|
Proxify AB
If you are looking for Proxify (Company) Proxify is a partly free, single-serving website that enables users to communicate more anonymously on the Internet. An example of this is to have Proxify use an SSH tunnel, already created and listening in on the localhost. This can be done using PuTTy to dynamically listen in to the host and redirecting traffic through the tunnel. Proxify is then used to hook applications into using the tunnel without configuring the different applications itself. Proxify matches its registration information with a WHOIS database, as reassurance. There are three general pre-configured options (max speed, max security, or compatibility) with users able to tweak the settings otherwise. Although free searches are offered, a message may appear: "Proxify is experiencing higher than normal traffic volume. We must restrict access to our free service during peak usage times to ensure the best possible experience for paid subscribers. Please login to your accoun ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Proxify AB
If you are looking for Proxify (Company) Proxify is a partly free, single-serving website that enables users to communicate more anonymously on the Internet. An example of this is to have Proxify use an SSH tunnel, already created and listening in on the localhost. This can be done using PuTTy to dynamically listen in to the host and redirecting traffic through the tunnel. Proxify is then used to hook applications into using the tunnel without configuring the different applications itself. Proxify matches its registration information with a WHOIS database, as reassurance. There are three general pre-configured options (max speed, max security, or compatibility) with users able to tweak the settings otherwise. Although free searches are offered, a message may appear: "Proxify is experiencing higher than normal traffic volume. We must restrict access to our free service during peak usage times to ensure the best possible experience for paid subscribers. Please login to your accoun ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Anonymizer
An anonymizer or an anonymous proxy is a tool that attempts to make activity on the Internet untraceable. It is a proxy server computer that acts as an intermediary and privacy shield between a client computer and the rest of the Internet. It accesses the Internet on the user's behalf, protecting personal information of the user by hiding the client computer's identifying information. Anonymous proxy is the opposite of transparent proxy, which sends user information in the connection request header. Purposes There are many reasons for using anonymizers, such as minimizing risk, prevention of identity theft, or protecting search histories from public disclosure. Some countries apply heavy censorship on the internet. Anonymizers can help to allow free access to all of the internet content, but they cannot help against persecution for accessing the anonymizer website itself. Furthermore, as information itself about anonymizer websites are banned in those countries, users are war ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
WHOIS
WHOIS (pronounced as the phrase "who is") is a query and response protocol that is widely used for querying databases that store the registered users or assignees of an Internet resource, such as a domain name, an IP address block or an autonomous system, but is also used for a wider range of other information. The protocol stores and delivers database content in a human-readable format.RFC 3912, ''WHOIS Protocol Specification'', L. Daigle (September 2004) The current iteration of the WHOIS protocol was drafted by the Internet Society, and is documented in . Whois is also the name of the command-line utility on most UNIX systems used to make WHOIS protocol queries. In addition WHOIS has a sister protocol called ''Referral Whois'' ( RWhois). History Elizabeth Feinler and her team (who had created the Resource Directory for ARPANET) were responsible for creating the first WHOIS directory in the early 1970s. Feinler set up a server in Stanford's Network Information Center (NIC) w ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
HTTPS
Hypertext Transfer Protocol Secure (HTTPS) is an extension of the Hypertext Transfer Protocol (HTTP). It is used for secure communication over a computer network, and is widely used on the Internet. In HTTPS, the communication protocol is encrypted using Transport Layer Security (TLS) or, formerly, Secure Sockets Layer (SSL). The protocol is therefore also referred to as HTTP over TLS, or HTTP over SSL. The principal motivations for HTTPS are authentication of the accessed website, and protection of the privacy and integrity of the exchanged data while in transit. It protects against man-in-the-middle attacks, and the bidirectional encryption of communications between a client and server protects the communications against eavesdropping and tampering. The authentication aspect of HTTPS requires a trusted third party to sign server-side digital certificates. This was historically an expensive operation, which meant fully authenticated HTTPS connections were usually found only ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Man-in-the-middle Attack
In cryptography and computer security, a man-in-the-middle, monster-in-the-middle, machine-in-the-middle, monkey-in-the-middle, meddler-in-the-middle, manipulator-in-the-middle (MITM), person-in-the-middle (PITM) or adversary-in-the-middle (AiTM) attack is a cyberattack where the attacker secretly relays and possibly alters the communications between two parties who believe that they are directly communicating with each other, as the attacker has inserted themselves between the two parties. One example of a MITM attack is active eavesdropping, in which the attacker makes independent connections with the victims and relays messages between them to make them believe they are talking directly to each other over a private connection, when in fact the entire conversation is controlled by the attacker. The attacker must be able to intercept all relevant messages passing between the two victims and inject new ones. This is straightforward in many circumstances; for example, an attacker wit ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
IP Address
An Internet Protocol address (IP address) is a numerical label such as that is connected to a computer network that uses the Internet Protocol for communication.. Updated by . An IP address serves two main functions: network interface identification and location addressing. Internet Protocol version 4 (IPv4) defines an IP address as a 32-bit number. However, because of the growth of the Internet and the depletion of available IPv4 addresses, a new version of IP (IPv6), using 128 bits for the IP address, was standardized in 1998. IPv6 deployment has been ongoing since the mid-2000s. IP addresses are written and displayed in human-readable notations, such as in IPv4, and in IPv6. The size of the routing prefix of the address is designated in CIDR notation by suffixing the address with the number of significant bits, e.g., , which is equivalent to the historically used subnet mask . The IP address space is managed globally by the Internet Assigned Numbers Authority (IA ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Firewall (computing)
In computing, a firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. A firewall typically establishes a barrier between a trusted network and an untrusted network, such as the Internet. History The term ''firewall'' originally referred to a wall intended to confine a fire within a line of adjacent buildings. Later uses refer to similar structures, such as the metal sheet separating the engine compartment of a vehicle or aircraft from the passenger compartment. The term was applied in the late 1980s to network technology that emerged when the Internet was fairly new in terms of its global use and connectivity. The predecessors to firewalls for network security were routers used in the late 1980s. Because they already segregated networks, routers could apply filtering to packets crossing them. Before it was used in real-life computing, the term appeared in the 1983 computer-hacking movie ' ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
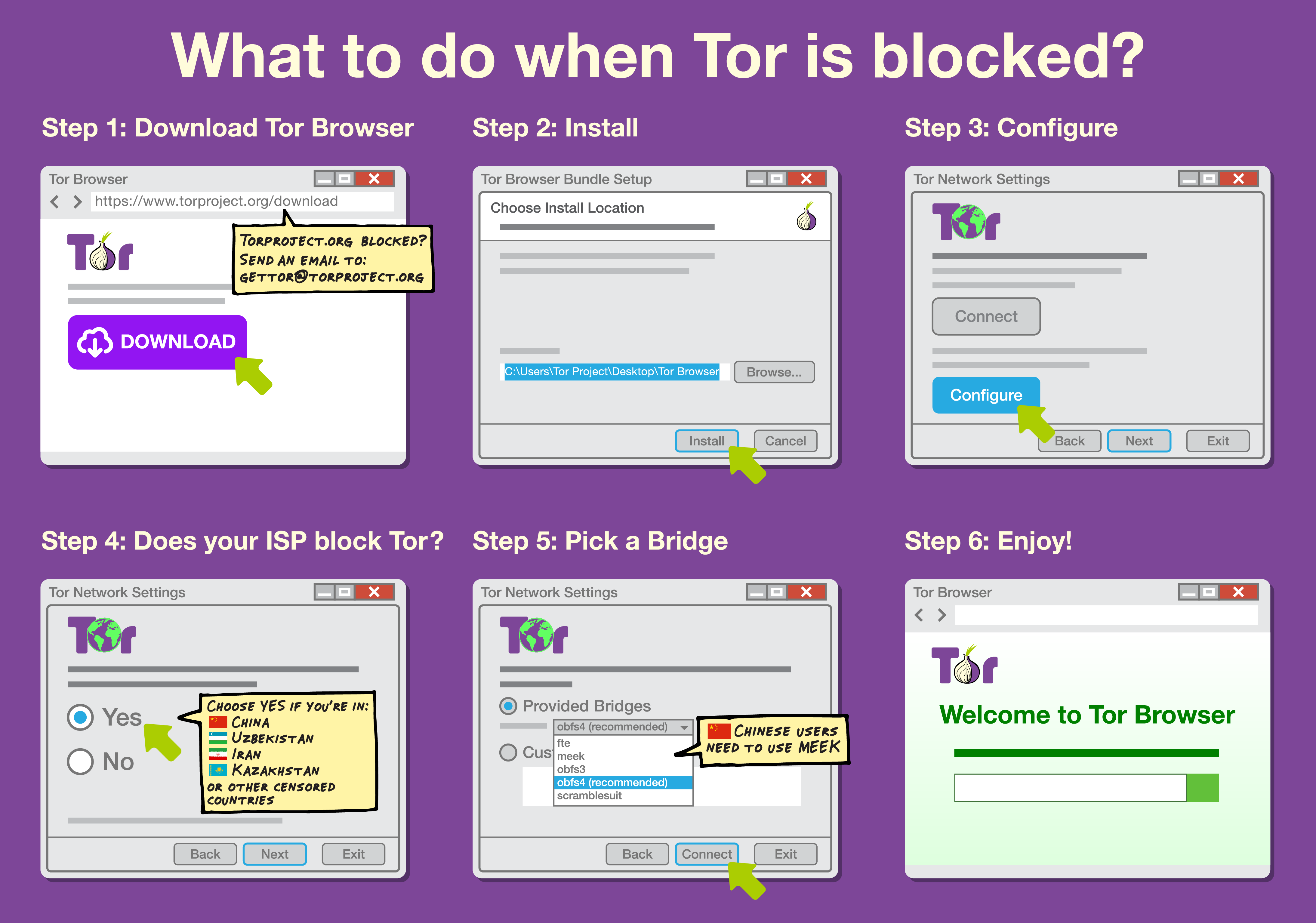
Internet Censorship Circumvention
Internet censorship circumvention is the use of various methods and tools to bypass internet censorship. Various techniques and methods are used to bypass Internet censorship, and have differing ease of use, speed, security, and risks. Some methods, such as the use of alternate DNS servers, evade blocking by using an alternate address or address lookup system to access the site. Techniques using website mirrors or archive sites rely on other copies of the site being available at different locations. Additionally, there are solutions that rely on gaining access to an Internet connection that is not subject to filtering, often in a different jurisdiction not subject to the same censorship laws, using technologies such as proxying, virtual private networks, or anonymization networks. An arms race has developed between censors and developers of circumvention software, resulting in more sophisticated blocking techniques by censors and the development of harder-to-detect tools by rese ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |