|
Steganography Tools
A steganography software tool allows a user to embed hidden data inside a carrier file, such as an image or video, and later extract that data. It is not necessary to conceal the message in the original file at all. Thus, it is not necessary to modify the original file and thus, it is difficult to detect anything. If a given section is subjected to successive bitwise manipulation to generate the cyphertext, then there is no evidence in the original file to show that it is being used to encrypt a file. Architecture Carrier The carrier is the signal, stream, or data file into which the hidden data is hidden by making subtle modifications. Examples include audio files, image files, documents, and executable files. In practice, the carrier should look and work the same as the original unmodified carrier, and should appear benign to anyone inspecting it. Certain properties can raise suspicion that a file is carrying hidden data: * If the hidden data is large relative to the carrie ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
OpenPuff Arch1
OpenPuff Steganography and Watermarking, sometimes abbreviated OpenPuff or Puff, is a free steganography tool for Microsoft Windows created by Cosimo Oliboni and still maintained as independent software. The program is notable for being the first steganography tool (version 1.01 released in December 2004) that: * lets users hide data in more than a single carrier file. When hidden data are split among a set of carrier files you get a carrier chain, with no enforced hidden data theoretical size limit (256MB, 512MB, ... depending only on the implementation) * implements 3 layers of hidden data obfuscation (cryptography, whitening and encoding) * extends deniable cryptography into deniable steganography Last revision supports a wide range of carrier formats * Images Bmp, Jpg, Png, Tga * Audios Aiff, Mp3, Wav * Videos 3gp, Mp4, Mpeg I, Mpeg II, Vob * Flash-Adobe Flv, Pdf, Swf Use OpenPuff is used primarily for anonymous asynchronous data sharing: * the sender hides a hid ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Deniable Encryption
In cryptography and steganography, plausibly deniable encryption describes encryption techniques where the existence of an encrypted file or message is deniable in the sense that an adversary cannot prove that the plaintext data exists. The users may convincingly deny that a given piece of data is encrypted, or that they are able to decrypt a given piece of encrypted data, or that some specific encrypted data exists. Such denials may or may not be genuine. For example, it may be impossible to prove that the data is encrypted without the cooperation of the users. If the data is encrypted, the users genuinely may not be able to decrypt it. Deniable encryption serves to undermine an attacker's confidence either that data is encrypted, or that the person in possession of it can decrypt it and provide the associated plaintext. Function Deniable encryption makes it impossible to prove the existence of the plaintext message without the proper decryption key. This may be done by allowing ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Espionage Techniques
Espionage, spying, or intelligence gathering is the act of obtaining secret or confidential information (intelligence) from non-disclosed sources or divulging of the same without the permission of the holder of the information for a tangible benefit. A person who commits espionage is called an ''espionage agent'' or ''spy''. Any individual or spy ring (a cooperating group of spies), in the service of a government, company, criminal organization, or independent operation, can commit espionage. The practice is clandestine, as it is by definition unwelcome. In some circumstances, it may be a legal tool of law enforcement and in others, it may be illegal and punishable by law. Espionage is often part of an institutional effort by a government or commercial concern. However, the term tends to be associated with state spying on potential or actual enemies for military purposes. Spying involving corporations is known as industrial espionage. One of the most effective ways to gat ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Steganography Detection
Steganalysis is the study of detecting messages hidden using steganography; this is analogous to cryptanalysis applied to cryptography. Overview The goal of steganalysis is to identify suspected packages, determine whether or not they have a payload encoded into them, and, if possible, recover that payload. Unlike cryptanalysis, in which intercepted data contains a message (though that message is encrypted), steganalysis generally starts with a pile of suspect data files, but little information about which of the files, if any, contain a payload. The steganalyst is usually something of a forensic statistician, and must start by reducing this set of data files (which is often quite large; in many cases, it may be the entire set of files on a computer) to the subset most likely to have been altered. Basic techniques The problem is generally handled with statistical analysis. A set of unmodified files of the same type, and ideally from the same source (for example, the same m ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Steganographic File System
Steganographic file systems are a kind of file system first proposed by Ross Anderson, Roger Needham, and Adi Shamir. Their paper proposed two main methods of hiding data: in a series of fixed size files originally consisting of random bits on top of which 'vectors' could be superimposed in such a way as to allow levels of security to decrypt all lower levels but not even know of the existence of any higher levels, or an entire partition is filled with random bits and files hidden in it. In a steganographic file system using the second scheme, files are not merely stored, nor stored encrypted, but the entire partition is randomized - encrypted files strongly resemble randomized sections of the partition, and so when files are stored on the partition, there is no easy way to discern between meaningless gibberish and the actual encrypted files. Furthermore, locations of files are derived from the key for the files, and the locations are hidden and available to only programs with ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
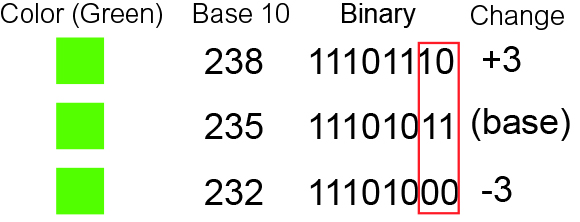
Least Significant Bit
In computing, bit numbering is the convention used to identify the bit positions in a binary number. Bit significance and indexing In computing, the least significant bit (LSB) is the bit position in a binary integer representing the binary 1s place of the integer. Similarly, the most significant bit (MSB) represents the highest-order place of the binary integer. The LSB is sometimes referred to as the ''low-order bit'' or ''right-most bit'', due to the convention in positional notation of writing less significant digits further to the right. The MSB is similarly referred to as the ''high-order bit'' or ''left-most bit''. In both cases, the LSB and MSB correlate directly to the least significant digit and most significant digit of a decimal integer. Bit indexing correlates to the positional notation of the value in base 2. For this reason, bit index is not affected by how the value is stored on the device, such as the value's byte order. Rather, it is a property of the num ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Metadata
Metadata is "data that provides information about other data", but not the content of the data, such as the text of a message or the image itself. There are many distinct types of metadata, including: * Descriptive metadata – the descriptive information about a resource. It is used for discovery and identification. It includes elements such as title, abstract, author, and keywords. * Structural metadata – metadata about containers of data and indicates how compound objects are put together, for example, how pages are ordered to form chapters. It describes the types, versions, relationships, and other characteristics of digital materials. * Administrative metadata – the information to help manage a resource, like resource type, permissions, and when and how it was created. * Reference metadata – the information about the contents and quality of Statistical data type, statistical data. * Statistical metadata – also called process data, may describe processes that collect, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Ancillary Data
Ancillary data is data that has been added to given data and uses the same form of transport. Common examples are cover art images for media files or streams, or digital data added to radio or television broadcasts. Television Ancillary data (commonly abbreviated as ANC data), in the context of television systems, refers to a means which by non-video information (such as audio, other forms of essence, and metadata) may be ''embedded'' within the serial digital interface. Ancillary data is standardized by SMPTE as ''SMPTE 291M: Ancillary Data Packet and Space Formatting''. Ancillary data can be located in non-picture portions of horizontal scan lines. This is known as horizontal ancillary data (HANC). Ancillary data can also be located in non-picture regions of the frame, This is known as vertical ancillary data (VANC). Technical details Location Ancillary data packets may be located anywhere within a serial digital data stream, with the following exceptions: * They should ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Steganalysis
Steganalysis is the study of detecting messages hidden using steganography; this is analogous to cryptanalysis applied to cryptography. Overview The goal of steganalysis is to identify suspected packages, determine whether or not they have a payload encoded into them, and, if possible, recover that payload. Unlike cryptanalysis, in which intercepted data contains a message (though that message is encrypted), steganalysis generally starts with a pile of suspect data files, but little information about which of the files, if any, contain a payload. The steganalyst is usually something of a forensic statistician, and must start by reducing this set of data files (which is often quite large; in many cases, it may be the entire set of files on a computer) to the subset most likely to have been altered. Basic techniques The problem is generally handled with statistical analysis. A set of unmodified files of the same type, and ideally from the same source (for example, the same m ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Obfuscation
Obfuscation is the obscuring of the intended meaning of communication by making the message difficult to understand, usually with confusing and ambiguous language. The obfuscation might be either unintentional or intentional (although intent usually is connoted), and is accomplished with circumlocution (talking around the subject), the use of jargon (technical language of a profession), and the use of an argot ( ingroup language) of limited communicative value to outsiders. In expository writing, unintentional obfuscation usually occurs in draft documents, at the beginning of composition; such obfuscation is illuminated with critical thinking and editorial revision, either by the writer or by an editor. Etymologically, the word ''obfuscation'' derives from the Latin , from ''obfuscāre'' (to darken); synonyms include the words beclouding and abstrusity. Medical Doctors are faulted for using jargon to conceal unpleasant facts from a patient; the American author and phys ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Covering Space
A covering of a topological space X is a continuous map \pi : E \rightarrow X with special properties. Definition Let X be a topological space. A covering of X is a continuous map : \pi : E \rightarrow X such that there exists a discrete space D and for every x \in X an open neighborhood U \subset X, such that \pi^(U)= \displaystyle \bigsqcup_ V_d and \pi, _:V_d \rightarrow U is a homeomorphism for every d \in D . Often, the notion of a covering is used for the covering space E as well as for the map \pi : E \rightarrow X. The open sets V_ are called sheets, which are uniquely determined up to a homeomorphism if U is connected. For each x \in X the discrete subset \pi^(x) is called the fiber of x. The degree of a covering is the cardinality of the space D. If E is path-connected, then the covering \pi : E \rightarrow X is denoted as a path-connected covering. Examples * For every topological space X there exists the covering \pi:X \rightarrow X with \pi(x)=x, which is ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |