|
Onion Routing
Onion routing is a technique for anonymous communication over a computer network. In an onion network, messages are encapsulated in layers of encryption, analogous to layers of an onion. The encrypted data is transmitted through a series of network nodes called onion routers, each of which "peels" away a single layer, uncovering the data's next destination. When the final layer is decrypted, the message arrives at its destination. The sender remains anonymous because each intermediary knows only the location of the immediately preceding and following nodes. While onion routing provides a high level of security and anonymity, there are methods to break the anonymity of this technique, such as timing analysis. History Onion routing was developed in the mid-1990s at the U.S. Naval Research Laboratory by employees Paul Syverson, Michael G. Reed, and David Goldschlag to protect U.S. intelligence communications online. It was then refined by the Defense Advanced Research Projects ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Onion Diagram
An onion diagram is a kind of chart that shows the Dependency (project management), dependencies among parts of an organization or process. The chart displays items in concentric circles, where the items in each ring depend on the items in the smaller rings. Information The onion diagram is able to show layers of a complete system in a few circles. Each of the circles is able to represent a component that is dependent upon the component on the inside of it shown by the circle inside of it. The main concept of the diagram is shown by the center circle of the diagram. This chart is used due to the fact that it has a clear visual representation that is easy to read, and it has a strong visual impact. Variations There is also the cultural onion which has seven layers to it including artifacts, behaviors, feelings, values, beliefs, worldview and ultimate allegiance. These layers organize a person's reality and life. The outer most layers are the most accessible while the in-depth ones ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
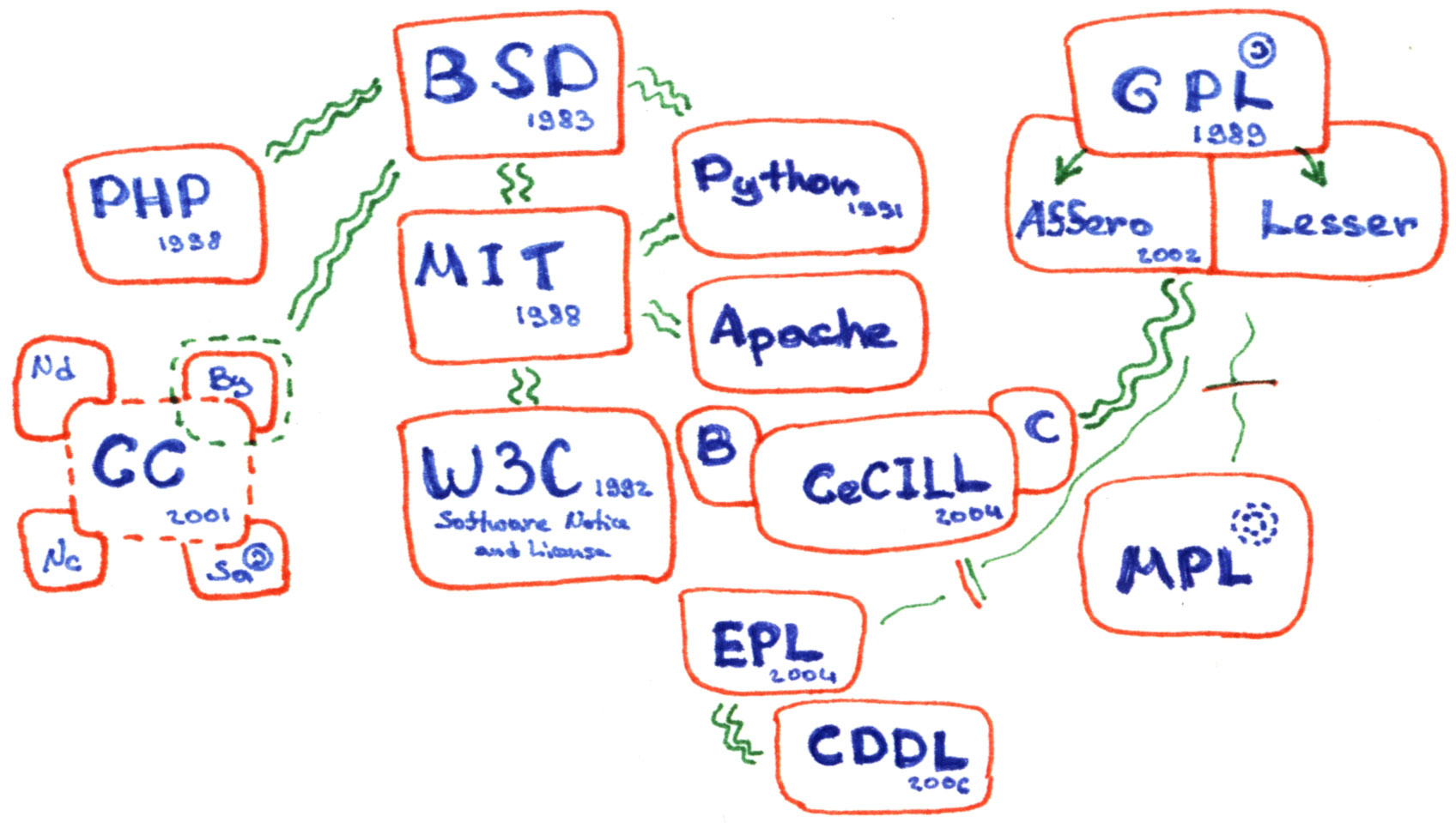
Free License
A free license or open license is a license which allows others to reuse another creator’s work as they wish. Without a special license, these uses are normally prohibited by copyright, patent or commercial license. Most free licenses are worldwide, royalty-free, non-exclusive, and perpetual (see copyright durations). Free licenses are often the basis of crowdsourcing and crowdfunding projects. The invention of the term "free license" and the focus on the rights of users were connected to the sharing traditions of the hacker culture of the 1970s public domain software ecosystem, the social and political free software movement (since 1980) and the open source movement (since the 1990s). These rights were codified by different groups and organizations for different domains in Free Software Definition, Open Source Definition, Debian Free Software Guidelines, Definition of Free Cultural Works and The Open Definition. [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
End-to-end Encryption
End-to-end encryption (E2EE) is a system of communication where only the communicating users can read the messages. In principle, it prevents potential eavesdroppers – including telecommunications service providers, telecom providers, Internet providers, malicious actors, and even the provider of the communication service – from being able to access the Key (cryptography), cryptographic keys needed to Encryption, decrypt the conversation. End-to-end encryption is intended to prevent data being read or secretly modified, other than by the true sender and recipient(s). The messages are encrypted by the sender but the third party does not have a means to decrypt them, and stores them encrypted. The recipients retrieve the encrypted data and decrypt it themselves. Because no third parties can decipher the data being communicated or stored, for example, companies that provide end-to-end encryption are unable to hand over texts of their customers' messages to the authorities. In ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Transport Layer Security
Transport Layer Security (TLS) is a cryptographic protocol designed to provide communications security over a computer network. The protocol is widely used in applications such as email, instant messaging, and voice over IP, but its use in securing HTTPS remains the most publicly visible. The TLS protocol aims primarily to provide security, including privacy (confidentiality), integrity, and authenticity through the use of cryptography, such as the use of certificates, between two or more communicating computer applications. It runs in the presentation layer and is itself composed of two layers: the TLS record and the TLS handshake protocols. The closely related Datagram Transport Layer Security (DTLS) is a communications protocol providing security to datagram-based applications. In technical writing you often you will see references to (D)TLS when it applies to both versions. TLS is a proposed Internet Engineering Task Force (IETF) standard, first defined in 1999, and th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Garlic Routing
Garlic routing is a variant of onion routing that encrypts multiple messages together to make it more difficult for attackers to perform traffic analysis and to increase the speed of data transfer. Michael J. Freedman defined "garlic routing" as an extension of onion routing, in which multiple messages are bundled together. He called each message a "bulb", whereas I2P calls them "garlic cloves". All messages, each with their own delivery instructions, are exposed at the endpoint. This allows the efficient bundling of an onion routing "reply block" with the original message. Garlic routing is one of the key factors that distinguishes I2P from Tor and other privacy or encryption networks. The name alludes to the garlic plant, whose structure this protocol resembles. "Garlic routing" was first coined by Michael J. Freedman in Roger Dingledine's Free Haven Master's thesis Section 8.1.1 (June 2000), as derived from Onion Routing. However, the garlic routing implementation in I2P di ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
HTTPS
Hypertext Transfer Protocol Secure (HTTPS) is an extension of the Hypertext Transfer Protocol (HTTP). It is used for secure communication over a computer network, and is widely used on the Internet. In HTTPS, the communication protocol is encrypted using Transport Layer Security (TLS) or, formerly, Secure Sockets Layer (SSL). The protocol is therefore also referred to as HTTP over TLS, or HTTP over SSL. The principal motivations for HTTPS are authentication of the accessed website, and protection of the privacy and integrity of the exchanged data while in transit. It protects against man-in-the-middle attacks, and the bidirectional encryption of communications between a client and server protects the communications against eavesdropping and tampering. The authentication aspect of HTTPS requires a trusted third party to sign server-side digital certificates. This was historically an expensive operation, which meant fully authenticated HTTPS connections were usually found only ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Internet Service Provider
An Internet service provider (ISP) is an organization that provides services for accessing, using, or participating in the Internet. ISPs can be organized in various forms, such as commercial, community-owned, non-profit, or otherwise privately owned. Internet services typically provided by ISPs can include Internet access, Internet transit, domain name registration, web hosting, Usenet service, and colocation. An ISP typically serves as the access point or the gateway that provides a user access to everything available on the Internet. Such a network can also be called as an eyeball network. History The Internet (originally ARPAnet) was developed as a network between government research laboratories and participating departments of universities. Other companies and organizations joined by direct connection to the backbone, or by arrangements through other connected companies, sometimes using dialup tools such as UUCP. By the late 1980s, a process was set in place ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Shared Secret
In cryptography, a shared secret is a piece of data, known only to the parties involved, in a secure communication. This usually refers to the key of a symmetric cryptosystem. The shared secret can be a password, a passphrase, a big number, or an array of randomly chosen bytes. The shared secret is either shared beforehand between the communicating parties, in which case it can also be called a pre-shared key, or it is created at the start of the communication session by using a key-agreement protocol, for instance using public-key cryptography such as Diffie–Hellman or using symmetric-key cryptography such as Kerberos. The shared secret can be used for authentication (for instance when logging into a remote system) using methods such as challenge–response or it can be fed to a key derivation function to produce one or more keys to use for encryption and/or MACing of messages. To make unique session and message keys the shared secret is usually combined with an i ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Public Key
Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a public key and a corresponding private key. Key pairs are generated with cryptographic algorithms based on mathematical problems termed one-way functions. Security of public-key cryptography depends on keeping the private key secret; the public key can be openly distributed without compromising security. In a public-key encryption system, anyone with a public key can encrypt a message, yielding a ciphertext, but only those who know the corresponding private key can decrypt the ciphertext to obtain the original message. For example, a journalist can publish the public key of an encryption key pair on a web site so that sources can send secret messages to the news organization in ciphertext. Only the journalist who knows the corresponding private key can decrypt the ciphertexts to obtain the sources' messages—an eavesdr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Asymmetric Key Cryptography
Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a public key and a corresponding private key. Key pairs are generated with cryptographic algorithms based on mathematical problems termed one-way functions. Security of public-key cryptography depends on keeping the private key secret; the public key can be openly distributed without compromising security. In a public-key encryption system, anyone with a public key can encrypt a message, yielding a ciphertext, but only those who know the corresponding private key can decrypt the ciphertext to obtain the original message. For example, a journalist can publish the public key of an encryption key pair on a web site so that sources can send secret messages to the news organization in ciphertext. Only the journalist who knows the corresponding private key can decrypt the ciphertexts to obtain the sources' messages—an eavesdrop ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Washington Post
''The Washington Post'' (also known as the ''Post'' and, informally, ''WaPo'') is an American daily newspaper published in Washington, D.C. It is the most widely circulated newspaper within the Washington metropolitan area and has a large national audience. Daily broadsheet editions are printed for D.C., Maryland, and Virginia. The ''Post'' was founded in 1877. In its early years, it went through several owners and struggled both financially and editorially. Financier Eugene Meyer purchased it out of bankruptcy in 1933 and revived its health and reputation, work continued by his successors Katharine and Phil Graham (Meyer's daughter and son-in-law), who bought out several rival publications. The ''Post'' 1971 printing of the Pentagon Papers helped spur opposition to the Vietnam War. Subsequently, in the best-known episode in the newspaper's history, reporters Bob Woodward and Carl Bernstein led the American press's investigation into what became known as the Watergate s ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |