state secrets on:
[Wikipedia]
[Google]
[Amazon]
Classified information is material that a government body deems to be
 ''Top Secret'' is the highest level of classified information. Information is further compartmented so that specific access using a code word after ''top secret'' is a legal way to hide collective and important information. Such material would cause "exceptionally grave damage" to national security if made publicly available. Prior to 1942, the United Kingdom and other members of the British Empire used ''Most Secret'', but this was later changed to match the United States' category name of ''Top Secret'' in order to simplify Allied interoperability.
''The Washington Post'' reported in an investigation entitled "Top Secret America" that, as of 2010, "An estimated 854,000 people ... hold top-secret security clearances" in the United States.
''Top Secret'' is the highest level of classified information. Information is further compartmented so that specific access using a code word after ''top secret'' is a legal way to hide collective and important information. Such material would cause "exceptionally grave damage" to national security if made publicly available. Prior to 1942, the United Kingdom and other members of the British Empire used ''Most Secret'', but this was later changed to match the United States' category name of ''Top Secret'' in order to simplify Allied interoperability.
''The Washington Post'' reported in an investigation entitled "Top Secret America" that, as of 2010, "An estimated 854,000 people ... hold top-secret security clearances" in the United States.
Information Access Law
(top secret), (secret) and (restricted). A top secret () government-issued document may be classified for a period of 25 years, which may be extended up to another 25 years. Thus, no document remains classified for more than 50 years. This is mandated by the 2011 Information Access Law (), a change from the previous rule, under which documents could have their classification time length renewed indefinitely, effectively shuttering state secrets from the public. The 2011 law applies retroactively to existing documents.
 The Criminal Law of the
The Criminal Law of the
State Secrets: China's Legal Labyrinth
'' (2007). Secrets can be classified into three categories: * Top Secret (), defined as "vital state secrets whose disclosure would cause extremely serious harm to state security and national interests" * Highly Secret (), defined as "important state secrets whose disclosure would cause serious harm to state security and national interests" * Secret (), defined as "ordinary state secrets whose disclosure would cause harm to state security and national interests"

 The Swedish classification has been updated due to increased NATO/PfP cooperation. All classified defence documents will now have both a Swedish classification (, , or ), and an English classification (Top Secret, Secret, Confidential, or Restricted). The term , "protected identity", is used in the case of protection of a threatened person, basically implying "secret identity", accessible only to certain members of the police force and explicitly authorised officials.
The Swedish classification has been updated due to increased NATO/PfP cooperation. All classified defence documents will now have both a Swedish classification (, , or ), and an English classification (Top Secret, Secret, Confidential, or Restricted). The term , "protected identity", is used in the case of protection of a threatened person, basically implying "secret identity", accessible only to certain members of the police force and explicitly authorised officials.
 Until 2013, the
Until 2013, the
Defence Vetting Agency
Carries out national security checks in the UK. *
Removing Knowledge
in ''
Los Alamos table of equivalent US and UK classifications
* Maret, Susan. ''On their own terms: A lexicon with an emphasis on information-related terms produced by the U.S. federal government''
FAS, 6th ed., 2016.
Marking Classified National Security Information
ISOO booklet.
The National Security Archive
– a collection of declassified documents acquired through the Freedom of Information Act (United States), FOIA.
Parliament of Montenegro
Law on confidentiality of data. .
Parliament of Serbia
Law on confidentiality of data. .
explaining rules and policies for handling classified information. {{DEFAULTSORT:Classified Information Information sensitivity
sensitive information
Information sensitivity is the control of access to information or knowledge that might result in loss of an advantage or level of security if disclosed to others.
Loss, misuse, modification, or unauthorized access to sensitive information can ...
that must be protected. Access is restricted by law
Law is a set of rules that are created and are enforceable by social or governmental institutions to regulate behavior,Robertson, ''Crimes against humanity'', 90. with its precise definition a matter of longstanding debate. It has been vario ...
or regulation to particular groups of people with the necessary security clearance
A security clearance is a status granted to individuals allowing them access to classified information (state or organizational secrets) or to restricted areas, after completion of a thorough background check. The term "security clearance" is ...
and need to know
The term "need to know", when used by government and other organizations (particularly those related to the military or espionage), describes the restriction of data which is considered very sensitive. Under need-to-know restrictions, even if one ...
, and mishandling of the material can incur criminal penalties.
A formal security clearance is required to view or handle classified material. The clearance process requires a satisfactory background investigation. Documents and other information must be properly marked "by the author" with one of several (hierarchical) levels of sensitivity—e.g. restricted, confidential, secret, and top secret. The choice of level is based on an impact assessment; governments have their own criteria, including how to determine the classification of an information asset and rules on how to protect information classified at each level. This process often includes security clearances for personnel handling the information.
Some corporation
A corporation is an organization—usually a group of people or a company—authorized by the state to act as a single entity (a legal entity recognized by private and public law "born out of statute"; a legal person in legal context) and ...
s and non-government organizations also assign levels of protection to their private information, either from a desire to protect trade secret
Trade secrets are a type of intellectual property that includes formulas, practices, processes, designs, instruments, patterns, or compilations of information that have inherent economic value because they are not generally known or readily ...
s, or because of laws and regulations governing various matters such as personal privacy, sealed legal proceedings and the timing of financial information releases.
With the passage of time much classified information can become less sensitive, and may be declassified and made public. Since the late twentieth century there has been freedom of information legislation
Freedom of information laws allow access by the general public to data held by national governments and, where applicable, by state and local governments. The emergence of freedom of information legislation was a response to increasing dissatisfa ...
in some countries, whereby the public is deemed to have the right to all information that is not considered to be damaging if released. Sometimes documents are released with information still considered confidential obscured ( redacted), as in the adjacent example.
The question exists among some political science and legal experts whether the definition of classified ought to be information that would cause injury to the cause of justice, human rights, etc., rather than information that would cause injury to the national interest; to distinguish when classifying information is in the collective best interest of a just society, or merely the best interest of a society acting unjustly to protect its people, government, or administrative officials from legitimate recourses consistent with a fair and just social contract.
Government classification
The purpose of classification is to protect information. Higher classifications protect information that might endanger national security. Classification formalises what constitutes a "state secret" and accords different levels of protection based on the expected damage the information might cause in the wrong hands. However, classified information is frequently "leaked" to reporters by officials for political purposes. Several U.S. presidents have leaked sensitive information to influence public opinion.Typical classification levels
Although the classification systems vary from country to country, most have levels corresponding to the following British definitions (from the highest level to lowest).Top Secret (TS)
 ''Top Secret'' is the highest level of classified information. Information is further compartmented so that specific access using a code word after ''top secret'' is a legal way to hide collective and important information. Such material would cause "exceptionally grave damage" to national security if made publicly available. Prior to 1942, the United Kingdom and other members of the British Empire used ''Most Secret'', but this was later changed to match the United States' category name of ''Top Secret'' in order to simplify Allied interoperability.
''The Washington Post'' reported in an investigation entitled "Top Secret America" that, as of 2010, "An estimated 854,000 people ... hold top-secret security clearances" in the United States.
''Top Secret'' is the highest level of classified information. Information is further compartmented so that specific access using a code word after ''top secret'' is a legal way to hide collective and important information. Such material would cause "exceptionally grave damage" to national security if made publicly available. Prior to 1942, the United Kingdom and other members of the British Empire used ''Most Secret'', but this was later changed to match the United States' category name of ''Top Secret'' in order to simplify Allied interoperability.
''The Washington Post'' reported in an investigation entitled "Top Secret America" that, as of 2010, "An estimated 854,000 people ... hold top-secret security clearances" in the United States.
Secret
''Secret'' material would cause "serious damage" to national security if it were publicly available. In the United States, operational "Secret" information can be marked with an additional "LimDis", to limit distribution.Confidential
''Confidential'' material would cause "damage" or be prejudicial to national security if publicly available.Restricted
''Restricted'' material would cause "undesirable effects" if publicly available. Some countries do not have such a classification in public sectors, such as commercial industries. Such a level is also known as "''Private'' Information".Official
''Official'' (equivalent to US DOD classification FOUO – For Official Use Only) material forms the generality of government business, public service delivery and commercial activity. This includes a diverse range of information, of varying sensitivities, and with differing consequences resulting from compromise or loss. Official information must be secured against athreat model Threat modeling is a process by which potential threats, such as structural vulnerabilities or the absence of appropriate safeguards, can be identified and enumerated, and countermeasures prioritized. The purpose of threat modeling is to provide de ...
that is broadly similar to that faced by a large private company.
The Official Sensitive classification replaced the Restricted classification in April 2014 in the UK; Official indicates the previously used Unclassified marking.
Unclassified
''Unclassified'' is technically not a classification level, but this is a feature of some classification schemes, used for government documents that do not merit a particular classification or which have been declassified. This is because the information is low-impact, and therefore does not require any special protection, such as vetting of personnel. A plethora of pseudo-classifications exist under this category.Clearance
''Clearance'' is a general classification, that comprises a variety of rules controlling the level of permission required to view some classified information, and how it must be stored, transmitted, and destroyed. Additionally, access is restricted on a "need to know
The term "need to know", when used by government and other organizations (particularly those related to the military or espionage), describes the restriction of data which is considered very sensitive. Under need-to-know restrictions, even if one ...
" basis. Simply possessing a clearance does not automatically authorize the individual to view all material classified at that level or below that level. The individual must present a legitimate "need to know" in addition to the proper level of clearance.
Compartmented information
In addition to the general risk-based classification levels, additional compartmented constraints on access exist, such as ( in the U.S.) Special Intelligence (SI), which protects intelligence sources and methods, No Foreign dissemination (NoForn), which restricts dissemination to U.S. nationals, and Originator Controlled dissemination (OrCon), which ensures that the originator can track possessors of the information. Information in these compartments is usually marked with specific keywords in addition to the classification level. Government information aboutnuclear weapon
A nuclear weapon is an explosive device that derives its destructive force from nuclear reactions, either fission (fission bomb) or a combination of fission and fusion reactions ( thermonuclear bomb), producing a nuclear explosion. Both bom ...
s often has an additional marking to show it contains such information (CNWDI {{Short description, Category of U.S. top secret classified data
Critical Nuclear Weapon Design Information (CNWDI, often pronounced ''SIN-widdy'' or ''SIN-wuh-dee'') is a U.S. Department of Defense (DoD) category of Top Secret Restricted Data or ...
).
International
When a government agency or group shares information between an agency or group of other country's government they will generally employ a special classification scheme that both parties have previously agreed to honour. For example, the marking Atomal, is applied to U.S. Restricted Data or Formerly Restricted Data and United Kingdom Atomic information that has been released to NATO. Atomal information is marked COSMIC Top Secret Atomal (CTSA), NATO Secret Atomal (NSAT), or NATO Confidential Atomal (NCA).NATO classifications
For example, sensitive information shared amongstNATO
The North Atlantic Treaty Organization (NATO, ; french: Organisation du traité de l'Atlantique nord, ), also called the North Atlantic Alliance, is an intergovernmental military alliance between 30 member states – 28 European and two No ...
allies has four levels of security classification; from most to least classified:
# COSMIC Top Secret (CTS)
# NATO Secret (NS)
# NATO Confidential (NC)
# NATO Restricted (NR)
A special case exists with regard to NATO Unclassified (NU) information. Documents with this marking are NATO property (copyright
A copyright is a type of intellectual property that gives its owner the exclusive right to copy, distribute, adapt, display, and perform a creative work, usually for a limited time. The creative work may be in a literary, artistic, educatio ...
) and must not be made public without NATO permission.
COSMIC is an acronym for "Control Of Secret Material in an International Command".
International organizations
* TheEuropean Union
The European Union (EU) is a supranational political and economic union of member states that are located primarily in Europe. The union has a total area of and an estimated total population of about 447million. The EU has often been de ...
has four levels: EU Top Secret, EU Secret, EU Confidential, EU Restricted. (Note that usually the French terms are used.)
**''Très Secret UE''/EU Top Secret: information and material the unauthorised disclosure of which could cause exceptionally grave prejudice to the essential interests of the European Union or of one or more of the Member States;
**''Secret UE''/EU Secret: information and material the unauthorised disclosure of which could seriously harm the essential interests of the European Union or of one or more of the Member States;
**''Confidentiel UE''/EU Confidential: information and material the unauthorised disclosure of which could harm the essential interests of the European Union or of one or more of the Member States;
**''Restreint UE''/EU Restricted: information and material the unauthorised disclosure of which could be disadvantageous to the interests of the European Union or of one or more of the Member States.
* Organisation for Joint Armament Cooperation, a European defence organisation, has three levels of classification: OCCAR Secret, OCCAR Confidential, and OCCAR Restricted.
* ECIPS, the European Centre for Information Policy and Security, has four levels of Security Information, COSMIC (Top Secret), EC-Secret, EC-Confidential and EC-Committees.
By country
Most countries employ some sort of classification system for certain government information. For example, inCanada
Canada is a country in North America. Its ten provinces and three territories extend from the Atlantic Ocean to the Pacific Ocean and northward into the Arctic Ocean, covering over , making it the world's second-largest country by tot ...
, information that the U.S. would classify SBU (Sensitive but Unclassified) is called "protected" and further subcategorised into levels A, B, and C.
Australia
On 19 July 2011, the National Security (NS) classification marking scheme and the Non-National Security (NNS) classification marking scheme in Australia was unified into one structure. As of 2018, the policy detailing howAustralian government
The Australian Government, also known as the Commonwealth Government, is the national government of Australia, a federal parliamentary constitutional monarchy. Like other Westminster-style systems of government, the Australian Government ...
entities handle classified information is defined in the Protective Security Policy Framework (PSPF). The PSPF is published by the Attorney-General's Department and covers security governance, information security
Information security, sometimes shortened to InfoSec, is the practice of protecting information by mitigating information risks. It is part of information risk management. It typically involves preventing or reducing the probability of unauthorize ...
, personal security, and physical security
Physical security describes security measures that are designed to deny unauthorized access to facilities, equipment and resources and to protect personnel and property from damage or harm (such as espionage, theft, or terrorist attacks). Physica ...
. A security classification can be applied to the information itself or an asset that holds information e.g., a USB
Universal Serial Bus (USB) is an industry standard that establishes specifications for cables, connectors and protocols for connection, communication and power supply (interfacing) between computers, peripherals and other computers. A broad ...
or laptop.
The PSPF outlines three categories of sensitive information, Unofficial, Official and Official: Sensitive. Additionally, the PSPF defines three levels of security classified information, Protected, Secret and Top Secret. Although not identical, the definitions of each classification broadly fit the British definitions.
A caveats is a warning that the information has special protections in addition to those indicated by the security classification. Australia has four categories of caveats:
* Codewords
In communication, a code word is an element of a standardized code or protocol. Each code word is assembled in accordance with the specific rules of the code and assigned a unique meaning. Code words are typically used for reasons of reliability, ...
(sensitive compartmented information)
* Foreign government markings
* Special handling instructions
* Releasability caveats
Special handling instructions are used to indicate particular precautions for information handling. They include Exclusive For, Cabinet and National Cabinet. A releasability caveat restricts information based on citizenship
Citizenship is a "relationship between an individual and a state to which the individual owes allegiance and in turn is entitled to its protection".
Each state determines the conditions under which it will recognize persons as its citizens, and ...
. The three in use are: Australian Eyes Only (AUSTEO), Australian Government Access Only (AGAO) and Releasable To (REL).
Additionally, the PSPF outlines Information Management Markers (IMM) as a way for entities to identify information that is subject to non-security related restrictions on access and use. These are: legal privilege, legislative secret, and personal privacy.
Brazil
There are three levels ofdocument classification
Document classification or document categorization is a problem in library science, information science and computer science. The task is to assign a document to one or more classes or categories. This may be done "manually" (or "intellectually") ...
under BraziliaInformation Access Law
(top secret), (secret) and (restricted). A top secret () government-issued document may be classified for a period of 25 years, which may be extended up to another 25 years. Thus, no document remains classified for more than 50 years. This is mandated by the 2011 Information Access Law (), a change from the previous rule, under which documents could have their classification time length renewed indefinitely, effectively shuttering state secrets from the public. The 2011 law applies retroactively to existing documents.
Canada
Background and hierarchy
The government of Canada employs two main types of sensitive information designation: Classified and Protected. The access and protection of both types of information is governed by the '' Security of Information Act'', effective 24 December 2001, replacing the ''Official Secrets Act 1981''. To access the information, a person must have the appropriate security clearance and the need to know. In addition, the caveat "Canadian Eyes Only" is used to restrict access to Classified or Protected information only to Canadian citizens with the appropriate security clearance and need to know.Special operational information
SOI is not a classification of data ''per se''. It is defined under the ''Security of Information Act'', and unauthorised release of such information constitutes a higher breach of trust, with a penalty of up to life imprisonment if the information is shared with a foreign entity or terrorist group. SOIs include: * military operations in respect of a potential, imminent or present armed conflict * the identity of confidential source of information, intelligence or assistance to the Government of Canada * tools used for information gathering or intelligence * the object of a covert investigation, or a covert collection of information or intelligence * the identity of any person who is under covert surveillance * encryption and cryptographic systems * information or intelligence to, or received from, a foreign entity or terrorist groupClassified information
Classified information can be designated ''Top Secret'', ''Secret'' or ''Confidential''. These classifications are only used on matters of national interest. * Top Secret: applies when compromise might reasonably cause exceptionally grave injury to the national interest. The possible impact must be great, immediate and irreparable. * Secret: applies when compromise might reasonably cause serious injury to the national interest. * Confidential: disclosure might reasonably cause injury to the national interest.Protected information
Protected information is not classified. It pertains to any sensitive information that does not relate to national security and cannot be disclosed under the access and privacy legislation because of the potential injury to particular public or private interests. * Protected C (Extremely Sensitive protected information): designates extremely sensitive information, which if compromised, could reasonably be expected to cause extremely grave injury outside the national interest. Examples include bankruptcy, identities of informants in criminal investigations, etc. * Protected B (Particularly Sensitive protected information): designates information that could cause severe injury or damage to the people or group involved if it was released. Examples include medical records, annual personnel performance reviews, income tax returns, etc. * Protected A (Low-Sensitive protected information): designates low sensitivity information that should not be disclosed to the public without authorization and could reasonably be expected to cause injury or embarrassment outside the national interest. Example of Protected A information include employee identification number, pay deposit banking information, etc. Federal Cabinet (Queen's Privy Council for Canada
The 's Privy Council for Canada (french: Conseil privé du Roi pour le Canada),) during the reign of a queen. sometimes called Majesty's Privy Council for Canada or simply the Privy Council (PC), is the full group of personal consultants to the ...
) papers are either protected (e.g., overhead slides prepared to make presentations to Cabinet) or classified (e.g., draft legislation, certain memos).
People's Republic of China
 The Criminal Law of the
The Criminal Law of the People's Republic of China
China, officially the People's Republic of China (PRC), is a country in East Asia. It is the world's most populous country, with a population exceeding 1.4 billion, slightly ahead of India. China spans the equivalent of five time zones and ...
(which is not operative in the special administrative regions of Hong Kong
Hong Kong ( (US) or (UK); , ), officially the Hong Kong Special Administrative Region of the People's Republic of China (abbr. Hong Kong SAR or HKSAR), is a city and special administrative region of China on the eastern Pearl River Delta i ...
and Macau
Macau or Macao (; ; ; ), officially the Macao Special Administrative Region of the People's Republic of China (MSAR), is a city and special administrative region of China in the western Pearl River Delta by the South China Sea. With a p ...
) makes it a crime to release a state secret. Regulation and enforcement is carried out by the National Administration for the Protection of State Secrets
The National Administration of State Secret Protection (NASSP; ) of the People's Republic of China is an institution of the State Council of the People's Republic of China that is responsible for the protection of classified information. The nam ...
.
Under the 1989 "Law on Guarding State Secrets", state secrets are defined as those that concern:
# Major policy decisions on state affairs
# The building of national defence and in the activities of the armed forces
# Diplomatic activities and in activities related to foreign countries and those to be maintained as commitments to foreign countries
# National economic and social development
# Science and technology
# Activities for preserving state security and the investigation of criminal offences
# Any other matters classified as "state secrets" by the national State Secrets BureauTranslation per Human Rights in China, State Secrets: China's Legal Labyrinth
'' (2007). Secrets can be classified into three categories: * Top Secret (), defined as "vital state secrets whose disclosure would cause extremely serious harm to state security and national interests" * Highly Secret (), defined as "important state secrets whose disclosure would cause serious harm to state security and national interests" * Secret (), defined as "ordinary state secrets whose disclosure would cause harm to state security and national interests"
France
In France, classified information is defined by article 413-9 of the Penal Code. The three levels of military classification are * (Very Secret Defence): Information deemed extremely harmful to national defence, and relative to governmental priorities in national defence. No service or organisation can elaborate, process, stock, transfer, display or destroy information or protected supports classified at this level without authorization from the Prime Minister or the national secretary for National Defence. Partial or exhaustive reproduction is strictly forbidden. * (Secret Defence): Information deemed very harmful to national defence. Such information cannot be reproduced without authorisation from the emitting authority, except in exceptional emergencies. * (Confidential Defence): Information deemed potentially harmful to national defence, or that could lead to uncovering some information classified at a higher level of security. Less sensitive information is "protected". The levels are * ("Confidential officers") * ("Confidential non-commissioned officers") * ("restricted information") * ("administrative restricted information") * (unprotected) A further caveat, (reserved France) restricts the document to French citizens (in its entirety or by extracts). This is not a classification level. Declassification of documents can be done by the (CCSDN), an independent authority. Transfer of classified information is done with double envelopes, the outer layer being plastified and numbered, and the inner in strong paper. Reception of the document involves examination of the physical integrity of the container and registration of the document. In foreign countries, the document must be transferred through specialised military mail or diplomatic bag. Transport is done by an authorised conveyor or habilitated person for mail under 20 kg. The letter must bear a seal mentioning "". Once a year, ministers have an inventory of classified information and supports by competent authorities. Once their usage period is expired, documents are transferred to archives, where they are either destroyed (by incineration, crushing, or overvoltage), or stored. In case of unauthorized release of classified information, competent authorities are theMinistry of Interior
An interior ministry (sometimes called a ministry of internal affairs or ministry of home affairs) is a government department that is responsible for internal affairs.
Lists of current ministries of internal affairs
Named "ministry"
* Ministry ...
, the ' ("high civil servant for defence and security") of the relevant ministry, and the General secretary for National Defence. Violation of such secrets is an offence punishable with seven years of imprisonment and a 100,000 euro fine; if the offence is committed by imprudence or negligence, the penalties are three years of imprisonment and a 45,000 euro fine.
Hong Kong
The Security Bureau is responsible for developing policies in regards to the protection and handling of confidential government information. In general, the system used in Hong Kong is very similar to the UK system, developed from the Colonial Hong Kong era. Four classifications exists in Hong Kong, from highest to lowest in sensitivity: * Top Secret () * Secret () * Confidential () ** Temporary Confidential () * Restricted () ** Restricted (staff) () ** Restricted (tender) () ** Restricted (administration) () Restricted documents are not classified ''per se'', but only those who have a need to know will have access to such information, in accordance with the ''Personal Data (Privacy) Ordinance''.New Zealand
New Zealand
New Zealand ( mi, Aotearoa ) is an island country in the southwestern Pacific Ocean. It consists of two main landmasses—the North Island () and the South Island ()—and over 700 smaller islands. It is the sixth-largest island count ...
uses the Restricted classification, which is lower than Confidential. People may be given access to Restricted information on the strength of an authorisation by their Head of department, without being subjected to the background vetting
Vetting is the process of performing a background check on someone before offering them employment, conferring an award, or doing fact-checking prior to making any decision. In addition, in intelligence gathering, assets are vetted to determine th ...
associated with Confidential, Secret and Top Secret clearances. New Zealand's security classifications and the national-harm requirements associated with their use are roughly similar to those of the United States.
In addition to national security classifications there are two additional security classifications, In Confidence and Sensitive, which are used to protect information of a policy and privacy nature. There are also a number of information markings used within ministries and departments of the government, to indicate, for example, that information should not be released outside the originating ministry.
Because of strict privacy requirements around personal information, personnel files are controlled in all parts of the public and private sectors. Information relating to the security vetting of an individual is usually classified at the In Confidence level.
Romania
InRomania
Romania ( ; ro, România ) is a country located at the crossroads of Central, Eastern, and Southeastern Europe. It borders Bulgaria to the south, Ukraine to the north, Hungary to the west, Serbia to the southwest, Moldova to the east, and ...
, classified information is referred to as "state secrets" () and is defined by the Penal Code as "documents and data that manifestly appear to have this status or have been declared or qualified as such by decision of Government". There are three levels of classification—Secret, Top Secret, and Top Secret of Particular Importance. The levels are set by the Romanian Intelligence Service
The Romanian Intelligence Service ( ro, Serviciul Român de Informații, abbreviated SRI) is Romania's main domestic intelligence service. Its role is to gather information relevant to national security and hand it over to relevant institutions, ...
and must be aligned with NATO regulations—in case of conflicting regulations, the latter are applied with priority. Dissemination of classified information to foreign agents or powers is punishable by up to life imprisonment, if such dissemination threatens Romania's national security.

Russia
In theRussian Federation
Russia (, , ), or the Russian Federation, is a transcontinental country spanning Eastern Europe and Northern Asia. It is the largest country in the world, with its internationally recognised territory covering , and encompassing one-eig ...
, a state secret (Государственная тайна) is information protected by the state on its military, foreign policy, economic, intelligence, counterintelligence, operational and investigative and other activities, dissemination of which could harm state security.
Sweden
 The Swedish classification has been updated due to increased NATO/PfP cooperation. All classified defence documents will now have both a Swedish classification (, , or ), and an English classification (Top Secret, Secret, Confidential, or Restricted). The term , "protected identity", is used in the case of protection of a threatened person, basically implying "secret identity", accessible only to certain members of the police force and explicitly authorised officials.
The Swedish classification has been updated due to increased NATO/PfP cooperation. All classified defence documents will now have both a Swedish classification (, , or ), and an English classification (Top Secret, Secret, Confidential, or Restricted). The term , "protected identity", is used in the case of protection of a threatened person, basically implying "secret identity", accessible only to certain members of the police force and explicitly authorised officials.
Switzerland
At the federal level, classified information in Switzerland is assigned one of three levels, which are from lowest to highest: Internal, Confidential, Secret. Respectively, these are, in German, , , ; in French, , , ; in Italian, , , . As in other countries, the choice of classification depends on the potential impact that the unauthorised release of the classified document would have on Switzerland, the federal authorities or the authorities of a foreign government. According to the Ordinance on the Protection of Federal Information, information is classified as Internal if its "disclosure to unauthorised persons may be disadvantageous to national interests." Information classified as Confidential could, if disclosed, compromise "the free formation of opinions and decision-making of the Federal Assembly or the Federal Council," jeopardise national monetary/economic policy, put the population at risk or adversely affect the operations of theSwiss Armed Forces
The Swiss Armed Forces (german: Schweizer Armee, french: Armée suisse, it, Esercito svizzero, rm, Armada svizra; ) operates on land and in the air, serving as the primary armed forces of Switzerland. Under the country's militia system, re ...
. Finally, the unauthorised release of Secret information could seriously compromise the ability of either the Federal Assembly or the Federal Council to function or impede the ability of the Federal Government or the Armed Forces to act.
Turkey
According to the related regulations inTurkey
Turkey ( tr, Türkiye ), officially the Republic of Türkiye ( tr, Türkiye Cumhuriyeti, links=no ), is a transcontinental country located mainly on the Anatolian Peninsula in Western Asia, with a small portion on the Balkan Peninsula in ...
, there are four levels of document classification: (top secret), (secret), (confidential) and (restricted). The fifth is , which means unclassified.
United Kingdom
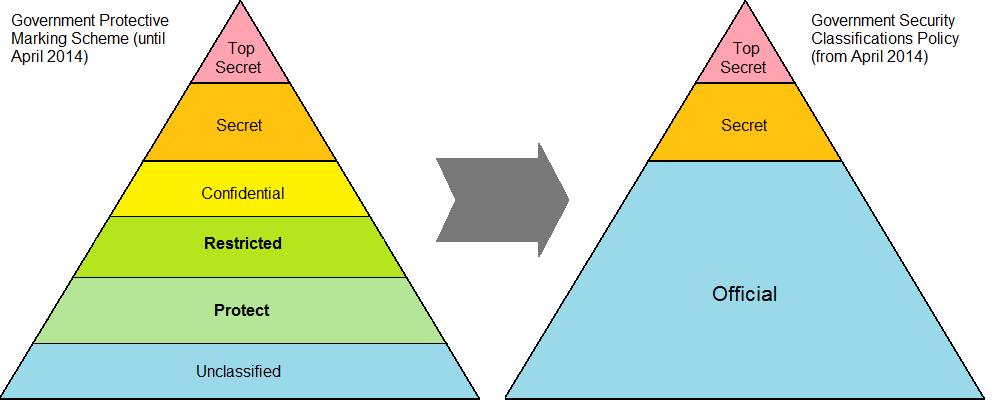
 Until 2013, the
Until 2013, the United Kingdom
The United Kingdom of Great Britain and Northern Ireland, commonly known as the United Kingdom (UK) or Britain, is a country in Europe, off the north-western coast of the European mainland, continental mainland. It comprises England, Scotlan ...
used five levels of classification—from lowest to highest, they were: Protect, Restricted, Confidential, Secret and Top Secret (formerly Most Secret). The Cabinet Office provides guidance on how to protect information, including the security clearances
A security clearance is a status granted to individuals allowing them access to classified information (state or organizational secrets) or to restricted areas, after completion of a thorough background check. The term "security clearance" is ...
required for personnel. Staff may be required to sign to confirm their understanding and acceptance of the Official Secrets Acts 1911 to 1989
An official is someone who holds an office (function or mandate, regardless whether it carries an actual working space with it) in an organization or government and participates in the exercise of authority, (either their own or that of their su ...
, although the Act applies regardless of signature. Protect is not in itself a security protective marking level (such as Restricted or greater), but is used to indicate information which should not be disclosed because, for instance, the document contains tax, national insurance, or other personal information.
Government documents without a classification may be marked as Unclassified or Not Protectively Marked.
This system was replaced by the Government Security Classifications Policy The Government Security Classifications Policy (GSCP) is a system for classifying sensitive government data in the United Kingdom.
GPMS
Historically, the Government Protective Marking Scheme was used by government bodies in the UK; it divides dat ...
, which has a simpler model: Top Secret, Secret, and Official from April 2014. Official Sensitive is a security marking which may be followed by one of three authorised descriptors: Commercial, LocSen (location sensitive) or Personal. Secret and Top Secret may include a caveat such as UK Eyes Only.
Also useful is that scientific discoveries may be classified via the D-Notice
In the United Kingdom, a DSMA-Notice (Defence and Security Media Advisory Notice) is an official request to news editors not to publish or broadcast items on specified subjects for reasons of national security. DSMA-Notices were formerly called a ...
system if they are deemed to have applications relevant to national security. These may later emerge when technology improves so for example the specialised processors and routing engines used in graphics cards are loosely based on top secret military chips designed for code breaking and image processing.
They may or may not have safeguards built in to generate errors when specific tasks are attempted and this is invariably independent of the card's operating system.
United States
The U.S. classification system is currently established underExecutive Order 13526
Executive Order 13526 was issued on December 29, 2009, by United States President Barack Obama.
and has three levels of classification—Confidential, Secret, and Top Secret. The U.S. had a Restricted level during World War II
World War II or the Second World War, often abbreviated as WWII or WW2, was a world war that lasted from 1939 to 1945. It involved the vast majority of the world's countries—including all of the great powers—forming two opposing ...
but no longer does. U.S. regulations state that information received from other countries at the Restricted level should be handled as Confidential. A variety of markings are used for material that is not classified, but whose distribution is limited administratively or by other laws, e.g., For Official Use Only
For Official Use Only (FOUO) is an information security designation used by some governments.
United States
Among U.S. government information, FOUO was primarily used by the U.S. Department of Defense as a handling instruction for Con ...
(FOUO), or Sensitive but Unclassified (SBU). The Atomic Energy Act of 1954 provides for the protection of information related to the design of nuclear weapons. The term "Restricted Data" is used to denote certain nuclear technology. Information about the storage, use or handling of nuclear material or weapons is marked "Formerly Restricted Data". These designations are used in addition to level markings (Confidential, Secret and Top Secret). Information protected by the Atomic Energy Act is protected by law and information classified under the Executive Order is protected by Executive privilege.
The U.S. government insists it is "not appropriate" for a court to question whether any document is legally classified.
In the 1973 trial of Daniel Ellsberg for releasing the Pentagon Papers, the judge did not allow any testimony from Ellsberg, claiming it was "irrelevant", because the assigned classification could not be challenged. The charges against Ellsberg were ultimately dismissed after it was revealed that the government had broken the law in secretly breaking into the office of Ellsberg's psychiatrist and in tapping his telephone without a warrant. Ellsberg insists that the legal situation in the U.S. in 2014 is worse than it was in 1973, and Edward Snowden could not get a fair trial. The State Secrets Protection Act of 2008 might have given judges the authority to review such questions in camera
''In camera'' (; Latin: "in a chamber"). is a legal term that means ''in private''. The same meaning is sometimes expressed in the English equivalent: ''in chambers''. Generally, ''in-camera'' describes court cases, parts of it, or process wh ...
, but the bill was not passed.
When a government agency acquires classified information through covert means, or designates a program as classified, the agency asserts "ownership" of that information and considers any public availability of it to be a violation of their ownership — even if the same information was acquired independently through "parallel reporting" by the press or others. For example, although the CIA drone program has been widely discussed in public since the early 2000s, and reporters personally observed and reported on drone missile strikes, the CIA still considers the very existence of the program to be classified in its entirety, and any public discussion of it technically constitutes exposure of classified information. "Parallel reporting" was an issue in determining what constitutes "classified" information during the Hillary Clinton email controversy
During her tenure as United States Secretary of State, Hillary Clinton drew controversy by using a private email server for official public communications rather than using official State Department email accounts maintained on federal servers ...
when Assistant Secretary of State for Legislative Affairs
The Assistant Secretary of State for Legislative Affairs is the head of the Bureau of Legislative Affairs within the United States Department of State
The United States Department of State (DOS), or State Department, is an executive department ...
Julia Frifield noted, "When policy officials obtain information from open sources, 'think tanks,' experts, foreign government officials, or others, the fact that some of the information may also have been available through intelligence channels does not mean that the information is necessarily classified."
Table of equivalent classification markings in various countries
Corporate classification
Privatecorporation
A corporation is an organization—usually a group of people or a company—authorized by the state to act as a single entity (a legal entity recognized by private and public law "born out of statute"; a legal person in legal context) and ...
s often require written confidentiality agreements
A non-disclosure agreement (NDA) is a legal contract or part of a contract between at least two parties that outlines confidential material, knowledge, or information that the parties wish to share with one another for certain purposes, but wish ...
and conduct background check
A background check is a process a person or company uses to verify that an individual is who they claim to be, and this provides an opportunity to check and confirm the validity of someone's criminal record, education, employment history, and oth ...
s on candidates for sensitive positions. In the U.S., the Employee Polygraph Protection Act prohibits private employers from requiring lie detector tests, but there are a few exceptions. Policies dictating methods for marking and safeguarding company-sensitive information (e.g. "IBM Confidential") are common and some companies have more than one level. Such information is protected under trade secret
Trade secrets are a type of intellectual property that includes formulas, practices, processes, designs, instruments, patterns, or compilations of information that have inherent economic value because they are not generally known or readily ...
laws. New product development teams are often sequestered and forbidden to share information about their efforts with un-cleared fellow employees, the original Apple Macintosh
The Mac (known as Macintosh until 1999) is a family of personal computers designed and marketed by Apple Inc., Apple Inc. Macs are known for their ease of use and minimalist designs, and are popular among students, creative professionals, and ...
project being a famous example. Other activities, such as mergers and financial report preparation generally involve similar restrictions. However, corporate security generally lacks the elaborate hierarchical clearance and sensitivity structures and the harsh criminal sanctions that give government classification systems their particular tone.
Traffic Light Protocol
TheTraffic Light Protocol
The Traffic Light Protocol (TLP) is a system for classifying sensitive information created in the early 2000s by the UK Government's National Infrastructure Security Coordination Centre (NISCC; now Centre for Protection of National Infrastructure ...
was developed by the Group of Eight
The Group of Eight (G8) was an inter-governmental political forum from 1997 until 2014. It had formed from incorporating Russia into the Group of Seven, or G7, and returned to its previous name after Russia left in 2014.
The forum originate ...
countries to enable the sharing of sensitive information between government agencies and corporations. This protocol has now been accepted as a model for trusted information exchange by over 30 other countries. The protocol provides for four "information sharing levels" for the handling of sensitive information.
See also
*Economic Espionage Act of 1996
The Economic Espionage Act of 1996 () was a 6 title Act of Congress dealing with a wide range of issues, including not only industrial espionage (''e.g.'', the theft or misappropriation of a trade secret and the National Information Infrastructu ...
(U.S.)
* Espionage
Espionage, spying, or intelligence gathering is the act of obtaining secret or confidential information (intelligence) from non-disclosed sources or divulging of the same without the permission of the holder of the information for a tangib ...
* Espionage Act of 1917
The Espionage Act of 1917 is a United States federal law enacted on June 15, 1917, shortly after the United States entered World War I. It has been amended numerous times over the years. It was originally found in Title 50 of the U.S. Code (War ...
(U.S.)
* Eyes only
* Five Eyes
The Five Eyes (FVEY) is an intelligence alliance comprising Australia, Canada, New Zealand, the United Kingdom, and the United States. These countries are parties to the multilateral UKUSA Agreement, a treaty for joint cooperation in sig ...
* Golden Shield Project
The Golden Shield Project (), also named National Public Security Work Informational Project, is the Chinese nationwide network-security fundamental constructional project by the e-government of the People's Republic of China. This project i ...
* Government Security Classifications Policy The Government Security Classifications Policy (GSCP) is a system for classifying sensitive government data in the United Kingdom.
GPMS
Historically, the Government Protective Marking Scheme was used by government bodies in the UK; it divides dat ...
(UK)
* Illegal number
An illegal number is a number that represents information which is illegal to possess, utter, propagate, or otherwise transmit in some legal jurisdiction. Any piece of digital information is representable as a number; consequently, if communicat ...
* Information security
Information security, sometimes shortened to InfoSec, is the practice of protecting information by mitigating information risks. It is part of information risk management. It typically involves preventing or reducing the probability of unauthorize ...
* Official Secrets Act (UK, India, Ireland, Malaysia, New Zealand)
* Security of Information Act (Canada)
* State Secrets Privilege (US)
* Wassenaar Arrangement
The Wassenaar Arrangement on Export Controls for Conventional Arms and Dual-Use Goods and Technologies is a multilateral export control regime (MECR) with 42 participating states including many former Comecon (Warsaw Pact) countries established ...
* WikiLeaks
WikiLeaks () is an international non-profit organisation that published news leaks and classified media provided by anonymous sources. Julian Assange, an Australian Internet activist, is generally described as its founder and director and ...
* UKUSA Agreement
The United Kingdom – United States of America Agreement (UKUSA, ) is a multilateral agreement for cooperation in signals intelligence between Australia, Canada, New Zealand, the United Kingdom, and the United States. The alliance of intellig ...
References
External links
Defence Vetting Agency
Carries out national security checks in the UK. *
Peter Galison
Peter Louis Galison (born May 17, 1955, New York) is an American historian and philosopher of science. He is the Joseph Pellegrino University Professor in history of science and physics at Harvard University.
Biography
Galison received his Ph.D. ...
Removing Knowledge
in ''
Critical Inquiry
''Critical Inquiry'' is a quarterly peer-reviewed academic journal in the humanities published by the University of Chicago Press on behalf of the Department of English Language and Literature (University of Chicago). While the topics and historic ...
'' n°31 (Autumn 2004).
* Goldman, Jan, & Susan Maret. ''Intelligence and information policy for national security: Key terms and concepts.'' Rowman & Littlefield, 2016.
* Lerner, Brenda Wilmoth, & K. Lee Lerner, eds. ''Terrorism: Essential primary sources.'' Thomson Gale, 2006.
Los Alamos table of equivalent US and UK classifications
* Maret, Susan. ''On their own terms: A lexicon with an emphasis on information-related terms produced by the U.S. federal government''
FAS, 6th ed., 2016.
Marking Classified National Security Information
ISOO booklet.
The National Security Archive
– a collection of declassified documents acquired through the Freedom of Information Act (United States), FOIA.
Parliament of Montenegro
Law on confidentiality of data. .
Parliament of Serbia
Law on confidentiality of data. .
explaining rules and policies for handling classified information. {{DEFAULTSORT:Classified Information Information sensitivity