|
Sanitization (classified Information)
Sanitization is the process of removing sensitive information from a document or other message (or sometimes encrypting it), so that the document may be distributed to a broader audience. When the intent is secrecy protection, such as in dealing with classified information, sanitization attempts to reduce the document's classification level, possibly yielding an unclassified document. When the intent is privacy protection, it is often called data anonymization. Originally, the term sanitization was applied to printed documents; it has since been extended to apply to computer files and the problem of data remanence. Redaction in its sanitization sense (as distinguished from its other editing sense) is the blacking out or deletion of text in a document or the result of doing so. It is intended to allow the selective disclosure of information in a document while keeping other parts of the document secret. Typically the result is a document that is suitable for publication or fo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Information Sensitivity
Information sensitivity is the control of access to information or knowledge that might result in loss of an advantage or level of security if disclosed to others. Loss, misuse, modification, or unauthorized access to sensitive information can adversely affect the privacy or welfare of an individual, trade secrets of a business or even the security and international relations of a nation depending on the level of sensitivity and nature of the information. Non-sensitive information Public information This refers to information that is already a matter of public record or knowledge. With regard to government and private organizations, access to or release of such information may be requested by any member of the public, and there are often formal processes laid out for how to do so. The accessibility of government-held public records is an important part of government transparency, accountability to its citizens, and the values of democracy. Public records may furthermore refe ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
National Security Agency
The National Security Agency (NSA) is a national-level intelligence agency of the United States Department of Defense, under the authority of the Director of National Intelligence (DNI). The NSA is responsible for global monitoring, collection, and processing of information and data for foreign and domestic intelligence and counterintelligence purposes, specializing in a discipline known as signals intelligence (SIGINT). The NSA is also tasked with the Information assurance, protection of U.S. communications networks and information systems. The NSA relies on a variety of measures to accomplish its mission, the majority of which are clandestine operations, clandestine. The existence of the NSA was not revealed until 1975. The NSA has roughly 32,000 employees. Originating as a unit to decipher coded communications in World War II, it was officially formed as the NSA by President Harry S. Truman in 1952. Between then and the end of the Cold War, it became the largest of the U.S. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Microsoft Word
Microsoft Word is a word processing software developed by Microsoft. It was first released on October 25, 1983, under the name ''Multi-Tool Word'' for Xenix systems. Subsequent versions were later written for several other platforms including: IBM PCs running DOS (1983), Apple Macintosh running the Classic Mac OS (1985), AT&T UNIX PC (1985), Atari ST (1988), OS/2 (1989), Microsoft Windows (1989), SCO Unix (1990) and macOS (2001). Using Wine, versions of Microsoft Word before 2013 can be run on Linux. Commercial versions of Word are licensed as a standalone product or as a component of Microsoft Office suite of software, which can be purchased either with a perpetual license or as part of a Microsoft 365 subscription. History Origins In 1981, Microsoft hired Charles Simonyi, the primary developer of Bravo, the first GUI word processor, which was developed at Xerox PARC. Simonyi started work on a word processor called ''Multi-Tool Word'' and soon hired Rich ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Backup
In information technology, a backup, or data backup is a copy of computer data taken and stored elsewhere so that it may be used to restore the original after a data loss event. The verb form, referring to the process of doing so, is " back up", whereas the noun and adjective form is "backup". Backups can be used to recover data after its loss from data deletion or corruption, or to recover data from an earlier time. Backups provide a simple form of disaster recovery; however not all backup systems are able to reconstitute a computer system or other complex configuration such as a computer cluster, active directory server, or database server. A backup system contains at least one copy of all data considered worth saving. The data storage requirements can be large. An information repository model may be used to provide structure to this storage. There are different types of data storage devices used for copying backups of data that is already in secondary storage onto archi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Undo
Undo is an interaction technique which is implemented in many computer programs. It erases the last change done to the document, reverting it to an older state. In some more advanced programs, such as graphic processing, undo will negate the last command done to the file being edited. With the possibility of undo, users can explore and work without fear of making mistakes, because they can easily be undone. The expectations for undo are easy to understand: to have a predictable functionality, and to include all "undoable" commands. Usually undo is available until the user undoes all executed operations. But there are some actions which are not stored in the undo list, and thus they cannot be undone. For example, ''save file'' is not undoable, but is queued in the list to show that it was executed. Another action which is usually not stored, and thus not undoable, is ''scrolling'' or ''selection''. The opposite of undo is ''redo''. The redo command reverses the undo or advances t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Feature (software Design)
In software, the term feature has several definitions. The Institute of Electrical and Electronics Engineers defines the term ''feature'' in IEEE 829 as " distinguishing characteristic of a software item (e.g., performance, portability, or functionality)."IEEE Std. 829-1998 Feature-rich A piece of software is said to be "feature-rich" when it has many options and functional capabilities available to the user. Progressive disclosure is a technique applied to reduce the potential confusion caused by displaying a wealth of features at once. Sometimes if a piece of software is very feature-rich, that can be seen as a bad thing. The terms feature creep and software bloat can be used to refer to software that is overly feature-rich. See also * Feature-oriented programming * Product family engineering * Software design Software design is the process by which an agent creates a specification of a software artifact intended to accomplish goals, using a set of primitive compo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
United States Department Of Defense
The United States Department of Defense (DoD, USDOD or DOD) is an executive branch department of the federal government charged with coordinating and supervising all agencies and functions of the government directly related to national security and the United States Armed Forces. The DoD is the largest employer in the world, with over 1.34 million active-duty service members (soldiers, marines, sailors, airmen, and guardians) as of June 2022. The DoD also maintains over 778,000 National Guard and reservists, and over 747,000 civilians bringing the total to over 2.87 million employees. Headquartered at the Pentagon in Arlington, Virginia, just outside Washington, D.C., the DoD's stated mission is to provide "the military forces needed to deter war and ensure our nation's security". The Department of Defense is headed by the secretary of defense, a cabinet-level head who reports directly to the president of the United States. Beneath the Department of Defense are t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
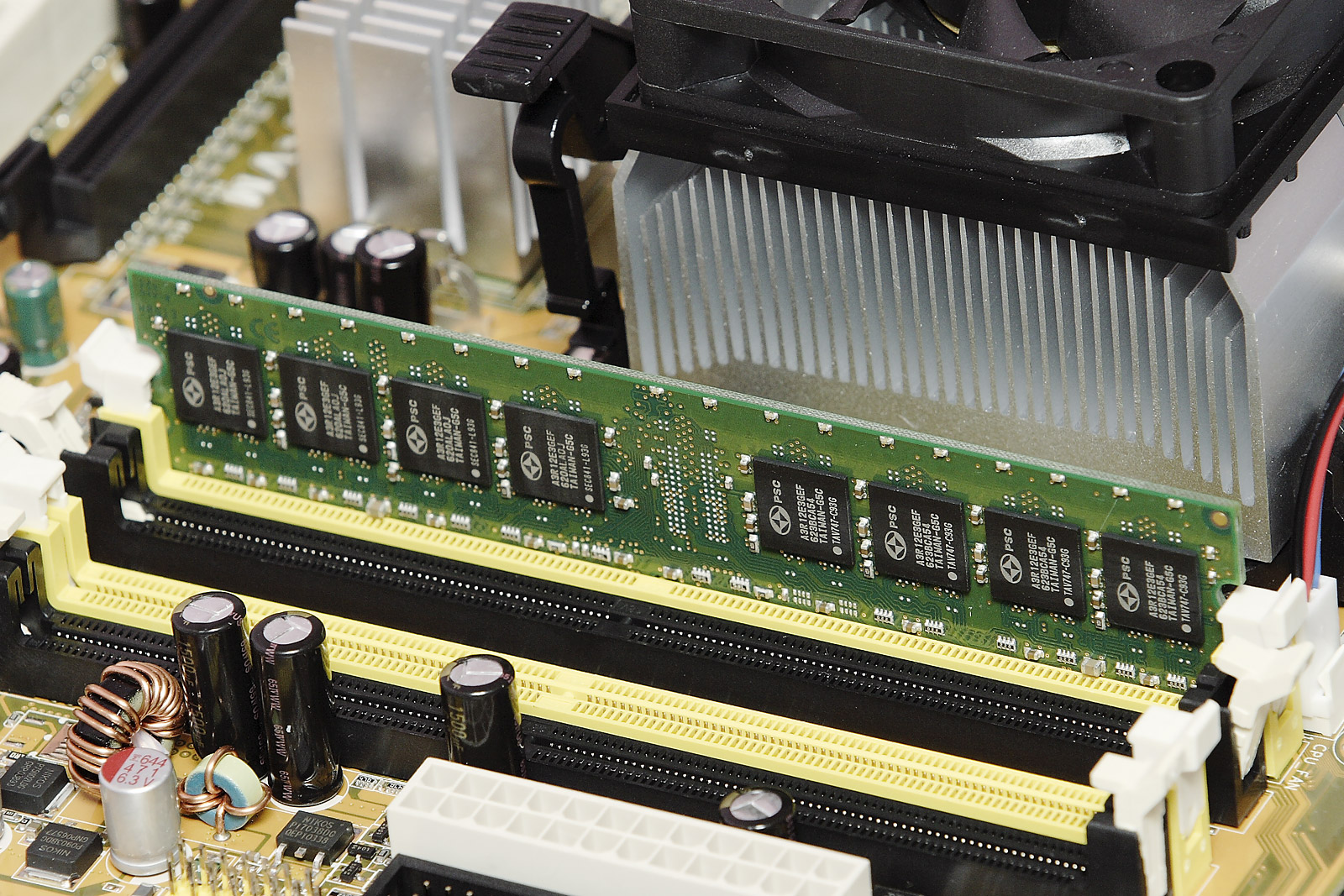
Random Access Memory
Random-access memory (RAM; ) is a form of computer memory that can be read and changed in any order, typically used to store working data and machine code. A random-access memory device allows data items to be read or written in almost the same amount of time irrespective of the physical location of data inside the memory, in contrast with other direct-access data storage media (such as hard disks, CD-RWs, DVD-RWs and the older magnetic tapes and drum memory), where the time required to read and write data items varies significantly depending on their physical locations on the recording medium, due to mechanical limitations such as media rotation speeds and arm movement. RAM contains multiplexing and demultiplexing circuitry, to connect the data lines to the addressed storage for reading or writing the entry. Usually more than one bit of storage is accessed by the same address, and RAM devices often have multiple data lines and are said to be "8-bit" or "16-bit", etc. devices ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Disk Storage
Disk storage (also sometimes called drive storage) is a general category of storage mechanisms where data is recorded by various electronic, magnetic, optical, or mechanical changes to a surface layer of one or more rotating disks. A disk drive is a device implementing such a storage mechanism. Notable types are the hard disk drive (HDD) containing a non-removable disk, the floppy disk drive (FDD) and its removable floppy disk, and various optical disc drives (ODD) and associated optical disc media. (The spelling ''disk'' and ''disc'' are used interchangeably except where trademarks preclude one usage, e.g. the Compact Disc logo. The choice of a particular form is frequently historical, as in IBM's usage of the ''disk'' form beginning in 1956 with the " IBM 350 disk storage unit".) Background Audio information was originally recorded by analog methods (see Sound recording and reproduction). Similarly the first video disc used an analog recording method. In the music ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Storage
Computer data storage is a technology consisting of computer components and recording media that are used to retain digital data. It is a core function and fundamental component of computers. The central processing unit (CPU) of a computer is what manipulates data by performing computations. In practice, almost all computers use a storage hierarchy, which puts fast but expensive and small storage options close to the CPU and slower but less expensive and larger options further away. Generally, the fast volatile technologies (which lose data when off power) are referred to as "memory", while slower persistent technologies are referred to as "storage". Even the first computer designs, Charles Babbage's Analytical Engine and Percy Ludgate's Analytical Machine, clearly distinguished between processing and memory (Babbage stored numbers as rotations of gears, while Ludgate stored numbers as displacements of rods in shuttles). This distinction was extended in the Von Neuman ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
USS Liberty Incident
The USS ''Liberty'' incident was an attack on a United States Navy technical research ship ( spy ship), , by Israeli Air Force jet fighter aircraft and Israeli Navy motor torpedo boats, on 8 June 1967, during the Six-Day War. The combined air and sea attack killed 34 crew members (naval officers, seamen, two marines, and one civilian NSA employee), wounded 171 crew members, and severely damaged the ship. At the time, the ship was in international waters north of the Sinai Peninsula, about northwest from the Egyptian city of Arish. Israel apologized for the attack, saying that the USS ''Liberty'' had been attacked in error after being mistaken for an Egyptian ship. Both the Israeli and U.S. governments conducted inquiries and issued reports that concluded the attack was a mistake due to Israeli confusion about the ship's identity. Others, including survivors of the attack, have rejected these conclusions and maintain that the attack was deliberate. In May 1968, the Isra ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Espionage
Espionage, spying, or intelligence gathering is the act of obtaining secret or confidential information ( intelligence) from non-disclosed sources or divulging of the same without the permission of the holder of the information for a tangible benefit. A person who commits espionage is called an ''espionage agent'' or ''spy''. Any individual or spy ring (a cooperating group of spies), in the service of a government, company, criminal organization, or independent operation, can commit espionage. The practice is clandestine, as it is by definition unwelcome. In some circumstances, it may be a legal tool of law enforcement and in others, it may be illegal and punishable by law. Espionage is often part of an institutional effort by a government or commercial concern. However, the term tends to be associated with state spying on potential or actual enemies for military purposes. Spying involving corporations is known as industrial espionage. One of the most effective ways t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |