|
Critical Section
In concurrent programming, concurrent accesses to shared resources can lead to unexpected or erroneous behavior, so parts of the program where the shared resource is accessed need to be protected in ways that avoid the concurrent access. One way to do so is known as a critical section or critical region. This protected section cannot be entered by more than one process or thread at a time; others are suspended until the first leaves the critical section. Typically, the critical section accesses a shared resource, such as a data structure, a peripheral device, or a network connection, that would not operate correctly in the context of multiple concurrent accesses. Need for critical sections Different codes or processes may consist of the same variable or other resources that need to be read or written but whose results depend on the order in which the actions occur. For example, if a variable is to be read by process A, and process B has to write to the same variabl ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Concurrent Programming
Concurrent means happening at the same time. Concurrency, concurrent, or concurrence may refer to: Law * Concurrence, in jurisprudence, the need to prove both ''actus reus'' and ''mens rea'' * Concurring opinion (also called a "concurrence"), a legal opinion which supports the conclusion, though not always the reasoning, of the majority. * Concurrent estate, a concept in property law * Concurrent resolution, a legislative measure passed by both chambers of the United States Congress * Concurrent sentences, in criminal law, periods of imprisonment that are served simultaneously Computing * Concurrency (computer science), the property of program, algorithm, or problem decomposition into order-independent or partially-ordered units * Concurrent computing, the overlapping execution of multiple interacting computational tasks * Concurrence (quantum computing), a measure used in quantum information theory * Concurrent Computer Corporation, an American computer systems manufacturer ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
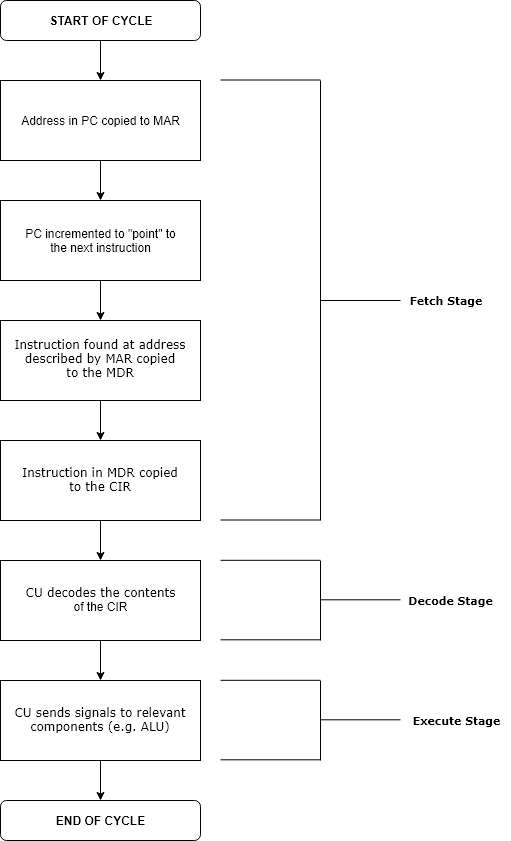
Execution (computers)
Execution in computer and software engineering is the process by which a computer or virtual machine reads and acts on the instructions of a computer program. Each instruction of a program is a description of a particular action which must be carried out, in order for a specific problem to be solved. Execution involves repeatedly following a ' fetch–decode–execute' cycle for each instruction done by control unit. As the executing machine follows the instructions, specific effects are produced in accordance with the semantics of those instructions. Programs for a computer may be executed in a batch process without human interaction or a user may type commands in an interactive session of an interpreter. In this case, the "commands" are simply program instructions, whose execution is chained together. The term run is used almost synonymously. A related meaning of both "to run" and "to execute" refers to the specific action of a user starting (or ''launching'' or ''invok ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
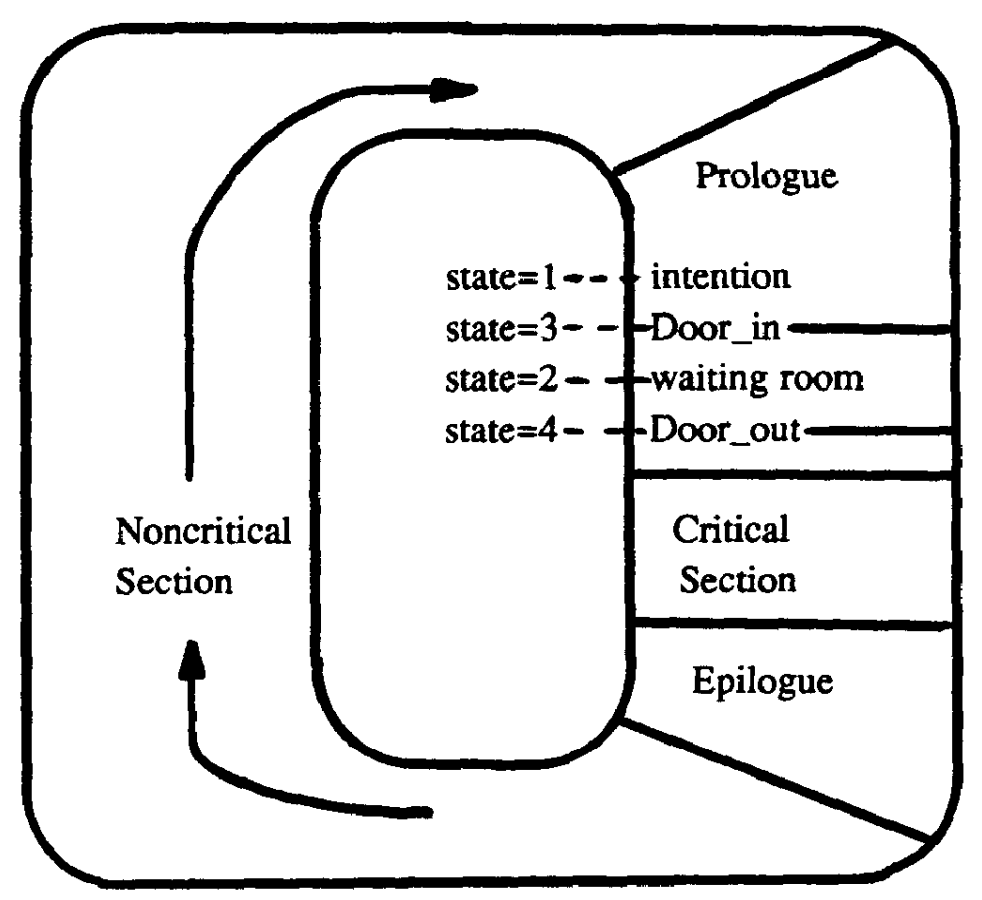
Szymański's Algorithm
Szymański's Mutual Exclusion Algorithm is a mutual exclusion algorithm devised by computer scientist Dr. Bolesław Szymański, which has many favorable properties including linear wait, and which extension solved the open problem posted by Leslie Lamport whether there is an algorithm with a constant number of communication bits per process that satisfies every reasonable fairness and failure-tolerance requirement that Lamport conceived of (Lamport's solution used n factorial communication variables vs. Szymański's 5). The algorithm The algorithm is modeled on a waiting room with an entry and exit doorway. Initially the entry door is open and the exit door is closed. All processes which request entry into the critical section at roughly the same time enter the waiting room; the last of them closes the entry door and opens the exit door. The processes then enter the critical section one by one (or in larger groups if the critical section permits this). The last process to leave ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mutual Exclusion
In computer science, mutual exclusion is a property of concurrency control, which is instituted for the purpose of preventing race conditions. It is the requirement that one thread of execution never enters a critical section while a concurrent thread of execution is already accessing said critical section, which refers to an interval of time during which a thread of execution accesses a shared resource or shared memory. The shared resource is a data object, which two or more concurrent threads are trying to modify (where two concurrent read operations are permitted but, no two concurrent write operations or one read and one write are permitted, since it leads to data inconsistency). Mutual exclusion algorithm ensures that if a process is already performing write operation on a data object ritical sectionno other process/thread is allowed to access/modify the same object until the first process has finished writing upon the data object ritical sectionand released the object ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Lamport's Bakery Algorithm
Lamport's bakery algorithm is a computer algorithm devised by computer scientist Leslie Lamport, as part of his long study of the formal correctness of concurrent systems, which is intended to improve the safety in the usage of shared resources among multiple threads by means of mutual exclusion. In computer science, it is common for multiple threads to simultaneously access the same resources. Data corruption can occur if two or more threads try to write into the same memory location, or if one thread reads a memory location before another has finished writing into it. Lamport's bakery algorithm is one of many mutual exclusion algorithms designed to prevent concurrent threads entering critical sections of code concurrently to eliminate the risk of data corruption. Algorithm Analogy Lamport envisioned a bakery with a numbering machine at its entrance so each customer is given a unique number. Numbers increase by one as customers enter the store. A global counter ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Eisenberg & McGuire Algorithm
The Eisenberg & McGuire algorithm is an algorithm for solving the critical sections problem, a general version of the dining philosophers problem. It was described in 1972 by Murray A. Eisenberg and Michael R. McGuire. Algorithm All the ''n''-processes share the following variables: enum pstate = ; pstate flags int turn; The variable turn is set arbitrarily to a number between 0 and ''n''−1 at the start of the algorithm. The flags variable for each process is set to WAITING whenever it intends to enter the critical section. flags takes either IDLE or WAITING or ACTIVE. Initially the flags variable for each process is initialized to IDLE. repeat until ((index >= n) && ((turn = i) , , (flags urn= IDLE))); /* Start of CRITICAL SECTION */ /* claim the turn and proceed */ turn := i; /* Critical Section Code of the Process */ /* End of CRITICAL SECTION */ /* find a process which is not IDLE */ /* (if there are no others, we will find ourselv ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Dekker's Algorithm
Dekker's algorithm is the first known correct solution to the mutual exclusion problem in concurrent programming where processes only communicate via shared memory. The solution is attributed to Dutch mathematician Th. J. Dekker by Edsger W. Dijkstra in an unpublished paper on sequential process descriptions and his manuscript on cooperating sequential processes. It allows two threads to share a single-use resource without conflict, using only shared memory for communication. It avoids the strict alternation of a naïve turn-taking algorithm, and was one of the first mutual exclusion algorithms to be invented. Overview If two processes attempt to enter a critical section at the same time, the algorithm will allow only one process in, based on whose it is. If one process is already in the critical section, the other process will busy wait for the first process to exit. This is done by the use of two flags, and , which indicate an intention to enter the critical section on t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Database Transaction
A database transaction symbolizes a unit of work, performed within a database management system (or similar system) against a database, that is treated in a coherent and reliable way independent of other transactions. A transaction generally represents any change in a database. Transactions in a database environment have two main purposes: # To provide reliable units of work that allow correct recovery from failures and keep a database consistent even in cases of system failure. For example: when execution prematurely and unexpectedly stops (completely or partially) in which case many operations upon a database remain uncompleted, with unclear status. # To provide isolation between programs accessing a database concurrently. If this isolation is not provided, the programs' outcomes are possibly erroneous. In a database management system, a transaction is a single unit of logic or work, sometimes made up of multiple operations. Any logical calculation done in a consistent mode in ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Erroneous Program
In the design of programming language A programming language is a system of notation for writing computer programs. Most programming languages are text-based formal languages, but they may also be graphical. They are a kind of computer language. The description of a programming l ...s, an erroneous program is one whose semantics are not well-defined, but where the language implementation is not obligated to signal an error either at compile or at execution time. For example, in Ada: :In addition to bounded errors, the language rules define certain kinds of errors as leading to erroneous execution. Like bounded errors, the implementation need not detect such errors either prior to or during run time. Unlike bounded errors, there is no language-specified bound on the possible effect of erroneous execution; the effect is in general not predictable.''Ada Reference Manual'' ISO/IEC 8652:1995(Epdf section 1.1.5. Defining a condition as "erroneous" means that the language implemen ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hash Table
In computing, a hash table, also known as hash map, is a data structure that implements an associative array or dictionary. It is an abstract data type that maps keys to values. A hash table uses a hash function to compute an ''index'', also called a ''hash code'', into an array of ''buckets'' or ''slots'', from which the desired value can be found. During lookup, the key is hashed and the resulting hash indicates where the corresponding value is stored. Ideally, the hash function will assign each key to a unique bucket, but most hash table designs employ an imperfect hash function, which might cause hash '' collisions'' where the hash function generates the same index for more than one key. Such collisions are typically accommodated in some way. In a well-dimensioned hash table, the average time complexity for each lookup is independent of the number of elements stored in the table. Many hash table designs also allow arbitrary insertions and deletions of key–value pa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Tree (data Structure)
In computer science, a tree is a widely used abstract data type that represents a hierarchical tree structure with a set of connected nodes. Each node in the tree can be connected to many children (depending on the type of tree), but must be connected to exactly one parent, except for the ''root'' node, which has no parent. These constraints mean there are no cycles or "loops" (no node can be its own ancestor), and also that each child can be treated like the root node of its own subtree, making recursion a useful technique for tree traversal. In contrast to linear data structures, many trees cannot be represented by relationships between neighboring nodes in a single straight line. Binary trees are a commonly used type, which constrain the number of children for each parent to exactly two. When the order of the children is specified, this data structure corresponds to an ordered tree in graph theory. A value or pointer to other data may be associated with every node in the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Linked List
In computer science, a linked list is a linear collection of data elements whose order is not given by their physical placement in memory. Instead, each element points to the next. It is a data structure consisting of a collection of nodes which together represent a sequence. In its most basic form, each node contains: data, and a reference (in other words, a ''link'') to the next node in the sequence. This structure allows for efficient insertion or removal of elements from any position in the sequence during iteration. More complex variants add additional links, allowing more efficient insertion or removal of nodes at arbitrary positions. A drawback of linked lists is that access time is linear (and difficult to pipeline). Faster access, such as random access, is not feasible. Arrays have better cache locality compared to linked lists. Linked lists are among the simplest and most common data structures. They can be used to implement several other common abstract data types ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |