|
Allow-list
A whitelist or allowlist is a list or register of entities that are being provided a particular privilege, service, mobility, access or recognition. Entities on the list will be accepted, approved and/or recognized. Whitelisting is the reverse of blacklisting, the practice of identifying entities that are denied, unrecognized, or ostracized. Email whitelists Spam filters often include the ability to "whitelist" certain sender IP addresses, email addresses or domain names to protect their email from being rejected or sent to a junk mail folder. These can be manually maintained by the user or system administrator - but can also refer to externally maintained whitelist services. Non-commercial whitelists Non-commercial whitelists are operated by various non-profit organizations, ISPs, and others interested in blocking spam. Rather than paying fees, the sender must pass a series of tests; for example, their email server must not be an open relay and have a static IP address. The ope ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
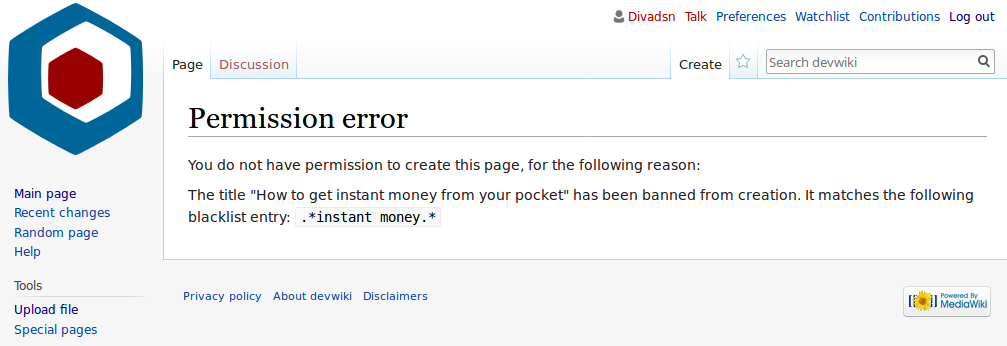
Blacklist (computing)
In computing, a blacklist, disallowlist, blocklist, or denylist is a basic access control mechanism that allows through all elements (email addresses, users, passwords, URLs, IP addresses, domain names, file hashes, etc.), except those explicitly mentioned. Those items on the list are denied access. The opposite is a whitelist, allowlist, or passlist, in which only items on the list are let through whatever gate is being used. A greylist contains items that are temporarily blocked (or temporarily allowed) until an additional step is performed. Blacklists can be applied at various points in a security architecture, such as a host, web proxy, DNS servers, email server, firewall, directory servers or application authentication gateways. The type of element blocked is influenced by the access control location. DNS servers may be well-suited to block domain names, for example, but not URLs. A firewall is well-suited for blocking IP addresses, but less so for blocking maliciou ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Lumension Security
Ivanti () is an IT software company headquartered in South Jordan, Utah, United States. It produces software for IT Security, IT Service Management, IT Asset Management, Unified Endpoint Management, Identity Management and supply chain management. It was formed in January 2017 with the merger of LANDESK and HEAT Software, and later acquired Cherwell Software. The company became more widely known after several major security incidents related to the VPN hardware it sells. History LANDESK LAN Systems was founded in 1985 and its software products acquired by Intel in 1991 to form its LANDESK division. LANDESK introduced the desktop management category in 1993. In 2002 LANDESK Software became a standalone company with headquarters near Salt Lake City, Utah. In 2006, Avocent purchased the company for $416 million. Also in 2006, LANDESK added process management technologies to its product line and extended into the consolidated service desk market with LANDESK Service Desk. In 2010 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Social Privilege
Social privilege is an advantage or entitlement that benefits individuals belonging to certain groups, often to the detriment of others. Privileged groups can be advantaged based on social class, wealth, education, caste, age, height, skin color, physical fitness, nationality, geographic location, cultural differences, ethnic or racial category, gender, gender identity, neurodiversity, physical disability, sexual orientation, religion, and other differentiating factors. Individuals can be privileged in one area, such as education, and not privileged in another area, such as health. The amount of privilege any individual has may change over time, such as when a person becomes disabled, or when a child becomes a young adult. The concept of privilege is generally considered to be a theoretical concept used in a variety of subjects and often linked to social inequality. Privilege is also linked to social and cultural forms of power. It began as an academic concept, but ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Malware
Malware (a portmanteau of ''malicious software'')Tahir, R. (2018)A study on malware and malware detection techniques . ''International Journal of Education and Management Engineering'', ''8''(2), 20. is any software intentionally designed to cause disruption to a computer, server (computing), server, Client (computing), client, or computer network, leak private information, gain unauthorized access to information or systems, deprive access to information, or which unknowingly interferes with the user's computer security and privacy. Researchers tend to classify malware into one or more sub-types (i.e. computer viruses, Computer worm, worms, Trojan horse (computing), Trojan horses, logic bombs, ransomware, spyware, adware, rogue software, Wiper (malware), wipers and keyloggers). Malware poses serious problems to individuals and businesses on the Internet. According to NortonLifeLock, Symantec's 2018 Internet Security Threat Report (ISTR), malware variants number has increased to 66 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Databases
In computing, a database is an organized collection of data or a type of data store based on the use of a database management system (DBMS), the software that interacts with end users, applications, and the database itself to capture and analyze the data. The DBMS additionally encompasses the core facilities provided to administer the database. The sum total of the database, the DBMS and the associated applications can be referred to as a database system. Often the term "database" is also used loosely to refer to any of the DBMS, the database system or an application associated with the database. Before digital storage and retrieval of data have become widespread, index cards were used for data storage in a wide range of applications and environments: in the home to record and store recipes, shopping lists, contact information and other organizational data; in business to record presentation notes, project research and notes, and contact information; in schools as flash card ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Antivirus Software
Antivirus software (abbreviated to AV software), also known as anti-malware, is a computer program used to prevent, detect, and remove malware. Antivirus software was originally developed to detect and remove computer viruses, hence the name. However, with the proliferation of other malware, antivirus software started to protect against other computer threats. Some products also include protection from malicious URLs, spam, and phishing. History 1971–1980 period (pre-antivirus days) The first known computer virus appeared in 1971 and was dubbed the " Creeper virus". This computer virus infected Digital Equipment Corporation's ( DEC) PDP-10 mainframe computers running the TENEX operating system.From the first email to the first YouTube video: a d ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Opt-in
Opt-in email is a term used when someone is not initially added to an emailing list and is instead given the option to join the emailing list. Typically, this is some sort of mailing list, newsletter, or advertising. Opt-out emails do not ask for permission to send emails, these emails are typically criticized as unsolicited bulk emails, better known as spam. Forms There are several common forms of opt-in email: Unconfirmed opt-in/single opt-in Someone first gives an email address to the list software (for instance, on a Web page), but no steps are taken to make sure that this address belongs to the person submitting it. This can cause email from the mailing list to be considered spam because simple typos of the email address can cause the email to be sent to someone else. Malicious subscriptions are also possible, as are subscriptions that are due to spammers forging email addresses that are sent to the email address used to subscribe to the mailing list. Confirmed o ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
DNSWL
An Internet filter is software that restricts or controls the content an Internet user is capable to access, especially when utilized to restrict material delivered over the Internet via the Web, Email, or other means. Such restrictions can be applied at various levels: a government can attempt to apply them nationwide (see Internet censorship), or they can, for example, be applied by an Internet service provider to its clients, by an employer to its personnel, by a school to its students, by a library to its visitors, by a parent to a child's computer, or by an individual user to their own computers. The motive is often to prevent access to content which the computer's owner(s) or other authorities may consider objectionable. When imposed without the consent of the user, content control can be characterised as a form of internet censorship. Some filter software includes time control functions that empowers parents to set the amount of time that child may spend accessing the Inter ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Closed Platform
A closed platform, walled garden, or closed ecosystem is a software system wherein the carrier or service provider has control over applications, content, and/or media, and restricts convenient access to non-approved applicants or content. This is in contrast to an open platform, wherein consumers generally have unrestricted access to applications and content. Overview For example, in telecommunications, the services and applications accessible on a cell phone on any given wireless device were formerly tightly controlled by the mobile operators. The operators limited the applications and developers that were available on users' home portals and home pages. Thus, a service provider might restrict user access to users whose account exhausted the pre-paid money on their account. This has long been a central issue constraining the telecommunications sector, as developers face huge hurdles in making their applications available to end-users. In a more extreme example, the regulated ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Blackballing
Blackballing is a rejection in a traditional form of secret ballot, where a white ball or ballot constitutes a vote in support and a black ball signifies opposition. The system is commonly used where an organization's rules provide that one or two objections, rather than a percentage of the vote (for example, more than 50%), are sufficient to defeat a proposition. Since the seventeenth century, these rules have commonly applied to elections to membership of many gentlemen's clubs and similar institutions such as Masonic lodges and fraternities. The principle of such election rules in a club is that it tends to preserve the current ethos of the club by ensuring that candidates are congenial to (almost) all the existing members. As a public difference of opinions could be divisive, the election is secret. In America, members of fraternal clubs often voted at their meetings without paper ballots as early as the 17th century. In order to progress, votes had to be unanimous in nat ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Blacklisting
Blacklisting is the action of a group or authority compiling a blacklist of people, countries or other entities to be avoided or distrusted as being deemed unacceptable to those making the list; if people are on a blacklist, then they are considered to have done something wrong, or they are considered to be untrustworthy. As a verb, blacklist can mean to put an individual or entity on such a list. A blacklist is synonymous with a list of banned persons or organizations, and is the opposite of a whitelist. Origins of the term The English dramatist Philip Massinger used the phrase "black list" in his 1639 tragedy '' The Unnatural Combat''. After the restoration of the English monarchy brought Charles II of England to the throne in 1660, a list of regicides named those to be punished for the execution of his father. The state papers of Charles II say "If any innocent soul be found in this black list, let him not be offended at me, but consider whether some mistaken principle or ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
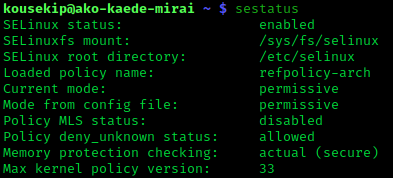
SE Linux
Security-Enhanced Linux (SELinux) is a Linux kernel Linux Security Modules, security module that provides a mechanism for supporting access control security policies, including mandatory access controls (MAC). SELinux is a set of kernel modifications and user-space tools that have been added to various Linux distributions. Its software architecture, architecture strives to separate enforcement of security decisions from the security policy, and streamlines the amount of software involved with security policy enforcement. The key concepts underlying SELinux can be traced to several earlier projects by the United States National Security Agency (NSA). Overview The NSA Security-enhanced Linux Team describes NSA SELinux as a set of patch (computing), patches to the Linux kernel and utilities to provide a strong, flexible, mandatory access control (MAC) architecture into the major subsystems of the kernel. It provides an enhanced mechanism to enforce the separation of information base ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |