|
Endpoint Detection And Response
Endpoint detection and response (EDR), also known as endpoint threat detection and response (ETDR), is a cybersecurity technology that continually monitors an "endpoint" (e.g. a client device such as a mobile phone, laptop, Internet of things device) to mitigate malicious cyber threats. History In 2013, Anton Chuvakin of Gartner coined the term "endpoint threat detection and response" for "tools primarily focused on detecting and investigating suspicious activities (and traces of such) other problems on hosts/endpoints". Now, it is commonly known as "endpoint detection and response". According to the ''Endpoint Detection and Response - Global Market Outlook (2017-2026)'' report, the adoption of Cloud-based software, cloud-based and On-premises software, on-premises EDR solutions are going to grow 26% annually, and will be valued at $7273.26 million by 2026. According to the ''Artificial intelligence, Artificial Intelligence (AI) in Cyber Security Market'' report by Zion Market R ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cybersecurity
Computer security (also cybersecurity, digital security, or information technology (IT) security) is a subdiscipline within the field of information security. It consists of the protection of computer software, systems and networks from threats that can lead to unauthorized information disclosure, theft or damage to hardware, software, or data, as well as from the disruption or misdirection of the services they provide. The significance of the field stems from the expanded reliance on computer systems, the Internet, and wireless network standards. Its importance is further amplified by the growth of smart devices, including smartphones, televisions, and the various devices that constitute the Internet of things (IoT). Cybersecurity has emerged as one of the most significant new challenges facing the contemporary world, due to both the complexity of information systems and the societies they support. Security is particularly crucial for systems that govern large-scale sy ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Artificial Intelligence
Artificial intelligence (AI) is the capability of computer, computational systems to perform tasks typically associated with human intelligence, such as learning, reasoning, problem-solving, perception, and decision-making. It is a field of research in computer science that develops and studies methods and software that enable machines to machine perception, perceive their environment and use machine learning, learning and intelligence to take actions that maximize their chances of achieving defined goals. High-profile applications of AI include advanced web search engines (e.g., Google Search); recommendation systems (used by YouTube, Amazon (company), Amazon, and Netflix); virtual assistants (e.g., Google Assistant, Siri, and Amazon Alexa, Alexa); autonomous vehicles (e.g., Waymo); Generative artificial intelligence, generative and Computational creativity, creative tools (e.g., ChatGPT and AI art); and Superintelligence, superhuman play and analysis in strategy games (e.g., ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Network Detection And Response
Network detection and response (NDR) refers to a category of network security products that detect abnormal system behaviors by continuously analyzing network traffic. NDR solutions apply behavioral analytics to inspect raw network packets and metadata for both internal (east-west) and external (north-south) network communications. Description NDR is delivered through a combination of hardware and software sensors, along with a software or SaaS management console. Organizations use NDR to detect and contain malicious post-breach activity such as ransomware or insider malicious activity. NDR focuses on identifying abnormal behavior patterns and anomalies rather than relying solely on signature-based threat detection. This allows NDR to spot weak signals and unknown threats from network traffic, like lateral movement or data exfiltration. NDR provides visibility into network activities to identify anomalies using machine learning algorithms. The automated response capab ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data Loss Prevention Software
Data loss prevention (DLP) software detects potential data breaches/data exfiltration transmissions and prevents them by monitoring, detecting and blocking sensitive data while ''in use'' (endpoint actions), ''in motion'' ( network traffic), and ''at rest'' (data storage). The terms " data loss" and " data leak" are related and are often used interchangeably.Asaf Shabtai, Yuval Elovici, Lior Rokach,A Survey of Data Leakage Detection and Prevention Solutions Springer-Verlag New York Incorporated, 2012 Data loss incidents turn into data leak incidents in cases where media containing sensitive information are lost and subsequently acquired by an unauthorized party. However, a data leak is possible without losing the data on the originating side. Other terms associated with data leakage prevention are information leak detection and prevention (ILDP), information leak prevention (ILP), content monitoring and filtering (CMF), information protection and control (IPC) and extrusion preve ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Endpoint Security
Endpoint security or endpoint protection is an approach to the protection of computer networks that are remotely bridged to client devices. The connection of endpoint devices such as laptops, tablets, mobile phones, and other wireless devices to corporate networks creates attack paths for security threats. Endpoint security attempts to ensure that such devices follow compliance to standards. The endpoint security space has evolved since the 2010s away from limited antivirus software and into more advanced, comprehensive defenses. This includes next-generation antivirus, threat detection, investigation, and response, device management, data loss prevention (DLP), patch management, and other considerations to face evolving threats. Corporate network security Endpoint security management is a software approach that helps to identify and manage the users' computer and data access over a corporate network. This allows the network administrator to restrict the use of sensitive ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mitre Corporation
The Mitre Corporation (stylized as The MITRE Corporation and MITRE) is an American not-for-profit organization with dual headquarters in Bedford, Massachusetts, and McLean, Virginia. It manages federally funded research and development centers (FFRDCs) supporting various U.S. government agencies in the aviation, defense, healthcare, homeland security, and cybersecurity fields, among others. MITRE formed in 1958 as a military think tank, spun out from the radar and computer research at the MIT Lincoln Laboratory. Over the years, MITRE's field of study had greatly diversified. In the 1990s, with the winding down of the Cold War, private companies complained that MITRE had an unfair advantage competing for civilian contracts; in 1996 this led to the civilian projects being spun off to a new company, Mitretek. Mitretek was renamed Noblis in 2007. Etymology The name MITRE was created by James McCormack Jr., one of the original board members. The name is not an acronym, althoug ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
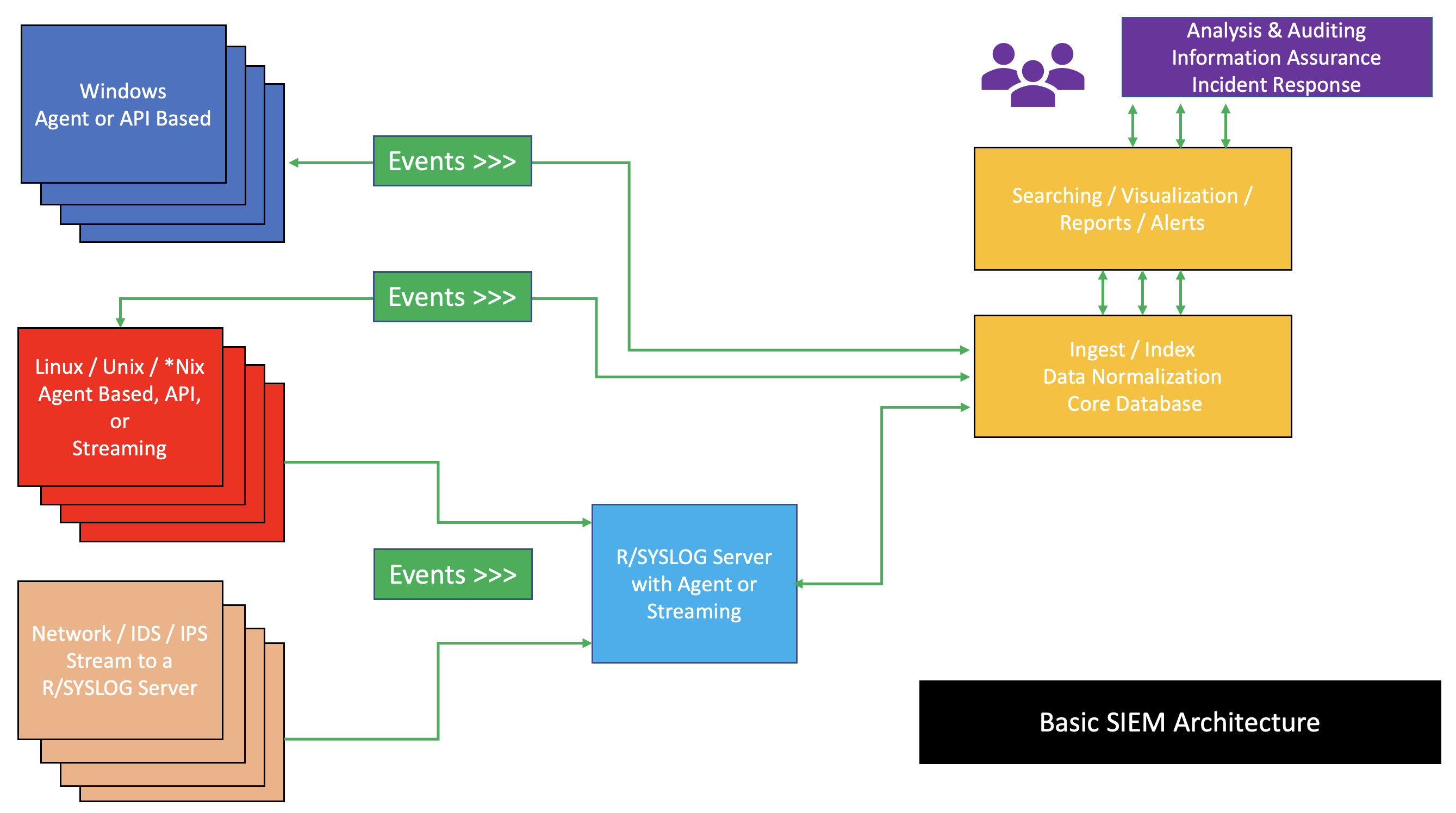
Security Information And Event Management
Security information and event management (SIEM) is a field within computer security that combines security information management (SIM) and security event management (SEM) to enable real-time analysis of security alerts generated by applications and network hardware. SIEM systems are central to Security operations center, security operations centers (SOCs), where they are employed to detect, investigate, and respond to security incidents. SIEM technology collects and aggregates data from various systems, allowing organizations to meet compliance requirements while safeguarding against Cyberattack, threats. National Institute of Standards and Technology (NIST) definition for SIEM tool is application that provides the ability to gather security data from information system components and present that data as actionable information via a single interface. SIEM tools can be implemented as software, hardware, or managed services. SIEM systems log security events and generating reports to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Advanced Persistent Threat
An advanced persistent threat (APT) is a stealthy threat actor, typically a State (polity), state or state-sponsored group, which gains unauthorized access to a computer network and remains undetected for an extended period. In recent times, the term may also refer to non-state-sponsored groups conducting large-scale targeted intrusions for specific goals. Such threat actors' motivations are typically political or economic. Every major business sector has recorded instances of cyberattacks by advanced actors with specific goals, whether to steal, spy, or disrupt. These targeted sectors include government, Arms industry, defense, financial services, Practice of law, legal services, Manufacturing, industrial, Telecommunication, telecoms, Final good, consumer goods and many more. Some groups utilize traditional espionage vectors, including Social engineering (security), social engineering, Human intelligence (intelligence gathering), human intelligence and Infiltration tactics, infil ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Machine Learning
Machine learning (ML) is a field of study in artificial intelligence concerned with the development and study of Computational statistics, statistical algorithms that can learn from data and generalise to unseen data, and thus perform Task (computing), tasks without explicit Machine code, instructions. Within a subdiscipline in machine learning, advances in the field of deep learning have allowed Neural network (machine learning), neural networks, a class of statistical algorithms, to surpass many previous machine learning approaches in performance. ML finds application in many fields, including natural language processing, computer vision, speech recognition, email filtering, agriculture, and medicine. The application of ML to business problems is known as predictive analytics. Statistics and mathematical optimisation (mathematical programming) methods comprise the foundations of machine learning. Data mining is a related field of study, focusing on exploratory data analysi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mobile Phone
A mobile phone or cell phone is a portable telephone that allows users to make and receive calls over a radio frequency link while moving within a designated telephone service area, unlike fixed-location phones ( landline phones). This radio frequency link connects to the switching systems of a mobile phone operator, providing access to the public switched telephone network (PSTN). Modern mobile telephony relies on a cellular network architecture, which is why mobile phones are often referred to as 'cell phones' in North America. Beyond traditional voice communication, digital mobile phones have evolved to support a wide range of additional services. These include text messaging, multimedia messaging, email, and internet access (via LTE, 5G NR or Wi-Fi), as well as short-range wireless technologies like Bluetooth, infrared, and ultra-wideband (UWB). Mobile phones also support a variety of multimedia capabilities, such as digital photography, video recordin ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Artificial Intelligence
Artificial intelligence (AI) is the capability of computer, computational systems to perform tasks typically associated with human intelligence, such as learning, reasoning, problem-solving, perception, and decision-making. It is a field of research in computer science that develops and studies methods and software that enable machines to machine perception, perceive their environment and use machine learning, learning and intelligence to take actions that maximize their chances of achieving defined goals. High-profile applications of AI include advanced web search engines (e.g., Google Search); recommendation systems (used by YouTube, Amazon (company), Amazon, and Netflix); virtual assistants (e.g., Google Assistant, Siri, and Amazon Alexa, Alexa); autonomous vehicles (e.g., Waymo); Generative artificial intelligence, generative and Computational creativity, creative tools (e.g., ChatGPT and AI art); and Superintelligence, superhuman play and analysis in strategy games (e.g., ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
On-premises Software
On-premises software (abbreviated to on-prem, and often written as "on-premise") is installed and runs on computers on the premises of the person or organization using the software, rather than at a remote facility such as a server farm or cloud. On-premises software is sometimes referred to as " shrinkwrap" software, and off-premises software is commonly called "software as a service" ("SaaS") or "cloud computing". The software consists of database and modules that are combined to particularly serve the unique needs of the large organizations regarding the automation of corporate-wide business system and its functions. Comparison between on-premises and cloud (SaaS) Location On-premises software is established within the organisation's internal system along with the hardware and other infrastructure necessary for the software to function. Cloud-based software is usually served via internet and it can be accessed by users online regardless of the time and their location. Un ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |