|
Magic Cookie
In computing, a magic cookie, or just cookie for short, is a token or short packet of data passed between communicating programs. The cookie is often used to identify a particular event or as "handle, transaction ID, or other token of agreement between cooperating programs". Usage Cookie data is typically not meaningful to the recipient program. The contents are opaque and not usually interpreted until the recipient passes the cookie data back to the sender or perhaps another program at a later time. In some cases, recipient programs are able to meaningfully compare two cookies for equality. The cookie can be used like a ticket. Early use The term ''magic cookie'' appears in the man page for the fseek routine in the C standard library, dating back at least to 1979, where it was stated: * "''ftell'' returns the current value of the offset relative to the beginning of the file associated with the named ''stream''. It is measured in bytes on UNIX; on some other systems it ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Computing
Computing is any goal-oriented activity requiring, benefiting from, or creating computer, computing machinery. It includes the study and experimentation of algorithmic processes, and the development of both computer hardware, hardware and software. Computing has scientific, engineering, mathematical, technological, and social aspects. Major computing disciplines include computer engineering, computer science, cybersecurity, data science, information systems, information technology, and software engineering. The term ''computing'' is also synonymous with counting and calculation, calculating. In earlier times, it was used in reference to the action performed by Mechanical computer, mechanical computing machines, and before that, to Computer (occupation), human computers. History The history of computing is longer than the history of computing hardware and includes the history of methods intended for pen and paper (or for chalk and slate) with or without the aid of tables. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Computer Program
A computer program is a sequence or set of instructions in a programming language for a computer to Execution (computing), execute. It is one component of software, which also includes software documentation, documentation and other intangible components. A ''computer program'' in its human-readable form is called source code. Source code needs another computer program to Execution (computing), execute because computers can only execute their native machine instructions. Therefore, source code may be Translator (computing), translated to machine instructions using a compiler written for the language. (Assembly language programs are translated using an Assembler (computing), assembler.) The resulting file is called an executable. Alternatively, source code may execute within an interpreter (computing), interpreter written for the language. If the executable is requested for execution, then the operating system Loader (computing), loads it into Random-access memory, memory and ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Event (computing)
In computing, an event is a detectable occurrence or change in the system's state, such as user input, hardware interrupts, system notifications, or changes in data or conditions, that the system is designed to monitor. Events trigger responses or actions and are fundamental to event-driven systems. These events can be handled synchronously, where the execution Thread (computing), thread is blocked until the event handler completes its processing, or asynchronously, where the event is processed independently, often through an event loop. Even when synchronous handling appears to block execution, the underlying mechanism in many systems is still asynchronous, managed by the event loop. Events can be implemented through various mechanisms such as Callback (computer programming), callbacks, message objects, signals, or interrupts, and events themselves are distinct from the implementation mechanisms used. Event propagation models, such as Event bubbling, bubbling, capturing, and pub/s ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Opaque Data Type
In computer science, an opaque data type is a data type whose concrete data structure is not defined in an interface. This enforces information hiding, since its values can only be manipulated by calling subroutines that have access to the missing information. The concrete representation of the type is hidden from its users, and the visible implementation is incomplete. A data type whose representation is visible is called transparent. Opaque data types are frequently used to implement abstract data types. Typical examples of opaque data types include handles for resources provided by an operating system to application software. For example, the POSIX standard for threads defines an application programming interface based on a number of opaque types that represent threads or synchronization primitives like mutexes or condition variables. An opaque pointer is a special case of an opaque data type, a datatype that is declared to be a pointer to a record or data structure ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Ticket (IT Security)
Kerberos () is a computer network, computer-network authentication cryptographic protocol, protocol that works on the basis of ''tickets'' to allow Node (networking), nodes communicating over a non-secure network to prove their identity to one another in a secure manner. Its designers aimed it primarily at a client–server model, and it provides mutual authentication—both the user and the server verify each other's identity. Kerberos protocol messages are protected against Computer insecurity#Eavesdropping, eavesdropping and replay attacks. Kerberos builds on symmetric-key cryptography and requires a trusted third party, and optionally may use public-key cryptography during certain phases of authentication.RFC 4556, abstract. Kerberos uses UDP port 88 by default. The protocol was named after the character ''cerberus, Kerberos'' (or ''Cerberus'') from Greek mythology, the ferocious three-headed guard dog of Hades. History and development The Massachusetts Institute of Technolog ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
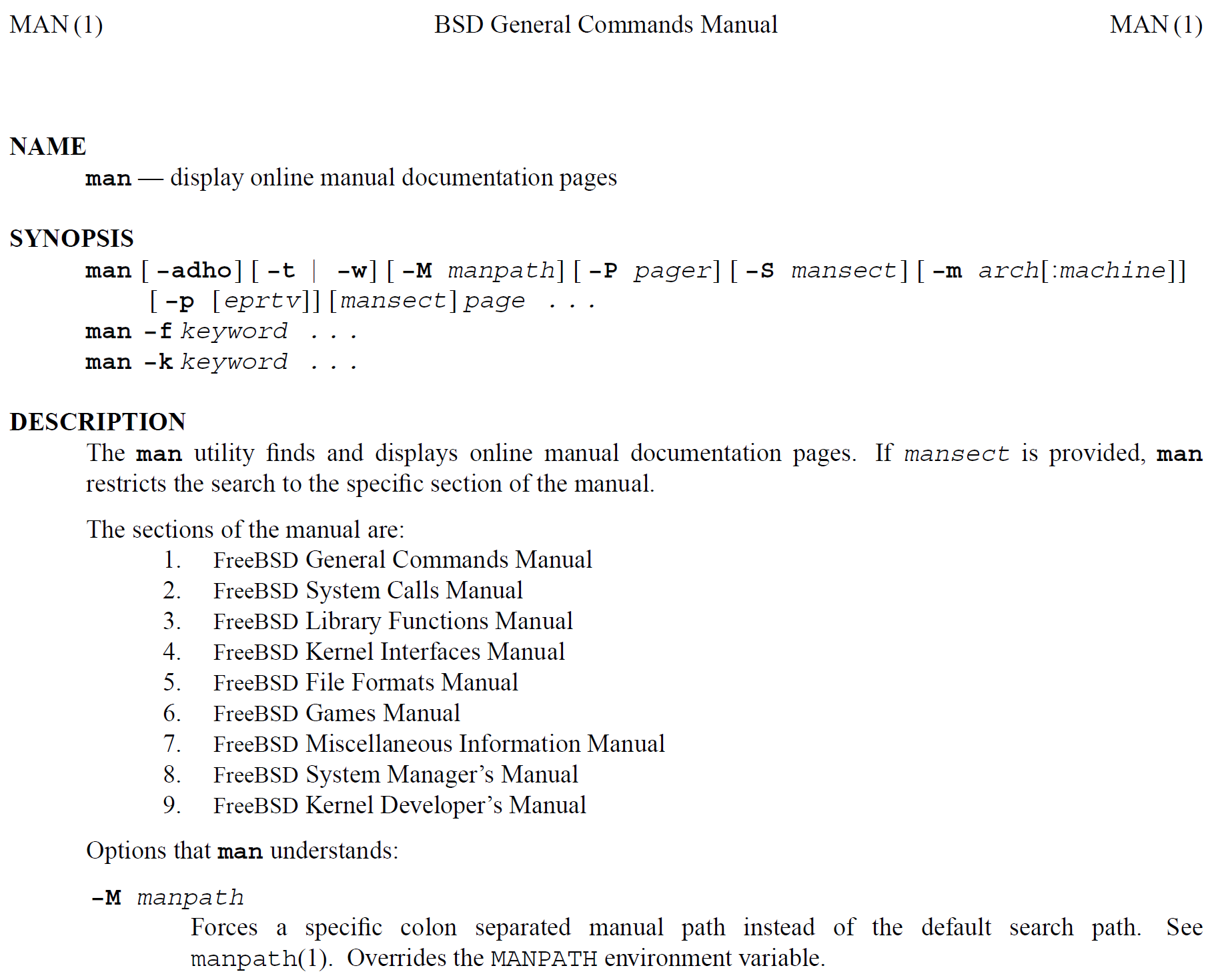
Man Page
A man page (short for manual page) is a form of software documentation found on Unix and Unix-like operating systems. Topics covered include programs, system libraries, system calls, and sometimes local system details. The local host administrators can create and install manual pages associated with the specific host. A manual end user may invoke a documentation page by issuing the man command followed by the name of the item for which they want the documentation. These manual pages are typically requested by end users, programmers and administrators doing real time work but can also be formatted for printing. By default, man typically uses a formatting program such as nroff with a macro package or mandoc, and also a terminal pager program such as more or less to display its output on the user's screen. Man pages are often referred to as an ''online'' form of software documentation, even though the man command does not require internet access. The environment variable M ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Fseek
The C (programming language), C programming language provides many standard library subroutine, functions for computer file, file input/output, input and output. These functions make up the bulk of the C standard library header file, header . The functionality descends from a "portable I/O package" written by Mike Lesk at Bell Labs in the early 1970s, and officially became part of the Unix operating system in Version 7 Unix, Version 7. The I/O functionality of C is fairly low-level by modern standards; C abstracts all file operations into operations on stream (computing), streams of bytes, which may be "input streams" or "output streams". Unlike some earlier programming languages, C has no direct support for random access, random-access data files; to read from a record in the middle of a file, the programmer must create a stream, fseek, seek to the middle of the file, and then read bytes in sequence from the stream. The stream model of file I/O was popularized by Unix, which was ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Cloakroom
A cloakroom, known as a coatroom and checkroom in North America, is a room for people to hang their coats, cloaks, canes, umbrellas, hats, or other outerwear when they enter a building. Cloakrooms are typically found inside large buildings, such as gymnasiums, schools, churches or meeting halls. In the UK, a cloakroom may also refer to a lavatory. In private homes, hatstands fulfill a similar function. Attendants Attended cloakrooms, or coat checks, are staffed rooms where coats and bags can be stored securely. Typically, a ticket or receipt is given to the customer, with a corresponding ticket attached to the garment or item. Coat checks are often found at the entrances to nightclubs, theaters, concert halls, larger restaurants, or museum A museum is an institution dedicated to displaying or Preservation (library and archive), preserving culturally or scientifically significant objects. Many museums have exhibitions of these objects on public display, and some have ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Real Life (reality)
Real life is a phrase used originally in literature to distinguish between the real world and fictional, virtual or idealized worlds, and in acting to distinguish between actors and the characters they portray. It has become a popular term on the Internet to describe events, people, activities, and interactions occurring offline; or otherwise not primarily through the medium of the Internet. It is also used as a metaphor to distinguish life in a vocational setting as opposed to an academic one, or adulthood and the adult world as opposed to childhood or adolescence. As distinct from fiction When used to distinguish from fictional worlds or universes against the consensus reality of the reader, the term has a long history: In her 1788 work, '' Original Stories from Real Life; with Conversations Calculated to Regulate the Affections, and Form the Mind to Truth and Goodness'', author Mary Wollstonecraft employs the term in her title, representing the work's focus on a middle-clas ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
HTTP Cookie
HTTP cookie (also called web cookie, Internet cookie, browser cookie, or simply cookie) is a small block of data (computing), data created by a web server while a user (computing), user is browsing a website and placed on the user's computer or other device by the user's web browser. Cookies are placed on the device used to access a website, and more than one cookie may be placed on a user's device during a session. Cookies serve useful and sometimes essential functions on the World Wide Web, web. They enable web servers to store program state, stateful information (such as items added in the shopping cart in an Online shopping, online store) on the user's device or to track the user's browsing activity (including clicking particular buttons, access control, logging in, or recording which Web browsing history, pages were visited in the past). They can also be used to save information that the user previously entered into Form (HTML), form fields, such as names, addresses, passw ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Website
A website (also written as a web site) is any web page whose content is identified by a common domain name and is published on at least one web server. Websites are typically dedicated to a particular topic or purpose, such as news, education, commerce, entertainment, or social media. Hyperlinking between web pages guides the navigation of the site, which often starts with a home page. The most-visited sites are Google, YouTube, and Facebook. All publicly-accessible websites collectively constitute the World Wide Web. There are also private websites that can only be accessed on a private network, such as a company's internal website for its employees. Users can access websites on a range of devices, including desktops, laptops, tablets, and smartphones. The app used on these devices is called a web browser. Background The World Wide Web (WWW) was created in 1989 by the British CERN computer scientist Tim Berners-Lee. On 30 April 1993, CERN announced that the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Authentication
Authentication (from ''authentikos'', "real, genuine", from αὐθέντης ''authentes'', "author") is the act of proving an Logical assertion, assertion, such as the Digital identity, identity of a computer system user. In contrast with identification, the act of indicating a person or thing's identity, authentication is the process of verifying that identity. Authentication is relevant to multiple fields. In art, antiques, and anthropology, a common problem is verifying that a given artifact was produced by a certain person, or in a certain place (i.e. to assert that it is not counterfeit), or in a given period of history (e.g. by determining the age via carbon dating). In computer science, verifying a user's identity is often required to allow access to confidential data or systems. It might involve validating personal identity documents. In art, antiques and anthropology Authentication can be considered to be of three types: The ''first'' type of authentication is accep ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |