|
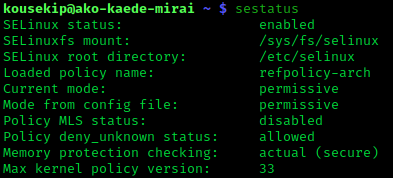
Security Enhanced Linux
Security-Enhanced Linux (SELinux) is a Linux kernel security module that provides a mechanism for supporting access control security policies, including mandatory access controls (MAC). SELinux is a set of kernel modifications and user-space tools that have been added to various Linux distributions. Its architecture strives to separate enforcement of security decisions from the security policy, and streamlines the amount of software involved with security policy enforcement. The key concepts underlying SELinux can be traced to several earlier projects by the United States National Security Agency (NSA). Overview The NSA Security-enhanced Linux Team describes NSA SELinux as a set of patches to the Linux kernel and utilities to provide a strong, flexible, mandatory access control (MAC) architecture into the major subsystems of the kernel. It provides an enhanced mechanism to enforce the separation of information based on confidentiality and integrity requirements, which allows t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Simple Desktop Display Manager
Simple Desktop Display Manager (SDDM) is a X display manager, display manager (a graphical login program) for the X11 and Wayland (display server protocol), Wayland windowing systems. SDDM was written from scratch in C++11 and supports theming via QML. SDDM is free and open-source software subject to the terms of the GNU General Public License version 2 or later. Adoption In 2013, Fedora (operating system), Fedora KDE members decided to default to SDDM in Fedora 21. KDE chose SDDM to be the successor of the KDE Display Manager for KDE Plasma 5. The LXQt developers recommend SDDM as a display manager. See also * LightDM, Light display manager, formerly written for Ubuntu (operating system), Ubuntu, now independent * GNOME Display Manager, GDM, the default graphical login program for GNOME References KDE Software Compilation Software that uses QML Software that uses Qt X display managers {{compu-graphics-stub ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Setuid
The Unix and Linux access rights flags setuid and setgid (short for ''set user identity'' and ''set group identity'') allow users to run an executable with the file system permissions of the executable's owner or group respectively and to change behaviour in directories. They are often used to allow users on a computer system to run programs with temporarily elevated privileges to perform a specific task. While the assumed user id or group id privileges provided are not always elevated, at a minimum they are specific. The flags setuid and setgid are needed for tasks that require different privileges than what the user is normally granted, such as the ability to alter system files or databases to change their login password. Some of the tasks that require additional privileges may not immediately be obvious, though, such as the ping command, which must send and listen for control packets on a network interface. File modes The setuid and setgid bits are normally represented a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
FreeBSD
FreeBSD is a free-software Unix-like operating system descended from the Berkeley Software Distribution (BSD). The first version was released in 1993 developed from 386BSD, one of the first fully functional and free Unix clones on affordable home-class hardware, and has since continuously been the most commonly used BSD-derived operating system. FreeBSD maintains a complete system, delivering a kernel, device drivers, userland utilities, and documentation, as opposed to Linux only delivering a kernel and drivers, and relying on third-parties such as GNU for system software. The FreeBSD source code is generally released under a permissive BSD license, as opposed to the copyleft GPL used by Linux. The project includes a security team overseeing all software shipped in the base distribution. Third-party applications may be installed using the pkg package management system or from source via FreeBSD Ports. The project is supported and promoted by the FreeBSD Foundation ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
TrustedBSD
FreeBSD is a free-software Unix-like operating system descended from the Berkeley Software Distribution (BSD). The first version was released in 1993 developed from 386BSD, one of the first fully functional and free Unix clones on affordable home-class hardware, and has since continuously been the most commonly used BSD-derived operating system. FreeBSD maintains a complete system, delivering a kernel, device drivers, userland utilities, and documentation, as opposed to Linux only delivering a kernel and drivers, and relying on third-parties such as GNU for system software. The FreeBSD source code is generally released under a permissive BSD license, as opposed to the copyleft GPL used by Linux. The project includes a security team overseeing all software shipped in the base distribution. Third-party applications may be installed using the pkg package management system or from source via FreeBSD Ports. The project is supported and promoted by the FreeBSD Foundation. Much ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
FLASK
Flask may refer to: Container * Hip flask, a small container used to carry liquid * Laboratory flask, laboratory glassware for holding larger volumes than simple test tubes ** Erlenmeyer flask, a common laboratory flask with a flat bottom, a conical body, and a cylindrical neck * Vacuum flask A vacuum flask (also known as a Dewar flask, Dewar bottle or thermos) is an insulating storage vessel that slows the speed at which its contents change in temperature. It greatly lengthens the time over which its contents remain hotter or coo ..., a container designed to keep warm drinks warm and refrigerated drinks cold Other * Flask (metal casting), a containing frame without a top or bottom, with sides only, used to hold molding sand * Flask (web framework), a web framework for the Python programming language * Powder flask, a small container for gunpowder * FLASK, the Flux Advanced Security Kernel, an operating system security architecture * Flask (unit), a unit used in UK ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Secure Computing Corporation
Secure Computing Corporation (SCC) was a public company that developed and sold computer security appliances and hosted services to protect users and data. McAfee acquired the company in 2008. The company also developed filtering systems used by governments such as Internet censorship in Iran, Iran and Communications in Saudi Arabia, Saudi Arabia that blocks their citizens from accessing information on the Internet.Snuffing out Net's benefit to democracy Jim Landers, ''Dallas Morning News'', December 20, 2005; accessed September 20, 2008.Iran targets dissent on the net Clark Boyd, ''BBC.com'', ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Network Associates
McAfee Corp. ( ), formerly known as McAfee Associates, Inc. from 1987 to 1997 and 2004 to 2014, Network Associates Inc. from 1997 to 2004, and Intel Security Group from 2014 to 2017, is an American proprietary software company focused on online protection for consumers worldwide headquartered in San Jose, California. The company was purchased by Intel in February 2011; with this acquisition, it became part of the Intel Security division. In 2017, Intel had a strategic deal with TPG Capital and converted Intel Security into a joint venture between both companies called McAfee. Thoma Bravo took a minority stake in the new company, and Intel retained a 49% stake. The owners took McAfee public on the NASDAQ in 2020, and in 2022 an investor group led by Advent International Corporation took it private again. History 1987–1999 The company was founded in 1987 as McAfee Associates, named for its founder John McAfee, who resigned from the company in 1994. McAfee was incorpora ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Open-source Software
Open-source software (OSS) is Software, computer software that is released under a Open-source license, license in which the copyright holder grants users the rights to use, study, change, and Software distribution, distribute the software and its source code to anyone and for any purpose. Open-source software may be developed in a collaborative, public manner. Open-source software is a prominent example of open collaboration, meaning any capable user is able to online collaboration, participate online in development, making the number of possible contributors indefinite. The ability to examine the code facilitates public trust in the software. Open-source software development can bring in diverse perspectives beyond those of a single company. A 2024 estimate of the value of open-source software to firms is $8.8 trillion, as firms would need to spend 3.5 times the amount they currently do without the use of open source software. Open-source code can be used for studying and a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Linux Kernel Mainline
The Linux kernel is a Free and open-source software, free and open source Unix-like kernel (operating system), kernel that is used in many computer systems worldwide. The kernel was created by Linus Torvalds in 1991 and was soon adopted as the kernel for the GNU operating system (OS) which was created to be a free software, free replacement for Unix. Since the late 1990s, it has been included in many Linux distributions, operating system distributions, many of which are called Linux. One such Linux kernel operating system is Android (operating system), Android which is used in many mobile and embedded devices. Most of the kernel code is written in C (programming language), C as supported by the GNU compiler collection (GCC) which has extensions beyond standard C. The code also contains assembly language, assembly code for architecture-specific logic such as optimizing memory use and task execution. The kernel has a Modular programming, modular design such that modules can be inte ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Rainbow Series
The Rainbow Series (sometimes known as the Rainbow Books) is a series of computer security standards and guidelines published by the United States government in the 1980s and 1990s. They were originally published by the U.S. Department of Defense Computer Security Center, and then by the National Computer Security Center. Objective These standards describe a process of evaluation for trusted systems. In some cases, U.S. government entities (as well as private firms) would require formal verification and validation, validation of computer technology using this process as part of their procurement criteria. Many of these standards have influenced, and have been superseded by, the Common Criteria. The books have nicknames based on the color of its cover. For example, the TCSEC, Trusted Computer System Evaluation Criteria was referred to as "The Orange Book." In the book entitled ''Applied Cryptography'', security expert Bruce Schneier states of NCSC-TG-021 that he "can't even be ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
National Security Agency
The National Security Agency (NSA) is an intelligence agency of the United States Department of Defense, under the authority of the director of national intelligence (DNI). The NSA is responsible for global monitoring, collection, and processing of information and data for global intelligence and counterintelligence purposes, specializing in a discipline known as signals intelligence (SIGINT). The NSA is also tasked with the protection of U.S. communications networks and information systems. The NSA relies on a variety of measures to accomplish its mission, the majority of which are clandestine. The NSA has roughly 32,000 employees. Originating as a unit to decipher coded communications in World War II, it was officially formed as the NSA by President Harry S. Truman in 1952. Between then and the end of the Cold War, it became the largest of the U.S. intelligence organizations in terms of personnel and budget. Still, information available as of 2013 indicates that the C ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Type Enforcement Architecture
The concept of type enforcement (TE), in the field of information technology, is an access control mechanism for regulating access in computer systems. Implementing TE gives priority to mandatory access control (MAC) over discretionary access control (DAC). Access clearance is first given to a subject (e.g. process) accessing objects (e.g. files, records, messages) based on rules defined in an attached security context. A security context in a domain is defined by a domain security policy. In the Linux security module (LSM) in SELinux, the security context is an extended attribute. Type enforcement implementation is a prerequisite for MAC, and a first step before multilevel security (MLS) or its replacement multi categories security (MCS). It is a complement of role-based access control (RBAC). Control Type enforcement implies fine-grained control over the operating system, not only to have control over process execution, but also over domain transition or authorization scheme ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |