|
Multiple Granularity Locking
In computer science, multiple granularity locking (MGL) is a locking method used in database management systems (DBMS) and relational databases. In multiple granularity locking, locks are set on objects that contain other objects. MGL exploits the hierarchical nature of the ''contains'' relationship. For example, a database may have files, which contain pages, which contain records. This can be thought of as a tree of objects, where each node contains its children. A lock on this structure (such as a shared or exclusive lock) locks the targeted node as well as all of its descendants. Multiple granularity locking is usually used with non-strict two-phase locking to guarantee serializability. Lock modes In addition to shared (S) locks and exclusive (X) locks from other locking schemes, like strict two-phase locking, MGL also uses intentional "locks", which do not directly lock a node, but instead denote the existence, or intent to add, a lock of the specified type lower in the node ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Science
Computer science is the study of computation, automation, and information. Computer science spans theoretical disciplines (such as algorithms, theory of computation, information theory, and automation) to practical disciplines (including the design and implementation of hardware and software). Computer science is generally considered an area of academic research and distinct from computer programming. Algorithms and data structures are central to computer science. The theory of computation concerns abstract models of computation and general classes of problems that can be solved using them. The fields of cryptography and computer security involve studying the means for secure communication and for preventing security vulnerabilities. Computer graphics and computational geometry address the generation of images. Programming language theory considers different ways to describe computational processes, and database theory concerns the management of repositories ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
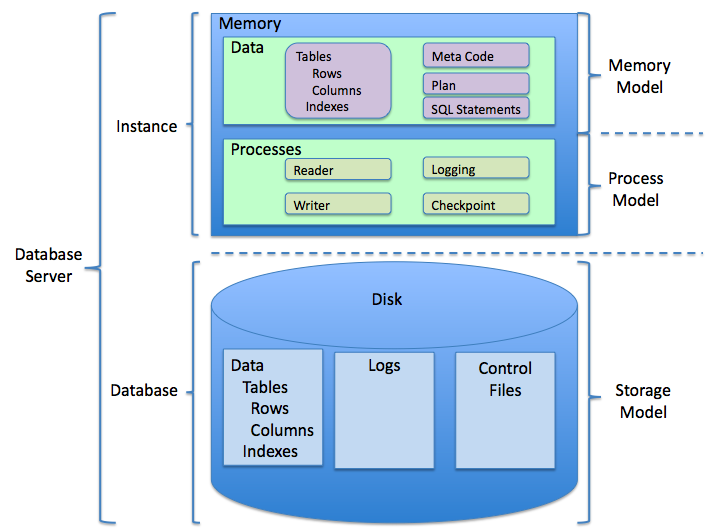
Database Management System
In computing, a database is an organized collection of data stored and accessed electronically. Small databases can be stored on a file system, while large databases are hosted on computer clusters or cloud storage. The design of databases spans formal techniques and practical considerations, including data modeling, efficient data representation and storage, query languages, security and privacy of sensitive data, and distributed computing issues, including supporting concurrent access and fault tolerance. A database management system (DBMS) is the software that interacts with end users, applications, and the database itself to capture and analyze the data. The DBMS software additionally encompasses the core facilities provided to administer the database. The sum total of the database, the DBMS and the associated applications can be referred to as a database system. Often the term "database" is also used loosely to refer to any of the DBMS, the database system or an applica ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Relational Database
A relational database is a (most commonly digital) database based on the relational model of data, as proposed by E. F. Codd in 1970. A system used to maintain relational databases is a relational database management system (RDBMS). Many relational database systems are equipped with the option of using the SQL (Structured Query Language) for querying and maintaining the database. History The term "relational database" was first defined by E. F. Codd at IBM in 1970. Codd introduced the term in his research paper "A Relational Model of Data for Large Shared Data Banks". In this paper and later papers, he defined what he meant by "relational". One well-known definition of what constitutes a relational database system is composed of Codd's 12 rules. However, no commercial implementations of the relational model conform to all of Codd's rules, so the term has gradually come to describe a broader class of database systems, which at a minimum: # Present the data to the user as rel ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Lock (computer Science)
In computer science, a lock or mutex (from mutual exclusion) is a synchronization primitive: a mechanism that enforces limits on access to a resource when there are many threads of execution. A lock is designed to enforce a mutual exclusion concurrency control policy, and with a variety of possible methods there exists multiple unique implementations for different applications. Types Generally, locks are ''advisory locks'', where each thread cooperates by acquiring the lock before accessing the corresponding data. Some systems also implement ''mandatory locks'', where attempting unauthorized access to a locked resource will force an exception in the entity attempting to make the access. The simplest type of lock is a binary semaphore. It provides exclusive access to the locked data. Other schemes also provide shared access for reading data. Other widely implemented access modes are exclusive, intend-to-exclude and intend-to-upgrade. Another way to classify locks is by what hap ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Tree (data Structure)
In computer science, a tree is a widely used abstract data type that represents a hierarchical tree structure with a set of connected nodes. Each node in the tree can be connected to many children (depending on the type of tree), but must be connected to exactly one parent, except for the ''root'' node, which has no parent. These constraints mean there are no cycles or "loops" (no node can be its own ancestor), and also that each child can be treated like the root node of its own subtree, making recursion a useful technique for tree traversal. In contrast to linear data structures, many trees cannot be represented by relationships between neighboring nodes in a single straight line. Binary trees are a commonly used type, which constrain the number of children for each parent to exactly two. When the order of the children is specified, this data structure corresponds to an ordered tree in graph theory. A value or pointer to other data may be associated with every node in the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Node (computer Science)
A node is a basic unit of a data structure, such as a linked list or tree data structure. Nodes contain data and also may link to other nodes. Links between nodes are often implemented by pointers. Nodes and Trees Nodes are often arranged into tree structures. A node represents the information contained in a single data structure. These nodes may contain a value or condition, or possibly serve as another independent data structure. Nodes are represented by a single parent node. The highest point on a tree structure is called a root node, which does not have a parent node, but serves as the parent or 'grandparent' of all of the nodes below it in the tree. The height of a node is determined by the total number of edges on the path from that node to the furthest leaf node, and the height of the tree is equal to the height of the root node. Node depth is determined by the distance between that particular node and the root node. The root node is said to have a depth of zero. Data ca ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
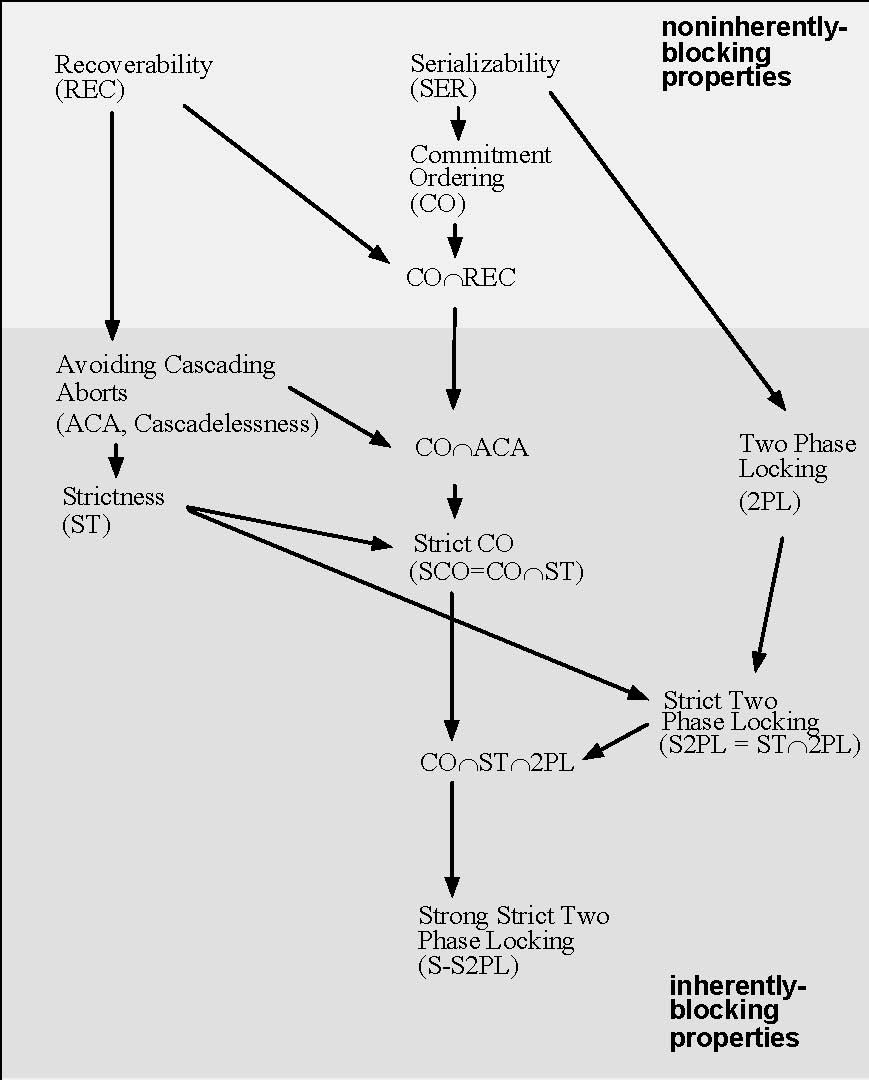
Two-phase Locking
In databases and transaction processing, two-phase locking (2PL) is a concurrency control method that guarantees serializability.Philip A. Bernstein, Vassos Hadzilacos, Nathan Goodman (1987) ''Concurrency Control and Recovery in Database Systems'' Addison Wesley Publishing Company, Gerhard Weikum, Gottfried Vossen (2001) ''Transactional Information Systems'' Elsevier, It is also the name of the resulting set of database transaction schedules (histories). The protocol uses locks, applied by a transaction to data, which may block (interpreted as signals to stop) other transactions from accessing the same data during the transaction's life. By the 2PL protocol, locks are applied and removed in two phases: # Expanding phase: locks are acquired and no locks are released. # Shrinking phase: locks are released and no locks are acquired. Two types of locks are used by the basic protocol: ''Shared'' and ''Exclusive'' locks. Refinements of the basic protocol may use more lock types. Using ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Serializability
In concurrency control of databases,Philip A. Bernstein, Vassos Hadzilacos, Nathan Goodman (1987)''Concurrency Control and Recovery in Database Systems''(free PDF download), Addison Wesley Publishing Company, Gerhard Weikum, Gottfried Vossen (2001)''Transactional Information Systems'' Elsevier, transaction processing (transaction management), and various transactional applications (e.g., transactional memoryMaurice Herlihy and J. Eliot B. Moss. ''Transactional memory: architectural support for lock-free data structures.'' Proceedings of the 20th annual international symposium on Computer architecture (ISCA '93). Volume 21, Issue 2, May 1993. and software transactional memory), both centralized and distributed, a transaction schedule is serializable if its outcome (e.g., the resulting database state) is equal to the outcome of its transactions executed serially, i.e. without overlapping in time. Transactions are normally executed concurrently (they overlap), since this is the mo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Database Transaction
A database transaction symbolizes a unit of work, performed within a database management system (or similar system) against a database, that is treated in a coherent and reliable way independent of other transactions. A transaction generally represents any change in a database. Transactions in a database environment have two main purposes: # To provide reliable units of work that allow correct recovery from failures and keep a database consistent even in cases of system failure. For example: when execution prematurely and unexpectedly stops (completely or partially) in which case many operations upon a database remain uncompleted, with unclear status. # To provide isolation between programs accessing a database concurrently. If this isolation is not provided, the programs' outcomes are possibly erroneous. In a database management system, a transaction is a single unit of logic or work, sometimes made up of multiple operations. Any logical calculation done in a consistent mode in ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Atomicity (programming)
{{Disambiguation ...
Atomicity may refer to: Chemistry * Atomicity (chemistry), the total number of atoms present in 1 molecule of a substance * Valence (chemistry), sometimes referred to as atomicity Computing * Atomicity (database systems), a property of database transactions which are guaranteed to either completely occur, or have no effects * Atomicity (programming), an operation appears to occur at a single instant between its invocation and its response * Atomicity, a property of an S-expression, in a symbolic language like Lisp Mathematics * Atomicity, an element of orthogonality in a component-based system * Atomicity, in order theory; see Atom (order theory) See also * Atom (other) An atom is a basic unit of matter consisting of a nucleus within a cloud of one or more electrons. Atom(s) may also refer to: Mathematics * Atom (time), a medieval unit of time * Atom (measure theory), a minimal measurable set * Atom (order theo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Concurrency Control
In information technology and computer science, especially in the fields of computer programming, operating systems, multiprocessors, and databases, concurrency control ensures that correct results for concurrent operations are generated, while getting those results as quickly as possible. Computer systems, both software and hardware, consist of modules, or components. Each component is designed to operate correctly, i.e., to obey or to meet certain consistency rules. When components that operate concurrently interact by messaging or by sharing accessed data (in memory or storage), a certain component's consistency may be violated by another component. The general area of concurrency control provides rules, methods, design methodologies, and theories to maintain the consistency of components operating concurrently while interacting, and thus the consistency and correctness of the whole system. Introducing concurrency control into a system means applying operation constraints wh ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Lock (computer Science)
In computer science, a lock or mutex (from mutual exclusion) is a synchronization primitive: a mechanism that enforces limits on access to a resource when there are many threads of execution. A lock is designed to enforce a mutual exclusion concurrency control policy, and with a variety of possible methods there exists multiple unique implementations for different applications. Types Generally, locks are ''advisory locks'', where each thread cooperates by acquiring the lock before accessing the corresponding data. Some systems also implement ''mandatory locks'', where attempting unauthorized access to a locked resource will force an exception in the entity attempting to make the access. The simplest type of lock is a binary semaphore. It provides exclusive access to the locked data. Other schemes also provide shared access for reading data. Other widely implemented access modes are exclusive, intend-to-exclude and intend-to-upgrade. Another way to classify locks is by what hap ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |