|
AVG Internet Security
AVG AntiVirus (previously known as AVG, an abbreviation of Anti-Virus Guard) is a line of antivirus software developed by AVG Technologies, a subsidiary of Avast, a part of Gen Digital. It is available for Windows, macOS and Android. History The brand AVG comes from Grisoft's first product, Anti-Virus Guard, launched in 1992 in the Czech Republic. In 1997, the first AVG licenses were sold in Germany and the UK. AVG was introduced in the US in 1998. The AVG Free Edition helped raise awareness of the AVG product line. In 2006, the AVG security package grew to include anti-spyware as AVG Technologies acquired ewido Networks, an anti-spyware group. AVG Technologies acquired Exploit Prevention Labs (XPL) in December 2007 and incorporated that company's LinkScanner safe search and surf technology into the AVG 8.0 security product range released in March 2008. In January 2009, AVG Technologies acquired Sana Security, a developer of identity theft prevention software. This software ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Gen Digital
Gen Digital Inc. (formerly Symantec Corporation and NortonLifeLock Inc.) is a multinational software company co-headquartered in both Prague, Czech Republic (European Union, EU) and Tempe, Arizona (United States, USA). The company provides computer security, cybersecurity software and services. Gen is a Fortune 500 company and a member of the S&P 500 stock-market index. It is listed at both Nasdaq, NASDAQ and Prague Stock Exchange. Its portfolio includes Norton (software), Norton, Avast (software), Avast, LifeLock, Avira (software), Avira, AVG (software), AVG, ReputationDefender, MoneyLion and CCleaner. On October 9, 2014, Symantec declared it would split into two independent publicly traded companies by the end of 2015. One company would focus on security, the other on information management. On January 29, 2016, Symantec sold its information-management subsidiary, named Veritas Technologies, Veritas, and which Symantec had acquired in 2004, to The Carlyle Group. On August 8, 2 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Quarantine (computing)
Quarantine was an antivirus software from the early 90s that automatically isolated infected files on a computer's hard disk. Files put in quarantine were then no longer capable of infecting their hosting system. Development and release In December 1988, shortly after the Morris Worm, work started on ''Quarantine'', an anti-malware and file reliability product. Released in April 1989, ''Quarantine'' was the first such product to use file signature instead of viral signature methods. The original ''Quarantine'' used Hunt's B-tree database of files with both their CRC16 and CRC-CCITT signatures. Doubling the signatures rendered useless, or at least immoderately difficult, attacks based on CRC invariant modifications. Release 2, April 1990, used a CRC-32 signature and one based on CRC-32 but with a few bits in each word shuffled. The subsequent MS-AV from Microsoft, designed by Check Point, apparently relied on only an eight bit checksum—at least out of a few thousand files there w ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Freeware
Freeware is software, often proprietary, that is distributed at no monetary cost to the end user. There is no agreed-upon set of rights, license, or EULA that defines ''freeware'' unambiguously; every publisher defines its own rules for the freeware it offers. For instance, modification, redistribution by third parties, and reverse engineering are permitted by some publishers but prohibited by others. Unlike with free and open-source software, which are also often distributed free of charge, the source code for freeware is typically not made available. Freeware may be intended to benefit its producer by, for example, encouraging sales of a more capable version, as in the freemium and shareware business models. History The term ''freeware'' was coined in 1982 by Andrew Fluegelman, who wanted to sell PC-Talk, the communications application he had created, outside of commercial distribution channels. Fluegelman distributed the program via the same process as ''shareware''. As s ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
1992 Software
Year 199 ( CXCIX) was a common year starting on Monday of the Julian calendar. At the time, it was sometimes known as year 952 ''Ab urbe condita''. The denomination 199 for this year has been used since the early medieval period, when the Anno Domini calendar era became the prevalent method in Europe for naming years. Events By place Roman Empire * Mesopotamia is partitioned into two Roman provinces divided by the Euphrates, Mesopotamia and Osroene. * Emperor Septimius Severus lays siege to the city-state Hatra in Central-Mesopotamia, but fails to capture the city despite breaching the walls. * Two new legions, I Parthica and III Parthica, are formed as a permanent garrison. China * Battle of Yijing: Chinese warlord Yuan Shao defeats Gongsun Zan. Korea * Geodeung succeeds Suro of Geumgwan Gaya, as king of the Korean kingdom of Gaya (traditional date). By topic Religion * Pope Zephyrinus succeeds Pope Victor I, as the 15th pope. Births Valerian Roman ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Comparison Of Antivirus Software
Legend The term "on-demand scan" refers to the possibility of performing a manual scan (by the user) on the entire computer/device, while "on-access scan" refers to the ability of a product to automatically scan every file at its creation or subsequent modification. The term " CloudAV" refers to the ability of a product to automatically perform scans on the cloud. The term " Email security" refers to the protection of email from viruses and malware, while " Antispam" refers to the protection from spam, scam and phishing attacks. The term " Web protection" usually includes protection from: infected and malicious URLs, phishing websites, online identity (privacy) protection and online banking protection. Many antivirus products use "third-party antivirus engine". This means that the antivirus engine is made by another producer; however, the malware signature and/or other parts of the product may (or may not) be done from the owner of the product itself. Desktop computers and se ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Internet Security
Internet security is a branch of computer security. It encompasses the Internet, browser security, web site security, and network security as it applies to other applications or operating systems as a whole. Its objective is to establish rules and measures to use against attacks over the Internet. The Internet is an inherently insecure channel for information exchange, with high risk of intrusion or fraud, such as phishing, online viruses, trojans, ransomware and worms. Many methods are used to combat these threats, including encryption and ground-up engineering. Threats Emerging Threats Emerging cyberthreats are a result of recent technological breakthroughs. For example, deepfakes use AI to produce audio and video that seems real but are actually fake, which increases the danger of fraud and false information. Furthermore, traditional risks can be automated and strengthened by AI-driven attacks, making them harder to identify and neutralize. Malicious software Maliciou ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Online Banking
Online banking, also known as internet banking, virtual banking, web banking or home banking, is a system that enables customers of a bank or other financial institution to conduct a range of financial transactions through the financial institution's website or mobile app. Since the early 2010s, this has become the most common way that customers access their bank accounts. The online banking system will typically connect to or be part of the core banking system operated by a bank to provide customers access to banking services in addition to or in place of historic branch banking. Online banking significantly reduces the banks' operating cost by reducing reliance on a physical branch network and offers convenience to some customers by lessening the need to visit a bank branch as well as being able to perform banking transactions even when branches are closed, for example outside the conventional banking hours or at weekends and on holidays. Internet banking provides personal an ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cross-site Scripting
Cross-site scripting (XSS) is a type of security vulnerability that can be found in some web applications. XSS attacks enable attackers to inject client-side scripts into web pages viewed by other users. A cross-site scripting vulnerability may be used by attackers to bypass access controls such as the same-origin policy. During the second half of 2007, XSSed documented 11,253 site-specific cross-site vulnerabilities, compared to 2,134 "traditional" vulnerabilities documented by Symantec. XSS effects vary in range from petty nuisance to significant security risk, depending on the sensitivity of the data handled by the vulnerable site and the nature of any security mitigation implemented by the site's owner network. OWASP considers the term cross-site scripting to be a misnomer. It initially was an attack that was used for breaching data across sites, but gradually started to include other forms of data injection attacks. Background Security on the web depends on a variety of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Google Chrome
Google Chrome is a web browser developed by Google. It was first released in 2008 for Microsoft Windows, built with free software components from Apple WebKit and Mozilla Firefox. Versions were later released for Linux, macOS, iOS, iPadOS, and also for Android (operating system), Android, where it is the default browser. The browser is also the main component of ChromeOS, where it serves as the platform for web applications. Most of Chrome's source code comes from Google's free and open-source software project Chromium (web browser), Chromium, but Chrome is licensed as proprietary freeware. WebKit was the original Browser engine, rendering engine, but Google eventually Fork (software development), forked it to create the Blink (browser engine), Blink engine; all Chrome variants except iOS used Blink as of 2017. , StatCounter estimates that Chrome has a 65% worldwide usage share of web browsers, browser market share (after peaking at 72.38% in November 2018) on personal comput ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Potentially Unwanted Program
A potentially unwanted program (PUP) or potentially unwanted application (PUA) is software that a user may perceive as unwanted or unnecessary. It is used as a subjective tagging criterion by security and parental control products. Such software may use an implementation that can compromise privacy or weaken the computer's security. Companies often bundle a wanted program download with a wrapper application and may offer to install an unwanted application, and in some cases without providing a clear opt-out method. Antivirus companies define the software bundled as potentially unwanted programs which can include software that displays Adware, intrusive advertising (adware), or tracks the user's Internet usage to sell information to advertisers (spyware), injects its own advertising into web pages that a user looks at, or uses premium SMS services to rack up charges for the user. A growing number of open-source software projects have expressed dismay at third-party websites wrapping t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
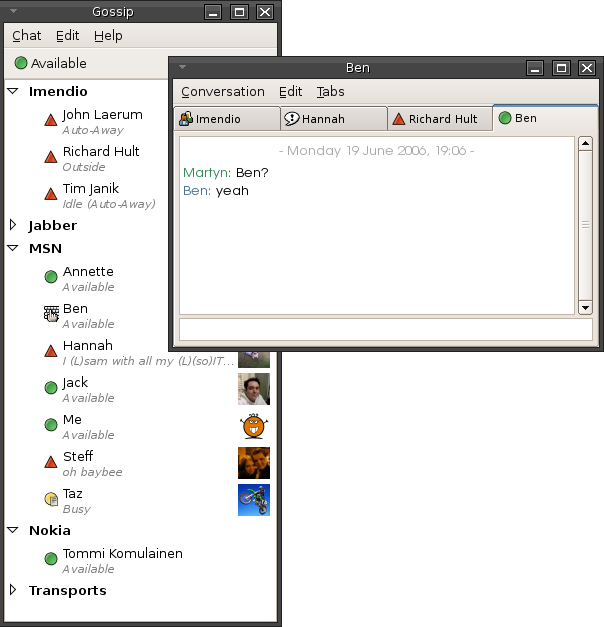
Instant Messenger
Instant messaging (IM) technology is a type of synchronous computer-mediated communication involving the immediate ( real-time) transmission of messages between two or more parties over the Internet or another computer network. Originally involving simple text message exchanges, modern IM applications and services (also called "social messengers", "messaging apps", "chat apps" or "chat clients") tend to also feature the exchange of multimedia, emojis, file transfer, VoIP (voice calling), and video chat capabilities. Instant messaging systems facilitate connections between specified known users (often using a contact list also known as a "buddy list" or "friend list") or in chat rooms, and can be standalone apps or integrated into a wider social media platform, or in a website where it can, for instance, be used for conversational commerce. Originally the term "instant messaging" was distinguished from "text messaging" by being run on a computer network instead of a cellular/ ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Web Analytics
Web analytics is the measurement, data collection, collection, analysis, and reporting of web Data (computing), data to understand and optimize web usage. Web analytics is not just a process for measuring web traffic but can be used as a tool for business and market research and assess and improve website effectiveness. Web analytics applications can also help companies measure the results of traditional print or Broadcasting, broadcast advertising campaigns. It can be used to estimate how traffic to a website changes after launching a new advertising campaign. Web analytics provides information about the number of visitors to a website and the number of page views, or creates user behaviour profiles. It helps gauge traffic and popularity trends, which is useful for market research. Basic steps of the web analytics process Most web analytics processes come down to four essential stages or steps, which are: * data collection, Collection of data: This stage is the collection of th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |