Internet censorship circumvention on:
[Wikipedia]
[Google]
[Amazon]
Internet censorship circumvention is the use of various methods and tools to bypass
, Dutton, William H.; Dopatka, Anna; Law, Ginette; Nash, Victoria, Division for Freedom of Expression, Democracy and Peace, United Nations Educational, Scientific and Cultural Organization (UNESCO), Paris, 2011, 103 pp., and risks from breaking the law.
Main Page
and there is also a mobile-formatted version a
Wikipedia, the free encyclopedia
If DNS resolution is disrupted but the site is not blocked in other ways, it may be possible to access a site directly through its
, The Citizen Lab, University of Toronto, September 2007
Military Thumb Drives Expose Larger Problem
''MSNBC'' Retrieved on 25 January 2007. One example of a widely adopted sneakernet network is
Casting A Wider Net: Lessons Learned in Delivering BBC Content on the Censored Internet
', Ronald Deibert, Canada Centre for Global Security Studies and Citizen Lab, Munk School of Global Affairs, University of Toronto, 11 October 2011
Censorship Wikia
an anti-censorship site that catalogs past and present censored works, using verifiable sources, and a forum to discuss organizing against and circumventing censorship
"Circumvention Tool Evaluation: 2011"
Hal Roberts, Ethan Zuckerman, and John Palfrey, Berkman Centre for Internet & Society, 18 August 2011
"Circumvention Tool Usage Report: 2010"
Hal Roberts, Ethan Zuckerman, Jillian York, Robert Faris, and John Palfrey, Berkman Centre for Internet & Society, 14 October 2010
Digital Security and Privacy for Human Rights Defenders
by Dmitri Vitaliev, Published by Front Line - The International Foundation for the Protection of Human Rights Defenders
"Digital Tools to Curb Snooping"
''New York Times'', 17 July 2013
Methods and Scripts useful for evading censorship through DNS filtering *
How to Bypass Internet Censorship
', also known by the titles: ''Bypassing Internet Censorship'' or ''Circumvention Tools'', a
ArabicBurmeseChinesePersianRussianSpanish
an
Vietnamese
"Leaping over the Firewall: A Review of Censorship Circumvention Tools"
, by Cormac Callanan (Ireland), Hein Dries-Ziekenheiner (Netherlands), Alberto Escudero-Pascual (Sweden), and Robert Guerra (Canada), Freedom House, April 2011
"Media Freedom Internet Cookbook"
by the
"Online Survival Kit"
We Fight Censorship project of Reporters Without Borders
Free Haven Project, accessed 16 September 2011 {{DEFAULTSORT:Internet Censorship Circumvention Internet security Content-control software Internet censorship Internet privacy Circumvention
internet censorship
Internet censorship is the legal control or suppression of what can be accessed, published, or viewed on the Internet. Censorship is most often applied to specific internet domains (such as Wikipedia.org) but exceptionally may extend to all Inte ...
.
Various techniques and methods are used to bypass Internet censorship, and have differing ease of use, speed, security, and risks. Some methods, such as the use of alternate DNS servers, evade blocking by using an alternate address or address lookup system to access the site. Techniques using website mirrors or archive site
In web archiving, an archive site is a website that stores information on webpages from the past for anyone to view.
Common techniques
Two common techniques for archiving websites are using a web crawler or soliciting user submissions:
# Using ...
s rely on other copies of the site being available at different locations. Additionally, there are solutions that rely on gaining access to an Internet connection that is not subject to filtering, often in a different jurisdiction not subject to the same censorship laws, using technologies such as proxying, virtual private networks
A virtual private network (VPN) extends a private network across a public network and enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network. The be ...
, or anonymization networks.
An arms race
An arms race occurs when two or more groups compete in military superiority. It consists of a competition between two or more states to have superior armed forces; a competition concerning production of weapons, the growth of a military, and t ...
has developed between censors and developers of circumvention software, resulting in more sophisticated blocking techniques by censors and the development of harder-to-detect tools by researchers. Estimates of adoption of circumvention tools vary substantially and are disputed. Barriers to adoption can include usability issues, difficulty finding reliable and trustworthy information about circumvention, lack of desire to access censored content,''Freedom of connection, freedom of expression: the changing legal and regulatory ecology shaping the Internet'', Dutton, William H.; Dopatka, Anna; Law, Ginette; Nash, Victoria, Division for Freedom of Expression, Democracy and Peace, United Nations Educational, Scientific and Cultural Organization (UNESCO), Paris, 2011, 103 pp., and risks from breaking the law.
Circumvention methods
There are many methods available that may allow the circumvention of Internet filtering, which can widely vary in terms of implementation difficulty, effectiveness, and resistance to detection.Alternate names and addresses
Filters may block specific domain names, either usingDNS hijacking
DNS hijacking, DNS poisoning, or DNS redirection is the practice of subverting the resolution of Domain Name System (DNS) queries. This can be achieved by malware that overrides a computer's TCP/IP configuration to point at a rogue DNS server unde ...
or URL filtering. Sites are sometimes accessible through alternate names and addresses that may not be blocked.
Some websites may offer the same content at multiple pages or domain names. For example, the English Wikipedia is available aMain Page
and there is also a mobile-formatted version a
Wikipedia, the free encyclopedia
If DNS resolution is disrupted but the site is not blocked in other ways, it may be possible to access a site directly through its
IP address
An Internet Protocol address (IP address) is a numerical label such as that is connected to a computer network that uses the Internet Protocol for communication.. Updated by . An IP address serves two main functions: network interface ident ...
or modifying the host file
The computer file hosts is an operating system file that maps hostnames to IP addresses. It is a plain text file. Originally a file named HOSTS.TXT was manually maintained and made available via file sharing by Stanford Research Institute for the ...
. Using alternative DNS servers, or public recursive name server
A public recursive name server (also called public DNS resolver) is a name server service that networked computers may use to query the Domain Name System (DNS), the decentralized Internet naming system, in place of (or in addition to) name servers ...
s (especially when used through an encrypted DNS client), may bypass DNS-based blocking.
Censors may block specific IP addresses. Depending on how the filtering is implemented, it may be possible to use different forms of the IP address, such as by specifying the address in a different base. For example, the following URLs all access the same site, although not all browsers will recognize all forms: http://1.1.1.1/ (dotted decimal), http://16843009/ (decimal), http://0001.0001.0001.0001/ (dotted octal), http://0x01010101/ (hexadecimal), and http://0x01.0x01.0x01.0x01/ (dotted hexadecimal).
Blockchain technology is an attempt to decentralize namespaces outside the control of a single entity. Decentralized namespaces enable censorship resistant domains. The BitDNS discussion began in 2010 with a desire to achieve names that are decentralized, secure and human readable.
Mirrors, caches, and copies
Cached pages: Some search engines keep copies of previously indexed webpages, or cached pages, which are often hosted by search engines and may not be blocked. For example,Google
Google LLC () is an American multinational technology company focusing on search engine technology, online advertising, cloud computing, computer software, quantum computing, e-commerce, artificial intelligence, and consumer electronics. ...
allows the retrieval of cached pages by entering "cache:''some-url''" as a search request.
Mirror and archive sites: Copies of web sites or pages may be available at mirror
A mirror or looking glass is an object that Reflection (physics), reflects an image. Light that bounces off a mirror will show an image of whatever is in front of it, when focused through the lens of the eye or a camera. Mirrors reverse the ...
or archive
An archive is an accumulation of historical records or materials – in any medium – or the physical facility in which they are located.
Archives contain primary source documents that have accumulated over the course of an individual or ...
sites such as the Internet Archive's Wayback Machine
The Wayback Machine is a digital archive of the World Wide Web founded by the Internet Archive, a nonprofit based in San Francisco, California. Created in 1996 and launched to the public in 2001, it allows the user to go "back in time" and see ...
or Archive.today
archive.today (or archive.is) is a web archiving site, founded in 2012, that saves snapshots on demand, and has support for JavaScript-heavy sites such as Google Maps and progressive web apps such as Twitter. archive.today records two snaps ...
. The Docker Registry Image Repository is a centralized storage, application stateless, and node
In general, a node is a localized swelling (a "knot") or a point of intersection (a vertex).
Node may refer to:
In mathematics
*Vertex (graph theory), a vertex in a mathematical graph
*Vertex (geometry), a point where two or more curves, lines, ...
scalable HTTP
The Hypertext Transfer Protocol (HTTP) is an application layer protocol in the Internet protocol suite model for distributed, collaborative, hypermedia information systems. HTTP is the foundation of data communication for the World Wide Web, ...
public service and has a performance bottleneck in the multinational upload and download scenario. Decentralized Docker Registry avoids this centralization drawback. DDR uses a network-structured P2P network
Peer-to-peer (P2P) computing or networking is a distributed application architecture that partitions tasks or workloads between peers. Peers are equally privileged, equipotent participants in the network. They are said to form a peer-to-peer n ...
to store and query mirror manifest file A manifest file in computing is a file containing metadata for a group of accompanying files that are part of a set or coherent unit. For example, the files of a computer program may have a manifest describing the name, version number, license and t ...
and blob routing, while each node serves as an independent mirror repository to provide mirror upload and download for the entire network.
RSS aggregators: RSS
RSS ( RDF Site Summary or Really Simple Syndication) is a web feed that allows users and applications to access updates to websites in a standardized, computer-readable format. Subscribing to RSS feeds can allow a user to keep track of many di ...
aggregators such as Feedly
Feedly is a news aggregator application for various web browsers and mobile devices running iOS and Android. It is also available as a cloud-based service. It compiles news feeds from a variety of online sources for the user to customize and sha ...
may be able to receive and pass on RSS feeds that are blocked when accessed directly.''Everyone's Guide to By-passing Internet Censorship'', The Citizen Lab, University of Toronto, September 2007
Alternative platforms
Decentralized Hosting: Content creators may publish to an alternative platform which is willing to host ones content.Napster
Napster was a peer-to-peer file sharing application. It originally launched on June 1, 1999, with an emphasis on digital audio file distribution. Audio songs shared on the service were typically encoded in the MP3 format. It was founded by Shawn ...
was the first peer to peer platform but got technically closed due to centralized bootstrapping vulnerabilities. Gnutella
Gnutella is a peer-to-peer network protocol. Founded in 2000, it was the first decentralized peer-to-peer network of its kind, leading to other, later networks adopting the model.
In June 2005, Gnutella's population was 1.81 million computer ...
was the first sustainable hosting by decentralization. Freenet's model is that "true freedom requires true anonymity." Later BitTorrent was developed to allocate resources with high performance and fairness. ZeroNet
ZeroNet is a decentralized web-like network of peer-to-peer users, created by Tamas Kocsis in 2015, programming for the network was based in Budapest, Hungary; is built in Python; and is fully open source. Instead of having an IP address, sites ...
was the first DHT to support dynamic and updateable webpages. YaCy
''YaCy'' (pronounced “ya see”) is a free distributed search engine, built on the principles of peer-to-peer (P2P) networks created by Michael Christen in 2003. The engine is written in Java and distributed on several hundred computers, , so- ...
is the leading distributed search.
Anonymity Networks: The anonymity Tor Onion
Tor, short for The Onion Router, is free and open-source software for enabling anonymous communication. It directs Internet traffic through a free, worldwide, volunteer overlay network, consisting of more than seven thousand relays, to conc ...
and I2P
The Invisible Internet Project (I2P) is an anonymous network layer (implemented as a mix network) that allows for censorship-resistant, peer-to-peer communication. Anonymous connections are achieved by encrypting the user's traffic (by using ...
provides leads to more willingness to host content that would otherwise be censored. However hosting implementation and location may bring issues, and the content is still hosted by a single entity which can be controlled.
Federated: Being semi-decentralised, federated platforms such as Nextcloud
Nextcloud is a suite of client-server software for creating and using file hosting services. Nextcloud provides functionally similar to Dropbox, Office 365 or Google Drive when used with integrated office suite solutions Collabora Online or Only ...
and IRC
Internet Relay Chat (IRC) is a text-based chat system for instant messaging. IRC is designed for group communication in discussion forums, called '' channels'', but also allows one-on-one communication via private messages as well as chat an ...
make it easier for users to find an instance where they are welcomed.
Providers with a different policy: DuckDuckGo
DuckDuckGo (DDG) is an internet search engine that emphasizes protecting searchers' privacy and avoiding the filter bubble of personalized search results. DuckDuckGo does not show search results from content farms. It uses various APIs of o ...
indexes results Google has delisted. However nothing by design keeps it so.
See: Darknets
Platform beguilement
Code-words: Users can use code-words which only the in-group are aware of the intended meaning. This is especially effective if the code-word is a common term. Word connotations: Users may put a common word into a context to be given a banned meaning. This relies on the censor being unwilling to ban such a common term. Link relaying: Users can link to a page which then contains a second link to a banned website which promotes the intended message. This linking to a page having a link prevents platforms from banning the direct link, and only requires an extra link click.Proxying
Web proxies: Proxy websites are configured to allow users to load external web pages through theproxy server
In computer networking, a proxy server is a server application that acts as an intermediary between a client requesting a resource and the server providing that resource.
Instead of connecting directly to a server that can fulfill a request ...
, permitting the user to load the page as if it is coming from the proxy server and not the (blocked) source. However, depending on how the proxy is configured, a censor may be able to determine the pages loaded and/or determine that the user is using a proxy server.
For example, the mobile Opera Mini
Opera Mini is a mobile web browser made by Opera. It was primarily designed for the Java ME platform, as a low-end sibling for Opera Mobile, but it is now developed exclusively for Android. It was previously developed for iOS, Windows 10 Mobile, ...
browser uses a proxy-based approach employing encryption and compression in order to speed up downloads. This has the side effect of allowing it to circumvent several approaches to Internet censorship. In 2009 this led the government of China to ban all but a special Chinese version of the browser.
Domain fronting: Circumvention software can implement a technique called domain fronting
Domain fronting is a technique for Internet censorship circumvention that uses different domain names in different communication layers of an HTTPS connection to discreetly connect to a different target domain than is discernable to third parties ...
, where the destination of a connection is hidden by passing the initial requests through a content delivery network
A content delivery network, or content distribution network (CDN), is a geographically distributed network of proxy servers and their data centers. The goal is to provide high availability and performance by distributing the service spatially re ...
or other popular site which censors may be unwilling to block. This technique was used by messaging applications including Signal and Telegram. Tor's meek uses Microsoft's Azure cloud. However, large cloud providers such as Amazon Web Services
Amazon Web Services, Inc. (AWS) is a subsidiary of Amazon.com, Amazon that provides Software as a service, on-demand cloud computing computing platform, platforms and Application programming interface, APIs to individuals, companies, and gover ...
and Google Cloud Google Cloud Platform offers numerous integrated cloud-computing services, including compute, network, and storage.
Products
Past and present products under the Google Cloud platform include:
Current
* Google Cloud Datastore, a NoSQL databa ...
no longer permit its use. Website owners can use a free account to use a Cloudflare domain for fronting.
SSH tunneling: By establishing an SSH tunnel
In computer networks, a tunneling protocol is a communication protocol which allows for the movement of data from one network to another. It involves allowing private network communications to be sent across a public network (such as the Internet ...
, a user can forward all their traffic over an encrypted channel, so both outgoing requests for blocked sites and the response from those sites are hidden from the censors, for whom it appears as unreadable SSH
The Secure Shell Protocol (SSH) is a cryptographic network protocol for operating network services securely over an unsecured network. Its most notable applications are remote login and command-line execution.
SSH applications are based on ...
traffic.
Virtual private network (VPN): Using a VPN
A virtual private network (VPN) extends a private network across a public network and enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network. The be ...
, A user who experiences internet censorship can create a secure connection to a more permissive country, and browse the internet as if they were situated in that country. Some services are offered for a monthly fee; others are ad-supported. According to GlobalWebIndex
GWI (formerly GlobalWebIndex) is an audience research company founded by Tom Smith in 2009 that provides audience insight to publishers, media agencies and marketers around the world. GWI profiles consumers across 48+ countries with a panel re ...
in 2014, there were over 400 million people use virtual private networks to circumvent censorship or for increased level of privacy although this number is not verifiable.
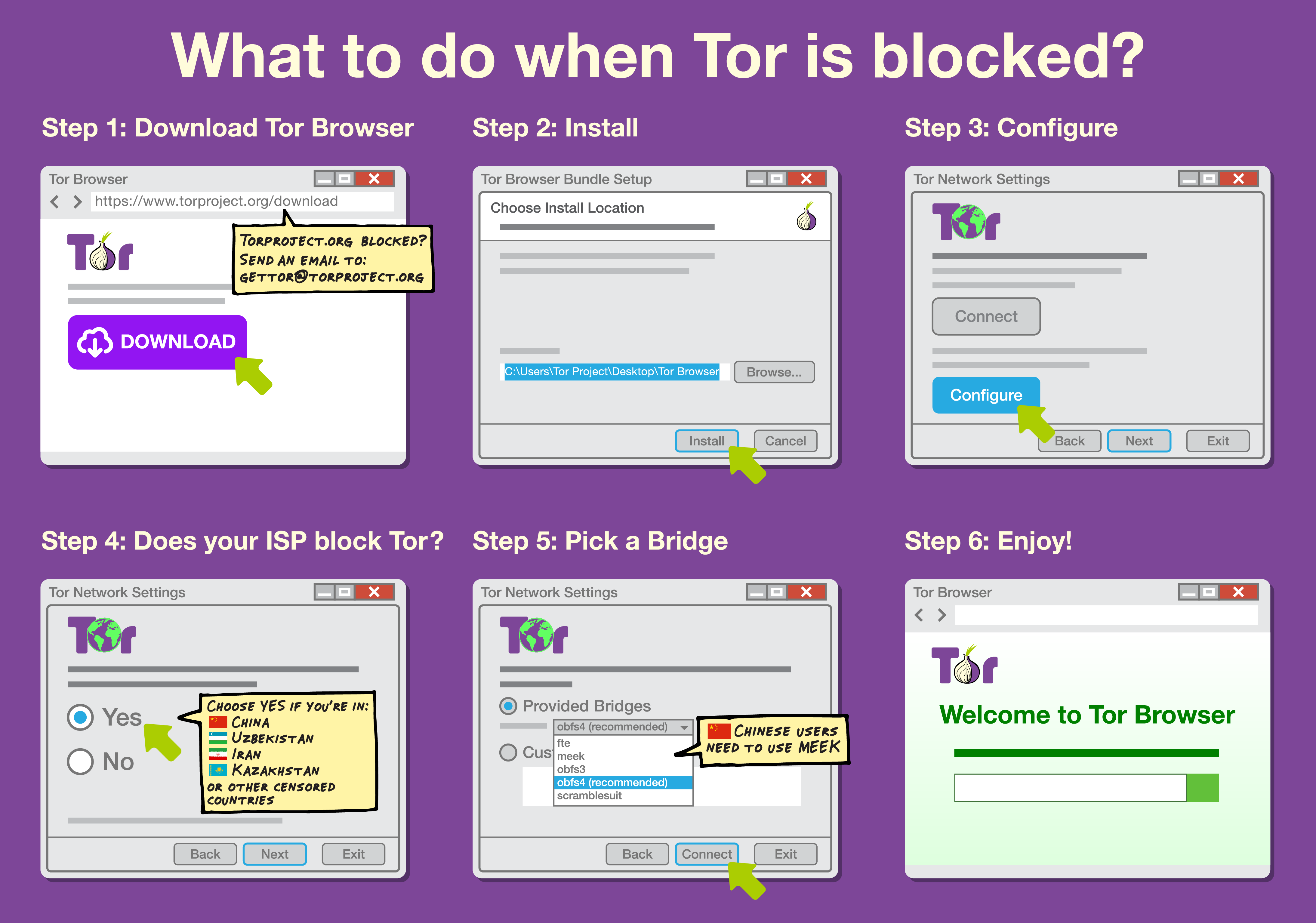
Tor: More advanced tools such as Tor
Tor, TOR or ToR may refer to:
Places
* Tor, Pallars, a village in Spain
* Tor, former name of Sloviansk, Ukraine, a city
* Mount Tor, Tasmania, Australia, an extinct volcano
* Tor Bay, Devon, England
* Tor River, Western New Guinea, Indonesia
Sc ...
route encrypted traffic through multiple servers to make the source and destination of traffic less traceable. It can in some cases be used to avoid censorship, especially when configured to use traffic obfuscation techniques.

Traffic obfuscation
A censor may be able to detect and block use of circumvention tools throughDeep Packet Inspection
Deep packet inspection (DPI) is a type of data processing that inspects in detail the data being sent over a computer network, and may take actions such as alerting, blocking, re-routing, or logging it accordingly. Deep packet inspection is oft ...
. There are efforts to make circumvention tools less detectable by randomizing the traffic, attempting to mimic a whitelisted protocol or tunneling traffic through a whitelisted site by using techniques including domain fronting or Meek. Tor and other circumvention tools have adopted multiple obfuscation techniques that users can use depending on the nature of their connection, which are sometimes called "Pluggable Transports".
Internet alternatives
Functionality that people may be after might overlap with non-internet services, such as traditionalpost
Post or POST commonly refers to:
*Mail, the postal system, especially in Commonwealth of Nations countries
**An Post, the Irish national postal service
**Canada Post, Canadian postal service
**Deutsche Post, German postal service
**Iraqi Post, Ira ...
, Bluetooth, or wakie-talkie. The following are some detailed examples:Alternative data transport
Datacasting
Datacasting (data broadcasting) is the broadcasting of data over a wide area via radio waves. It most often refers to supplemental information sent by television stations along with digital terrestrial television (DTT), but may also be applied ...
allows transmission of Web pages and other information via satellite broadcast channels bypassing the Internet entirely. This requires a satellite dish and suitable receiver hardware but provides a powerful means of avoiding censorship. Because the system is entirely receive only for the end user, a suitably air-gapped computer can be impossible to detect.
Sneakernets
Asneakernet
Sneakernet, also called sneaker net, is an informal term for the transfer of electronic information by physically moving media such as magnetic tape, floppy disks, optical discs, USB flash drives or external hard drives between computers, rather ...
is the transfer of electronic information, especially computer files, by physically carrying data on storage media from one place to another. A sneakernet can move data regardless of network restrictions simply by not using the network at all.Sullivan, Bob (13 April 2006Military Thumb Drives Expose Larger Problem
''MSNBC'' Retrieved on 25 January 2007. One example of a widely adopted sneakernet network is
El Paquete Semanal
''El Paquete Semanal'' ("The Weekly Package") or ''El Paquete'' is a one terabyte collection of digital material distributed since around 2008 on the underground market in Cuba as a substitute for broadband Internet. Since 2015, it has been the pri ...
in Cuba.
Adoption of circumvention tools
Circumvention tools have seen spikes in adoption in response to high-profile blocking attempts, however, studies measuring adoption of circumvention tools in countries with persistent and widespread censorship report mixed results.In response to persistent censorship
Measures and estimates of circumvention tool adoption have reported widely divergent results. A 2010 study by Harvard University researchers estimated that very few users use censorship circumvention tools—likely less than 3% of users even in countries that consistently implement widespread censorship. Other studies have reported substantially larger estimates, but have been disputed. In China, anecdotal reports suggest that adoption of circumvention tools is particularly high in certain communities, such as universities, and a survey byFreedom House
Freedom House is a non-profit, majority U.S. government funded organization in Washington, D.C., that conducts research and advocacy on democracy, political freedom, and human rights. Freedom House was founded in October 1941, and Wendell Wil ...
found that users generally did not find circumvention tools to be difficult to use. Market research firm GlobalWebIndex
GWI (formerly GlobalWebIndex) is an audience research company founded by Tom Smith in 2009 that provides audience insight to publishers, media agencies and marketers around the world. GWI profiles consumers across 48+ countries with a panel re ...
has reported that there are over 35 million Twitter users and 63 million Facebook users in China (both services are blocked). However, these estimates have been disputed; Facebook's advertising platform estimates 1 million users in China, and other reports of Twitter adoption estimate 10 million users. Other studies have pointed out that efforts to block circumvention tools in China have reduced adoption of those tools; the Tor network previously had over 30,000 users connecting from China but as of 2014 had only approximately 3,000 Chinese users.
In Thailand
Thailand ( ), historically known as Siam () and officially the Kingdom of Thailand, is a country in Southeast Asia, located at the centre of the Indochinese Peninsula, spanning , with a population of almost 70 million. The country is bo ...
, internet censorship has existed since 2002, and there is sporadic and inconsistent filtering. In a small-scale survey of 229 Thai internet users, a research group at the University of Washington found that 63% of surveyed users attempted to use circumvention tools, and 90% were successful in using those tools. Users often made on-the-spot decisions about use of circumvention tools based on limited or unreliable information, and had a variety of perceived threats, some more abstract and others more concrete based on personal experiences.
In response to blocking events
In response to the 2014 blocking of Twitter inTurkey
Turkey ( tr, Türkiye ), officially the Republic of Türkiye ( tr, Türkiye Cumhuriyeti, links=no ), is a list of transcontinental countries, transcontinental country located mainly on the Anatolia, Anatolian Peninsula in Western Asia, with ...
, information about alternate DNS servers was widely shared, as using another DNS server such as Google Public DNS
Google Public DNS is a Domain Name System (DNS) service offered to Internet users worldwide by Google. It functions as a recursive name server.
Google Public DNS was announced on December 3, 2009, in an effort described as "making the web faster ...
allowed users to access Twitter. The day after the block, the total number of posts made in Turkey was up 138%, according to Brandwatch
Brandwatch is a social media suite company owned by Cision. Brandwatch sells two different solutions: Consumer Intelligence and Social Media Management.
Consumer Intelligence is made up of three different products: Consumer Research and add-ons Vi ...
, an internet measurement firm.
After an April 2018 ban on the Telegram
Telegraphy is the long-distance transmission of messages where the sender uses symbolic codes, known to the recipient, rather than a physical exchange of an object bearing the message. Thus flag semaphore is a method of telegraphy, whereas p ...
messaging app in Iran, web searches for VPN and other circumvention software increased as much as 48× for some search terms, but there was evidence that users were downloading unsafe software. As many as a third of Iranian internet users used the Psiphon
Psiphon is a free and open-source Internet censorship circumvention tool that uses a combination of secure communication and obfuscation technologies, such as a VPN, SSH, and a Web proxy. Psiphon is a centrally managed and geographically diverse ...
tool in the days immediately following the block, and in June 2018 as many as 3.5 million Iranian users continued to use the tool.
Anonymity, risks, and trust
Circumvention andanonymity
Anonymity describes situations where the acting person's identity is unknown. Some writers have argued that namelessness, though technically correct, does not capture what is more centrally at stake in contexts of anonymity. The important idea he ...
are different. Circumvention systems are designed to bypass blocking, but they do not usually protect identities. Anonymous systems protect a user's identity. And while they can contribute to circumvention, that is not their primary function. It is important to understand that open public proxy sites do not provide anonymity and can view and record the location of computers making requests as well as the websites accessed.
In many jurisdictions accessing blocked content is a serious crime
In ordinary language, a crime is an unlawful act punishable by a State (polity), state or other authority. The term ''crime'' does not, in modern criminal law, have any simple and universally accepted definition,Farmer, Lindsay: "Crime, definit ...
, particularly content that is considered child pornography
Child pornography (also called CP, child sexual abuse material, CSAM, child porn, or kiddie porn) is pornography that unlawfully exploits children for sexual stimulation. It may be produced with the direct involvement or sexual assault of a chi ...
, a threat to national security
National security, or national defence, is the security and defence of a sovereign state, including its citizens, economy, and institutions, which is regarded as a duty of government. Originally conceived as protection against military atta ...
, or an incitement of violence. Thus it is important to understand the circumvention technologies and the protections they do or do not provide and to use only tools that are appropriate in a particular context. Great care must be taken to install, configure, and use circumvention tools properly. Individuals associated with high-profile rights organizations, dissident
A dissident is a person who actively challenges an established Political system, political or Organized religion, religious system, doctrine, belief, policy, or institution. In a religious context, the word has been used since the 18th century, and ...
, protest, or reform groups should take extra precautions to protect their online identities.
Circumvention sites and tools should be provided and operated by trusted third parties located outside the censoring jurisdiction that do not collect identities and other personal information. Best are trusted family and friends personally known to the circumventor, but when family and friends are not available, sites and tools provided by individuals or organizations that are only known by their reputations or through the recommendations and endorsement of others may need to be used. Commercial circumvention services may provide anonymity while surfing the Internet, but could be compelled by law to make their records and users' personal information available to law enforcement.
Software
There are five general types of Internet censorship circumvention software: CGI proxies use a script running on aweb server
A web server is computer software and underlying hardware that accepts requests via HTTP (the network protocol created to distribute web content) or its secure variant HTTPS. A user agent, commonly a web browser or web crawler, initiate ...
to perform the proxying function. A CGI proxy client sends the requested url embedded within the data portion of an HTTP request to the CGI proxy server. The CGI proxy server pulls the ultimate destination information from the data embedded in the HTTP request, sends out its own HTTP request to the ultimate destination, and then returns the result to the proxy client. A CGI proxy tool's security can be trusted as far as the operator of the proxy server can be trusted. CGI proxy tools require no manual configuration of the browser or client software installation, but they do require that the user use an alternative, potentially confusing browser interface within the existing browser.
HTTP proxies send HTTP requests
The Hypertext Transfer Protocol (HTTP) is an application layer protocol in the Internet protocol suite model for distributed, collaborative, hypermedia information systems. HTTP is the foundation of data communication for the World Wide Web, w ...
through an intermediate proxying server. A client connecting through a HTTP proxy sends exactly the same HTTP request to the proxy as it would send to the destination server unproxied. The HTTP proxy parses the HTTP request; sends its own HTTP request to the ultimate destination server; and then returns the response back to the proxy client. An HTTP proxy tool's security can be trusted as far as the operator of the proxy server can be trusted. HTTP proxy tools require either manual configuration of the browser or client side software that can configure the browser for the user. Once configured, an HTTP proxy tool allows the user transparently to use his normal browser interface.
Application proxies are similar to HTTP proxies, but support a wider range of online applications.
Peer-to-peer
Peer-to-peer (P2P) computing or networking is a distributed application architecture that partitions tasks or workloads between peers. Peers are equally privileged, equipotent participants in the network. They are said to form a peer-to-peer n ...
systems store content across a range of participating volunteer servers combined with technical techniques such as re-routing to reduce the amount of trust placed on volunteer servers or on social networks to establish trust relationships between server and client users. Peer-to-peer system can be trusted as far as the operators of the various servers can be trusted or to the extent that the architecture of the peer-to-peer system limits the amount of information available to any single server and the server operators can be trusted not to cooperate to combine the information they hold.
Re-routing systems send requests and responses through a series of proxying servers, encrypting the data again at each proxy, so that a given proxy knows at most either where the data came from or is going to, but not both. This decreases the amount of trust required of the individual proxy hosts.
Below is a list of different Internet censorship circumvention software:
See also
*Anonymous P2P
An anonymous P2P communication system is a peer-to-peer distributed application in which the nodes, which are used to share resources, or participants are anonymous or pseudonymous. Anonymity of participants is usually achieved by special routi ...
* Bypassing content-control filters
*Computer surveillance
Computer and network surveillance is the monitoring of computer activity and data stored locally on a computer or data being transferred over computer networks such as the Internet. This monitoring is often carried out covertly and may be comple ...
*Content-control software
An Internet filter is software that restricts or controls the content an Internet user is capable to access, especially when utilized to restrict material delivered over the Internet via the Web, Email, or other means. Content-control software det ...
*Crypto-anarchism
Crypto-anarchism or cyberanarchism is a political ideology focusing on protection of privacy, political freedom, and economic freedom, the adherents of which use cryptographic software for confidentiality and security while sending and receiving ...
*Cypherpunk
A cypherpunk is any individual advocating widespread use of strong cryptography and privacy-enhancing technologies as a route to social and political change. Originally communicating through the Cypherpunks electronic mailing list, informal g ...
*Electronic Frontier Foundation
The Electronic Frontier Foundation (EFF) is an international non-profit digital rights group based in San Francisco, California. The foundation was formed on 10 July 1990 by John Gilmore, John Perry Barlow and Mitch Kapor to promote Internet ci ...
- an international non-profit digital rights advocacy and legal organization
*Freedom of information
Freedom of information is freedom of a person or people to publish and consume information. Access to information is the ability for an individual to seek, receive and impart information effectively. This sometimes includes "scientific, indigeno ...
*Freedom of speech
Freedom of speech is a principle that supports the freedom of an individual or a community to articulate their opinions and ideas without fear of retaliation, censorship, or legal sanction. The right to freedom of expression has been recogni ...
* Global Internet Freedom Consortium (GIFC) - a consortium of organizations that develop and deploy anti-censorship technologies
* Bypassing the Great Firewall of China
*Internet freedom Internet freedom is an umbrella term that encompasses digital rights, freedom of information, the right to Internet access, freedom from Internet censorship, and net neutrality.
Some believe that Internet freedom is not a human right. They think t ...
*Internet privacy
Internet privacy involves the right or mandate of personal privacy concerning the storing, re-purposing, provision to third parties, and displaying of information pertaining to oneself via Internet. Internet privacy is a subset of data privacy. Pr ...
*Mesh networking
A mesh network is a local area network topology in which the infrastructure nodes (i.e. bridges, switches, and other infrastructure devices) connect directly, dynamically and non-hierarchically to as many other nodes as possible and cooperate wit ...
*Open Technology Fund
The Open Technology Fund (OTF) is an American nonprofit corporation that aims to support global Internet freedom technologies. Its mission is to "support open technologies and communities that increase free expression, circumvent censorship, and ...
(OTF) – a U.S. Government funded program created in 2012 at Radio Free Asia to support global Internet freedom technologies
*Proxy list
A proxy list is a list of open HTTP/HTTPS/SOCKS proxy servers all on one website. Proxies allow users to make indirect network connections to other computer network services. Proxy lists include the IP addresses of computers hosting open proxy se ...
* Tactical Technology Collective – a non-profit foundation promoting the use of free and open source software for non-governmental organizations, and producers of NGO-in-A-Box
References
External links
*Casting A Wider Net: Lessons Learned in Delivering BBC Content on the Censored Internet
', Ronald Deibert, Canada Centre for Global Security Studies and Citizen Lab, Munk School of Global Affairs, University of Toronto, 11 October 2011
Censorship Wikia
an anti-censorship site that catalogs past and present censored works, using verifiable sources, and a forum to discuss organizing against and circumventing censorship
"Circumvention Tool Evaluation: 2011"
Hal Roberts, Ethan Zuckerman, and John Palfrey, Berkman Centre for Internet & Society, 18 August 2011
"Circumvention Tool Usage Report: 2010"
Hal Roberts, Ethan Zuckerman, Jillian York, Robert Faris, and John Palfrey, Berkman Centre for Internet & Society, 14 October 2010
Digital Security and Privacy for Human Rights Defenders
by Dmitri Vitaliev, Published by Front Line - The International Foundation for the Protection of Human Rights Defenders
"Digital Tools to Curb Snooping"
''New York Times'', 17 July 2013
Methods and Scripts useful for evading censorship through DNS filtering *
How to Bypass Internet Censorship
', also known by the titles: ''Bypassing Internet Censorship'' or ''Circumvention Tools'', a
FLOSS
Free and open-source software (FOSS) is a term used to refer to groups of software consisting of both free software and open-source software where anyone is freely licensed to use, copy, study, and change the software in any way, and the source ...
Manual, 10 March 2011, 240 pp. Translations have been published iArabic
an
Vietnamese
"Leaping over the Firewall: A Review of Censorship Circumvention Tools"
, by Cormac Callanan (Ireland), Hein Dries-Ziekenheiner (Netherlands), Alberto Escudero-Pascual (Sweden), and Robert Guerra (Canada), Freedom House, April 2011
"Media Freedom Internet Cookbook"
by the
OSCE Representative on Freedom of the Media The OSCE Representative on Freedom of the Media functions as a watchdog on media developments in all 57 participating member states of the Organization for Security and Co-operation in Europe (OSCE). The representative provides early warning on viol ...
, Vienna, 2004
"Online Survival Kit"
We Fight Censorship project of Reporters Without Borders
Free Haven Project, accessed 16 September 2011 {{DEFAULTSORT:Internet Censorship Circumvention Internet security Content-control software Internet censorship Internet privacy Circumvention