|
Mdadm
mdadm is a Linux utility used to manage and monitor software RAID devices. It is used in modern Linux distributions in place of older software RAID utilities such as raidtools2 or raidtools. mdadm is free software originally maintained by, and copyrighted to, Neil Brown of SUSE, and licensed under the terms of version 2 or later of the GNU General Public License. Name The name is derived from the ''md'' (multiple device) device nodes it ''administers'' or manages, and it replaced a previous utility ''mdctl''. The original name was "Mirror Disk", but was changed as more functions were added. The name is now understood to be short for Multiple Disk and Device Management. Overview Linux software RAID configurations can include anything presented to the Linux kernel as a block device. This includes whole hard drives (for example, ), and their partitions (for example, ). RAID configurations * ''RAID 0'' – Block-level striping. MD can handle devices of d ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Trim (computing)
A trim command (known as TRIM in the ATA command set, and UNMAP in the SCSI command set) allows an operating system to inform a solid-state drive (SSD) which blocks of data are no longer considered to be 'in use' and therefore can be erased internally. Trim was introduced soon after SSDs were introduced. Because low-level operation of SSDs differs significantly from hard drives, the typical way in which operating systems handle operations like deletes and formats resulted in unanticipated progressive performance degradation of write operations on SSDs. Trimming enables the SSD to more efficiently handle garbage collection, which would otherwise slow future write operations to the involved blocks.Shimpi, Anand Lal. (18 March 2009). p. 10. TRIM is an ATA command (Advanced Technology Attachment Command) that allows an OS to inform SSD about the blocks of data no longer in use. The SSD then deletes such blocks of data to make a way for newer blocks of data. TRIM is basically used ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
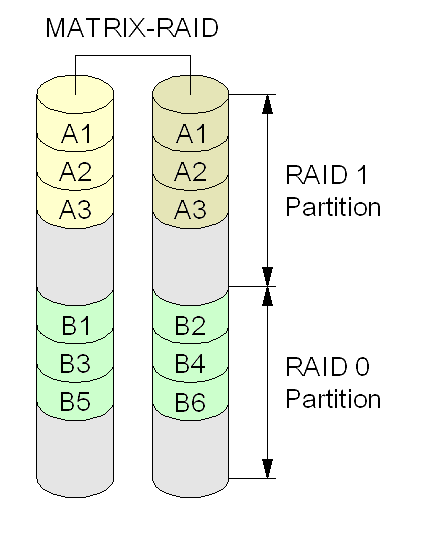
Intel Rapid Storage Technology
Intel Rapid Storage Technology (RST) is a driver SATA AHCI and a firmware-based RAID solution built into a wide range of Intel chipsets. Currently also is installed as a driver for Intel Optane temporary storage units. It contains two operation modes that do not follow the SATA standard, it follows two Intel specific modes. The name modes and the application that contains them have been renamed since the first version. Until 2010 it contains AHCI and Matrix RAID modes. The first mode is the Intel driver SATA normal and the latter mode is a fake RAID. Up to version 4 it is included on Intel Application Accelerator RAID Edition, between versions 5 and 8.9 it is included on Intel Matrix Storage Manager (IMSM), since version 9 it is included on Intel Rapid Storage Technology (IRST) preferring the driver modes to be named RST AHCI and RST AHCI RAID instead of Matrix RAID. The latter is also known as RST RAID mode, since it is the mode that Intel recommends to use, even if you are ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data Striping
In computer data storage, data striping is the technique of segmenting logically sequential data, such as a file, so that consecutive segments are stored on different physical storage devices. Striping is useful when a processing device requests data more quickly than a single storage device can provide it. By spreading segments across multiple devices which can be accessed concurrently, total data throughput is increased. It is also a useful method for balancing I/O load across an array of disks. Striping is used across disk drives in redundant array of independent disks (RAID) storage, network interface controllers, disk arrays, different computers in clustered file systems and grid-oriented storage, and RAM in some systems. Method One method of striping is done by interleaving sequential segments on storage devices in a round-robin fashion from the beginning of the data sequence. This works well for streaming data, but subsequent random accesses will require knowledge ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Disk Data Format
The SNIA Common RAID Disk Data Format (DDF) defines a standard data structure describing how data is formatted across disks in a RAID group. The DDF structure allows a basic level of interoperability between different suppliers of RAID technology. The Common RAID Raid, RAID or Raids may refer to: Attack * Raid (military), a sudden attack behind the enemy's lines without the intention of holding ground * Corporate raid, a type of hostile takeover in business * Panty raid, a prankish raid by male colleg ... DDF structure benefits storage users by enabling in-place data migration or recovery after controller failure using systems from different vendors. DDF is an external metadata format that is compatible with the mdraid subsystem in the Linux kernel. The mdadm command-line utility is a part of the mdraid subsystem. References External links Common RAID Disk Data Format (DDF) Specification v2.0Using DDF volumes with Linux Kernel RAID {{Compu-storage-stub ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Initramfs
In Linux systems, initrd (''initial ramdisk'') is a scheme for loading a temporary root file system into memory, to be used as part of the Linux startup process. initrd and initramfs refer to two different methods of achieving this. Both are commonly used to make preparations before the real root file system can be mounted. Rationale Many Linux distributions ship a single, generic Linux kernel image one that the distribution's developers create specifically to boot on a wide variety of hardware. The device drivers for this generic kernel image are included as loadable kernel modules because statically compiling many drivers into one kernel causes the kernel image to be much larger, perhaps too large to boot on computers with limited memory, or in some cases to cause boot-time crashes or other problems due to probing for nonexistent or conflicting hardware. This static-compiled kernel approach also leaves modules in kernel memory which are no longer used or needed, and raises the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
C (programming Language)
C (''pronounced like the letter c'') is a General-purpose language, general-purpose computer programming language. It was created in the 1970s by Dennis Ritchie, and remains very widely used and influential. By design, C's features cleanly reflect the capabilities of the targeted CPUs. It has found lasting use in operating systems, device drivers, protocol stacks, though decreasingly for application software. C is commonly used on computer architectures that range from the largest supercomputers to the smallest microcontrollers and embedded systems. A successor to the programming language B (programming language), B, C was originally developed at Bell Labs by Ritchie between 1972 and 1973 to construct utilities running on Unix. It was applied to re-implementing the kernel of the Unix operating system. During the 1980s, C gradually gained popularity. It has become one of the measuring programming language popularity, most widely used programming languages, with C compilers avail ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Degraded Mode
When a RAID array experiences the failure of one or more disks, it can enter degraded mode, a fallback mode that generally allows the continued usage of the array, but either loses the performance boosts of the RAID technique (such as a RAID-1 mirror across two disks when one of them fails; performance will fall back to that of a normal, single drive) or experiences severe performance penalties due to the necessity to reconstruct the damaged data from error correction data. Depending on the severity of the problem, the array may be placed into a ''read-only'' mode, either automatically or by the system administrator A system administrator, or sysadmin, or admin is a person who is responsible for the upkeep, configuration, and reliable operation of computer systems, especially multi-user computers, such as servers. The system administrator seeks to en ..., until it can be corrected. Such corrections may or may not be possible to do ''on-line'' (as opposed to an "off-line ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Daemon (computer Software)
In multitasking computer operating systems, a daemon ( or ) is a computer program that runs as a background process, rather than being under the direct control of an interactive user. Traditionally, the process names of a daemon end with the letter ''d'', for clarification that the process is in fact a daemon, and for differentiation between a daemon and a normal computer program. For example, is a daemon that implements system logging facility, and is a daemon that serves incoming SSH connections. In a Unix environment, the parent process of a daemon is often, but not always, the init process. A daemon is usually created either by a process forking a child process and then immediately exiting, thus causing init to adopt the child process, or by the init process directly launching the daemon. In addition, a daemon launched by forking and exiting typically must perform other operations, such as dissociating the process from any controlling terminal (tty). Such procedures ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Storage Networking Industry Association
The Storage Networking Industry Association (SNIA) is a registered 501(c)(6) non-profit trade association incorporated in December 1997. SNIA has more than 185 unique members, 2,000 active contributing members and over 50,000 IT end users and storage professionals. The SNIA absorbed the Small Form Factor Committee. SNIA's membership community participates in the following storage-related technical working groups: * Certification * Cloud Storage Technologies * Computational Storage * Data Management * Data Security * Dictionary * Networked Storage * Next Generation Data Center * Persistent Memory * Physical Storage * Power Efficiency Measurement * Storage Management Initiative – Specification (SMI-S) * Storage Management Swordfish Protocol SNIA and its technical council maintain a vendor-neutral dictionary and glossary of storage networking, data, and information management terminology. The SNIA dictionary won an award for publication excellence in 2009 and 2012 from the B ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Fake RAID
Raid, RAID or Raids may refer to: Attack * Raid (military), a sudden attack behind the enemy's lines without the intention of holding ground * Corporate raid, a type of hostile takeover in business * Panty raid, a prankish raid by male college students on the living quarters of female students to steal panties as trophies * Police raid, a police action involving the entering of a house with the intent to capture personnel or evidence, often taking place early in the morning * Union raid, when an outsider trade union takes over the membership of an existing union Arts, entertainment, and media Films * ''Raid'' (1947 film), an East German film * ''Raid'' (2003 film), a 2003 Finnish film * ''Raid'' (2018 film), an Indian period crime thriller Gaming * Raid (gaming), a type of mission in a video game where a large number of people combine forces to defeat a powerful enemy * ''Raid'' (video game), a Nintendo Entertainment System title released by Sachen in 1989 * '' Raid over Mos ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
/boot
In Linux, and other Unix-like operating systems, the directory holds files used in booting the operating system. The usage is standardized in the Filesystem Hierarchy Standard. Contents The contents are mostly Linux kernel files or boot loader files, depending on the boot loader, most commonly (on Linux) LILO or GRUB. Linux * vmlinux – the Linux kernel * initrd.img – a temporary file system, used prior to loading the kernel * System.map – a symbol lookup table LILO LILO creates and uses the following files: * map – a key file, which records where files needed by LILO during boot are stored. Following kernel upgrades, this file must be regenerated by running the "map installer", which is otherwise the system will not boot. * boot.''xxyy'' – these 512-byte files are backups of boot sectors, either the master boot record (MBR) or volume boot record (VBR), created when LILO overwrites a boot sector. ''xx'' and ''yy'' are the major and minor device numbers in hex; for ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
GNU GRUB
GNU GRUB (short for GNU GRand Unified Bootloader, commonly referred to as GRUB) is a boot loader package from the GNU Project. GRUB is the reference implementation of the Free Software Foundation's Multiboot Specification, which provides a user the choice to boot one of multiple operating systems installed on a computer or select a specific kernel configuration available on a particular operating system's partitions. GNU GRUB was developed from a package called the ''Grand Unified Bootloader'' (a play on Grand Unified Theory). It is predominantly used for Unix-like systems. The GNU operating system uses GNU GRUB as its boot loader, as do most Linux distributions and the Solaris operating system on x86 systems, starting with the Solaris 10 1/06 release. Operation Booting When a computer is turned on, its BIOS finds the primary bootable device (usually the computer's hard disk) and runs the initial bootstrap program from the master boot record (MBR). The MBR is the firs ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |