|
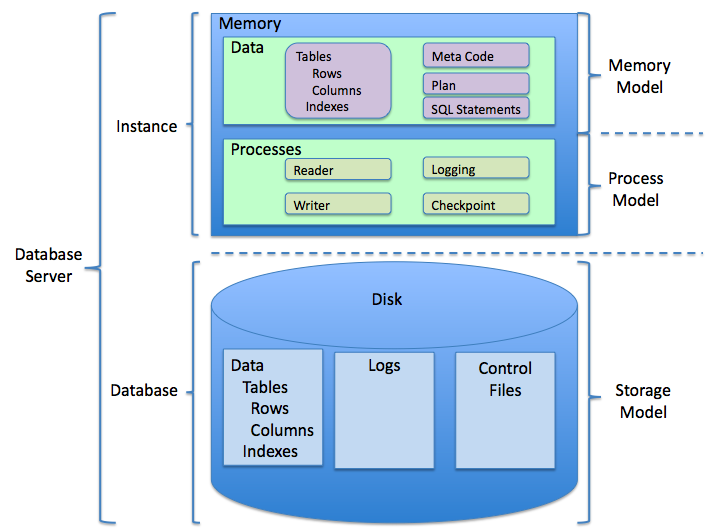
Unisys OS 2200 Databases
{{Short description, Aspect of Unisys OS 2200 operating system The OS 2200 database managers are all part of the Universal Data System (UDS). UDS provides a common control structure for multiple different data models. Flat files (sequential, multi-keyed indexed sequential – MSAM, and fixed-block), network (DMS), and relational (RDMS) data models all share a common locking, recovery, and clustering mechanism. OS 2200 applications can use any mixtures of these data models along with the high-volume transaction file system within the same program while retaining a single common recovery mechanism. The database managers are implemented as a protected subsystem and are called as a procedure from user programs and other subsystems. The implementation as a subsystem means that there is no upper limit to the potential concurrency of activities (threads) executing in the database manager. The thread of each user executes the database manager code but within its protection domain s ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Unisys OS 2200 Operating System
OS 2200 is the operating system for the Unisys ClearPath Dorado family of mainframe systems. The operating system kernel of OS 2200 is a lineal descendant of Exec 8 for the UNIVAC 1108. Documentation and other information on current and past Unisys systems can be found on the Unisys public support website.Current Unisys documentation is available on thUnisys public support web site For OS 2200 products, select one of the ClearPath Dorado platforms (e.g., Dorado 800 or Dorado 8300) and then the release level (usually the highest numbered one unless you are looking for something specific in an earlier release). That will take you to a search page where you can search by title or document content. See Unisys 2200 Series system architecture for a description of the machine architecture and its relationship to the OS 2200 operating system. Unisys stopped producing ClearPath Dorado hardware in the early 2010s, and the operating system is now run under emulation. History There we ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Network Model
The network model is a database model conceived as a flexible way of representing objects and their relationships. Its distinguishing feature is that the schema, viewed as a graph in which object types are nodes and relationship types are arcs, is not restricted to being a hierarchy or lattice. The network model was adopted by the CODASYL Data Base Task Group in 1969 and underwent a major update in 1971. It is sometimes known as the CODASYL model for this reason. A number of network database systems became popular on mainframe and minicomputers through the 1970s before being widely replaced by relational databases in the 1980s. Overview While the hierarchical database model structures data as a tree of records, with each record having one parent record and many children, the network model allows each record to have multiple parent and child records, forming a generalized graph structure. This property applies at two levels: the schema is a generalized graph of record types ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Relational Database
A relational database is a (most commonly digital) database based on the relational model of data, as proposed by E. F. Codd in 1970. A system used to maintain relational databases is a relational database management system (RDBMS). Many relational database systems are equipped with the option of using the SQL (Structured Query Language) for querying and maintaining the database. History The term "relational database" was first defined by E. F. Codd at IBM in 1970. Codd introduced the term in his research paper "A Relational Model of Data for Large Shared Data Banks". In this paper and later papers, he defined what he meant by "relational". One well-known definition of what constitutes a relational database system is composed of Codd's 12 rules. However, no commercial implementations of the relational model conform to all of Codd's rules, so the term has gradually come to describe a broader class of database systems, which at a minimum: # Present the data to the user as rel ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Java Database Connectivity
Java Database Connectivity (JDBC) is an application programming interface (API) for the programming language Java, which defines how a client may access a database. It is a Java-based data access technology used for Java database connectivity. It is part of the Java Standard Edition platform, from Oracle Corporation. It provides methods to query and update data in a database, and is oriented toward relational databases. A JDBC-to-ODBC bridge enables connections to any ODBC-accessible data source in the Java virtual machine (JVM) host environment. History and implementation Sun Microsystems released JDBC as part of Java Development Kit (JDK) 1.1 on February 19, 1997. Since then it has been part of the Java Platform, Standard Edition (Java SE). The JDBC classes are contained in the Java package and . Starting with version 3.1, JDBC has been developed under the Java Community Process. JSR 54 specifies JDBC 3.0 (included in J2SE 1.4), JSR 114 specifies the JDBC Rowset additions, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
OLE DB
OLE DB (''Object Linking and Embedding, Database'', sometimes written as OLEDB or OLE-DB), an API designed by Microsoft, allows accessing data from a variety of sources in a uniform manner. The API provides a set of interfaces implemented using the Component Object Model (COM); it is otherwise unrelated to OLE. Microsoft originally intended OLE DB as a higher-level replacement for, and successor to, ODBC, extending its feature set to support a wider variety of non-relational databases, such as object databases and spreadsheets that do not necessarily implement. Methodology OLE DB separates the data store from the application that needs access to it through a set of abstractions that include the datasource, session, command, and rowsets. This was done because different applications need access to different types and sources of data, and do not necessarily want to know how to access functionality with technology-specific methods. OLE DB is conceptually divided into ''consumers ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Open Database Connectivity
In computing, Open Database Connectivity (ODBC) is a standard application programming interface (API) for accessing database management systems (DBMS). The designers of ODBC aimed to make it independent of database systems and operating systems. An application written using ODBC can be ported to other platforms, both on the client and server side, with few changes to the data access code. ODBC accomplishes DBMS independence by using an ''ODBC driver'' as a translation layer between the application and the DBMS. The application uses ODBC functions through an ''ODBC driver manager'' with which it is linked, and the driver passes the query to the DBMS. An ODBC driver can be thought of as analogous to a printer driver or other driver, providing a standard set of functions for the application to use, and implementing DBMS-specific functionality. An application that can use ODBC is referred to as "ODBC-compliant". Any ODBC-compliant application can access any DBMS for which a driver i ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
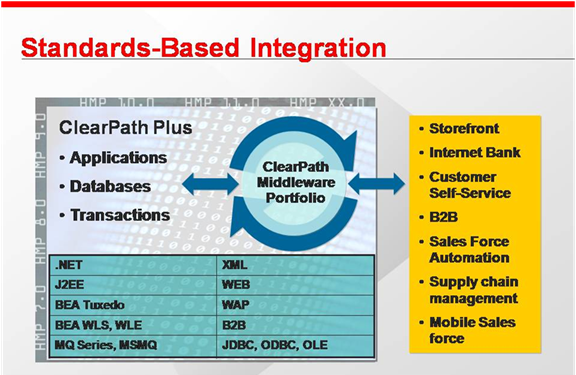
Unisys OS 2200 Distributed Processing
OS 2200 supports all commonly used, and many not so commonly used, distributed processing protocols, APIs, and development technology. The X/Open Distributed Transaction Processing model and standards are the basis for much of the OS 2200 capability.Unisys Corporation (2000). Open Distributed Transaction Processing Getting Started. (Unisys publication 7833 5007). Roseville, MN. http://public.support.unisys.com/2200/docs/cp14.0/pdf/78335007-007.pdf Full support for the X/Open XA APIs including two-phase commit are built into transaction middleware, the database managers, and even clustering. The J2EE model is also fully supported. It uses the XA capabilities of the system but provides the J2EE APIs and protocols. IBM WebSphere MQ (AKA MQSeries), MSMQ,Unisys Corporation (2013). ClearPath OS 2200 Interface for Microsoft Message Queuing Help. (Unisys publication 6885 2722). Roseville, MN. http://public.support.unisys.com/2200/docs/cp14.0/chm/68852722-003/68852722-003.chm and ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Journal (computing)
In the field of databases in computer science, a transaction log (also transaction journal, database log, binary log or audit trail) is a history of actions executed by a database management system used to guarantee ACID properties over crashes or hardware failures. Physically, a log is a file listing changes to the database, stored in a stable storage format. If, after a start, the database is found in an inconsistent state or not been shut down properly, the database management system reviews the database logs for uncommitted transactions and rolls back the changes made by these transactions. Additionally, all transactions that are already committed but whose changes were not yet materialized in the database are re-applied. Both are done to ensure atomicity and durability of transactions. This term is not to be confused with other, human-readable logs that a database management system usually provides. In database management systems, a journal is the record of data alter ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Audit Trail
An audit trail (also called audit log) is a security-relevant chronological record, set of records, and/or destination and source of records that provide documentary evidence of the sequence of activities that have affected at any time a specific operation, procedure, event, or device. Audit records typically result from activities such as financial transactions, scientific research and health care data transactions, or communications by individual people, systems, accounts, or other entities. The process that creates an audit trail is typically required to always run in a privileged mode, so it can access and supervise all actions from all users; a normal user should not be allowed to stop/change it. Furthermore, for the same reason, the trail file or database table with a trail should not be accessible to normal users. Another way of handling this issue is through the use of a role-based security model in the software. The software can operate with the closed-looped controls, or ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |