|
Government Security Classifications Policy
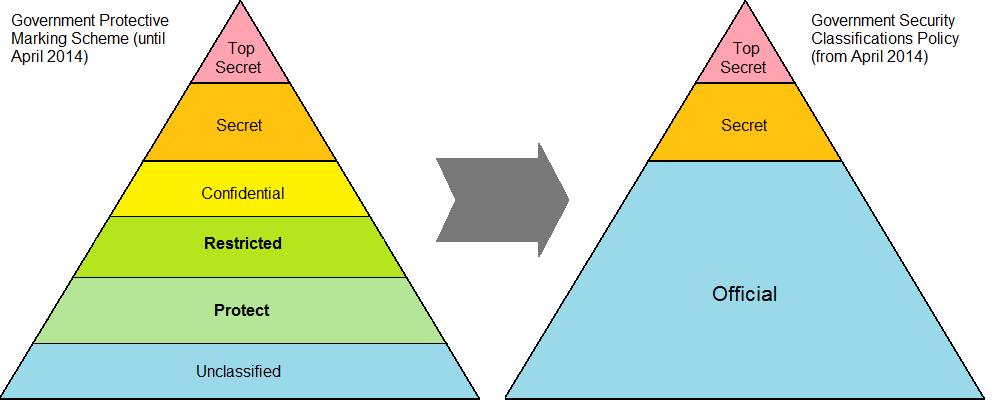
The Government Security Classifications Policy (GSCP) is a system for classifying sensitive government data in the United Kingdom. GPMS Historically, the Government Protective Marking Scheme was used by government bodies in the UK; it divides data into UNCLASSIFIED, PROTECT, RESTRICTED, CONFIDENTIAL, SECRET and TOP SECRET. This system was designed for paper-based records; it is not easily adapted to modern government work and is not widely understood. Current classifications The GSCP uses three levels of classification: OFFICIAL, SECRET and TOP SECRET. This is simpler than the old model and there is no direct relationship between the old and new classifications. "Unclassified" is deliberately omitted from the new model. Government bodies are not expected to automatically remark existing data, so there may be cases where organisations working under the new system still handle some data marked according to the old system. Information Asset Owners continue to be responsible for inf ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Classified Information In The United Kingdom
Classified information in the United Kingdom is a system used to protect information from intentional or inadvertent release to unauthorised readers. The system is organised by the Cabinet Office and is implemented throughout central and local government and critical national infrastructure. The system is also used by private sector bodies that provide services to the public sector. The current classification system, the Government Security Classifications Policy, replaced the old Government Protective Marking Scheme in 2014. Since classifications can last for 100 years many documents are still covered by the old scheme. Policy Policy is set by the Cabinet Office. The Security Policy Framework (SPF) superseded the Manual of Protective Security and contains the primary internal protective security policy and guidance on security and risk management for His Majesty's Government (HMG) Departments and associated bodies. It is the source on which all localised security policies are ba ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
SC Clearance
In the United Kingdom, government policy requires that staff undergo security vetting in order to gain access to government information. The government uses four levels of personnel security controls depending on the level of assurance required. Three of these levels are types of national security vetting clearance. Vetting is intended to assure government bodies that the individual has not been involved in espionage, terrorism, sabotage or actions intended to overthrow or undermine Parliamentary democracy by political, industrial or violent means. It also assures the department that the individual has not been a member of, or associated with, an organisation which has advocated such activities or has demonstrated a lack of reliability through dishonesty, lack of integrity or behaviour. Finally, the process assures the department that the individual will not be subject to pressure or improper influence through past behaviour or personal circumstances. Vetting is usually carrie ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Compartmentalization (information Security)
{{Disambiguation ...
Compartmentalization or compartmentalisation may refer to: * Compartmentalization (biology) * Compartmentalization (engineering) * Compartmentalization (fire protection) * Compartmentalization (information security) * Compartmentalization (psychology) * Compartmentalization of decay in trees Compartmentalization of decay in trees (CODIT) is a concept created by plant pathologist Alex Shigo after studying wood-decay fungus patterns. Theoretical background In keeping with the theory of spontaneous generation, in which living things c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
List X Site
A List X site is a commercial site (i.e. non-government) on UK soil that is approved to hold UK government protectively marked information marked as 'Secret' or above, or international partners information classified ‘Confidential’ or above. This changed from 'Confidential and above' with the introduction of the Government Security Classification Scheme. It is applied to a company's specific site (or facility within that site) and not a company as a whole. The term has been used since the 1930s and is equivalent to facility security clearance (FSC) used in other countries. Locations with this status are those normally involved with defence research and manufacturing that is vital to national security. The complete list of sites is itself classified. The list is administered by Defence Security and Assurance Services (DSAS), part of the Ministry of Defence. A similar scheme, 'List N'', is used for sites relating to civil nuclear research or power generation, and is administer ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cabinet Office
The Cabinet Office is a department of His Majesty's Government responsible for supporting the prime minister and Cabinet. It is composed of various units that support Cabinet committees and which co-ordinate the delivery of government objectives via other departments. As of December 2021, it has over 10,200 staff, most of whom are civil servants, some of whom work in Whitehall. Staff working in the Prime Minister's Office are part of the Cabinet Office. Responsibilities The Cabinet Office's core functions are: * Supporting collective government, helping to ensure the effective development, coordination and implementation of policy; * Supporting the National Security Council and the Joint Intelligence Organisation, coordinating the government's response to crises and managing the UK's cyber security; * Promoting efficiency and reform across government through innovation, transparency, better procurement and project management, by transforming the delivery of services, and impr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Security Policy Framework
The Security Policy Framework (or "SPF") is a set of high-level policies on security, mainly affecting the UK government and its suppliers. The structure has changed over time. Version 11 was published in October 2013; it has 20 "Mandatory Requirements" grouped into four policy areas. Previously the SPF had as many as 70 Mandatory Requirements, which were more detailed, and which were grouped into 7 areas: :1: Governance, Risk Management & Compliance :2: Protective Marking & Asset Control :3: Personnel Security :4: Information Security & Assurance :5: Physical Security :6: Counter-Terrorism :7: Business Continuity Business continuity may be defined as "the capability of an organization to continue the delivery of products or services at pre-defined acceptable levels following a disruptive incident", and business continuity planning (or business continuity a ... These mandatory requirements are a baseline which apply to all UK government departments; higher requirements may apply i ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Security Vetting In The United Kingdom
In the United Kingdom, government policy requires that staff undergo security vetting in order to gain access to government information. The government uses four levels of personnel security controls depending on the level of assurance required. Three of these levels are types of national security vetting clearance. Vetting is intended to assure government bodies that the individual has not been involved in espionage, terrorism, sabotage or actions intended to overthrow or undermine Parliamentary democracy by political, industrial or violent means. It also assures the department that the individual has not been a member of, or associated with, an organisation which has advocated such activities or has demonstrated a lack of reliability through dishonesty, lack of integrity or behaviour. Finally, the process assures the department that the individual will not be subject to pressure or improper influence through past behaviour or personal circumstances. Vetting is usually carrie ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
HMG IA Policy No
HMG may refer to: Businesses and organisations * His Majesty's Government (term), a Commonwealth state's executive **Government of Canada **Government of Gibraltar **Government of New Zealand **Government of the United Kingdom * Holland Media Groep, Dutch TV broadcaster * Human Media Group, American multi-channel network * Hyundai Motor Group, South Korean car manufacturer Science and technology * Heavy machine gun, a class of larger-caliber weapon * High-mobility group, a group of proteins that act on DNA * HMG-CoA β-Hydroxy β-methylglutaryl-CoA (HMG-CoA), also known as 3-hydroxy-3-methylglutaryl coenzyme A, is an intermediate in the mevalonate and ketogenesis pathways. It is formed from acetyl CoA and acetoacetyl CoA by HMG-CoA synthase. The research of ..., a metabolic intermediate biomolecule * HMG Heat and Waterproof Adhesive * Human menopausal gonadotrophin, a fertility drug * '' Human Molecular Genetics'', a scientific journal {{disambiguation ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Information Assurance Standard 1 & 2
HMG Information Assurance Standard No.1, usually abbreviated to IS1, was a security standard applied to government computer systems in the UK. The standard was used to assess – and suggest responses to – technical risks to the confidentiality, integrity and availability of government information. The modelling technique used in the standard was an adaptation of Domain Based Security. In confidentiality terms, IS1 did not apply to information which was not protectively marked, but it may still have been used to assess risks to the integrity and availability of such information. The UK Cabinet Office Security Policy Framework requires that all ICT systems that manage government information or that are interconnected to them are assessed to identify technical risks. IS1 was the standard method for doing this and was mandated by previous versions of the Security Policy Framework, but other methods may now be used. The results of an IS1 assessment, and the responses to risks, wa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Official Secrets Act
An Official Secrets Act (OSA) is legislation that provides for the protection of state secrets and official information, mainly related to national security but in unrevised form (based on the UK Official Secrets Act 1911) can include all information held by government bodies. OSAs are currently in-force in over 40 countries (mostly former British colonies) including Bangladesh, Kenya, Pakistan, Hong Kong, India, Ireland, Myanmar, Uganda, Malaysia, Singapore and the United Kingdom, and have previously existed in Canada and New Zealand. There were earlier English and British precedents, long before the acts enumerated here. As early as the 16th Century, following Francis Drake's circumnavigation, Queen Elizabeth I declared that all written accounts of Drake's voyages were to become the 'Queen's secrets of the Realm'. In addition, Drake and the other participants of his voyages were sworn to their secrecy on the pain of death; the Queen intended to keep Drake's activities away f ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
DV Clearance
In the United Kingdom, government policy requires that staff undergo security vetting in order to gain access to government information. The government uses four levels of personnel security controls depending on the level of assurance required. Three of these levels are types of national security vetting clearance. Vetting is intended to assure government bodies that the individual has not been involved in espionage, terrorism, sabotage or actions intended to overthrow or undermine Parliamentary democracy by political, industrial or violent means. It also assures the department that the individual has not been a member of, or associated with, an organisation which has advocated such activities or has demonstrated a lack of reliability through dishonesty, lack of integrity or behaviour. Finally, the process assures the department that the individual will not be subject to pressure or improper influence through past behaviour or personal circumstances. Vetting is usually carrie ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Freedom Of Information Act 2000
The Freedom of Information Act 2000 (c. 36) is an Act of the Parliament of the United Kingdom that creates a public "right of access" to information held by public authorities. It is the implementation of freedom of information legislation Freedom of information laws allow access by the general public to data held by national governments and, where applicable, by state and local governments. The emergence of freedom of information legislation was a response to increasing dissatisfa ... in the United Kingdom on a national level. Its application is limited in Scotland (which has its own freedom of information legislation) to UK Government offices located in Scotland. The Act implements a manifesto commitment of the Labour Party in the 1997 United Kingdom general election, 1997 general election, developed by David Clark, Baron Clark of Windermere, David Clark as a 1997 White Paper. The final version of the Act was criticised by freedom of information campaigners as a diluted f ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |