|
Self-Protecting Digital Content
{{Refimprove, date=March 2008 Self Protecting Digital Content (SPDC), is a copy protection (digital rights management) architecture which allows restriction of access to, and copying of, the next generation of optical discs and streaming/downloadable content. Overview Designed by Cryptography Research, Inc. of San Francisco, SPDC executes code from the encrypted content on the DVD player, enabling the content providers to change DRM systems in case an existing system is compromised. It adds functionality to make the system "dynamic", as opposed to "static" systems in which the system and keys for encryption and decryption do not change, thus enabling one compromised key to decode all content released using that encryption system. "Dynamic" systems attempt to make future content released immune to existing methods of circumvention. Playback method If a method of playback used in previously released content is revealed to have a weakness, either by review or because it has al ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Copy Protection
Copy protection, also known as content protection, copy prevention and copy restriction, describes measures to enforce copyright by preventing the reproduction of software, films, music, and other media. Copy protection is most commonly found on videotapes, DVDs, Blu-ray discs, HD-DVDs, computer software discs, video game discs and cartridges, audio CDs and some VCDs. Some methods of copy protection have also led to criticism because it caused inconvenience for paying consumers or secretly installed additional or unwanted software to detect copying activities on the consumer's computer. Making copy protection effective while protecting consumer rights remains a problem with media publication. Terminology Media corporations have always used the term copy protection, but critics argue that the term tends to sway the public into identifying with the publishers, who favor restriction technologies, rather than with the users. Copy prevention and copy control may be more neutr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Virtual Environment
A virtual environment is a networked application that allows a user to interact with both the computing environment and the work of other users. Email, chat, and web-based document sharing Document and file collaboration are the tools or systems set up to help multiple people work together on a single document or file to achieve a single final version. Normally, this is software that allows teams to work on a single document, such as ... applications are all examples of virtual environments. Simply put, it is a networked common operating space. Once the fidelity of the virtual environment is such that it "creates a psychological state in which the individual perceives himself or herself as existing within the virtual environment" (Blascovich, 2002, p. 129) then the virtual environment (VE) has progressed into the realm of immersive virtual environments (IVEs). References * Blascovich, J. (2002).Social Influence within Immersive Virtual Environments In R. Schroeder (Ed.), Th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Posterizing
Posterization or posterisation of an image is the conversion of a continuous gradation of tone to several regions of fewer tones, causing abrupt changes from one tone to another. This was originally done with photographic processes to create posters. It can now be done photographically or with digital image processing, and may be deliberate or an unintended artifact of color quantization. Cause The effect may be created deliberately, or happen accidentally. For artistic effect, most image editing programs provide a posterization feature, or photographic processes may be used. Unwanted posterization, also known as banding, may occur when the color depth, sometimes called bit depth, is insufficient to accurately sample a continuous gradation of color tone. As a result, a continuous gradient appears as a series of discrete steps or bands of color — hence the name. When discussing fixed pixel displays, such as LCD and plasma televisions, this effect is referred to as false c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
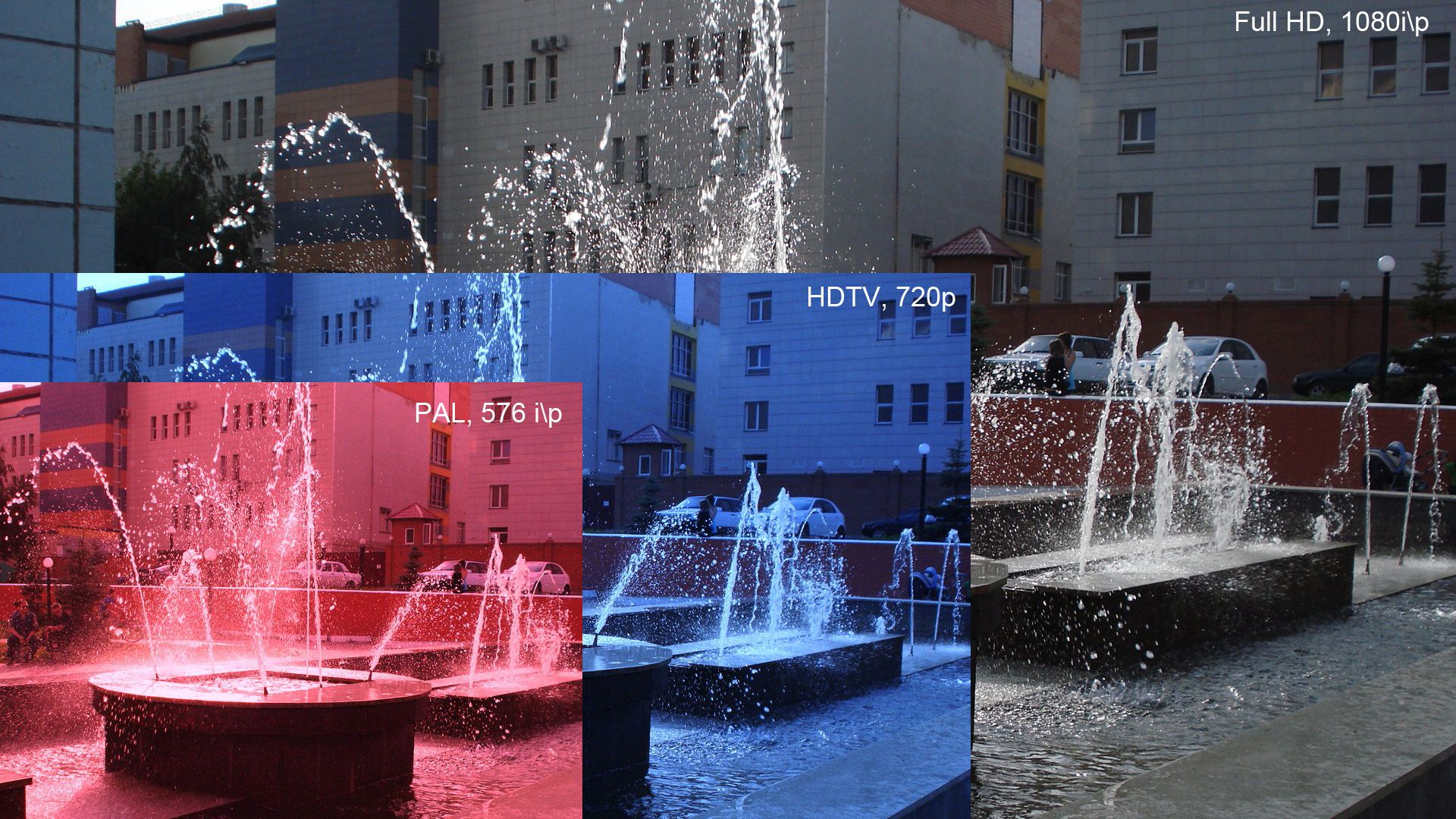
1080p
1080p (1920×1080 progressively displayed pixels; also known as Full HD or FHD, and BT.709) is a set of HDTV high-definition video modes characterized by 1,920 pixels displayed across the screen horizontally and 1,080 pixels down the screen vertically; the ''p'' stands for progressive scan, ''i.e.'' non-interlaced. The term usually assumes a widescreen aspect ratio of 16:9, implying a resolution of 2.1 megapixels. It is often marketed as Full HD or FHD, to contrast 1080p with 720p resolution screens. Although 1080p is sometimes informally referred to as 2K, these terms reflect two distinct technical standards, with differences including resolution and aspect ratio. 1080p video signals are supported by ATSC standards in the United States and DVB standards in Europe. Applications of the 1080p standard include television broadcasts, Blu-ray Discs, smartphones, Internet content such as YouTube videos and Netflix TV shows and movies, consumer-grade televisions and p ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Analog Hole
The analog hole (also known as the analog loophole or analog gap) is a perceived fundamental and inevitable vulnerability in copy protection schemes for noninteractive works in digital formats which can be exploited to duplicate copy-protected works using analog means. Once digital information is converted to a human-perceptible (analog) form, it is a relatively simple matter to digitally recapture that analog reproduction in an unrestricted form, thereby fundamentally circumventing any and all restrictions placed on copyrighted digitally distributed work. Media publishers who use digital rights management (DRM), to restrict how a work can be used, perceive the necessity to make it visible or audible as a "hole" in the control that DRM otherwise affords them. Overview Although the technology for creating digital recordings from analog sources has existed for some time, it was not necessarily viewed as a "hole" until the widespread deployment of DRM in the late 1990s. However, i ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Internet
The Internet (or internet) is the global system of interconnected computer networks that uses the Internet protocol suite (TCP/IP) to communicate between networks and devices. It is a ''internetworking, network of networks'' that consists of private, public, academic, business, and government networks of local to global scope, linked by a broad array of electronic, wireless, and optical networking technologies. The Internet carries a vast range of information resources and services, such as the inter-linked hypertext documents and Web application, applications of the World Wide Web (WWW), email, electronic mail, internet telephony, telephony, and file sharing. The origins of the Internet date back to the development of packet switching and research commissioned by the United States Department of Defense in the 1960s to enable time-sharing of computers. The primary precursor network, the ARPANET, initially served as a backbone for interconnection of regional academic and mi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
HDCP
High-bandwidth Digital Content Protection (HDCP) is a form of digital copy protection developed by Intel Corporation to prevent copying of digital audio and video content as it travels across connections. Types of connections include DisplayPort (DP), Digital Visual Interface (DVI), and High-Definition Multimedia Interface (HDMI), as well as less popular or now deprecated protocols like Gigabit Video Interface (GVIF) and Unified Display Interface (UDI). The system is meant to stop HDCP-encrypted content from being played on unauthorized devices or devices which have been modified to copy HDCP content. Before sending data, a transmitting device checks that the receiver is authorized to receive it. If so, the transmitter encrypts the data to prevent eavesdropping as it flows to the receiver. In order to make a device that plays HDCP-enabled content, the manufacturer must obtain a license for the patent from Intel subsidiary Digital Content Protection LLC, pay an annual fee, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Firmware
In computing, firmware is a specific class of computer software that provides the low-level control for a device's specific hardware. Firmware, such as the BIOS of a personal computer, may contain basic functions of a device, and may provide hardware abstraction services to higher-level software such as operating systems. For less complex devices, firmware may act as the device's complete operating system, performing all control, monitoring and data manipulation functions. Typical examples of devices containing firmware are embedded systems (running embedded software), home and personal-use appliances, computers, and computer peripherals. Firmware is held in non-volatile memory devices such as ROM, EPROM, EEPROM, and flash memory. Updating firmware requires ROM integrated circuits to be physically replaced, or EPROM or flash memory to be reprogrammed through a special procedure. Some firmware memory devices are permanently installed and cannot be changed after manufact ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Emulator
In computing, an emulator is hardware or software that enables one computer system (called the ''host'') to behave like another computer system (called the ''guest''). An emulator typically enables the host system to run software or use peripheral devices designed for the guest system. Emulation refers to the ability of a computer program in an electronic device to emulate (or imitate) another program or device. Many printers, for example, are designed to emulate HP LaserJet printers because so much software is written for HP printers. If a non-HP printer emulates an HP printer, any software written for a real HP printer will also run in the non-HP printer emulation and produce equivalent printing. Since at least the 1990s, many video game enthusiasts and hobbyists have used emulators to play classic arcade games from the 1980s using the games' original 1980s machine code and data, which is interpreted by a current-era system, and to emulate old video game consoles. A hardw ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer
A computer is a machine that can be programmed to Execution (computing), carry out sequences of arithmetic or logical operations (computation) automatically. Modern digital electronic computers can perform generic sets of operations known as Computer program, programs. These programs enable computers to perform a wide range of tasks. A computer system is a nominally complete computer that includes the Computer hardware, hardware, operating system (main software), and peripheral equipment needed and used for full operation. This term may also refer to a group of computers that are linked and function together, such as a computer network or computer cluster. A broad range of Programmable logic controller, industrial and Consumer electronics, consumer products use computers as control systems. Simple special-purpose devices like microwave ovens and remote controls are included, as are factory devices like industrial robots and computer-aided design, as well as general-purpose devi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Fingerprint (computing)
In computer science, a fingerprinting algorithm is a procedure that maps an arbitrarily large data item (such as a computer file) to a much shorter bit string, its fingerprint, that uniquely identifies the original data for all practical purposesA. Z. Broder. Some applications of Rabin's fingerprinting method. In Sequences II: Methods in Communications, Security, and Computer Science, pages 143--152. Springer-Verlag, 1993 just as human fingerprints uniquely identify people for practical purposes. This fingerprint may be used for data deduplication purposes. This is also referred to as file fingerprinting, data fingerprinting, or structured data fingerprinting. Fingerprints are typically used to avoid the comparison and transmission of bulky data. For instance, a web browser or proxy server can efficiently check whether a remote file has been modified, by fetching only its fingerprint and comparing it with that of the previously fetched copy.Detecting duplicate and near-duplica ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Digital Rights Management
Digital rights management (DRM) is the management of legal access to digital content. Various tools or technological protection measures (TPM) such as access control technologies can restrict the use of proprietary hardware and copyrighted works. DRM technologies govern the use, modification, and distribution of copyrighted works (such as software and multimedia content), as well as systems that enforce these policies within devices. Laws in many countries criminalize the circumvention of DRM, communication about such circumvention, and the creation and distribution of tools used for such circumvention. Such laws are part of the United States' Digital Millennium Copyright Act (DMCA), and the European Union's Information Society Directive (the French DADVSI is an example of a member state of the European Union implementing the directive). DRM techniques include licensing agreements and encryption. The industry has expanded the usage of DRM to various hardware products, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |