|
Negative Testing
Negative testing is a method of testing an application or system to improve the likelihood that an application works as intended/specified and can handle unexpected input and user behavior. Invalid data is inserted to compare the output against the given input. Negative testing is also known as failure testing or error path testing. When performing negative testing exceptions are expected. This shows that the application is able to handle improper user behavior. Users input values that do not work in the system to test its ability to handle incorrect values or system failure. Purpose * The purpose of negative testing is to prevent the application from crashing and it also helps improve the quality of an application by detecting defects. * Negative testing helps you to improve the testing coverage of the application. * Negative testing makes the application more stable and reliable. * Negative testing together with positive testing allows users to test the application with any v ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Application Software
Application software is any computer program that is intended for end-user use not operating, administering or programming the computer. An application (app, application program, software application) is any program that can be categorized as application software. Common types of applications include word processor, media player and accounting software. The term ''application software'' refers to all applications collectively and can be used to differentiate from system and utility software. Applications may be bundled with the computer and its system software or published separately. Applications may be proprietary or open-source. The short term ''app'' (coined in 1981 or earlier) became popular with the 2008 introduction of the iOS App Store, to refer to applications for mobile devices such as smartphones and tablets. Later, with introduction of the Mac App Store (in 2010) and Windows Store (in 2011), the term was extended in popular use to include desktop a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Systems Failure
''Systems Failure'' is a role-playing game written by Bill Coffin and published by Palladium Books in July 1999. Contents The fictional premise for the game is that during the "Millennium bug" scare, actual "Bugs" appeared. They are energy beings from beyond Earth (whether another dimension or another planet is not clear) that invaded at the end of 1999, leaving a post-apocalyptic world in their wake. The Bugs feed on energy and are capable of transmitting themselves through modern power transmission and phone lines. The Bugs come in several varieties. There are the drone-like Army Ants who have only basic intelligence, the more intelligent Assassin Bugs who can replicate human speech, though imperfectly, and the flying Lightning Bugs, amongst others. All of them are able to turn themselves into energy or rapidly call up reinforcements. In addition to these, there are "brain bugs", a variety that can invade human minds and turn them into zombie-like servants of the Bugs. Playe ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Input Data
In computing, input/output (I/O, i/o, or informally io or IO) is the communication between an information processing system, such as a computer, and the outside world, such as another computer system, peripherals, or a human operator. Inputs are the signals or data received by the system and outputs are the signals or data sent from it. The term can also be used as part of an action; to "perform I/O" is to perform an input or output operation. are the pieces of hardware used by a human (or other system) to communicate with a computer. For instance, a keyboard or computer mouse is an input device for a computer, while monitors and printers are output devices. Devices for communication between computers, such as modems and network cards, typically perform both input and output operations. Any interaction with the system by an interactor is an input and the reaction the system responds is called the output. The designation of a device as either input or output depends on persp ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Crash (computing)
In computing, a crash, or system crash, occurs when a computer program such as a software application or an operating system stops functioning properly and exits. On some operating systems or individual applications, a crash reporting service will report the crash and any details relating to it (or give the user the option to do so), usually to the developer(s) of the application. If the program is a critical part of the operating system, the entire system may crash or hang, often resulting in a kernel panic or fatal system error. Most crashes are the result of a software bug. Typical causes include accessing invalid memory addresses, incorrect address values in the program counter, buffer overflow, overwriting a portion of the affected program code due to an earlier bug, executing invalid machine instructions (an illegal or unauthorized opcode), or triggering an unhandled exception. The original software bug that started this chain of events is typically considere ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
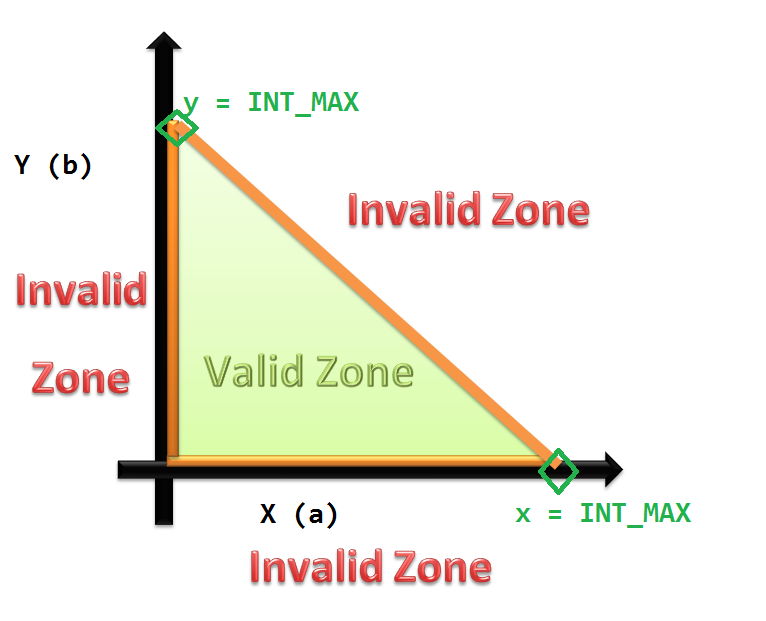
Boundary-value Analysis
Boundary-value analysis is a software testing technique in which tests are designed to include representatives of boundary values in a range. The idea comes from the Boundary (topology), boundary. Given that there is a set of test vectors to test the system, a topology can be defined on that set. Those inputs which belong to the same equivalence class as defined by the equivalence partitioning theory would constitute the basis (topology), basis. Given that the basis sets are neighbourhood (mathematics), neighbors, there would exist a boundary between them. The test vectors on either side of the boundary are called boundary values. In practice, this would require that the test vectors can be ordered, and that the individual parameters follows some kind of order (either partial order or total order). Formal definition Formally, the boundary values can be defined as below: :Let the set of the test vectors be . :Let's assume that there is an ordering relation defined over them, as . ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Test Scenario
Scenario testing is a software testing activity that uses scenarios: hypothetical stories to help the tester work through a complex problem or test system. The ideal scenario test is a credible, complex, compelling or motivating story; the outcome of which is easy to evaluate. These tests are usually different from test cases in that test cases are single steps whereas scenarios cover a number of steps. History Cem Kaner coined the phrase scenario test by October 2003. He commented that one of the most difficult aspects of testing was maintaining step-by-step test cases along with their expected results. His paper attempted to find a way to reduce the re-work of complicated written tests and incorporate the ease of use cases. A few months later, Hans Buwalda wrote about a similar approach he had been using that he called "soap opera testing". Like television soap operas these tests were both exaggerated in activity and condensed in time. The key to both approaches was to avoid step ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Equivalence Partitioning
Equivalence partitioning or equivalence class partitioning (ECP) is a software testing technique that divides the input data of a software unit into partitions of equivalent data from which test cases can be derived. In principle, test cases are designed to cover each partition at least once. This technique tries to define test cases that uncover classes of errors, thereby reducing the total number of test cases that must be developed. An advantage of this approach is reduction in the time required for testing software due to lesser number of test cases. Equivalence partitioning is typically applied to the inputs of a tested component, but may be applied to the outputs in rare cases. The equivalence partitions are usually derived from the requirements specification for input attributes that influence the processing of the test object. The fundamental concept of ECP comes from equivalence class which in turn comes from equivalence relation. A software system is in effect a comput ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data Analysis
Data analysis is the process of inspecting, Data cleansing, cleansing, Data transformation, transforming, and Data modeling, modeling data with the goal of discovering useful information, informing conclusions, and supporting decision-making. Data analysis has multiple facets and approaches, encompassing diverse techniques under a variety of names, and is used in different business, science, and social science domains. In today's business world, data analysis plays a role in making decisions more scientific and helping businesses operate more effectively. Data mining is a particular data analysis technique that focuses on statistical modeling and knowledge discovery for predictive rather than purely descriptive purposes, while business intelligence covers data analysis that relies heavily on aggregation, focusing mainly on business information. In statistical applications, data analysis can be divided into descriptive statistics, exploratory data analysis (EDA), and Statistical h ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |