|
Trusted Information Systems
Trusted Information Systems (TIS) was a computer security research and development company during the 1980s and 1990s, performing computer and communications (information) security research for organizations such as NSA, DARPA, ARL, AFRL, SPAWAR, and others. History TIS was founded in 1983 by NSA veteran Steve Walker, and at various times employed notable information security experts including David Elliott Bell, Martha BranstadJohn Pescatore , Marcus Ranum, Wei Xu, John Williams Steve Lipner and |
McAfee
McAfee Corp. ( ), formerly known as McAfee Associates, Inc. from 1987 to 1997 and 2004 to 2014, Network Associates Inc. from 1997 to 2004, and Intel Security Group from 2014 to 2017, is an American global computer security software company headquartered in San Jose, California. The company was purchased by Intel in February 2011, and became part of the Intel Security division. In 2017, Intel had a strategic deal with TPG Capital and converted Intel Security into a joint venture between both companies called McAfee. Thoma Bravo took a minority stake in the new company, and Intel retained a 49% stake. The owners took McAfee public on the NASDAQ in 2020, and in 2022 an investor group led by Advent International Corporation took it private again. History 1987–1999 The company was founded in 1987 as McAfee Associates, named for its founder John McAfee, who resigned from the company in 1994. McAfee was incorporated in the state of Delaware in 1992. In 1993, McAfee stepped d ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Marcus J
Marcus, Markus, Márkus or Mărcuș may refer to: * Marcus (name), a masculine given name * Marcus (praenomen), a Roman personal name Places * Marcus, a Asteroid belt, main belt asteroid, also known as List of minor planets: 369001–370000#088, (369088) Marcus 2008 GG44 * Mărcuş, a village in Dobârlău Commune, Covasna County, Romania * Marcus, Illinois, an unincorporated community * Marcus, Iowa, a city * Marcus, South Dakota, an unincorporated community * Marcus, Washington, a town * Marcus Island, Japan, also known as Minami-Tori-shima * Mărcuș River, Romania * Marcus Township, Cherokee County, Iowa Other uses * Markus, a beetle genus in family Cantharidae * Marcus (album), ''Marcus'' (album), 2008 album by Marcus Miller * Marcus (comedian), finalist on ''Last Comic Standing'' season 6 * Marcus Amphitheater, Milwaukee, Wisconsin * Marcus Center, Milwaukee, Wisconsin * Marcus & Co., American jewelry retailer * Marcus by Goldman Sachs, an online bank * USS Marcus (DD-321), U ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Domain Name System
The Domain Name System (DNS) is a hierarchical and distributed naming system for computers, services, and other resources in the Internet or other Internet Protocol (IP) networks. It associates various information with domain names assigned to each of the associated entities. Most prominently, it translates readily memorized domain names to the numerical IP addresses needed for locating and identifying computer services and devices with the underlying network protocols. The Domain Name System has been an essential component of the functionality of the Internet since 1985. The Domain Name System delegates the responsibility of assigning domain names and mapping those names to Internet resources by designating authoritative name servers for each domain. Network administrators may delegate authority over sub-domains of their allocated name space to other name servers. This mechanism provides distributed and fault-tolerant service and was designed to avoid a single large ce ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Simple Network Management Protocol
Simple Network Management Protocol (SNMP) is an Internet Standard protocol for collecting and organizing information about managed devices on IP networks and for modifying that information to change device behaviour. Devices that typically support SNMP include cable modems, routers, switches, servers, workstations, printers, and more. SNMP is widely used in network management for network monitoring. SNMP exposes management data in the form of variables on the managed systems organized in a management information base (MIB) which describe the system status and configuration. These variables can then be remotely queried (and, in some circumstances, manipulated) by managing applications. Three significant versions of SNMP have been developed and deployed. SNMPv1 is the original version of the protocol. More recent versions, SNMPv2c and SNMPv3, feature improvements in performance, flexibility and security. SNMP is a component of the Internet Protocol Suite as defined by the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
S/MIME
S/MIME (Secure/Multipurpose Internet Mail Extensions) is a standard for public key encryption and signing of MIME data. S/MIME is on an IETF standards track and defined in a number of documents, most importantly . It was originally developed by RSA Data Security and the original specification used the IETF MIME specification with the de facto industry standard PKCS#7 secure message format. Change control to S/MIME has since been vested in the IETF and the specification is now layered on Cryptographic Message Syntax (CMS), an IETF specification that is identical in most respects with PKCS #7. S/MIME functionality is built into the majority of modern email software and interoperates between them. Since it is built on CMS, MIME can also hold an advanced digital signature. Function S/MIME provides the following cryptographic security services for electronic messaging applications: * Authentication * Message integrity * Non-repudiation of origin (using digital signatures) * Pr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Gauntlet Firewall
Gauntlet or the gauntlet may refer to: Common uses *Gauntlet (glove), protective gloves used as a form of armor *Running the gauntlet, a form of physical punishment Arts, entertainment, and media Fictional characters * Gauntlet (comics), a Marvel Comics superhero *Gauntlet (Inhuman), a Marvel Comics supervillain Games * ''Gauntlet'' (1985 video game), a 1985 four-player arcade game with many followups: **'' Gauntlet II'', a 1986 arcade sequel **'' Gauntlet: The Third Encounter'', a 1990 game for the Atari Lynx **'' Gauntlet III: The Final Quest'', a 1991 home computer game **'' Gauntlet IV'', a 1994 video game for the Sega Genesis **''Gauntlet Legends'', a 1998 arcade game **''Gauntlet Dark Legacy'', a 2000 arcade game **'' Gauntlet: Seven Sorrows'', a 2005 video game ** ''Gauntlet'' (2014 video game), developed by Arrowhead Game studios ** ''Gauntlet'' (Nintendo DS), an unreleased remake of the first game * ''Gauntlet'' (Donald R. Lebeau video game), a 1984 shoot 'em up game for ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
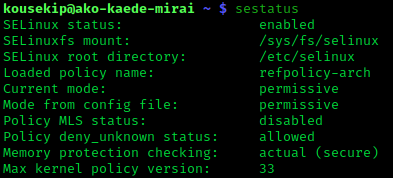
SELinux
Security-Enhanced Linux (SELinux) is a Linux kernel security module that provides a mechanism for supporting access control security policies, including mandatory access controls (MAC). SELinux is a set of kernel modifications and user-space tools that have been added to various Linux distributions. Its architecture strives to separate enforcement of security decisions from the security policy, and streamlines the amount of software involved with security policy enforcement. The key concepts underlying SELinux can be traced to several earlier projects by the United States National Security Agency (NSA). Overview The NSA Security-enhanced Linux Team describes NSA SELinux as a set of patches to the Linux kernel and utilities to provide a strong, flexible, mandatory access control (MAC) architecture into the major subsystems of the kernel. It provides an enhanced mechanism to enforce the separation of information based on confidentiality and integrity requirements, which allow ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Trusted Mach
Trust is the willingness of one party (the trustor) to become vulnerable to another party (the trustee) on the presumption that the trustee will act in ways that benefit the trustor. In addition, the trustor does not have control over the actions of the trustee. Scholars distinguish between generalized trust (also known as social trust), which is the extension of trust to a relatively large circle of unfamiliar others, and particularized trust, which is contingent on a specific situation or a specific relationship. As the trustor is uncertain about the outcome of the trustee's actions, the trustor can only develop and evaluate expectations. Such expectations are formed with a view to the motivations of the trustee, dependent on their characteristics, the situation, and their interaction. The uncertainty stems from the risk of failure or harm to the trustor if the trustee does not behave as desired. In the social sciences, the subtleties of trust are a subject of ongoing resea ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Operating System
An operating system (OS) is system software that manages computer hardware, software resources, and provides common daemon (computing), services for computer programs. Time-sharing operating systems scheduler (computing), schedule tasks for efficient use of the system and may also include accounting software for cost allocation of Scheduling (computing), processor time, mass storage, printing, and other resources. For hardware functions such as input and output and memory allocation, the operating system acts as an intermediary between programs and the computer hardware, although the application code is usually executed directly by the hardware and frequently makes system calls to an OS function or is interrupted by it. Operating systems are found on many devices that contain a computer from cellular phones and video game consoles to web servers and supercomputers. The dominant general-purpose personal computer operating system is Microsoft Windows with a market share of aroun ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Security-evaluated Operating System
In computing, security-evaluated operating systems have achieved certification from an external security-auditing organization, the most popular evaluations are Common Criteria (CC) and FIPS 140-2. Oracle Solaris Trusted Solaris 8 was a security-focused version of the Solaris Unix operating system. Aimed primarily at the government computing sector, Trusted Solaris adds detailed auditing of all tasks, pluggable authentication, mandatory access control, additional physical authentication devices, and fine-grained access control(FGAC). Versions of Trusted Solaris through version 8 are Common Criteria certified. Trusted Solaris Version 8 received the EAL 4 certification level augmented by a number of protection profiles. BAE Systems' STOP BAE Systems' STOP version 6.0.E received an EAL4+ in April 2004 and the 6.1.E version received an EAL5+ certification in March 2005. STOP version 6.4 U4 received an EAL5+ certification in July 2008. Versions of STOP prior to STOP 6 ha ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Xenix
Xenix is a discontinued version of the Unix operating system for various microcomputer platforms, licensed by Microsoft from AT&T Corporation in the late 1970s. The Santa Cruz Operation (SCO) later acquired exclusive rights to the software, and eventually replaced it with SCO UNIX (now known as SCO OpenServer). In the mid-to-late 1980s, Xenix was the most common Unix variant, measured according to the number of machines on which it was installed. Microsoft chairman Bill Gates said at Unix Expo in 1996 that, for a long time, Microsoft had the highest-volume AT&T Unix license. History Bell Labs, the developer of Unix, was part of the regulated Bell System and could not sell Unix directly to most end users (academic and research institutions excepted); it could, however, license it to software vendors who would then resell it to end users (or their own resellers), combined with their own added features. Microsoft, which expected that Unix would be its operating system of the fut ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |