|
Deniable Encryption
In cryptography and steganography, plausibly deniable encryption describes encryption techniques where the existence of an encrypted file or message is deniable in the sense that an adversary cannot prove that the plaintext data exists. The users may convincingly deny that a given piece of data is encrypted, or that they are able to decrypt a given piece of encrypted data, or that some specific encrypted data exists. Such denials may or may not be genuine. For example, it may be impossible to prove that the data is encrypted without the cooperation of the users. If the data is encrypted, the users genuinely may not be able to decrypt it. Deniable encryption serves to undermine an attacker's confidence either that data is encrypted, or that the person in possession of it can decrypt it and provide the associated plaintext. Function Deniable encryption makes it impossible to prove the existence of the plaintext message without the proper decryption key. This may be done by allowing ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptography
Cryptography, or cryptology (from grc, , translit=kryptós "hidden, secret"; and ''graphein'', "to write", or ''-logia'', "study", respectively), is the practice and study of techniques for secure communication in the presence of adversarial behavior. More generally, cryptography is about constructing and analyzing protocols that prevent third parties or the public from reading private messages. Modern cryptography exists at the intersection of the disciplines of mathematics, computer science, information security, electrical engineering, digital signal processing, physics, and others. Core concepts related to information security ( data confidentiality, data integrity, authentication, and non-repudiation) are also central to cryptography. Practical applications of cryptography include electronic commerce, chip-based payment cards, digital currencies, computer passwords, and military communications. Cryptography prior to the modern age was effectively synonymo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptographically Secure Pseudorandom Number Generator
A cryptographically secure pseudorandom number generator (CSPRNG) or cryptographic pseudorandom number generator (CPRNG) is a pseudorandom number generator (PRNG) with properties that make it suitable for use in cryptography. It is also loosely known as a cryptographic random number generator (CRNG) (see Random number generation § "True" vs. pseudo-random numbers). Most cryptographic applications require random numbers, for example: * key generation * nonces * salts in certain signature schemes, including ECDSA, RSASSA-PSS The "quality" of the randomness required for these applications varies. For example, creating a nonce in some protocols needs only uniqueness. On the other hand, the generation of a master key requires a higher quality, such as more entropy. And in the case of one-time pads, the information-theoretic guarantee of perfect secrecy only holds if the key material comes from a true random source with high entropy, and thus any kind of pseudorandom number gen ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
BestCrypt
BestCrypt, developed bJetico is a commercial disk encryption app available for Windows, Linux, macOS and Android. BestCrypt comes in two editions: BestCrypt Volume Encryption to encrypt entire disk volumes; BestCrypt Container Encryption to encrypt virtual disks stored as computer files. BestCrypt also provides the complimentary data erasure utility BCWipe. Cryptographic Algorithms BestCrypt supports a wide variety of block cipher algorithms including AES, Serpent, Blowfish, Twofish, DES, Triple DES, GOST 28147-89. All ciphers support CBC and LRW modes of operation while AES, Twofish and Serpent also support XTS mode. Features * Create and mount a virtual drive encrypted using AES, Blowfish, Twofish, CAST-128 and various other encryption methods. BestCrypt v.8 and higher can alternatively mount a subfolder on a NTFS disk instead of a drive. Encrypted virtual disk images are compatible across Windows, Linux and Mac OS X. * Encrypt a set of files into a single, sel ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
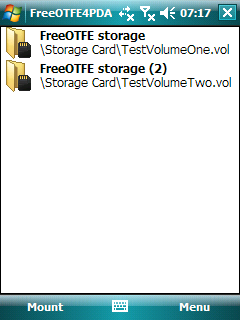
LibreCrypt
FreeOTFE is a discontinued open source computer program for on-the-fly disk encryption (OTFE). On Microsoft Windows, and Windows Mobile (using FreeOTFE4PDA), it can create a virtual drive within a file or partition, to which anything written is automatically encrypted before being stored on a computer's hard or USB drive. It is similar in function to other disk encryption programs including TrueCrypt and Microsoft's BitLocker. The author, Sarah Dean, went absent as of 2011. The FreeOTFE website is unreachable as of June 2013 and the domain name is now registered by a domain squatter. The original program can be downloaded froa mirror at Sourceforge In June 2014, a fork of the project now named LibreCrypt appeared on GitHub. Overview ''FreeOTFE'' was initially released by Sarah Dean in 2004, and was the first open source code disk encryption system that provided a modular architecture allowing 3rd parties to implement additional algorithms if needed. Older FreeOTFE licensing ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
GitHub
GitHub, Inc. () is an Internet hosting service for software development and version control using Git. It provides the distributed version control of Git plus access control, bug tracking, software feature requests, task management, continuous integration, and wikis for every project. Headquartered in California, it has been a subsidiary of Microsoft since 2018. It is commonly used to host open source software development projects. As of June 2022, GitHub reported having over 83 million developers and more than 200 million repositories, including at least 28 million public repositories. It is the largest source code host . History GitHub.com Development of the GitHub.com platform began on October 19, 2007. The site was launched in April 2008 by Tom Preston-Werner, Chris Wanstrath, P. J. Hyett and Scott Chacon after it had been made available for a few months prior as a beta release. GitHub has an annual keynote called GitHub Universe. Organizat ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Volume (computing)
In computer data storage, a volume or logical drive is a single accessible storage area with a single file system, typically (though not necessarily) resident on a single partition of a hard disk. Although a volume might be different from a physical disk drive, it can still be accessed with an operating system's logical interface. However, a volume differs from a partition. Differences from partition A volume is not the same thing as a partition. For example, a floppy disk might be accessible as a volume, even though it does not contain a partition, as floppy disks cannot be partitioned with most modern computer software. Also, an OS can recognize a partition without recognizing any volume associated with it, as when the OS cannot interpret the filesystem stored there. This situation occurs, for example, when Windows NT-based OSes encounter disks with non-Microsoft OS partitions, such as the ext3 filesystem commonly used with Linux. Another example occurs in the Intel world w ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Disk Encryption Software
Disk encryption software is computer security software that protects the confidentiality of data stored on computer media (e.g., a hard disk, floppy disk, or USB device) by using disk encryption. Compared to access controls commonly enforced by an operating system (OS), encryption passively protects data confidentiality even when the OS is not active, for example, if data is read directly from the hardware or by a different OS. In addition crypto-shredding suppresses the need to erase the data at the end of the disk's lifecycle. Disk encryption generally refers to wholesale encryption that operates on an entire volume mostly transparently to the user, the system, and applications. This is generally distinguished from file-level encryption that operates by user invocation on a single file or group of files, and which requires the user to decide which specific files should be encrypted. Disk encryption usually includes all aspects of the disk, including directories, so that an a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Timestamp
A timestamp is a sequence of characters or encoded information identifying when a certain event occurred, usually giving date and time of day, sometimes accurate to a small fraction of a second. Timestamps do not have to be based on some absolute notion of time, however. They can have any epoch, can be relative to any arbitrary time, such as the power-on time of a system, or to some arbitrary time in the past. The term "timestamp" derives from rubber stamps used in offices to stamp the current date, and sometimes time, in ink on paper documents, to record when the document was received. Common examples of this type of timestamp are a postmark on a letter or the "in" and "out" times on a time card. In modern times usage of the term has expanded to refer to digital date and time information attached to digital data. For example, computer files contain timestamps that tell when the file was last modified, and digital cameras add timestamps to the pictures they take, recordin ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptographic Hash Function
A cryptographic hash function (CHF) is a hash algorithm (a map of an arbitrary binary string to a binary string with fixed size of n bits) that has special properties desirable for cryptography: * the probability of a particular n-bit output result (hash value) for a random input string ("message") is 2^ (like for any good hash), so the hash value can be used as a representative of the message; * finding an input string that matches a given hash value (a ''pre-image'') is unfeasible, unless the value is selected from a known pre-calculated dictionary (" rainbow table"). The ''resistance'' to such search is quantified as security strength, a cryptographic hash with n bits of hash value is expected to have a ''preimage resistance'' strength of n bits. A ''second preimage'' resistance strength, with the same expectations, refers to a similar problem of finding a second message that matches the given hash value when one message is already known; * finding any pair of different messa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Randomness
In common usage, randomness is the apparent or actual lack of pattern or predictability in events. A random sequence of events, symbols or steps often has no order and does not follow an intelligible pattern or combination. Individual random events are, by definition, unpredictable, but if the probability distribution is known, the frequency of different outcomes over repeated events (or "trials") is predictable.Strictly speaking, the frequency of an outcome will converge almost surely to a predictable value as the number of trials becomes arbitrarily large. Non-convergence or convergence to a different value is possible, but has probability zero. For example, when throwing two dice, the outcome of any particular roll is unpredictable, but a sum of 7 will tend to occur twice as often as 4. In this view, randomness is not haphazardness; it is a measure of uncertainty of an outcome. Randomness applies to concepts of chance, probability, and information entropy. The fields o ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Chaff (radar Countermeasure)
Chaff, originally called Window by the British and ''Düppel'' by the Second World War era German Luftwaffe (from the Berlin suburb where it was first developed), is a radar countermeasure in which aircraft or other targets spread a cloud of small, thin pieces of aluminium, metallized glass fibre or plastic, which either appears as a cluster of primary targets on radar screens or swamps the screen with multiple returns, in order to confuse and distract. Modern armed forces use chaff (in naval applications, for instance, using short-range SRBOC rockets) to distract radar-guided missiles from their targets. Most military aircraft and warships have chaff dispensing systems for self-defense. An intercontinental ballistic missile may release in its midcourse phase several independent warheads as well as penetration aids such as decoy balloons and chaff. Modern radar systems can distinguish chaff from target objects by measuring the Doppler shift; chaff quickly loses speed compared t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |