|
End-to-end Encryption
End-to-end encryption (E2EE) is a system of communication where only the communicating users can read the messages. In principle, it prevents potential eavesdroppers – including telecommunications service providers, telecom providers, Internet providers, malicious actors, and even the provider of the communication service – from being able to access the Key (cryptography), cryptographic keys needed to Encryption, decrypt the conversation. End-to-end encryption is intended to prevent data being read or secretly modified, other than by the true sender and recipient(s). The messages are encrypted by the sender but the third party does not have a means to decrypt them, and stores them encrypted. The recipients retrieve the encrypted data and decrypt it themselves. Because no third parties can decipher the data being communicated or stored, for example, companies that provide end-to-end encryption are unable to hand over texts of their customers' messages to the authorities. In ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Telecommunications Service Providers
A telephone company, also known as a telco, telephone service provider, or telecommunications operator, is a kind of communications service provider (CSP), more precisely a telecommunications service provider (TSP), that provides telecommunications services such as telephony and data communications access. Many telephone companies were at one time government agencies or privately owned but state-regulated monopoly, monopolies. The government agencies are often referred to, primarily in Europe, as PTTs (postal, telegraph and telephone services). Telephone companies are common carriers, and in the United States are also called local exchange carriers. With the advent of mobile telephony, telephone companies now include wireless carriers, or mobile network operators. Most telephone companies now also function as internet service providers (ISPs), and the distinction between a telephone company and an ISP may disappear completely over time, as the current trend for supplier converg ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
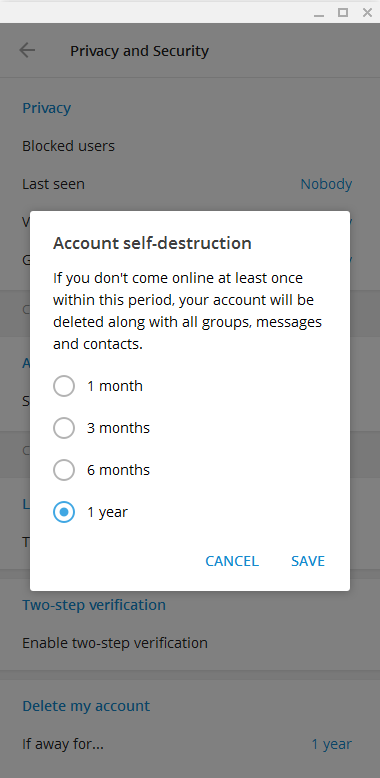
Telegram (software)
Telegram Messenger is a globally accessible freemium, cross-platform, encrypted, cloud-based and centralized instant messaging (IM) service. The application also provides optional end-to-end encrypted chats, popularly known as secret chat and video calling, VoIP, file sharing and several other features. It was launched for iOS on 14 August 2013 and Android on 20 October 2013. The servers of Telegram are distributed worldwide with five data centers in different parts of the world, while the operational center is based in Dubai, United Arab Emirates. Various client apps are available for desktop and mobile platforms including official apps for Android, iOS, Windows, macOS, and Linux (although registration requires an iOS or Android device and a working phone number). There are also two official Telegram web twin apps, WebK and WebZ, and numerous unofficial clients that make use of Telegram's protocol. Telegram's official components are open source, with the exception of the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
One-to-one Mapping
In mathematics, an injective function (also known as injection, or one-to-one function) is a function that maps distinct elements of its domain to distinct elements; that is, implies . (Equivalently, implies in the equivalent contrapositive statement.) In other words, every element of the function's codomain is the image of one element of its domain. The term must not be confused with that refers to bijective functions, which are functions such that each element in the codomain is an image of exactly one element in the domain. A homomorphism between algebraic structures is a function that is compatible with the operations of the structures. For all common algebraic structures, and, in particular for vector spaces, an is also called a . However, in the more general context of category theory, the definition of a monomorphism differs from that of an injective homomorphism. This is thus a theorem that they are equivalent for algebraic structures; see for more details. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Natural Language
In neuropsychology, linguistics, and philosophy of language, a natural language or ordinary language is any language that has evolved naturally in humans through use and repetition without conscious planning or premeditation. Natural languages can take different forms, such as speech or signing. They are distinguished from constructed and formal languages such as those used to program computers or to study logic. Defining natural language Natural language can be broadly defined as different from * artificial and constructed languages, e.g. computer programming languages * constructed international auxiliary languages * non-human communication systems in nature such as whale and other marine mammal vocalizations or honey bees' waggle dance. All varieties of world languages are natural languages, including those that are associated with linguistic prescriptivism or language regulation. ( Nonstandard dialects can be viewed as a wild type in comparison with stan ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Binary-to-text Encoding
A binary-to-text encoding is encoding of data in plain text. More precisely, it is an encoding of binary data in a sequence of printable characters. These encodings are necessary for transmission of data when the channel does not allow binary data (such as email or NNTP) or is not 8-bit clean. PGP documentation () uses the term "ASCII armor" for binary-to-text encoding when referring to Base64. Overview The basic need for a binary-to-text encoding comes from a need to communicate arbitrary binary data over preexisting communications protocols that were designed to carry only English language human-readable text. Those communication protocols may only be 7-bit safe (and within that avoid certain ASCII control codes), and may require line breaks at certain maximum intervals, and may not maintain whitespace. Thus, only the 94 printable ASCII characters are "safe" to use to convey data. Description The ASCII text-encoding standard uses 7 bits to encode characters. With this i ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Public Key Fingerprint
In public-key cryptography, a public key fingerprint is a short sequence of bytes used to identify a longer public key. Fingerprints are created by applying a cryptographic hash function to a public key. Since fingerprints are shorter than the keys they refer to, they can be used to simplify certain key management tasks. In Microsoft software, "thumbprint" is used instead of "fingerprint." Creating public key fingerprints A public key fingerprint is typically created through the following steps: # A public key (and optionally some additional data) is encoded into a sequence of bytes. To ensure that the same fingerprint can be recreated later, the encoding must be deterministic, and any additional data must be exchanged and stored alongside the public key. The additional data is typically information which anyone using the public key should be aware of. Examples of additional data include: which protocol versions the key should be used with (in the case of PGP fingerprints); ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Web Of Trust
In cryptography, a web of trust is a concept used in PGP, GnuPG, and other OpenPGP-compatible systems to establish the authenticity of the binding between a public key and its owner. Its decentralized trust model is an alternative to the centralized trust model of a public key infrastructure (PKI), which relies exclusively on a certificate authority (or a hierarchy of such). As with computer networks, there are many independent webs of trust, and any user (through their public key certificate) can be a part of, and a link between, multiple webs. The web of trust concept was first put forth by PGP creator Phil Zimmermann in 1992 in the manual for PGP version 2.0: Note the use of the word emergence in this context. The web of trust makes use of the concept of emergence. Operation of a web of trust All OpenPGP-compliant implementations include a certificate vetting scheme to assist with this; its operation has been termed a web of trust. OpenPGP certificates (which include ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Certificate Authority Security Council
The Certificate Authority Security Council (CASC) is a multi-vendor industry advocacy group created to conduct research, promote Internet security standards and educate the public on Internet security issues. History The group was founded in February 2013 with the seven largest certificate authorities, issuers of SSL certificates — Comodo, Symantec, Trend Micro, DigiCert, Entrust, GlobalSign and GoDaddy. DigiCert withdrew from the group June 15, 2018. Objectives The CASC supports the efforts of the CA/Browser Forum and other standards-setting bodies. They support the development of enhancements that improve the Secure Sockets Layer (SSL) and the operations of the certificate authorities (CA). According to Robin Alden, CTO of Comodo and member of the Council, the CASC will serve as a united front for all of the CAs involved: "While not a standards-setting organization, we’re committed to supplementing standards-setting organizations by providing education, research, and ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Authentication Cookie
HTTP cookies (also called web cookies, Internet cookies, browser cookies, or simply cookies) are small blocks of data created by a web server while a user is browsing a website and placed on the user's computer or other device by the user's web browser. Cookies are placed on the device used to access a website, and more than one cookie may be placed on a user's device during a session. Cookies serve useful and sometimes essential functions on the web. They enable web servers to store stateful information (such as items added in the shopping cart in an online store) on the user's device or to track the user's browsing activity (including clicking particular buttons, logging in, or recording which pages were visited in the past). They can also be used to save for subsequent use information that the user previously entered into form fields, such as names, addresses, passwords, and payment card numbers. Authentication cookies are commonly used by web servers to authenticate that ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Public Key Cryptography
Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a public key and a corresponding private key. Key pairs are generated with cryptographic algorithms based on mathematical problems termed one-way functions. Security of public-key cryptography depends on keeping the private key secret; the public key can be openly distributed without compromising security. In a public-key encryption system, anyone with a public key can encrypt a message, yielding a ciphertext, but only those who know the corresponding private key can decrypt the ciphertext to obtain the original message. For example, a journalist can publish the public key of an encryption key pair on a web site so that sources can send secret messages to the news organization in ciphertext. Only the journalist who knows the corresponding private key can decrypt the ciphertexts to obtain the sources' messages—an eavesd ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Key Exchange
Key exchange (also key establishment) is a method in cryptography by which cryptographic keys are exchanged between two parties, allowing use of a cryptographic algorithm. If the sender and receiver wish to exchange encrypted messages, each must be equipped to encrypt messages to be sent and decrypt messages received. The nature of the equipping they require depends on the encryption technique they might use. If they use a code, both will require a copy of the same codebook. If they use a cipher, they will need appropriate keys. If the cipher is a symmetric key cipher, both will need a copy of the same key. If it is an asymmetric key cipher with the public/private key property, both will need the other's public key. Channel of exchange Key exchange is done either in-band or out-of-band. The key exchange problem The key exchange problem describes ways to exchange whatever keys or other information are needed for establishing a secure communication channel so that no one els ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Client-side Encryption
Client-side encryption is the cryptographic technique of encrypting data on the sender's side, before it is transmitted to a server such as a cloud storage service. Client-side encryption features an encryption key that is not available to the service provider, making it difficult or impossible for service providers to decrypt hosted data. Client-side encryption allows for the creation of applications whose providers cannot access the data its users have stored, thus offering a high level of privacy. Those applications are sometimes marketed under the misleading term "zero-knowledge". Details Client-side encryption seeks to eliminate the potential for data to be viewed by service providers (or third parties that compel service providers to deliver access to data), client-side encryption ensures that data and files that are stored in the cloud can only be viewed on the client-side of the exchange. By remaining encrypted through each intermediary server, client-side encryption ensures ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |