|
Fingerprint (computing)
In computer science, a fingerprinting algorithm is a procedure that maps an arbitrarily large data item (remove, as a computer file) to a much shorter bit string, its ''fingerprint'', that uniquely identifies the original data for all practical purposes just as human fingerprints uniquely identify people for practical purposes. This fingerprint may be used for data deduplication purposes. This is also referred to as ''file fingerprinting'', ''data fingerprinting'', or ''structured data fingerprinting''. Fingerprints are typically used to avoid the comparison and transmission of bulky data. For instance, a remove, web browser or proxy server can efficiently check whether a remote, by fetching only its fingerprint and comparing it with that of the previously fetched copy. Fingerprint functions may be seen as high-performance hash functions used to uniquely identify substantial blocks of data where cryptographic functions may be. Special algorithms exist for audio and video fingerpr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hash Collision
In computer science, a hash collision or hash clash is when two distinct pieces of data in a hash table share the same hash value. The hash value in this case is derived from a hash function which takes a data input and returns a fixed length of bits. Although hash algorithms, especially cryptographic hash algorithms, have been created with the intent of being Collision resistance, collision resistant, they can still sometimes map different data to the same hash (by virtue of the pigeonhole principle). Malicious users can take advantage of this to mimic, access, or alter data. Due to the possible negative applications of hash collisions in data management and computer security (in particular, cryptographic hash functions), collision avoidance has become an important topic in computer security. Background Hash collisions can be unavoidable depending on the number of objects in a set and whether or not the bit string they are mapped to is long enough in length. When there is a s ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
National Drug Intelligence Center
The United States National Drug Intelligence Center (NDIC), established in 1993, was a component of the U.S. Department of Justice and a member of the Intelligence Community. ThGeneral Counterdrug Intelligence Plan implemented in February 2000, designated NDIC as the nation's principal center for strategic domestic counterdrug intelligence. The NDIC ceased to exist on June 15, 2012. Its former DOMEX and strategic analysis functions transferred over to the Drug Enforcement Administration (DEA). Creation On September 5, 1989 President George H.W. Bush with his Director of the Office of National Drug Control Policy (ONDCP) William Bennett, unveiled hiNational Drug Control Strategywhich outlined the President's strategy for coordinating the combined efforts of various federal programs to reduce drug use and drug trafficking in the United States. The inaugural strategy was to announce that ONDCP would develop an intelligence center that would unite U.S. drug-related analytical ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Usage Share Of Web Browsers
The usage share of web browsers is the portion, often expressed as a percentage, of visitors to a group of web sites that use a particular web browser. Accuracy Measuring browser usage in the number of requests (page hits) made by each user agent can be misleading. Overestimation Not all requests are generated by a user, as a user agent can make requests at regular time intervals without user input. In this case, the user's activity might be overestimated. Some examples: * Certain anti-virus products fake their user agent string to appear to be popular browsers. This is done to trick attack sites that might display clean content to the scanner, but not to the browser.'' The Register'' reported in June 2008 that traffic from AVG Linkscanner, using an IE6 user agent string, outstripped human link clicks by nearly 10 to 1. * A user who revisits a site shortly after changing or upgrading browsers may be double-counted under some methods; overall numbers at the time of a new v ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Randomizing Function
Random number generation is a process by which, often by means of a random number generator (RNG), a sequence of numbers or symbols is generated that cannot be reasonably predicted better than by random chance. This means that the particular outcome sequence will contain some patterns detectable in hindsight but impossible to foresee. True random number generators can be '' hardware random-number generators'' (HRNGs), wherein each generation is a function of the current value of a physical environment's attribute that is constantly changing in a manner that is practically impossible to model. This would be in contrast to so-called "random number generations" done by ''pseudorandom number generators'' (PRNGs), which generate numbers that only look random but are in fact predetermined—these generations can be reproduced simply by knowing the state of the PRNG. Various applications of randomness have led to the development of different methods for generating random data. Some of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Public Key Fingerprint
In public-key cryptography, a public key fingerprint is a short sequence of bytes used to identify a longer public key. Fingerprints are created by applying a cryptographic hash function to a public key. Since fingerprints are shorter than the keys they refer to, they can be used to simplify certain key management tasks. In Microsoft software, "thumbprint" is used instead of "fingerprint." Creating public key fingerprints A public key fingerprint is typically created through the following steps: # A public key (and optionally some additional data) is encoded into a sequence of bytes. To ensure that the same fingerprint can be recreated later, the encoding must be deterministic, and any additional data must be exchanged and stored alongside the public key. The additional data is typically information which anyone using the public key should be aware of. Examples of additional data include: which protocol versions the key should be used with (in the case of PGP fingerprints); ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Error Correcting Code
In computing, telecommunication, information theory, and coding theory, forward error correction (FEC) or channel coding is a technique used for controlling errors in data transmission over unreliable or noisy communication channels. The central idea is that the sender encodes the message in a redundant way, most often by using an error correction code, or error correcting code (ECC). The redundancy allows the receiver not only to detect errors that may occur anywhere in the message, but often to correct a limited number of errors. Therefore a reverse channel to request re-transmission may not be needed. The cost is a fixed, higher forward channel bandwidth. The American mathematician Richard Hamming pioneered this field in the 1940s and invented the first error-correcting code in 1950: the Hamming (7,4) code. FEC can be applied in situations where re-transmissions are costly or impossible, such as one-way communication links or when transmitting to multiple receivers in m ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
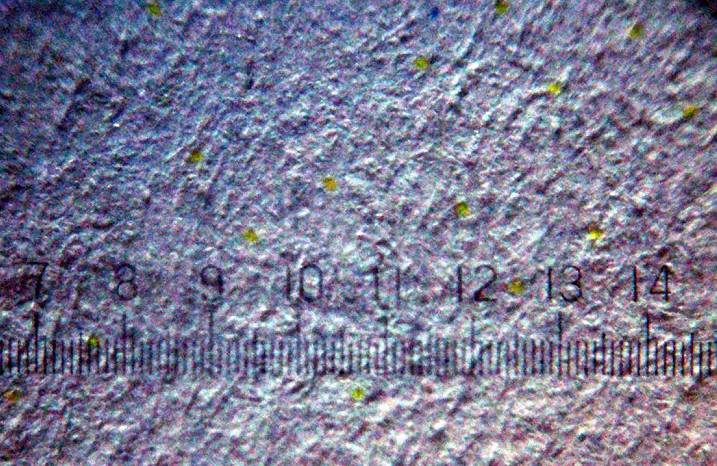
Machine Identification Code
Printer tracking dots, also known as printer steganography, DocuColor tracking dots, yellow dots, secret dots, or a machine identification code (MIC), is a digital watermarking, digital watermark which many color laser printing, laser printers and photocopiers produce on every printed page that identifies the specific device that was used to print the document. Developed by Xerox and Canon Inc., Canon in the mid-1980s, the existence of these tracking codes became public only in 2004. History In the mid-1980s, Xerox pioneered an encoding mechanism for a unique number represented by tiny dots spread over the entire print area, and first deployed this scheme in its DocuColor line of printers. Xerox developed this surreptitious tracking code "to assuage fears that their color copiers could be used to counterfeit bills" and received U.S. Patent No. 5515451 describing the use of the yellow dots to identify the source of a copied or printed document. The scheme was then widely deployed ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Device Fingerprint
A device fingerprint or machine fingerprint is information collected about the software and hardware of a remote computing device for the purpose of identification. The information is usually assimilated into a brief identifier using a fingerprinting algorithm. A browser fingerprint is information collected specifically by interaction with the web browser of the device. Device fingerprints can be used to fully or partially identify individual devices even when persistent cookies (and zombie cookies) cannot be read or stored in the browser, the client IP address is hidden, or one switches to another browser on the same device. This may allow a service provider to detect and prevent identity theft and credit card fraud, but also to compile long-term records of individuals' browsing histories (and deliver targeted advertising or targeted exploits) even when they are attempting to avoid tracking – raising a major concern for internet privacy advocates. History Basic web brows ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
TCP/IP Stack Fingerprinting
TCP/IP stack fingerprinting is the remote detection of the characteristics of a TCP/IP stack implementation. The combination of parameters may then be used to infer the remote machine's operating system (aka, OS fingerprinting), or incorporated into a device fingerprint. TCP/IP Fingerprint Specifics Certain parameters within the TCP protocol definition are left up to the implementation. Different operating systems, and different versions of the same operating system, set different defaults for these values. By collecting and examining these values, one may differentiate among various operating systems and implementations of TCP/IP. The TCP/IP fields that may vary include the following: * Initial packet size (16 bits) * Initial TTL (8 bits) * Window size (16 bits) * Max segment size (16 bits) * Window scaling value (8 bits) * "don't fragment" flag (1 bit) * "sackOK" flag (1 bit) * "nop" flag (1 bit) These values may be combined to form a 67-bit signature, or fingerprint, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Digital Video Fingerprinting
Video fingerprinting or video hashing are a class of dimension reduction techniques in which a system identifies, extracts and then summarizes characteristic components of a video as a unique or a set of multiple '' perceptual hashes'' or ''fingerprints'', enabling that video to be uniquely identified. This technology has proven to be effective at searching and comparing video files. History and process Video fingerprinting was first developed into practical use by Philips in 2002.Oostveen, J., Kalker, T., & Haitsma, J. (2002, March). Feature extraction and a database strategy for video fingerprinting. In ''International Conference on Advances in Visual Information Systems'' (pp. 117-128). Springer, Berlin, Heidelberg. Different methods exist for video fingerprinting. Van Oostveen relied on changes in patterns of image intensity over successive video frames. This makes the video fingerprinting robust against limited changes in color—or the transformation of color into gray scale ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Canvas Fingerprinting
Canvas fingerprinting is one of a number of Device fingerprint, browser fingerprinting techniques for Web tracking, tracking online users that allow websites to identify and track visitors using the HTML5 canvas element instead of browser cookies or other similar means. The technique received wide media coverage in 2014 after researchers from Princeton University and Katholieke Universiteit Leuven, KU Leuven University described it in their paper ''The Web never forgets''. Description Canvas fingerprinting works by exploiting the HTML5 canvas element. As described by Acar et al. in: Variations in which the graphics processing unit (GPU), or the Device driver, graphics driver, is installed may cause the fingerprint variation. The fingerprint can be stored and shared with advertising partners to identify users when they visit affiliated websites. A profile can be created from the user's browsing activity, allowing advertisers to Targeted advertising, target advertise to the user's i ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Automatic Content Recognition
Automatic content recognition (ACR) is a technology used to identify content played on a media device or presented within a media file. Devices with ACR can allow for the collection of content consumption information automatically at the screen or speaker level itself, without any user-based input or search efforts. This information may be collected for purposes such as personalized advertising, content recommendations, or sale to companies that aggregate customer data. How it works To start the process, a short media clip (audio, video, or both) is selected from within a media file or captured as displayed on a device such as a smart TV. Using techniques such as fingerprinting and watermarking, the selected content is compared by the ACR software with a database of known recorded works. If the fingerprint of the media clip finds a match, the ACR software returns the corresponding metadata regarding the media as well as other associated or recommended content back to the client a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |