomba" ( pl, bomba kryptologiczna), which had been designed in Poland at the Biuro Szyfrów (Cipher Bureau) by cryptologist Marian Rejewski, who had been breaking German Enigma messages for the previous seven years, using it and earlier machines. The initial design of the British bombe was produced in 1939 at the UK Government Code and Cypher School (GC&CS) at Bletchley Park by Alan Turing, with an important refinement devised in 1940 by Gordon Welchman. The engineering design and construction was the work of Harold Keen of the British Tabulating Machine Company. The first bo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Deep Crack
In cryptography, the EFF DES cracker (nicknamed "Deep Crack") is a machine built by the Electronic Frontier Foundation (EFF) in 1998, to perform a brute force search of the Data Encryption Standard (DES) cipher's key space – that is, to decrypt an encrypted message by trying every possible key. The aim in doing this was to prove that the key size of DES was not sufficient to be secure. Background DES uses a 56-bit key, meaning that there are 256 possible keys under which a message can be encrypted. This is exactly 72,057,594,037,927,936, or approximately 72 quadrillion possible keys. One of the major criticisms of DES, when proposed in 1975, was that the key size was too short. Martin Hellman and Whitfield Diffie of Stanford University estimated that a machine fast enough to test that many keys in a day would have cost about $20 million in 1976, an affordable sum to national intelligence agencies such as the US National Security Agency. Subsequent advances in the price/perf ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |