|
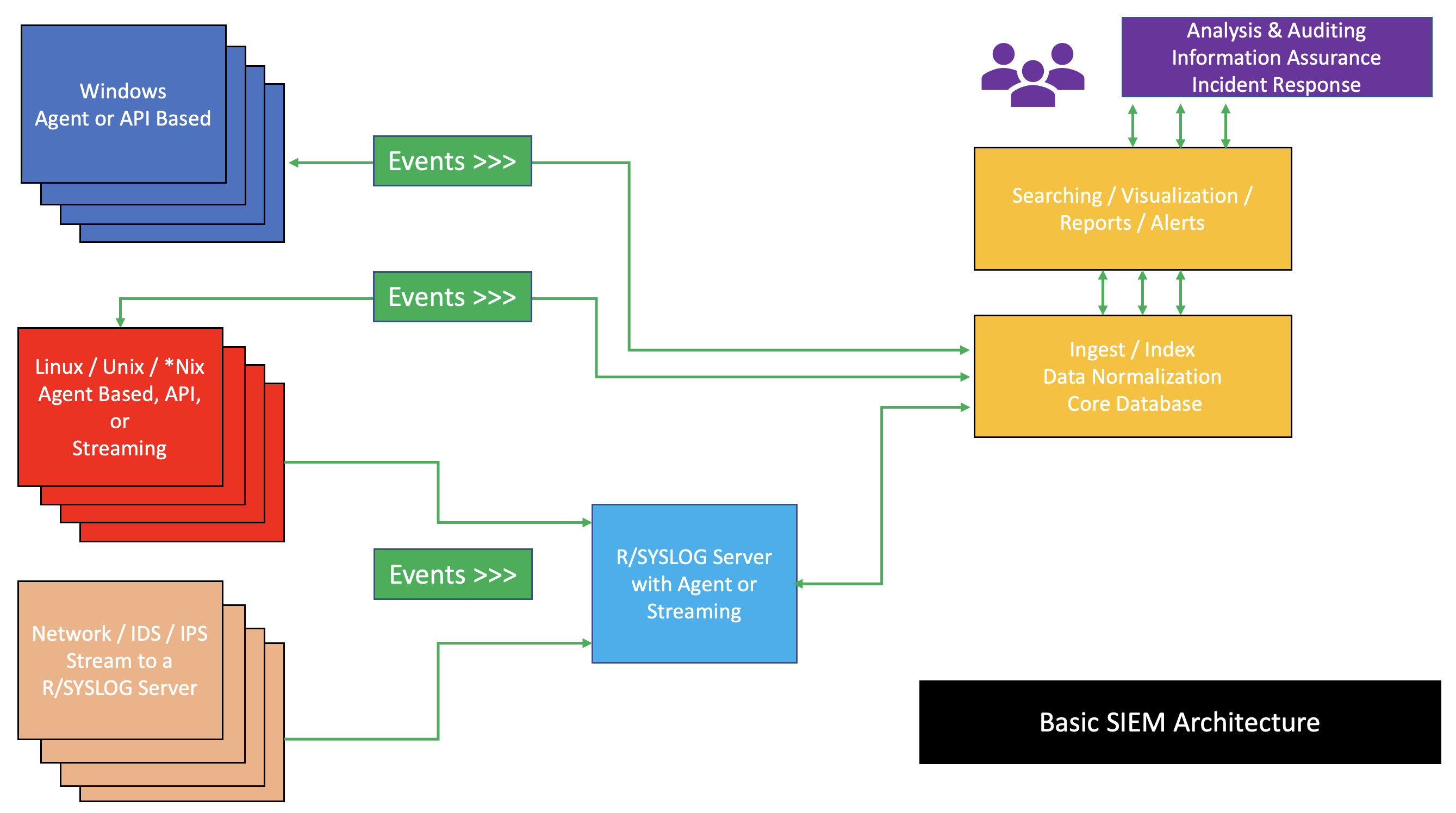
SIEM
Security information and event management (SIEM) is a field within computer security that combines security information management (SIM) and security event management (SEM) to enable real-time analysis of security alerts generated by applications and network hardware. SIEM systems are central to Security operations center, security operations centers (SOCs), where they are employed to detect, investigate, and respond to security incidents. SIEM technology collects and aggregates data from various systems, allowing organizations to meet compliance requirements while safeguarding against Cyberattack, threats. National Institute of Standards and Technology (NIST) definition for SIEM tool is application that provides the ability to gather security data from information system components and present that data as actionable information via a single interface. SIEM tools can be implemented as software, hardware, or managed services. SIEM systems log security events and generating reports to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Security Event Manager
Security event management (SEM), and the related Security information management, SIM and SIEM, are computer security disciplines that use data inspection tools to centralize the storage and interpretation of logs or events generated by other software running on a network. Overview The acronyms ''SEM'', ''SIM,'' and ''SIEM'' have sometimes been used interchangeably, but generally refer to the different primary focus of products: * ''Log management'': Focus on simple collection and storage of data logging, log messages and audit trails * ''Security information management'' (Security information management, SIM): Long-term storage and analysis and reporting of log data. * ''Security event manager'' (SEM): Real-time monitoring, correlation of events, notifications, and console views. * ''Security information and event management'' (Security information and event management, SIEM): Combines SIM and SEM and provides real-time analysis of security alerts generated by network hardware and a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Security Event Management
Security event management (SEM), and the related SIM and SIEM, are computer security disciplines that use data inspection tools to centralize the storage and interpretation of logs or events generated by other software running on a network. Overview The acronyms ''SEM'', ''SIM,'' and ''SIEM'' have sometimes been used interchangeably, but generally refer to the different primary focus of products: * ''Log management'': Focus on simple collection and storage of log messages and audit trails * ''Security information management'' ( SIM): Long-term storage and analysis and reporting of log data. * ''Security event manager'' (SEM): Real-time monitoring, correlation of events, notifications, and console views. * ''Security information and event management'' (SIEM): Combines SIM and SEM and provides real-time analysis of security alerts generated by network hardware and applications. Event logs Many systems and applications which run on a computer network generate events which are kept i ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Security Information Management
Security information management (SIM) is an information security industry term for the collection of data such as log files into a central repository for trend analysis. Overview SIM products generally are software agents running on the computer systems that are monitored. The recorded log information is then sent to a centralized server that acts as a "security console". The console typically displays reports, charts, and graphs of that information, often in real time. Some software agents can incorporate local filters to reduce and manipulate the data that they send to the server, although typically from a forensic point of view you would collect all audit and accounting logs to ensure you can recreate a security incident. The security console is monitored by an administrator who reviews the consolidated information and takes action in response to any alerts issued. The data that is sent to the server to be correlated and analyzed are normalized by the software agents into a c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Intrusion Detection
An intrusion detection system (IDS) is a device or software application that monitors a network or systems for malicious activity or policy violations. Any intrusion activity or violation is typically either reported to an administrator or collected centrally using a security information and event management (SIEM) system. A SIEM system combines outputs from multiple sources and uses alarm filtering techniques to distinguish malicious activity from false alarms. IDS types range in scope from single computers to large networks. The most common classifications are network intrusion detection systems (NIDS) and host-based intrusion detection systems (HIDS). A system that monitors important operating system files is an example of an HIDS, while a system that analyzes incoming network traffic is an example of an NIDS. It is also possible to classify IDS by detection approach. The most well-known variants are signature-based detection (recognizing bad patterns, such as exploitatio ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Security Information Management
Security information management (SIM) is an information security industry term for the collection of data such as log files into a central repository for trend analysis. Overview SIM products generally are software agents running on the computer systems that are monitored. The recorded log information is then sent to a centralized server that acts as a "security console". The console typically displays reports, charts, and graphs of that information, often in real time. Some software agents can incorporate local filters to reduce and manipulate the data that they send to the server, although typically from a forensic point of view you would collect all audit and accounting logs to ensure you can recreate a security incident. The security console is monitored by an administrator who reviews the consolidated information and takes action in response to any alerts issued. The data that is sent to the server to be correlated and analyzed are normalized by the software agents into a c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Security
Computer security (also cybersecurity, digital security, or information technology (IT) security) is a subdiscipline within the field of information security. It consists of the protection of computer software, systems and computer network, networks from Threat (security), threats that can lead to unauthorized information disclosure, theft or damage to computer hardware, hardware, software, or Data (computing), data, as well as from the disruption or misdirection of the Service (economics), services they provide. The significance of the field stems from the expanded reliance on computer systems, the Internet, and wireless network standards. Its importance is further amplified by the growth of smart devices, including smartphones, televisions, and the various devices that constitute the Internet of things (IoT). Cybersecurity has emerged as one of the most significant new challenges facing the contemporary world, due to both the complexity of information systems and the societi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
SECaaS
Security as a service (SECaaS) is a business model in which a service provider integrates their security services into a corporate infrastructure on a subscription basis more cost-effectively than most individuals or corporations can provide on their own when the total cost of ownership is considered. SECaaS is inspired by the "software as a service" model as applied to information security type services and does not require on-premises hardware, avoiding substantial capital outlays. These security services often include authentication, anti-virus, anti-malware/spyware, intrusion detection, Penetration testing, and security event management, among others. Outsourced security licensing and delivery are boasting a multibillion-dollar market. SECaaS provides users with Internet security services providing protection from online threats and attacks such as DDoS that are constantly searching for access points to compromise websites. As the demand and use of cloud computing skyrockets, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Log Management
Log management is the process for generating, transmitting, storing, accessing, and disposing of log data. A log data (or ''logs'') is composed of entries (records), and each entry contains information related to a specific event that occur within an organization's computing assets, including physical and virtual platforms, networks, services, and cloud environments. The process of log management generally breaks down into: * Log collection - a process of capturing actual data from log files, application standard output stream (Standard streams, stdout), network Network socket, socket and other sources. * Logs aggregation (centralization) - a process of putting all the log data together in a single place for the sake of further analysis or/and retention. * Log storage and retention - a process of handling large volumes of log data according to corporate or regulatory policies (compliance). * Log analysis - a process that helps operations and security team to handle system performa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Anti-malware
Antivirus software (abbreviated to AV software), also known as anti-malware, is a computer program used to prevent, detect, and remove malware. Antivirus software was originally developed to detect and remove computer viruses, hence the name. However, with the proliferation of other malware, antivirus software started to protect against other computer threats. Some products also include protection from malicious URLs, spam, and phishing. History 1971–1980 period (pre-antivirus days) The first known computer virus appeared in 1971 and was dubbed the " Creeper virus". This computer virus infected Digital Equipment Corporation's ( DEC) PDP-10 mainframe computers running the TENEX operating system.From the first email to the first YouTube video: a d ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Authentication
Authentication (from ''authentikos'', "real, genuine", from αὐθέντης ''authentes'', "author") is the act of proving an Logical assertion, assertion, such as the Digital identity, identity of a computer system user. In contrast with identification, the act of indicating a person or thing's identity, authentication is the process of verifying that identity. Authentication is relevant to multiple fields. In art, antiques, and anthropology, a common problem is verifying that a given artifact was produced by a certain person, or in a certain place (i.e. to assert that it is not counterfeit), or in a given period of history (e.g. by determining the age via carbon dating). In computer science, verifying a user's identity is often required to allow access to confidential data or systems. It might involve validating personal identity documents. In art, antiques and anthropology Authentication can be considered to be of three types: The ''first'' type of authentication is accep ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Virtualization
In computing, virtualization (abbreviated v12n) is a series of technologies that allows dividing of physical computing resources into a series of virtual machines, operating systems, processes or containers. Virtualization began in the 1960s with IBM CP/CMS. The control program CP provided each user with a simulated stand-alone System/360 computer. In hardware virtualization, the '' host machine'' is the machine that is used by the virtualization and the ''guest machine'' is the virtual machine. The words ''host'' and ''guest'' are used to distinguish the software that runs on the physical machine from the software that runs on the virtual machine. The software or firmware that creates a virtual machine on the host hardware is called a '' hypervisor'' or ''virtual machine monitor''. Hardware virtualization is not the same as hardware emulation. Hardware-assisted virtualization facilitates building a virtual machine monitor and allows guest OSes to be run in isolation. Deskt ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |