|
Pseudonymisation
Pseudonymization is a data management and de-identification procedure by which personally identifiable information fields within a data record are replaced by one or more artificial identifiers, or pseudonyms. A single pseudonym for each replaced field or collection of replaced fields makes the data record less identifiable while remaining suitable for data analysis and data processing. Pseudonymization (or pseudonymisation, the spelling under European guidelines) is one way to comply with the European Union's General Data Protection Regulation (GDPR) demands for secure data storage of personal information. Pseudonymized data can be restored to its original state with the addition of information which allows individuals to be re-identified. In contrast, anonymization is intended to prevent re-identification of individuals within the dataset. Clause 18, Module Four, footnote 2 of the Adoption by the European Commission of the Implementing Decisions (EU) 2021/914 “requires rende ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
General Data Protection Regulation
The General Data Protection Regulation (Regulation (EU) 2016/679), abbreviated GDPR, is a European Union regulation on information privacy in the European Union (EU) and the European Economic Area (EEA). The GDPR is an important component of EU privacy law and human rights law, in particular Article 8(1) of the Charter of Fundamental Rights of the European Union. It also governs the transfer of personal data outside the EU and EEA. The GDPR's goals are to enhance individuals' control and rights over their personal information and to simplify the regulations for international business. It supersedes the Data Protection Directive 95/46/EC and, among other things, simplifies the terminology. The European Parliament and Council of the European Union adopted the GDPR on 14 April 2016, to become effective on 25 May 2018. As an EU regulation (instead of a directive), the GDPR has direct legal effect and does not require transposition into national law. However, it also provide ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
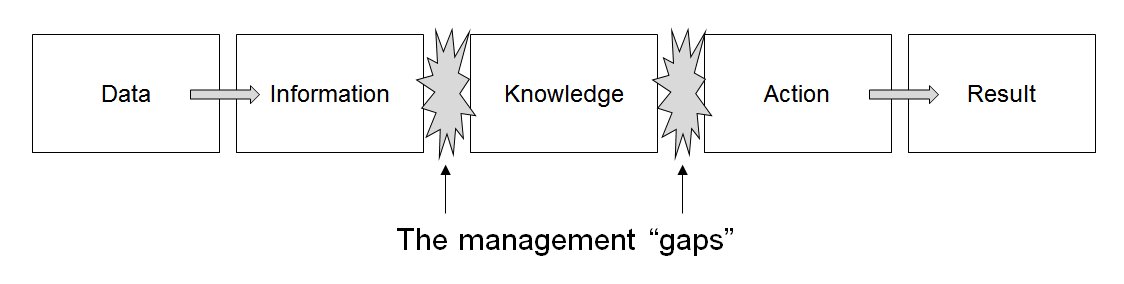
Data Management
Data management comprises all disciplines related to handling data as a valuable resource, it is the practice of managing an organization's data so it can be analyzed for decision making. Concept The concept of data management emerged alongside the evolution of computing technology. In the 1950s, as computers became more prevalent, organizations began to grapple with the challenge of organizing and storing data efficiently. Early methods relied on punch cards and manual sorting, which were labor-intensive and prone to errors. The introduction of database management systems in the 1970s marked a significant milestone, enabling structured storage and retrieval of data. By the 1980s, relational database models revolutionized data management, emphasizing the importance of data as an asset and fostering a data-centric mindset in business. This era also saw the rise of data governance practices, which prioritized the organization and regulation of data to ensure quality and complian ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Inference Attack
An Inference Attack is a data mining technique performed by analyzing data in order to illegitimately gain knowledge about a subject or database. A subject's sensitive information can be considered as leaked if an adversary can infer its real value with a high confidence. This is an example of breached information security. An Inference attack occurs when a user is able to infer from trivial information more robust information about a database without directly accessing it. The object of Inference attacks is to piece together information at one security level to determine a fact that should be protected at a higher security level. While inference attacks were originally discovered as a threat in statistical databases, today they also pose a major privacy threat in the domain of mobile and IoT sensor data. Data from accelerometers, which can be accessed by third-party apps without user permission in many mobile devices, has been used to infer rich information about users based on t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
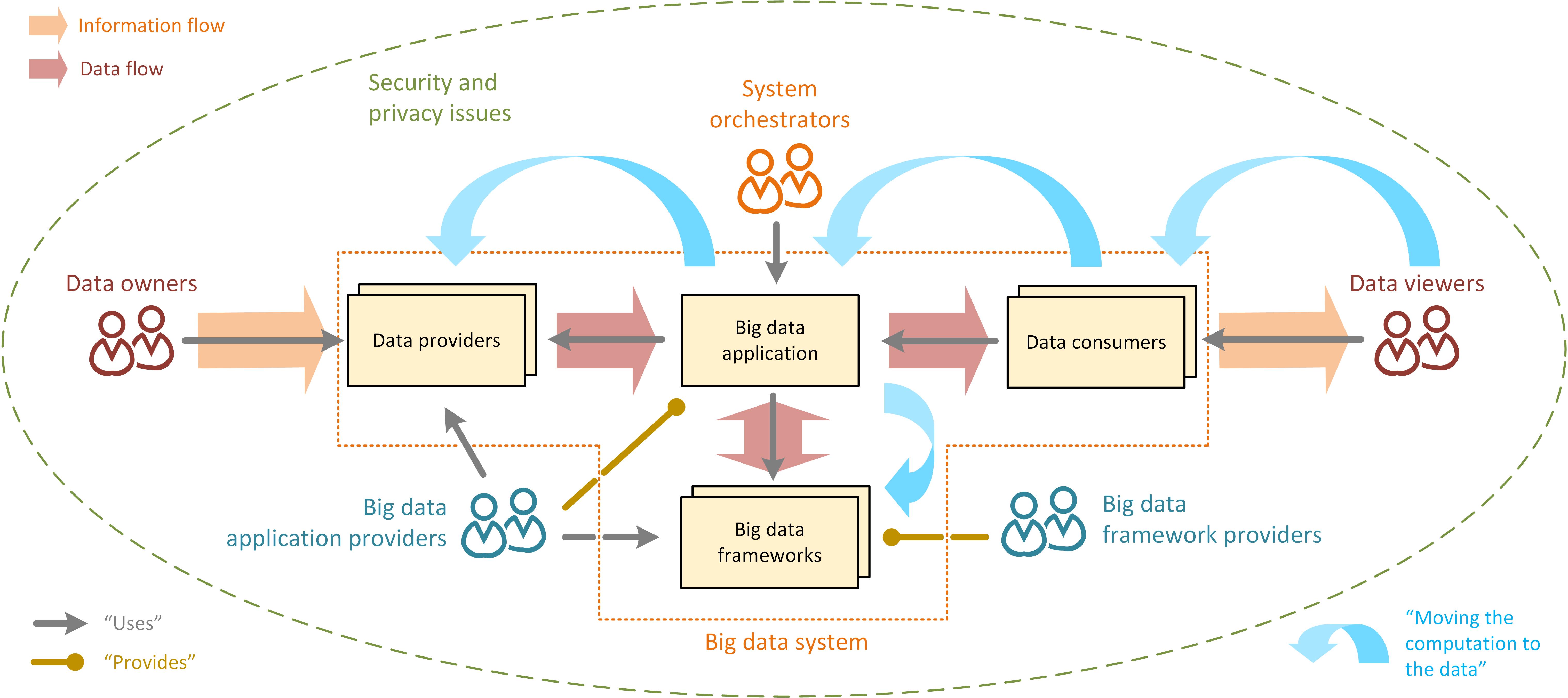
Big Data
Big data primarily refers to data sets that are too large or complex to be dealt with by traditional data processing, data-processing application software, software. Data with many entries (rows) offer greater statistical power, while data with higher complexity (more attributes or columns) may lead to a higher false discovery rate. Big data analysis challenges include Automatic identification and data capture, capturing data, Computer data storage, data storage, data analysis, search, Data sharing, sharing, Data transmission, transfer, Data visualization, visualization, Query language, querying, updating, information privacy, and data source. Big data was originally associated with three key concepts: ''volume'', ''variety'', and ''velocity''. The analysis of big data presents challenges in sampling, and thus previously allowing for only observations and sampling. Thus a fourth concept, ''veracity,'' refers to the quality or insightfulness of the data. Without sufficient investm ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Personally Identifiable Information
Personal data, also known as personal information or personally identifiable information (PII), is any information related to an identifiable person. The abbreviation PII is widely used in the United States, but the phrase it abbreviates has four common variants based on ''personal'' or ''personally'', and ''identifiable'' or ''identifying''. Not all are equivalent, and for legal purposes the effective definitions vary depending on the jurisdiction and the purposes for which the term is being used. Under European Union and United Kingdom data protection regimes, which centre primarily on the General Data Protection Regulation (GDPR), the term "personal data" is significantly broader, and determines the scope of the regulatory regime. National Institute of Standards and Technology Special Publication 800-122 defines personally identifiable information as "any information about an individual maintained by an agency, including (1) any information that can be used to distinguish or t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Encryption
In Cryptography law, cryptography, encryption (more specifically, Code, encoding) is the process of transforming information in a way that, ideally, only authorized parties can decode. This process converts the original representation of the information, known as plaintext, into an alternative form known as ciphertext. Despite its goal, encryption does not itself prevent interference but denies the intelligible content to a would-be interceptor. For technical reasons, an encryption scheme usually uses a pseudo-random encryption Key (cryptography), key generated by an algorithm. It is possible to decrypt the message without possessing the key but, for a well-designed encryption scheme, considerable computational resources and skills are required. An authorized recipient can easily decrypt the message with the key provided by the originator to recipients but not to unauthorized users. Historically, various forms of encryption have been used to aid in cryptography. Early encryption ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Genetic Privacy
Genetic privacy involves the concept of personal privacy concerning the storing, repurposing, provision to third parties, and displaying of information pertaining to one's genetic information. This concept also encompasses privacy regarding the ability to identify specific individuals by their genetic sequence, and the potential to gain information on specific characteristics about that person via portions of their genetic information, such as their propensity for specific diseases or their immediate or distant ancestry. With the public release of genome sequence information of participants in large-scale research studies, questions regarding participant privacy have been raised. In some cases, it has been shown that it is possible to identify previously anonymous participants from large-scale genetic studies that released gene sequence information. Genetic privacy concerns also arise in the context of criminal law because the government can sometimes overcome criminal suspects' ge ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Genetic Data
A genome is all the genetic information of an organism. It consists of nucleotide sequences of DNA (or RNA in RNA viruses). The nuclear genome includes protein-coding genes and non-coding genes, other functional regions of the genome such as regulatory sequences (see non-coding DNA), and often a substantial fraction of junk DNA with no evident function. Almost all eukaryotes have mitochondria and a small mitochondrial genome. Algae and plants also contain chloroplasts with a chloroplast genome. The study of the genome is called genomics. The genomes of many organisms have been sequenced and various regions have been annotated. The first genome to be sequenced was that of the virus φX174 in 1977; the first genome sequence of a prokaryote (''Haemophilus influenzae'') was published in 1995; the yeast (''Saccharomyces cerevisiae'') genome was the first eukaryotic genome to be sequenced in 1996. The Human Genome Project was started in October 1990, and the first draft sequences of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Health Insurance Portability And Accountability Act
The Health Insurance Portability and Accountability Act of 1996 (HIPAA or the Ted Kennedy, Kennedy–Nancy Kassebaum, Kassebaum Act) is a United States Act of Congress enacted by the 104th United States Congress and signed into law by President Bill Clinton on August 21, 1996. It aimed to alter the transfer of healthcare information, stipulated the guidelines by which personally identifiable information maintained by the healthcare and healthcare insurance industries should be protected from fraud and theft, and addressed some limitations on Health insurance in the United States, healthcare insurance coverage. It generally prohibits Health professional, healthcare providers and businesses called covered entities from disclosing protected information to anyone other than a patient and the patient's authorized representatives without their consent. The bill does not restrict patients from receiving information about themselves (with limited exceptions). Furthermore, it does not proh ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data Confidentiality
Confidentiality involves a set of rules or a promise sometimes executed through confidentiality agreements that limits the access to or places restrictions on the distribution of certain types of information. Legal confidentiality By law, lawyers are often required to keep confidential anything on the representation of a client. The duty of confidentiality is much broader than the attorney–client evidentiary privilege, which only covers ''communications'' between the attorney and the client. Both the privilege and the duty serve the purpose of encouraging clients to speak frankly about their cases. This way, lawyers can carry out their duty to provide clients with zealous representation. Otherwise, the opposing side may be able to surprise the lawyer in court with something he did not know about his client, which may weaken the client's position. Also, a distrustful client might hide a relevant fact he thinks is incriminating, but that a skilled lawyer could turn to the cli ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Patient Privacy
Medical privacy, or health privacy, is the practice of maintaining the security and confidentiality of patient records. It involves both the conversational discretion of health care providers and the security of medical records. The terms can also refer to the physical privacy of patients from other patients and providers while in a medical facility, and to modesty in medical settings. Modern concerns include the degree of disclosure to insurance companies, employers, and other third parties. The advent of electronic medical records (EMR) and patient care management systems (PCMS) have raised new concerns about privacy, balanced with efforts to reduce duplication of services and medical errors. Most developed countries including Australia, Canada, Turkey, the United Kingdom, the United States, New Zealand, and the Netherlands have enacted laws protecting people's medical health privacy. However, many of these health-securing privacy laws have proven less effective in practice th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
E-health
eHealth describes healthcare services which are supported by digital processes, communication or technology such as electronic prescribing, Telehealth, or Electronic health record, Electronic Health Records (EHRs). The term "eHealth" originated in the 1990s, initially conceived as "Internet medicine," but has since evolved to have a broader range of technologies and innovations aimed at enhancing healthcare delivery and accessibility. According to the World Health Organization (WHO), eHealth encompasses not only internet-based healthcare services but also modern advancements such as artificial intelligence, mHealth (mobile health), and telehealth, which collectively aim to improve accessibility and efficiency in healthcare delivery. Usage of the term varies widely. A study in 2005 found 51 unique definitions of eHealth, reflecting its diverse applications and interpretations. While some argue that it is interchangeable with health informatics as a broad term covering electronic/ ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |