|
Whirlpool (algorithm)
In computer science and cryptography, Whirlpool (sometimes styled WHIRLPOOL) is a cryptographic hash function. It was designed by Vincent Rijmen (co-creator of the Advanced Encryption Standard) and Paulo S. L. M. Barreto, who first described it in 2000. The hash has been recommended by the NESSIE project. It has also been adopted by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC) as part of the joint ISO/IEC 10118-3 international standard. Design features Whirlpool is a hash designed after the Square block cipher, and is considered to be in that family of block cipher functions. Whirlpool is a Miyaguchi-Preneel construction based on a substantially modified Advanced Encryption Standard (AES). Whirlpool takes a message of any length less than 2256 bits and returns a 512-bit message digest. The authors have declared that :"WHIRLPOOL is not (and will never be) patented. It may be used free of charge for ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Vincent Rijmen
Vincent Rijmen (; born 16 October 1970) is a Belgian cryptographer and one of the two designers of the Rijndael, the Advanced Encryption Standard. Rijmen is also the co-designer of the WHIRLPOOL cryptographic hash function, and the block ciphers Anubis, KHAZAD, Square, NOEKEON and SHARK. In 1993, Rijmen obtained a degree in electronics engineering at the Katholieke Universiteit Leuven. Afterwards, he was a PhD student at the ESAT/ COSIC lab of the K.U.Leuven. In 1997, Rijmen finished his doctoral dissertation titled ''Cryptanalysis and design of iterated block ciphers''. After his PhD he did postdoctoral work at the COSIC lab, on several occasions collaborating with Joan Daemen. One of their joint projects resulted in the algorithm Rijndael, which in October 2000 was selected by the National Institute for Standards and Technology (NIST) to become the Advanced Encryption Standard (AES). Since 1 August 2001, Rijmen has been working as chief cryptographer at Cryptomat ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
S-box
In cryptography, an S-box (substitution-box) is a basic component of symmetric key algorithms which performs substitution. In block ciphers, they are typically used to obscure the relationship between the key and the ciphertext, thus ensuring Shannon's property of confusion. Mathematically, an S-box is a vectorial Boolean function. In general, an S-box takes some number of input bits, ''m'', and transforms them into some number of output bits, ''n'', where ''n'' is not necessarily equal to ''m''. An ''m''×''n'' S-box can be implemented as a lookup table with 2''m'' words of ''n'' bits each. Fixed tables are normally used, as in the Data Encryption Standard (DES), but in some ciphers the tables are generated dynamically from the key (e.g. the Blowfish and the Twofish encryption algorithms). Example One good example of a fixed table is the S-box from DES (S5), mapping 6-bit input into a 4-bit output: Given a 6-bit input, the 4-bit output is found by selecting the row using ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
TrueCrypt
TrueCrypt is a discontinued source-available freeware utility used for on-the-fly encryption (OTFE). It can create a virtual encrypted disk within a file, or encrypt a partition or the whole storage device ( pre-boot authentication). On 28 May 2014, the TrueCrypt website announced that the project was no longer maintained and recommended users find alternative solutions. Though development of TrueCrypt has ceased, an independent audit of TrueCrypt (published in March 2015) has concluded that no significant flaws are present. Two projects forked from TrueCrypt: VeraCrypt (active) and CipherShed (abandoned). History TrueCrypt was initially released as version 1.0 in February 2004, based on E4M (Encryption for the Masses). Several versions and many additional minor releases have been made since then, with the most current version being 7.1a. E4M and SecurStar dispute Original release of TrueCrypt was made by anonymous developers called "the TrueCrypt Team". Shortly af ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
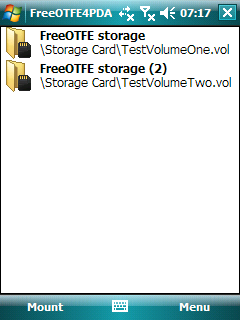
FreeOTFE
FreeOTFE is a discontinued open source computer program for on-the-fly disk encryption (OTFE). On Microsoft Windows, and Windows Mobile (using FreeOTFE4PDA), it can create a virtual drive within a file or partition, to which anything written is automatically encrypted before being stored on a computer's hard or USB drive. It is similar in function to other disk encryption programs including TrueCrypt and Microsoft's BitLocker. The author, Sarah Dean, went absent as of 2011. The FreeOTFE website is unreachable as of June 2013 and the domain name is now registered by a domain squatter. The original program can be downloaded froa mirror at Sourceforge In June 2014, a fork of the project now named LibreCrypt appeared on GitHub. Overview ''FreeOTFE'' was initially released by Sarah Dean in 2004, and was the first open source code disk encryption system that provided a modular architecture allowing 3rd parties to implement additional algorithms if needed. Older FreeOTFE licensi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Java (programming Language)
Java is a high-level, class-based, object-oriented programming language that is designed to have as few implementation dependencies as possible. It is a general-purpose programming language intended to let programmers ''write once, run anywhere'' ( WORA), meaning that compiled Java code can run on all platforms that support Java without the need to recompile. Java applications are typically compiled to bytecode that can run on any Java virtual machine (JVM) regardless of the underlying computer architecture. The syntax of Java is similar to C and C++, but has fewer low-level facilities than either of them. The Java runtime provides dynamic capabilities (such as reflection and runtime code modification) that are typically not available in traditional compiled languages. , Java was one of the most popular programming languages in use according to GitHub, particularly for client–server web applications, with a reported 9 million developers. Java was originally de ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
C (programming Language)
C (''pronounced like the letter c'') is a General-purpose language, general-purpose computer programming language. It was created in the 1970s by Dennis Ritchie, and remains very widely used and influential. By design, C's features cleanly reflect the capabilities of the targeted CPUs. It has found lasting use in operating systems, device drivers, protocol stacks, though decreasingly for application software. C is commonly used on computer architectures that range from the largest supercomputers to the smallest microcontrollers and embedded systems. A successor to the programming language B (programming language), B, C was originally developed at Bell Labs by Ritchie between 1972 and 1973 to construct utilities running on Unix. It was applied to re-implementing the kernel of the Unix operating system. During the 1980s, C gradually gained popularity. It has become one of the measuring programming language popularity, most widely used programming languages, with C compilers avail ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Reference Implementation
In the software development process, a reference implementation (or, less frequently, sample implementation or model implementation) is a program that implements all requirements from a corresponding specification. The reference implementation often accompanies a technical standard, and demonstrates what should be considered the "correct" behavior of any other implementation of it. Characteristics and examples Reference implementations of algorithms, for instance cryptographic algorithms, are often the result or the input of standardization processes. In this function they are often dedicated to the public domain with their source code as public domain software. Examples are the first CERN's httpd, Serpent cipher, base64 variants, and SHA-3. The Openwall Project maintains a list of several algorithms with their reference source code in the public domain. A reference implementation may or may not be production quality. For example, the Fraunhofer reference implementation ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Clustering Illusion
The clustering illusion is the tendency to erroneously consider the inevitable "streaks" or "clusters" arising in small samples from random distributions to be non-random. The illusion is caused by a human tendency to underpredict the amount of variability likely to appear in a small sample of random or pseudorandom data. Examples Thomas Gilovich, an early author on the subject, argued that the effect occurs for different types of random dispersions, including two-dimensional data such as clusters in the locations of impact of World War II V-1 flying bombs on maps of London; or seeing patterns in stock market price fluctuations over time. Although Londoners developed specific theories about the pattern of impacts within London, a statistical analysis by R. D. Clarke originally published in 1946 showed that the impacts of V-2 rockets on London were a close fit to a random distribution. Similar biases Using this cognitive bias in causal reasoning may result in the Texas sharp ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
The Quick Brown Fox Jumps Over The Lazy Dog
"The quick brown fox jumps over the lazy dog" is an English-language pangram — a sentence that contains all the letters of the alphabet. The phrase is commonly used for touch-typing practice, testing typewriters and computer keyboards, displaying examples of fonts, and other applications involving text where the use of all letters in the alphabet is desired. History The earliest known appearance of the phrase was in '' The Boston Journal''. In an article titled "Current Notes" in the February 9, 1885, edition, the phrase is mentioned as a good practice sentence for writing students: "A favorite copy set by writing teachers for their pupils is the following, because it contains every letter of the alphabet: 'A quick brown fox jumps over the lazy dog.'" Dozens of other newspapers published the phrase over the next few months, all using the version of the sentence starting with "A" rather than "The". The earliest known use of the phrase starting with "The" is from the 1888 bo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
ASCII
ASCII ( ), abbreviated from American Standard Code for Information Interchange, is a character encoding standard for electronic communication. ASCII codes represent text in computers, telecommunications equipment, and other devices. Because of technical limitations of computer systems at the time it was invented, ASCII has just 128 code points, of which only 95 are , which severely limited its scope. All modern computer systems instead use Unicode, which has millions of code points, but the first 128 of these are the same as the ASCII set. The Internet Assigned Numbers Authority (IANA) prefers the name US-ASCII for this character encoding. ASCII is one of the IEEE milestones. Overview ASCII was developed from telegraph code. Its first commercial use was as a seven-bit teleprinter code promoted by Bell data services. Work on the ASCII standard began in May 1961, with the first meeting of the American Standards Association's (ASA) (now the American National Standards I ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hexadecimal
In mathematics and computing, the hexadecimal (also base-16 or simply hex) numeral system is a positional numeral system that represents numbers using a radix (base) of 16. Unlike the decimal system representing numbers using 10 symbols, hexadecimal uses 16 distinct symbols, most often the symbols "0"–"9" to represent values 0 to 9, and "A"–"F" (or alternatively "a"–"f") to represent values from 10 to 15. Software developers and system designers widely use hexadecimal numbers because they provide a human-friendly representation of binary-coded values. Each hexadecimal digit represents four bits (binary digits), also known as a nibble (or nybble). For example, an 8-bit byte can have values ranging from 00000000 to 11111111 in binary form, which can be conveniently represented as 00 to FF in hexadecimal. In mathematics, a subscript is typically used to specify the base. For example, the decimal value would be expressed in hexadecimal as . In programming, a number ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Exclusive Or
Exclusive or or exclusive disjunction is a logical operation that is true if and only if its arguments differ (one is true, the other is false). It is symbolized by the prefix operator J and by the infix operators XOR ( or ), EOR, EXOR, , , , , , and . The negation of XOR is the logical biconditional, which yields true if and only if the two inputs are the same. It gains the name "exclusive or" because the meaning of "or" is ambiguous when both operands are true; the exclusive or operator ''excludes'' that case. This is sometimes thought of as "one or the other but not both". This could be written as "A or B, but not, A and B". Since it is associative, it may be considered to be an ''n''-ary operator which is true if and only if an odd number of arguments are true. That is, ''a'' XOR ''b'' XOR ... may be treated as XOR(''a'',''b'',...). Truth table The truth table of A XOR B shows that it outputs true whenever the inputs differ: Equivalences, elimination, and introd ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |