Common Access Cards on:
[Wikipedia]
[Google]
[Amazon]
 The Common Access Card, also commonly referred to as the CAC is a
The Common Access Card, also commonly referred to as the CAC is a
Navy CAC PMO
/ref> has also created a CAC PIN Reset workstation capable of resetting a locked CAC PIN. For some DoD networks,
 The Common Access Card, also commonly referred to as the CAC is a
The Common Access Card, also commonly referred to as the CAC is a smart card
A smart card, chip card, or integrated circuit card (ICC or IC card) is a physical electronic authentication device, used to control access to a resource. It is typically a plastic credit card-sized card with an embedded integrated circuit (IC) c ...
about the size of a credit card. It is the standard identification for Active Duty United States Defense personnel, to include the Selected Reserve
The Selected Reserve (also called SELRES, SR, or mistakenly Selective Reserve) are the members of a U.S. military Ready Reserve unit that are enrolled in the Ready Reserve program and the reserve unit that they are attached to. Selected Reserve me ...
and National Guard
National Guard is the name used by a wide variety of current and historical uniformed organizations in different countries. The original National Guard was formed during the French Revolution around a cadre of defectors from the French Guards.
N ...
, United States Department of Defense
The United States Department of Defense (DoD, USDOD or DOD) is an executive branch department of the federal government charged with coordinating and supervising all agencies and functions of the government directly related to national secur ...
(DoD) civilian employees, United States Coast Guard
The United States Coast Guard (USCG) is the maritime security, search and rescue, and law enforcement service branch of the United States Armed Forces and one of the country's eight uniformed services. The service is a maritime, military, mu ...
(USCG) civilian employees and eligible DoD and USCG contractor personnel. It is also the principal card used to enable physical access to buildings and controlled spaces, and it provides access to defense computer networks and systems. It also serves as an identification card under the Geneva Conventions
upright=1.15, Original document in single pages, 1864
The Geneva Conventions are four treaties, and three additional protocols, that establish international legal standards for humanitarian treatment in war. The singular term ''Geneva Conv ...
(especially the Third Geneva Convention
The Third Geneva Convention, relative to the treatment of prisoners of war, is one of the four treaties of the Geneva Conventions. The Geneva Convention relative to the Treatment of Prisoners of War was first adopted in 1929, but significantl ...
). In combination with a personal identification number
A personal identification number (PIN), or sometimes redundantly a PIN number or PIN code, is a numeric (sometimes alpha-numeric) passcode used in the process of authenticating a user accessing a system.
The PIN has been the key to facilitatin ...
, a CAC satisfies the requirement for two-factor authentication
Multi-factor authentication (MFA; encompassing two-factor authentication, or 2FA, along with similar terms) is an electronic authentication method in which a user is granted access to a website or application only after successfully presenting ...
: something the user knows combined with something the user has. The CAC also satisfies the requirements for digital signature
A digital signature is a mathematical scheme for verifying the authenticity of digital messages or documents. A valid digital signature, where the prerequisites are satisfied, gives a recipient very high confidence that the message was created b ...
and data encryption
In cryptography, encryption is the process of encoding information. This process converts the original representation of the information, known as plaintext, into an alternative form known as ciphertext. Ideally, only authorized parties can decip ...
technologies: authentication, integrity and non-repudiation Non-repudiation refers to a situation where a statement's author cannot successfully dispute its authorship or the validity of an associated contract. The term is often seen in a legal setting when the authenticity of a signature is being challenged ...
.
The CAC is a controlled item. As of 2008, DoD has issued over 17 million smart cards. This number includes reissues to accommodate changes in name, rank, or status and to replace lost or stolen cards. As of the same date, approximately 3.5 million unterminated or active CACs are in circulation. DoD has deployed an issuance infrastructure at over 1,000 sites in more than 25 countries around the world and is rolling out more than one million card readers and associated middleware.
Issuance
The CAC is issued to Active United States Armed Forces (Regular, Reserves and National Guard) in the Department of Defense and the U.S. Coast Guard; DoD civilians; USCG civilians; non-DoD/other government employees and State Employees of the National Guard; and eligible DoD and USCG contractors who need access to DoD or USCG facilities and/or DoD computer network systems: *Active Duty U.S. Armed Forces (to include Cadets and Midshipmen of the U.S. Service Academies) *Reserve members of the U.S. Armed Forces *National Guard (Army National Guard and Air National Guard) members of the U.S. Armed Forces *National Oceanic and Atmospheric Administration
The National Oceanic and Atmospheric Administration (abbreviated as NOAA ) is an United States scientific and regulatory agency within the United States Department of Commerce that forecasts weather, monitors oceanic and atmospheric conditi ...
*United States Public Health Service
The United States Public Health Service (USPHS or PHS) is a collection of agencies of the Department of Health and Human Services concerned with public health, containing nine out of the department's twelve operating divisions. The Assistant ...
*Emergency-Essential Employees
*Contingency Contractor Employees
*Contracted college & university ROTC Cadets and Midshipmen
*Deployed Overseas Civilians
*Non-Combatant Personnel
*DoD/Uniformed Service Civilians residing on military installations in CONUS
''Conus'' is a genus of predatory sea snails, or cone snails, marine gastropod mollusks in the family Conidae.Bouchet, P.; Gofas, S. (2015). Conus Linnaeus, 1758. In: MolluscaBase (2015). Accessed through: World Register of Marine Species ...
, Hawaii
Hawaii ( ; haw, Hawaii or ) is a state in the Western United States, located in the Pacific Ocean about from the U.S. mainland. It is the only U.S. state outside North America, the only state that is an archipelago, and the only ...
, Alaska
Alaska ( ; russian: Аляска, Alyaska; ale, Alax̂sxax̂; ; ems, Alas'kaaq; Yup'ik: ''Alaskaq''; tli, Anáaski) is a state located in the Western United States on the northwest extremity of North America. A semi-exclave of the U.S ...
, Puerto Rico
Puerto Rico (; abbreviated PR; tnq, Boriken, ''Borinquen''), officially the Commonwealth of Puerto Rico ( es, link=yes, Estado Libre Asociado de Puerto Rico, lit=Free Associated State of Puerto Rico), is a Caribbean island and Unincorporated ...
, or Guam
Guam (; ch, Guåhan ) is an organized, unincorporated territory of the United States in the Micronesia subregion of the western Pacific Ocean. It is the westernmost point and territory of the United States (reckoned from the geographic ce ...
*DoD/Uniformed Service Civilians or Contracted Civilian residing in a foreign country for at least 365 days
*Presidential Appointees approved by the United States Senate
The United States Senate is the upper chamber of the United States Congress, with the House of Representatives being the lower chamber. Together they compose the national bicameral legislature of the United States.
The composition and ...
*DoD Civilian employees, and United States Military veterans with a Veterans Affairs Disability rating of 100% P&T
*Eligible DoD and USCG Contractor Employees
*Non-DoD/other government and state employees of the National Guard
Future plans include the ability to store additional information through the incorporation of RFID
Radio-frequency identification (RFID) uses electromagnetic fields to automatically identify and track tags attached to objects. An RFID system consists of a tiny radio transponder, a radio receiver and transmitter. When triggered by an electroma ...
chips or other contactless technology to allow seamless access to DoD facilities.
The program that is currently used to issue CAC IDs is called the Real-Time Automated Personnel Identification System The Real-Time Automated Personnel Identification System (RAPIDS) is a United States Department of Defense (DoD) system used to issue the definitive credential within DoD. RAPIDS uses information stored in the DoD Defense Enrollment Eligibility Rep ...
(RAPIDS). RAPIDS interfaces with the Joint Personnel Adjudication System (JPAS), and uses this system to verify that the candidate has passed a background investigation and FBI fingerprint check. Applying for a CAC requires DoD form 1172-2 to be filled out and then filed with RAPIDS.
The system is secure and monitored by the DoD at all times. Different RAPIDS sites have been set up throughout military installations in and out of combat theater to issue new cards.
Design
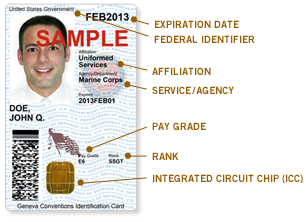
On the front of the card, the background shows the phrase "U.S. DEPARTMENT OF DEFENSE" repeated across the card. A color photo of the owner is placed on the top left corner. Below the photo is the name of the owner. The top right corner displays the expiration date. Other information on the front include (if applicable) the owner'spay grade A pay grade is a unit in systems of monetary compensation for employment. It is commonly used in public service, both civil and military, but also for companies of the private sector. Pay grades facilitate the employment process by providing a fi ...
, rank and federal identifier. A PDF417
PDF417 is a stacked linear barcode format used in a variety of applications such as transport, identification cards, and inventory management. "PDF" stands for Portable Data File. The "417" signifies that each pattern in the code consists of 4 ...
stacked two-dimensional barcode is displayed on the bottom left corner. And, an integrated circuit chip (ICC) is placed near the bottom-middle of the card.
There are three color code schemes used on the front of the CAC. A blue bar across the owner's name shows that the owner is a non-U.S. citizen. A green bar shows that the owner is a contractor. No bar is for all other personnel—including military personnel and civil workers, among others.
The back of the card has a ghost image of the owner. And if applicable, the card also contains the date of birth, blood type, DoD benefits number, Geneva Convention category, and DoD Identification Number (also used as the Geneva Convention number, replacing the previously used Social Security Number). The DoD number is also known as the Electronic data interchange Personal Identifier (EDIPI). A Code 39
Code 39 (also known as Alpha39, Code 3 of 9, Code 3/9, Type 39, USS Code 39, or USD-3) is a variable length, discrete barcode symbology.
The Code 39 specification defines 43 characters, consisting of uppercase letters (A through Z), numeric digi ...
linear barcode, as well as a magnetic strip is placed on the top and bottom of the card. The DoD ID/EDIPI number stays with the owner throughout his or her career with the DoD or USCG, even when he or she changes armed services or other departments within the DoD or the USCG. For retired U.S. military personnel who subsequently become DoD or USCG civilians or DoD or USCG contractors, the DoD ID/EDIPI Number on their CAC will be the same as on their DD Form 2 Retired ID Card. For non-military spouses, unremarried former spouses, and widows/widowers of active, Reserve or Retired U.S. military personnel who themselves become DoD or USCG civilians or DoD or USCG contractors, the DoD ID/EDIPI Number on their CAC will be the same as on their DD 1173 Uniformed Services Privilege and Identification Card (e.g., Dependent ID card).
The front of the CAC is fully laminated, while the back is only laminated in the lower half (to avoid interference with the magnetic stripe).
The CAC is said to be resistant to identity fraud, tampering, counterfeiting, and exploitation and provides an electronic means of rapid authentication.
There are currently four different variants of CACs. The Geneva Conventions Identification Card is the most common CAC and is given to active duty/reserve armed forces and uniformed service members. The Geneva Convention Accompany Forces Card is issued to emergency-essential civilian personnel. The ID and Privilege Common Access Card is for civilians residing on military installations. The ID card is for DOD/Government Agency identification for civilian employees.
Encryption
Until 2008, all CACs were encrypted using 1,024-bit encryption. Starting 2008, the DoD switched to 2,048-bit encryption. Personnel with the older CACs had to get new CACs by the deadline. On October 1, 2012, all certificates encrypted with less than 2,048-bits were placed on revocation status, rendering legacy CACs useless except for visual identification.Usage
The CAC is designed to providetwo-factor authentication
Multi-factor authentication (MFA; encompassing two-factor authentication, or 2FA, along with similar terms) is an electronic authentication method in which a user is granted access to a website or application only after successfully presenting ...
: what you have (the physical card) and what you know (the PIN
A pin is a device used for fastening objects or material together.
Pin or PIN may also refer to:
Computers and technology
* Personal identification number (PIN), to access a secured system
** PIN pad, a PIN entry device
* PIN, a former Dutch ...
). This CAC technology allows for rapid authentication, and enhanced physical and logical security. The card can be used in a variety of ways.
Visual identification
The CAC can be used for visual identification by way of matching the color photo with the owner. This is used for when the user passes through a guarded gate, or purchases items from a store, such as a PX/BX that require a level of privileges to use the facility. Some states allow the CAC to be used as a government-issued ID card, such as for voting or applying for a drivers license.Magnetic stripe
Themagnetic stripe
The term digital card can refer to a physical item, such as a memory card on a camera, or, increasingly since 2017, to the digital content hosted
as a virtual card or cloud card, as a digital virtual representation of a physical card. They share ...
can be read by swiping the card through a magnetic stripe reader, much like a credit card. The magnetic stripe is actually blank when the CAC is issued. However, its use is reserved for localized physical security systems. The magnetic stripe was removed first quarter 2018.
Integrated circuit chip (ICC)
The integrated circuit chip (ICC) contains information about the owner, including the PIN and one or morePKI PKI may refer to:
* Partai Komunis Indonesia, the Communist Party of Indonesia
* Peter Kiewit Institute, an Information Technology and Engineering school of the University of Nebraska system
* Protein kinase inhibitor, a type of enzyme inhibitor th ...
digital certificates. The ICC comes in different capacities, with the more recent versions issued at 64 and 144 kilobytes (KB).
The CAC can be used for access into computers and networks equipped with one or more of a variety of smartcard
A smart card, chip card, or integrated circuit card (ICC or IC card) is a physical electronic authentication device, used to control access to a resource. It is typically a plastic credit card-sized card with an embedded integrated circuit (IC) c ...
readers. Once inserted into the reader, the device asks the user for a PIN. Once the PIN is entered, the PIN is matched with the stored PIN on the CAC. If successful, the EDIPI number is read off the ID certificate on the card, and then sent to a processing system where the EDIPI number is matched with an access control system, such as Active Directory
Active Directory (AD) is a directory service developed by Microsoft for Windows domain networks. It is included in most Windows Server operating systems as a set of processes and services. Initially, Active Directory was used only for centr ...
or LDAP
The Lightweight Directory Access Protocol (LDAP ) is an open, vendor-neutral, industry standard application protocol for accessing and maintaining distributed directory information services over an Internet Protocol (IP) network. Directory serv ...
. The DoD standard is that after three incorrect PIN attempts, the chip on the CAC will lock.
The EDIPI number is stored in a PKI certificate. Depending on the owner, the CAC contains one or three PKI certificates. If the CAC is used for identification purposes only, an ID certificate is all that is needed. However, in order to access a computer, sign a document, or encrypt email, signature and encryption certificates are also required.
A CAC works in virtually all modern computer operating systems. Besides the reader, drivers and middleware are also required in order to read and process a CAC. The only approved Microsoft Windows middleware for CAC is ActivClient—available only to authorized DoD personnel. Other non-Windows alternatives include LPS-Public—a non-hard drive based solution.
DISA
Disa is the heroine of a Swedish legendary saga, which was documented by Olaus Magnus, in 1555. It is believed to be from the Middle Ages, but includes Old Norse themes.
It was elaborated by Johannes Messenius in his drama ''Disa'', which was t ...
now requires all DoD-based intranet sites to provide user authentication by way of a CAC in order to access the site. Authentication systems vary depending on the type of system, such as Active Directory
Active Directory (AD) is a directory service developed by Microsoft for Windows domain networks. It is included in most Windows Server operating systems as a set of processes and services. Initially, Active Directory was used only for centr ...
, RADIUS
In classical geometry, a radius ( : radii) of a circle or sphere is any of the line segments from its center to its perimeter, and in more modern usage, it is also their length. The name comes from the latin ''radius'', meaning ray but also the ...
, or other access control list
In computer security, an access-control list (ACL) is a list of permissions associated with a system resource (object). An ACL specifies which users or system processes are granted access to objects, as well as what operations are allowed on giv ...
.
CAC is based on X.509
In cryptography, X.509 is an International Telecommunication Union (ITU) standard defining the format of public key certificates. X.509 certificates are used in many Internet protocols, including TLS/SSL, which is the basis for HTTPS, the secur ...
certificates with software middleware enabling an operating system to interface with the card via a hardware card reader. Although card manufacturers such as Schlumberger
Schlumberger Limited (), doing business as SLB, is an oilfield services company. Schlumberger has four principal executive offices located in Paris, Houston, London, and The Hague.
Schlumberger is the world's largest offshore drilling comp ...
provided a suite of smartcard, hardware card reader and middleware for both Linux
Linux ( or ) is a family of open-source Unix-like operating systems based on the Linux kernel, an operating system kernel first released on September 17, 1991, by Linus Torvalds. Linux is typically packaged as a Linux distribution, which i ...
and Windows
Windows is a group of several proprietary graphical operating system families developed and marketed by Microsoft. Each family caters to a certain sector of the computing industry. For example, Windows NT for consumers, Windows Server for ...
, not all other CAC systems integrators did likewise. In an attempt to correct this situation, Apple
An apple is an edible fruit produced by an apple tree (''Malus domestica''). Apple trees are cultivated worldwide and are the most widely grown species in the genus '' Malus''. The tree originated in Central Asia, where its wild ances ...
Federal Systems has done work for adding some support for Common Access Cards to their later Snow Leopard operating system updates out of the box using the MUSCLE (Movement for the Use of Smartcards in a Linux Environment) project. The procedure for this was documented historically by the Naval Postgraduate School
The Naval Postgraduate School (NPS) is a public graduate school operated by the United States Navy and located in Monterey, California.
It offers master’s and doctoral degrees in more than 70 fields of study to the U.S. Armed Forces, DOD ci ...
in the publication "CAC on a Mac" although today the school uses commercial software. According to the independent military testers and help desks, not all cards are supported by the open source code associated with Apple's work, particularly the recent CACNG or CAC-NG PIV II CAC cards. Third party support for CAC Cards on the Mac are available from vendors such as Centrify and Thursby Software. Apple's Federal Engineering Management suggest not using the out-of-the-box support in Mac OS X 10.6 Snow Leopard but instead supported third party solutions. Mac OS X 10.7 Lion has no native smart card support. Thursby's PKard for iOS software extends CAC support to Apple iPads and iPhones. Some work has also been done in the Linux realm. Some users are using the MUSCLE project combined with Apple's Apple Public Source License
The Apple Public Source License (APSL) is the open-source and free software license under which Apple's Darwin operating system was released in 2000. A free and open-source software license was voluntarily adopted to further involve the communit ...
d Common Access Card software. Another approach to solve this problem, which is now well documented, involves the use of a new project, CoolKey, to gain Common Access Card functionality. This document is available publicly from the Naval Research Laboratory
The United States Naval Research Laboratory (NRL) is the corporate research laboratory for the United States Navy and the United States Marine Corps. It was founded in 1923 and conducts basic scientific research, applied research, technological ...
's Ocean Dynamics and Predictions Branch. The Software Protection Initiative offers a LiveCD
A live CD (also live DVD, live disc, or live operating system) is a complete bootable computer installation including operating system which runs directly from a CD-ROM or similar storage device into a computer's memory, rather than loading f ...
with CAC middleware and DoD certificate within a browser-focused, minimized Linux OS, called LPS-Public that works on x86 Windows, Mac, and Linux computers.
Bar codes
The CAC has two types of bar codes:PDF417
PDF417 is a stacked linear barcode format used in a variety of applications such as transport, identification cards, and inventory management. "PDF" stands for Portable Data File. The "417" signifies that each pattern in the code consists of 4 ...
in the front and Code 39
Code 39 (also known as Alpha39, Code 3 of 9, Code 3/9, Type 39, USS Code 39, or USD-3) is a variable length, discrete barcode symbology.
The Code 39 specification defines 43 characters, consisting of uppercase letters (A through Z), numeric digi ...
in the rear.
PDF417 Sponsor Barcode
PDF417 Dependent Barcode
RFID technology
There are also some security risks in RFID. To prevent theft of information in RFID, in November 2010, 2.5 million radio frequency shielding sleeves were delivered to the DoD, and another roughly 1.7 million more were to be delivered the following January 2011. RAPIDS ID offices worldwide are required to issue a sleeve with every CAC. When a CAC is placed in a holder along with other RFID cards, it can also cause problems, such as attempting to open a door with an access card when it is in the same holder as a CAC. Despite these challenges at least one civilian organization, NOAA, uses the RFID technology to access facilities nationwide. Access is usually granted after first removing the CAC from the RF shield and then holding it against a reader either mounted on a wall or located on a pedestal. Once the CAC is authenticated to a local security server either the door will release or a signal will be displayed to security guards to grant access to the facility.Common problems
The ICC is fragile and regular wear can make the card unusable. Older cards tend to de-laminate with repeated insertion/removal from readers, but this problem appears to be less significant with the newer ( PIV-compliant) cards. Also, the gold contacts on the ICC can become dirty and require cleaning with eithersolvents
A solvent (s) (from the Latin '' solvō'', "loosen, untie, solve") is a substance that dissolves a solute, resulting in a solution. A solvent is usually a liquid but can also be a solid, a gas, or a supercritical fluid. Water is a solvent for ...
or a rubber pencil eraser.
Fixing or replacing a CAC typically requires access to a RAPIDS
Rapids are sections of a river where the river bed has a relatively steep gradient, causing an increase in water velocity and turbulence.
Rapids are hydrological features between a ''run'' (a smoothly flowing part of a stream) and a ''cascade' ...
facility, causing some practical problems. In remote locations around the world without direct Internet access or physical access to a RAPIDS facility, a CAC is rendered useless if the card expires, or if the maximum number of re-tries of the PIN is reached. Based on the regulations for CAC use, a user on TAD / TDY must visit a RAPIDS facility to replace or unlock a CAC, usually requiring travel to another geographical location or even returning to one's home location. The CAC PMO/ref> has also created a CAC PIN Reset workstation capable of resetting a locked CAC PIN. For some DoD networks,
Active Directory
Active Directory (AD) is a directory service developed by Microsoft for Windows domain networks. It is included in most Windows Server operating systems as a set of processes and services. Initially, Active Directory was used only for centr ...
(AD) is used to authenticate users. Access to the computer's parent Active Directory is required when attempting to authenticate with a CAC for a given computer, for the first time. Use of, for example a field replaced laptop computer that was not prepared with the user's CAC before shipment would be impossible to use without some form of direct access to Active Directory beforehand. Other remedies include establishing contact with the intranet by using public broadband Internet and then VPN
A virtual private network (VPN) extends a private network across a public network and enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network. The be ...
to the intranet, or even satellite Internet access
Satellite Internet access is Internet access provided through communication satellites. Modern consumer grade satellite Internet service is typically provided to individual users through geostationary satellites that can offer relatively high d ...
via a VSAT
A very-small-aperture terminal (VSAT) is a two-way satellite ground station with a dish antenna that is smaller than 3.8 meters. The majority of VSAT antennas range from 75 cm to 1.2 m. Bit rates, in most cases, range from 4 kbit/s up to 16 ...
system when in locations where telecommunications is not available, such as in a natural disaster location.
See also
References
External links
* * * * *{{cite web, url=http://www.dmdc.osd.mil/rsl, website=dmdc.osd.mil, title= RAPIDS Site Locator Identity documents of the United States Smart cards United States Department of Defense publications