SELinux on:
[Wikipedia]
[Google]
[Amazon]
Security-Enhanced Linux (SELinux) is a
preserved
by the Internet Archive Wayback Machine. The scope of their contributions was listed in the page and has been omitted for brevity, but it can be accessed through the archived copy.
 SELinux has been implemented in Android since version 4.3.
Among free community-supported Linux distributions,
SELinux has been implemented in Android since version 4.3.
Among free community-supported Linux distributions,
Security-Enhanced Linux
at the
Linux kernel
The Linux kernel is a Free and open-source software, free and open source Unix-like kernel (operating system), kernel that is used in many computer systems worldwide. The kernel was created by Linus Torvalds in 1991 and was soon adopted as the k ...
security module that provides a mechanism for supporting access control
In physical security and information security, access control (AC) is the action of deciding whether a subject should be granted or denied access to an object (for example, a place or a resource). The act of ''accessing'' may mean consuming ...
security policies, including mandatory access control
In computer security, mandatory access control (MAC) refers to a type of access control by which a secured environment (e.g., an operating system or a database) constrains the ability of a ''subject'' or ''initiator'' to access or modify on an ' ...
s (MAC).
SELinux is a set of kernel modifications and user-space tools that have been added to various Linux distribution
A Linux distribution, often abbreviated as distro, is an operating system that includes the Linux kernel for its kernel functionality. Although the name does not imply product distribution per se, a distro—if distributed on its own—is oft ...
s. Its architecture
Architecture is the art and technique of designing and building, as distinguished from the skills associated with construction. It is both the process and the product of sketching, conceiving, planning, designing, and construction, constructi ...
strives to separate enforcement of security decisions from the security policy, and streamlines the amount of software involved with security policy enforcement. The key concepts underlying SELinux can be traced to several earlier projects by the United States National Security Agency (NSA).
Overview
The NSA Security-enhanced Linux Team describes NSA SELinux asa set of patches to theA Linux kernel integrating SELinux enforces mandatory access control policies that confine user programs and system services, as well as access to files and network resources. Limiting privilege to the minimum required to work reduces or eliminates the ability of these programs and daemons to cause harm if faulty or compromised (for example via buffer overflows or misconfigurations). This confinement mechanism operates independently of the traditional Linux ( discretionary) access control mechanisms. It has no concept of a "root"Linux kernel The Linux kernel is a Free and open-source software, free and open source Unix-like kernel (operating system), kernel that is used in many computer systems worldwide. The kernel was created by Linus Torvalds in 1991 and was soon adopted as the k ...and utilities to provide a strong, flexible, mandatory access control (MAC) architecture into the major subsystems of the kernel. It provides an enhanced mechanism to enforce the separation of information based on confidentiality and integrity requirements, which allows threats of tampering, and bypassing of application security mechanisms, to be addressed and enables the confinement of damage that can be caused by malicious or flawed applications. It includes a set of sample security policy configuration files designed to meet common, general-purpose security goals.
superuser
In computing, the superuser is a special user account used for system administration. Depending on the operating system (OS), the actual name of this account might be root, administrator, admin or supervisor. In some cases, the actual name of the ...
, and does not share the well-known shortcomings of the traditional Linux security mechanisms, such as a dependence on setuid
The Unix and Linux access rights flags setuid and setgid (short for ''set user identity'' and ''set group identity'') allow users to run an executable with the file system permissions of the executable's owner or group respectively and to chang ...
/setgid
The Unix and Linux access rights flags setuid and setgid (short for ''set user identity'' and ''set group identity'') allow users to run an executable with the file system permissions of the executable's owner or group respectively and to change ...
binaries.
The security of an "unmodified" Linux system (a system without SELinux) depends on the correctness of the kernel, of all the privileged applications, and of each of their configurations. A fault in any one of these areas may allow the compromise of the entire system. In contrast, the security of a "modified" system (based on an SELinux kernel) depends primarily on the correctness of the kernel and its security-policy configuration. While problems with the correctness or configuration of applications may allow the limited compromise of individual user programs and system daemons, they do not necessarily pose a threat to the security of other user programs and system daemons or to the security of the system as a whole.
From a purist perspective, SELinux provides a hybrid of concepts and capabilities drawn from mandatory access controls, mandatory integrity controls, role-based access control
In computer systems security, role-based access control (RBAC) or role-based security is an approach to restricting system access to authorized users, and to implementing mandatory access control (MAC) or discretionary access control, discretion ...
(RBAC), and type enforcement architecture. Third-party tools enable one to build a variety of security policies.
History
The earliest work directed toward standardizing an approach providing mandatory and discretionary access controls (MAC and DAC) within a UNIX (more precisely, POSIX) computing environment can be attributed to theNational Security Agency
The National Security Agency (NSA) is an intelligence agency of the United States Department of Defense, under the authority of the director of national intelligence (DNI). The NSA is responsible for global monitoring, collection, and proces ...
's Trusted UNIX (TRUSIX) Working Group, which met from 1987 to 1991 and published one Rainbow Book (#020A), and produced a formal model and associated evaluation evidence prototype (#020B) that was ultimately unpublished.
SELinux was designed to demonstrate the value of mandatory access controls to the Linux community and how such controls could be added to Linux. Originally, the patches that make up SELinux had to be explicitly applied to the Linux kernel source; SELinux was merged into the Linux kernel mainline
The Linux kernel is a Free and open-source software, free and open source Unix-like kernel (operating system), kernel that is used in many computer systems worldwide. The kernel was created by Linus Torvalds in 1991 and was soon adopted as the k ...
in the 2.6 series of the Linux kernel.
The NSA, the original primary developer of SELinux, released the first version to the open source
Open source is source code that is made freely available for possible modification and redistribution. Products include permission to use and view the source code, design documents, or content of the product. The open source model is a decentrali ...
development community under the GNU GPL
The GNU General Public Licenses (GNU GPL or simply GPL) are a series of widely used free software licenses, or ''copyleft'' licenses, that guarantee end users the freedom to run, study, share, or modify the software. The GPL was the first ...
on December 22, 2000. The software was merged into the mainline Linux kernel 2.6.0-test3, released on 8 August 2003. Other significant contributors include Red Hat
Red Hat, Inc. (formerly Red Hat Software, Inc.) is an American software company that provides open source software products to enterprises and is a subsidiary of IBM. Founded in 1993, Red Hat has its corporate headquarters in Raleigh, North ...
, Network Associates, Secure Computing Corporation
Secure Computing Corporation (SCC) was a public company that developed and sold computer security appliances and hosted services to protect users and data. McAfee acquired the company in 2008.
The company also developed filtering systems used b ...
, Tresys Technology, and Trusted Computer Solutions. Experimental ports of the FLASK/TE implementation have been made available via the TrustedBSD
FreeBSD is a free-software Unix-like operating system descended from the Berkeley Software Distribution (BSD). The first version was released in 1993 developed from 386BSD, one of the first fully functional and free Unix clones on affordable h ...
Project for the FreeBSD
FreeBSD is a free-software Unix-like operating system descended from the Berkeley Software Distribution (BSD). The first version was released in 1993 developed from 386BSD, one of the first fully functional and free Unix clones on affordable ...
and Darwin operating systems.
Security-Enhanced Linux implements the Flux Advanced Security Kernel (FLASK). Such a kernel contains architectural components prototyped in the Fluke operating system. These provide general support for enforcing many kinds of mandatory access control policies, including those based on the concepts of type enforcement, role-based access control
In computer systems security, role-based access control (RBAC) or role-based security is an approach to restricting system access to authorized users, and to implementing mandatory access control (MAC) or discretionary access control, discretion ...
, and multilevel security
Multilevel security or multiple levels of security (MLS) is the application of a computer system to process information with incompatible classifications (i.e., at different security levels), permit access by users with different security clearan ...
. FLASK, in turn, was based on DTOS, a Mach-derived Distributed Trusted Operating System, as well as on Trusted Mach, a research project from Trusted Information Systems
Trusted Information Systems, Inc. (TIS), was a computer security research and development company during the 1980s and 1990s, performing computer and communications (information) security research for organizations such as NSA, DARPA, ARL, AFRL ...
that had an influence on the design and implementation of DTOS.
Original and external contributors
A comprehensive list of the original and external contributors to SELinux was hosted at the NSA website until maintenance ceased sometime in 2009. The following list reproduces the original apreserved
by the Internet Archive Wayback Machine. The scope of their contributions was listed in the page and has been omitted for brevity, but it can be accessed through the archived copy.
Users, policies and security contexts
SELinux users and roles do not have to be related to the actual system users and roles. For every current user or process, SELinux assigns a three string context consisting of a username, role, and domain (or type). This system is more flexible than normally required: as a rule, most of the real users share the same SELinux username, and all access control is managed through the third tag, the domain. The circumstances under which a process is allowed into a certain domain must be configured in the policies. The commandruncon allows for the launching of a process into an explicitly specified context (user, role, and domain), but SELinux may deny the transition if it is not approved by the policy.
Files, network ports, and other hardware also have an SELinux context, consisting of a name, role (seldom used), and type. In the case of file systems, mapping between files and the security contexts is called labeling. The labeling is defined in policy files but can also be manually adjusted without changing the policies. Hardware types are quite detailed, for instance, bin_t (all files in the folder /bin) or postgresql_port_t (PostgreSQL port, 5432). The SELinux context for a remote file system can be specified explicitly at mount time.
SELinux adds the -Z switch to the shell commands ls, ps, and some others, allowing the security context of the files or process to be seen.
Typical policy rules consist of explicit permissions, for example, which domains the user must possess to perform certain actions with the given target (read, execute, or, in case of network port, bind or connect), and so on. More complex mappings are also possible, involving roles and security levels.
A typical policy consists of a mapping (labeling) file, a rule file, and an interface file, that define the domain transition. These three files must be compiled together with the SELinux tools to produce a single policy file. The resulting policy file can be loaded into the kernel to make it active. Loading and unloading policies does not require a reboot. The policy files are either hand written or can be generated from the more user friendly SELinux management tool. They are normally tested in permissive mode first, where violations are logged but allowed. The audit2allow tool can be used later to produce additional rules that extend the policy to allow all legitimate activities of the application being confined.
Features
SELinux features include: * Clean separation of policy from enforcement * Well-defined policy interfaces * Support for applications querying the policy and enforcing access control (for example,cron
The cron command-line utility is a job scheduler on Unix-like operating systems. Users who set up and maintain software environments use cron to schedule jobs (commands or shell scripts), also known as cron jobs, to run periodically at fixed t ...
d running jobs in the correct context)
* Independence of specific policies and policy languages
* Independence of specific security-label formats and contents
* Individual labels and controls for kernel objects and services
* Support for policy changes
* Separate measures for protecting system integrity (domain-type) and data confidentiality (multilevel security
Multilevel security or multiple levels of security (MLS) is the application of a computer system to process information with incompatible classifications (i.e., at different security levels), permit access by users with different security clearan ...
)
* Flexible policy
* Controls over process initialization and inheritance, and program execution
* Controls over file systems, directories, files, and open file descriptor
In Unix and Unix-like computer operating systems, a file descriptor (FD, less frequently fildes) is a process-unique identifier (handle) for a file or other input/output resource, such as a pipe or network socket.
File descriptors typically h ...
s
* Controls over sockets, messages, and network interfaces
* Controls over the use of "capabilities"
* Cached information on access-decisions via the ''Access Vector Cache'' (AVC)
* Default-deny policy (anything not explicitly specified in the policy is disallowed)
Adoption
 SELinux has been implemented in Android since version 4.3.
Among free community-supported Linux distributions,
SELinux has been implemented in Android since version 4.3.
Among free community-supported Linux distributions, Fedora
A fedora () is a hat with a soft brim and indented crown.Kilgour, Ruth Edwards (1958). ''A Pageant of Hats Ancient and Modern''. R. M. McBride Company. It is typically creased lengthwise down the crown and "pinched" near the front on both sides ...
was one of the earliest adopters, including support for it by default since Fedora Core 2. Other distributions include support for it such as Debian
Debian () is a free and open-source software, free and open source Linux distribution, developed by the Debian Project, which was established by Ian Murdock in August 1993. Debian is one of the oldest operating systems based on the Linux kerne ...
as of version 9 Stretch release and Ubuntu
Ubuntu ( ) is a Linux distribution based on Debian and composed primarily of free and open-source software. Developed by the British company Canonical (company), Canonical and a community of contributors under a Meritocracy, meritocratic gover ...
as of 8.04 Hardy Heron. As of version 11.1, openSUSE
openSUSE () is a free and open-source software, free and open-source Linux distribution developed by the openSUSE project. It is offered in two main variations: ''Tumbleweed'', an upstream rolling release distribution, and ''Leap'', a stable r ...
contains SELinux "basic enablement". SUSE Linux Enterprise (SLE) 11 features SELinux as a "technology preview".
SELinux is popular in systems based on Linux containers, such as CoreOS Container Linux and rkt. It is useful as an additional security control to help further enforce isolation between deployed containers and their host.
SELinux is available since 2005 as part of Red Hat Enterprise Linux
Red Hat Enterprise Linux (RHEL) is a commercial Linux distribution developed by Red Hat. Red Hat Enterprise Linux is released in server versions for x86-64, Power ISA, ARM64, and IBM Z and a desktop version for x86-64. Fedora Linux and ...
(RHEL) version 4 and all future releases. This presence is also reflected in corresponding versions of derived systems such as CentOS
CentOS (, from Community Enterprise Operating System; also known as CentOS Linux) is a discontinued Linux distribution that provided a free and open-source community-supported computing platform, functionally compatible with its upstream (softw ...
, Scientific Linux
Scientific Linux (SL) is a discontinued Linux distribution produced by Fermilab, CERN, DESY and by ETH Zurich. It is a Free and open-source software, free and open-source operating system based on Red Hat Enterprise Linux.
This product is derive ...
, AlmaLinux
AlmaLinux is a free and open source Linux distribution, developed by the AlmaLinux OS Foundation, a 501(c) organization, to provide a community-supported, Deployment environment, production-grade enterprise operating system that is Binary-code co ...
and Rocky Linux. The supported policy in RHEL4 is targeted policy which aims for maximum ease of use and thus is not as restrictive as it might be. Future versions of RHEL are planned to have more targets in the targeted policy which will mean more restrictive policies. RHEL version 5 introduced multilevel security
Multilevel security or multiple levels of security (MLS) is the application of a computer system to process information with incompatible classifications (i.e., at different security levels), permit access by users with different security clearan ...
(MLS) policy for servers only. Fedora Linux 10 introduced a minimum policy, designed for certain platforms such as low-memory devices and virtual machines
In computing, a virtual machine (VM) is the virtualization or emulator, emulation of a computer system. Virtual machines are based on computer architectures and provide the functionality of a physical computer. Their implementations may involve ...
.
openSUSE Tumbleweed transitioned from AppArmor to SELinux for new installation since 11 February 2025, upcoming SLE/openSUSE Leap 16 will be shipped with SELinux by default as well. openSUSE/SLE adopted RHEL/Fedora policies for its SELinux implementation although with some differences. AppArmor is retained for existing Tumbleweed and SLE/openSUSE Leap 15.x installation (users can manually migrate their existing installation to SELinux). AppArmor is also available as install-time selection for users who prefer it.
Use case scenarios
SELinux can potentially control which activities a system allows each user, process, and daemon, with very precise specifications. It is used to confine daemons such as database engines or web servers that have clearly defined data access and activity rights. This limits potential harm from a confined daemon that becomes compromised. Command-line utilities include:chcon,
restorecon,
restorecond,
runcon,
secon,
fixfiles,
setfiles,
load_policy,
booleans,
getsebool,
setsebool,
togglesebool
setenforce,
semodule,
postfix-nochroot,
check-selinux-installation,
semodule_package,
checkmodule,
selinux-config-enforcing,
selinuxenabled,
and selinux-policy-upgrade
Examples
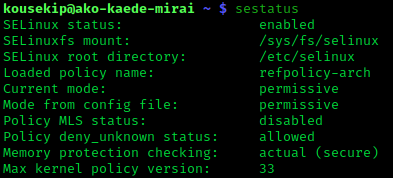
To put SELinux into enforcing mode: :setenforce 1
To query the SELinux status:
:getenforce
Comparison with AppArmor
SELinux represents one of several possible approaches to the problem of restricting the actions that installed software can take. Another popular alternative is called AppArmor and is available onSUSE Linux Enterprise Server
SUSE Linux Enterprise (SLE) is a Linux-based operating system developed by SUSE. It is available in two editions, suffixed with Server (SLES) for servers and mainframes, and Desktop (SLED) for workstations and desktop computers.
Its major ve ...
(SLES), openSUSE
openSUSE () is a free and open-source software, free and open-source Linux distribution developed by the openSUSE project. It is offered in two main variations: ''Tumbleweed'', an upstream rolling release distribution, and ''Leap'', a stable r ...
, and Debian-based platforms. AppArmor was developed as a component to the now-defunct Immunix Linux platform. Because AppArmor and SELinux differ radically from one another, they form distinct alternatives for software control. Whereas SELinux re-invents certain concepts to provide access to a more expressive set of policy choices, AppArmor was designed to be simple by extending the same administrative semantics used for DAC up to the mandatory access control level.
There are several key differences:
* One important difference is that AppArmor identifies file system objects by path name instead of inode. This means that, for example, a file that is inaccessible may become accessible under AppArmor when a hard link is created to it, while SELinux would deny access through the newly created hard link.
** As a result, AppArmor can be said not to be a type enforcement system, as files are not assigned a type; instead, they are merely referenced in a configuration file.
* SELinux and AppArmor also differ significantly in how they are administered and how they integrate into the system.
* Since it endeavors to recreate traditional DAC controls with MAC-level enforcement, AppArmor's set of operations is also considerably smaller than those available under most SELinux implementations. For example, AppArmor's set of operations consist of: read, write, append, execute, lock, and link. Most SELinux implementations will support numbers of operations orders of magnitude more than that. For example, SELinux will usually support those same permissions, but also includes controls for mknod, binding to network sockets, implicit use of POSIX capabilities, loading and unloading kernel modules, various means of accessing shared memory, etc.
* There are no controls in AppArmor for categorically bounding POSIX capabilities. Since the current implementation of capabilities contains no notion of a subject for the operation (only the actor and the operation) it is usually the job of the MAC layer to prevent privileged operations on files outside the actor's enforced realm of control (i.e. "Sandbox"). AppArmor can prevent its own policy from being altered, and prevent file systems from being mounted/unmounted, but does nothing to prevent users from stepping outside their approved realms of control.
** For example, it may be deemed beneficial for help desk employees to change ownership or permissions on certain files even if they don't own them (for example, on a departmental file share). The administrator does not want to give the user(s) root access on the box so they give them CAP_FOWNER or CAP_DAC_OVERRIDE. Under SELinux the administrator (or platform vendor) can configure SELinux to deny all capabilities to otherwise unconfined users, then create confined domains for the employee to be able to transition into after logging in, one that can exercise those capabilities, but only upon files of the appropriate type.
* There is no notion of multilevel security with AppArmor, thus there is no hard BLP or Biba enforcement available..
* AppArmor configuration is done using solely regular flat files. SELinux (by default in most implementations) uses a combination of flat files (used by administrators and developers to write human readable policy before it's compiled) and extended attributes.
* SELinux supports the concept of a "remote policy server" (configurable via /etc/selinux/semanage.conf) as an alternative source for policy configuration. Central management of AppArmor is usually complicated considerably since administrators must decide between configuration deployment tools being run as root (to allow policy updates) or configured manually on each server.
Similar systems and enhancements
Isolation of processes can also be accomplished by mechanisms such asvirtualization
In computing, virtualization (abbreviated v12n) is a series of technologies that allows dividing of physical computing resources into a series of virtual machines, operating systems, processes or containers.
Virtualization began in the 1960s wit ...
; the OLPC project, for example, in its first implementation sandboxed individual applications in lightweight Vservers. Also, the NSA has adopted some of the SELinux concepts in Security-Enhanced Android.
General Dynamics
General Dynamics Corporation (GD) is an American publicly traded aerospace and defense corporation headquartered in Reston, Virginia. As of 2020, it was the fifth largest defense contractor in the world by arms sales and fifth largest in the Unit ...
builds and distributes PitBull Trusted Operating System, a multilevel security
Multilevel security or multiple levels of security (MLS) is the application of a computer system to process information with incompatible classifications (i.e., at different security levels), permit access by users with different security clearan ...
(MLS) enhancement for Red Hat Enterprise Linux
Red Hat Enterprise Linux (RHEL) is a commercial Linux distribution developed by Red Hat. Red Hat Enterprise Linux is released in server versions for x86-64, Power ISA, ARM64, and IBM Z and a desktop version for x86-64. Fedora Linux and ...
.
Multi-Category Security (MCS) is an enhancement to SELinux for Red Hat Enterprise Linux
Red Hat Enterprise Linux (RHEL) is a commercial Linux distribution developed by Red Hat. Red Hat Enterprise Linux is released in server versions for x86-64, Power ISA, ARM64, and IBM Z and a desktop version for x86-64. Fedora Linux and ...
that allows users to label files with categories, in order to further restrict access through discretionary access control and type enforcement. Categories provide additional compartments within sensitivity levels used by multilevel security
Multilevel security or multiple levels of security (MLS) is the application of a computer system to process information with incompatible classifications (i.e., at different security levels), permit access by users with different security clearan ...
(MLS).
See also
* * * * * * * * * *References
External links
*Security-Enhanced Linux
at the
National Security Agency
The National Security Agency (NSA) is an intelligence agency of the United States Department of Defense, under the authority of the director of national intelligence (DNI). The NSA is responsible for global monitoring, collection, and proces ...
in the Internet Archive
The Internet Archive is an American 501(c)(3) organization, non-profit organization founded in 1996 by Brewster Kahle that runs a digital library website, archive.org. It provides free access to collections of digitized media including web ...
*
*
{{Authority control
Linux kernel features
Linux security software
National Security Agency
Red Hat software
Unix file system technology
Free software programmed in C