|
String Intern Pool
In computer science, string interning is a method of storing only one copy of each distinct string value, which must be immutable. Interning strings makes some string processing tasks more time- or space-efficient at the cost of requiring more time when the string is created or interned. The distinct values are stored in a string intern pool. The single copy of each string is called its ''intern'' and is typically looked up by a method of the string class, for example String.intern() in Java. All compile-time constant strings in Java are automatically interned using this method. String interning is supported by some modern object-oriented programming languages, including Java, Python, PHP (since 5.4), Lua and .NET languages. Lisp, Scheme, Julia, Ruby and Smalltalk are among the languages with a symbol type that are basically interned strings. The library of the Standard ML of New Jersey contains an atom type that does the same thing. Objective-C's selectors, which are mainly us ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
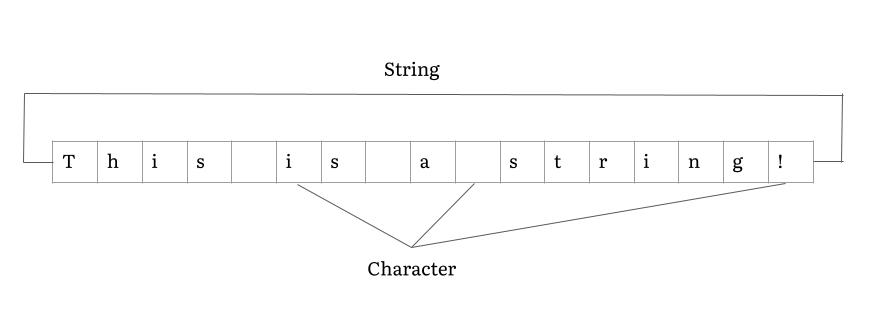
String (computer Science)
In computer programming, a string is traditionally a sequence of characters, either as a literal constant or as some kind of variable. The latter may allow its elements to be mutated and the length changed, or it may be fixed (after creation). A string is generally considered as a data type and is often implemented as an array data structure of bytes (or words) that stores a sequence of elements, typically characters, using some character encoding. ''String'' may also denote more general arrays or other sequence (or list) data types and structures. Depending on the programming language and precise data type used, a variable declared to be a string may either cause storage in memory to be statically allocated for a predetermined maximum length or employ dynamic allocation to allow it to hold a variable number of elements. When a string appears literally in source code, it is known as a string literal or an anonymous string. In formal languages, which are used in mathemati ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Primitive Wrapper Class
In object-oriented programming, a wrapper class is a class that encapsulates types, so that those types can be used to create object instances and methods in another class that needs those types. So a primitive wrapper class is a wrapper class that encapsulates, hides or ''wraps'' data types from the eight primitive data types, so that these can be used to create instantiated objects with methods in another class or in other classes.J. Murach, ''Murach's Java Programming'', 4th Edition, Mike Murach and Associates, Inc., 2011. The primitive wrapper classes are found in the Java API. Primitive wrapper classes are used to create an that needs to represent primitive types in classes (i.e., in the Java API), in the package and in the reflection package. Collection classes are Java API-defined classes that can store objects in a manner similar to how data structures like arrays store primitive data types like int, double, long or char, etc., but arrays store primitive data t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Double-checked Locking
In software engineering, double-checked locking (also known as "double-checked locking optimization") is a software design pattern used to reduce the overhead of acquiring a lock by testing the locking criterion (the "lock hint") before acquiring the lock. Locking occurs only if the locking criterion check indicates that locking is required. The pattern, when implemented in some language/hardware combinations, can be unsafe. At times, it can be considered an anti-pattern.David Bacon et alThe "Double-Checked Locking is Broken" Declaration It is typically used to reduce locking overhead when implementing "lazy initialization" in a multi-threaded environment, especially as part of the Singleton pattern. Lazy initialization avoids initializing a value until the first time it is accessed. Usage in C++11 For the singleton pattern, double-checked locking is not needed: Singleton& GetInstance() C++11 and beyond also provide a built-in double-checked locking pattern in the form of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Multithreading (software)
In computer science, a thread of execution is the smallest sequence of programmed instructions that can be managed independently by a scheduler, which is typically a part of the operating system. The implementation of threads and processes differs between operating systems. In Modern Operating Systems, Tanenbaum shows that many distinct models of process organization are possible.TANENBAUM, Andrew S. Modern Operating Systems. 1992. Prentice-Hall International Editions, ISBN 0-13-595752-4. In many cases, a thread is a component of a process. The multiple threads of a given process may be executed concurrently (via multithreading capabilities), sharing resources such as memory, while different processes do not share these resources. In particular, the threads of a process share its executable code and the values of its dynamically allocated variables and non- thread-local global variables at any given time. History Threads made an early appearance under the name of "task ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Protocol (computing)
A communication protocol is a system of rules that allows two or more entities of a communications system to transmit information via any kind of variation of a physical quantity. The protocol defines the rules, syntax, semantics and synchronization of communication and possible error recovery methods. Protocols may be implemented by hardware, software, or a combination of both. Communicating systems use well-defined formats for exchanging various messages. Each message has an exact meaning intended to elicit a response from a range of possible responses pre-determined for that particular situation. The specified behavior is typically independent of how it is to be implemented. Communication protocols have to be agreed upon by the parties involved. To reach an agreement, a protocol may be developed into a technical standard. A programming language describes the same for computations, so there is a close analogy between protocols and programming languages: ''protocols are to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Magic Number (programming)
In computer programming, a magic number is any of the following: * A unique value with unexplained meaning or multiple occurrences which could (preferably) be replaced with a named constant * A constant numerical or text value used to identify a file format or protocol; for files, see List of file signatures * A distinctive unique value that is unlikely to be mistaken for other meanings (e.g., Globally Unique Identifiers) Unnamed numerical constants The term ''magic number'' or ''magic constant'' refers to the anti-pattern of using numbers directly in source code. This has been referred to as breaking one of the oldest rules of programming, dating back to the COBOL, FORTRAN and PL/1 manuals of the 1960s. The use of unnamed magic numbers in code obscures the developers' intent in choosing that number, increases opportunities for subtle errors (e.g. is every digit correct in 3.14159265358979323846 and is this equal to 3.14159?) and makes it more difficult for the program to be ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Storage
Computer data storage is a technology consisting of computer components and recording media that are used to retain digital data. It is a core function and fundamental component of computers. The central processing unit (CPU) of a computer is what manipulates data by performing computations. In practice, almost all computers use a storage hierarchy, which puts fast but expensive and small storage options close to the CPU and slower but less expensive and larger options further away. Generally, the fast volatile technologies (which lose data when off power) are referred to as "memory", while slower persistent technologies are referred to as "storage". Even the first computer designs, Charles Babbage's Analytical Engine and Percy Ludgate's Analytical Machine, clearly distinguished between processing and memory (Babbage stored numbers as rotations of gears, while Ludgate stored numbers as displacements of rods in shuttles). This distinction was extended in the Von Neuman ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Network
A computer network is a set of computers sharing resources located on or provided by network nodes. The computers use common communication protocols over digital interconnections to communicate with each other. These interconnections are made up of telecommunication network technologies, based on physically wired, optical, and wireless radio-frequency methods that may be arranged in a variety of network topologies. The nodes of a computer network can include personal computers, servers, networking hardware, or other specialised or general-purpose hosts. They are identified by network addresses, and may have hostnames. Hostnames serve as memorable labels for the nodes, rarely changed after initial assignment. Network addresses serve for locating and identifying the nodes by communication protocols such as the Internet Protocol. Computer networks may be classified by many criteria, including the transmission medium used to carry signals, bandwidth, communications ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Identity (object-oriented Programming)
In object-oriented programming, object-oriented design and object-oriented analysis, the identity of an object is its being distinct from any other object, regardless of the values of the objects' properties. Having identity is a fundamental property of objects. This is closely related to the philosophical concept of identity. Identity and references A reference can be used to refer to an object with a specific identity. A reference contains the information that is necessary for the identity property to be realized in the programming language, and allows access to the object with the identity. A type of a target of a reference is a role. Typically, references are isomorphic to memory addresses. However, multiple such references can refer to the same object, if some form of address mapping is present ( virtual addresses / page tables / memory segments). Object identity is less useful as a semantic concept in environments or situations in which the structure of objects is not ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Data Storage
Computer data storage is a technology consisting of computer components and recording media that are used to retain digital data. It is a core function and fundamental component of computers. The central processing unit (CPU) of a computer is what manipulates data by performing computations. In practice, almost all computers use a storage hierarchy, which puts fast but expensive and small storage options close to the CPU and slower but less expensive and larger options further away. Generally, the fast volatile technologies (which lose data when off power) are referred to as "memory", while slower persistent technologies are referred to as "storage". Even the first computer designs, Charles Babbage's Analytical Engine and Percy Ludgate's Analytical Machine, clearly distinguished between processing and memory (Babbage stored numbers as rotations of gears, while Ludgate stored numbers as displacements of rods in shuttles). This distinction was extended in the Von Neuma ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Time Complexity
In computer science, the time complexity is the computational complexity that describes the amount of computer time it takes to run an algorithm. Time complexity is commonly estimated by counting the number of elementary operations performed by the algorithm, supposing that each elementary operation takes a fixed amount of time to perform. Thus, the amount of time taken and the number of elementary operations performed by the algorithm are taken to be related by a constant factor. Since an algorithm's running time may vary among different inputs of the same size, one commonly considers the worst-case time complexity, which is the maximum amount of time required for inputs of a given size. Less common, and usually specified explicitly, is the average-case complexity, which is the average of the time taken on inputs of a given size (this makes sense because there are only a finite number of possible inputs of a given size). In both cases, the time complexity is generally express ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Null-terminated String
In computer programming, a null-terminated string is a character string stored as an array containing the characters and terminated with a null character (a character with a value of zero, called NUL in this article). Alternative names are C string, which refers to the C programming language and ASCIIZ (although C can use encodings other than ASCII). The length of a string is found by searching for the (first) NUL. This can be slow as it takes O(''n'') (linear time) with respect to the string length. It also means that a string cannot contain a NUL (there is a NUL in memory, but it is after the last character, not "in" the string). History Null-terminated strings were produced by the .ASCIZ directive of the PDP-11 assembly languages and the ASCIZ directive of the MACRO-10 macro assembly language for the PDP-10. These predate the development of the C programming language, but other forms of strings were often used. At the time C (and the languages that it was derived from) w ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |