|
ZeroNet
ZeroNet is a decentralized web-like network of peer-to-peer users, created by Tamas Kocsis in 2015, programming for the network was based in Budapest, Hungary; is built in Python; and is fully open source. Instead of having an IP address, sites are identified by a public key (specifically a bitcoin address). The private key allows the owner of a site to sign and publish changes, which propagate through the network. Sites can be accessed through an ordinary web browser when using the ZeroNet application, which acts as a local webhost for such pages. In addition to using bitcoin cryptography, ZeroNet uses trackers from the BitTorrent network to negotiate connections between peers. ZeroNet is not anonymous by default, but it supports routing traffic through the Tor network. The ZeroNet website and bittorrent tracker are blocked in mainland China. Despite the censorship, however, it's still possible to access ZeroNet from behind the Great Firewall of China, even over Tor, by bootstr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Tamas Kocsis
Tamas may refer to: * ''Tamas'' (philosophy), a concept of darkness and death in Hindu philosophy * Tamás (name), a given name in Hungarian (Thomas) * ''Tamas'' (film), a 1987 TV series/movie directed by Govind Nihalani * ''Tamas'' (novel), a 1975 novel by Bhisham Sahni * Christian Tămaș, Romanian writer * Gabriel Tamaș Gabriel Sebastian Tamaș (; born 9 November 1983) is a Romanian professional footballer who plays as a centre-back for Liga II club Concordia Chiajna. Tamaș started out as a senior at FC Brașov in the 1998–99 season, and is a journeyman w ... (born 1983), Romanian footballer * Vladimir Tămaș, Romanian footballer See also * Tama (other) {{Disambiguation, surname hu:Tamás ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Network
A computer network is a set of computers sharing resources located on or provided by network nodes. The computers use common communication protocols over digital interconnections to communicate with each other. These interconnections are made up of telecommunication network technologies, based on physically wired, optical, and wireless radio-frequency methods that may be arranged in a variety of network topologies. The nodes of a computer network can include personal computers, servers, networking hardware, or other specialised or general-purpose hosts. They are identified by network addresses, and may have hostnames. Hostnames serve as memorable labels for the nodes, rarely changed after initial assignment. Network addresses serve for locating and identifying the nodes by communication protocols such as the Internet Protocol. Computer networks may be classified by many criteria, including the transmission medium used to carry signals, bandwidth, communications pro ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
DMCA Takedown
The Online Copyright Infringement Liability Limitation Act (OCILLA) is United States federal law that creates a conditional 'safe harbor' for online service providers (OSP) (a group which includes internet service providers (ISP) and other Internet intermediaries) by shielding them for their own acts of direct copyright infringement (when they make unauthorized copies) as well as shielding them from potential secondary liability for the infringing acts of others. OCILLA was passed as a part of the 1998 Digital Millennium Copyright Act (DMCA) and is sometimes referred to as the " Safe Harbor" provision or as "DMCA 512" because it addeSection 512to Title 17 of the United States Code. By exempting Internet intermediaries from copyright infringement liability provided they follow certain rules, OCILLA attempts to strike a balance between the competing interests of copyright owners and digital users. Overview The 1998 DMCA was the U.S. implementation of the 1996 WIPO Copyright Treat ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Domain Fronting
Domain fronting is a technique for Internet censorship circumvention that uses different domain names in different communication layers of an HTTPS connection to discreetly connect to a different target domain than is discernable to third parties monitoring the requests and connections. Due to quirks in security certificates, the redirect systems of the content delivery networks (CDNs) used as 'domain fronts', and the protection provided by HTTPS, censors are typically unable to differentiate circumvention ("domain-fronted") traffic from overt non-fronted traffic for any given domain name. As such they are forced to either allow all traffic to the domain front—including circumvention traffic—or block the domain front entirely, which may result in expensive collateral damage and has been likened to "blocking the rest of the Internet". Domain fronting does not conform to HTTP standards that require the SNI extension and HTTP Host header to contain the same domain. Many large c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
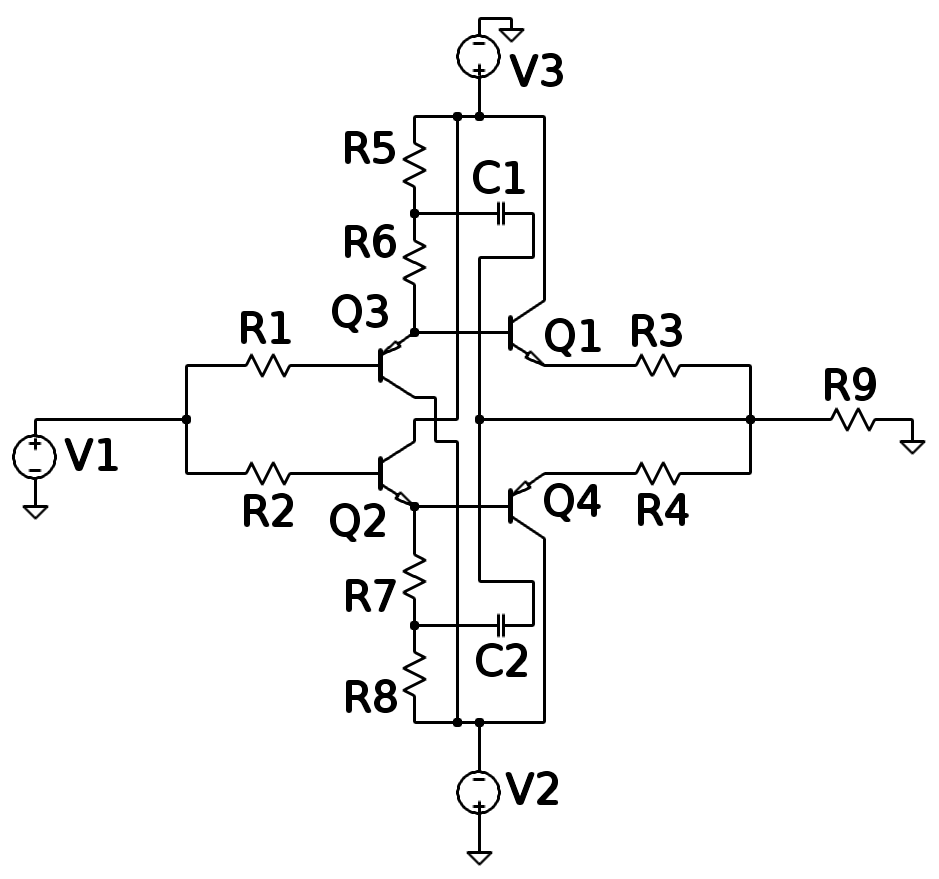
Bootstrapping (electronics)
In the field of electronics, a technique where part of the output of a system is used at startup can be described as bootstrapping. A bootstrap circuit is one where part of the output of an amplifier stage is applied to the input, so as to alter the input impedance of the amplifier. When applied deliberately, the intention is usually to increase rather than decrease the impedance. In the domain of MOSFET circuits, bootstrapping is commonly used to mean pulling up the operating point of a transistor above the power supply rail. The same term has been used somewhat more generally for dynamically altering the operating point of an operational amplifier (by shifting both its positive and negative supply rail) in order to increase its output voltage swing (relative to the ground). In the sense used in this paragraph, bootstrapping an operational amplifier means "using a signal to drive the reference point of the op-amp's power supplies". A more sophisticated use of this rail boots ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Great Firewall Of China
The Great Firewall (''GFW''; ) is the combination of legislative actions and technologies enforced by the People's Republic of China to regulate the Internet domestically. Its role in internet censorship in China is to block access to selected foreign websites and to slow down cross-border internet traffic. The Great Firewall operates by checking transmission control protocol (TCP) packets for keywords or sensitive words. If the keywords or sensitive words appear in the TCP packets, access will be closed. If one link is closed, more links from the same machine will be blocked by the Great Firewall. The effect includes: limiting access to foreign information sources, blocking foreign internet tools (e.g. Google Search, Facebook, Twitter, Wikipedia, and others) and mobile apps, and requiring foreign companies to adapt to domestic regulations. Besides censorship, the Great Firewall has also influenced the development of China's internal internet economy by giving preference to domesti ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Tor (anonymity Network)
Tor, short for The Onion Router, is free and open-source software for enabling anonymous communication. It directs Internet traffic through a free, worldwide, volunteer overlay network, consisting of more than seven thousand relays, to conceal a user's location and usage from anyone performing network surveillance or traffic analysis. Using Tor makes it more difficult to trace a user's Internet activity. Tor's intended use is to protect the personal privacy of its users, as well as their freedom and ability to communicate confidentially through IP address anonymity using Tor exit nodes. History The core principle of Tor, onion routing, was developed in the mid-1990s by United States Naval Research Laboratory employees, mathematician Paul Syverson, and computer scientists Michael G. Reed and David Goldschlag, to protect American intelligence communications online. Onion routing is implemented by means of encryption in the application layer of the communication protocol stack ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptography
Cryptography, or cryptology (from grc, , translit=kryptós "hidden, secret"; and ''graphein'', "to write", or ''-logia'', "study", respectively), is the practice and study of techniques for secure communication in the presence of adversarial behavior. More generally, cryptography is about constructing and analyzing protocols that prevent third parties or the public from reading private messages. Modern cryptography exists at the intersection of the disciplines of mathematics, computer science, information security, electrical engineering, digital signal processing, physics, and others. Core concepts related to information security ( data confidentiality, data integrity, authentication, and non-repudiation) are also central to cryptography. Practical applications of cryptography include electronic commerce, chip-based payment cards, digital currencies, computer passwords, and military communications. Cryptography prior to the modern age was effectively synonymo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Bitcoin
Bitcoin ( abbreviation: BTC; sign: ₿) is a decentralized digital currency that can be transferred on the peer-to-peer bitcoin network. Bitcoin transactions are verified by network nodes through cryptography and recorded in a public distributed ledger called a blockchain. The cryptocurrency was invented in 2008 by an unknown person or group of people using the name Satoshi Nakamoto. The currency began use in 2009, when its implementation was released as open-source software. The word "''bitcoin''" was defined in a white paper published on October 31, 2008. It is a compound of the words ''bit'' and ''coin''. The legality of bitcoin varies by region. Nine countries have fully banned bitcoin use, while a further fifteen have implicitly banned it. A few governments have used bitcoin in some capacity. El Salvador has adopted Bitcoin as legal tender, although use by merchants remains low. Ukraine has accepted cryptocurrency donations to fund the resistance to the 2022 Russ ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
IP Address
An Internet Protocol address (IP address) is a numerical label such as that is connected to a computer network that uses the Internet Protocol for communication.. Updated by . An IP address serves two main functions: network interface identification and location addressing. Internet Protocol version 4 (IPv4) defines an IP address as a 32-bit number. However, because of the growth of the Internet and the depletion of available IPv4 addresses, a new version of IP (IPv6), using 128 bits for the IP address, was standardized in 1998. IPv6 deployment has been ongoing since the mid-2000s. IP addresses are written and displayed in human-readable notations, such as in IPv4, and in IPv6. The size of the routing prefix of the address is designated in CIDR notation by suffixing the address with the number of significant bits, e.g., , which is equivalent to the historically used subnet mask . The IP address space is managed globally by the Internet Assigned Numbers Authority (IA ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Open Source Software
Open-source software (OSS) is computer software that is released under a license in which the copyright holder grants users the rights to use, study, change, and distribute the software and its source code to anyone and for any purpose. Open-source software may be developed in a collaborative public manner. Open-source software is a prominent example of open collaboration, meaning any capable user is able to participate online in development, making the number of possible contributors indefinite. The ability to examine the code facilitates public trust in the software. Open-source software development can bring in diverse perspectives beyond those of a single company. A 2008 report by the Standish Group stated that adoption of open-source software models has resulted in savings of about $60 billion per year for consumers. Open source code can be used for studying and allows capable end users to adapt software to their personal needs in a similar way user scripts a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |