|
JTAG Header
JTAG (named after the Joint Test Action Group which codified it) is an industry standard for verifying designs of and testing printed circuit boards after manufacture. JTAG implements standards for on-chip instrumentation in electronic design automation (EDA) as a complementary tool to digital simulation. It specifies the use of a dedicated debug port implementing a serial communications interface for low-overhead access without requiring direct external access to the system address and data buses. The interface connects to an on-chip Test Access Port (TAP) that implements a stateful protocol to access a set of test registers that present chip logic levels and device capabilities of various parts. The Joint Test Action Group formed in 1985 to develop a method of verifying designs and testing printed circuit boards after manufacture. In 1990 the Institute of Electrical and Electronics Engineers codified the results of the effort in IEEE Standard 1149.1-1990, entitled ''Standard ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Technical Standard
A technical standard is an established Social norm, norm or requirement for a repeatable technical task which is applied to a common and repeated use of rules, conditions, guidelines or characteristics for products or related processes and production methods, and related management systems practices. A technical standard includes definition of terms; classification of components; delineation of procedures; specification of dimensions, materials, performance, designs, or operations; measurement of quality and quantity in describing materials, processes, products, systems, services, or practices; test methods and sampling procedures; or descriptions of fit and measurements of size or strength. It is usually a formal document that establishes uniform engineering or technical criteria, methods, processes, and practices. In contrast, a custom, convention, company product, corporate standard, and so forth that becomes generally accepted and dominant is often called a ''de facto'' standar ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Boundary Scan
Boundary scan is a method for testing interconnects (wire lines) on printed circuit boards or sub-blocks inside an integrated circuit (IC). Boundary scan is also widely used as a debugging method to watch integrated circuit pin states, measure voltage, or analyze sub-blocks inside an integrated circuit. The Joint Test Action Group (JTAG) developed a specification for boundary scan testing that was standardized in 1990 as the IEEE Std. 1149.1-1990. In 1994, a supplement that contains a description of the boundary scan description language (BSDL) was added which describes the boundary-scan logic content of IEEE Std 1149.1 compliant devices. Since then, this standard has been adopted by electronic device companies all over the world. Boundary scan is now mostly synonymous with JTAG.IEEE Std 1149.1 (JTAG) Testability ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Programmer (hardware)
In the context of Installation (computer programs), installing firmware onto a device, a programmer, device programmer, chip programmer, Programmable read-only memory#Programming, device burner, or PROM writer is a device that writes, a.k.a. burns, firmware to a target device's non-volatile memory. Typically, the target device memory is one of the following types: Programmable read-only memory, PROM, EPROM, EEPROM, Flash memory, MultiMediaCard#eMMC, eMMC, Magnetoresistive random-access memory, MRAM, Ferroelectric RAM, FeRAM, Non-volatile random-access memory, NVRAM, Programmable logic device, PLD, Programmable logic array, PLA, Programmable Array Logic, PAL, Generic array logic, GAL, Complex programmable logic device, CPLD, Field Programmable Gate Array, FPGA. Connection Generally, a programmer connects to a device in one of two ways. Insertion In some cases, the target device is inserted into a socket (usually Zero insertion force, ZIF) on the programmer. If the de ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
FPGA
A field-programmable gate array (FPGA) is a type of configurable integrated circuit that can be repeatedly programmed after manufacturing. FPGAs are a subset of logic devices referred to as programmable logic devices (PLDs). They consist of an array of programmable logic device, programmable logic block, logic blocks with a connecting grid, that can be configured "in the field" to interconnect with other logic blocks to perform various digital functions. FPGAs are often used in limited (low) quantity production of custom-made products, and in research and development, where the higher cost of individual FPGAs is not as important, and where creating and manufacturing a custom circuit would not be feasible. Other applications for FPGAs include the telecommunications, automotive, aerospace, and industrial sectors, which benefit from their flexibility, high signal processing speed, and parallel processing abilities. A FPGA configuration is generally written using a hardware descr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
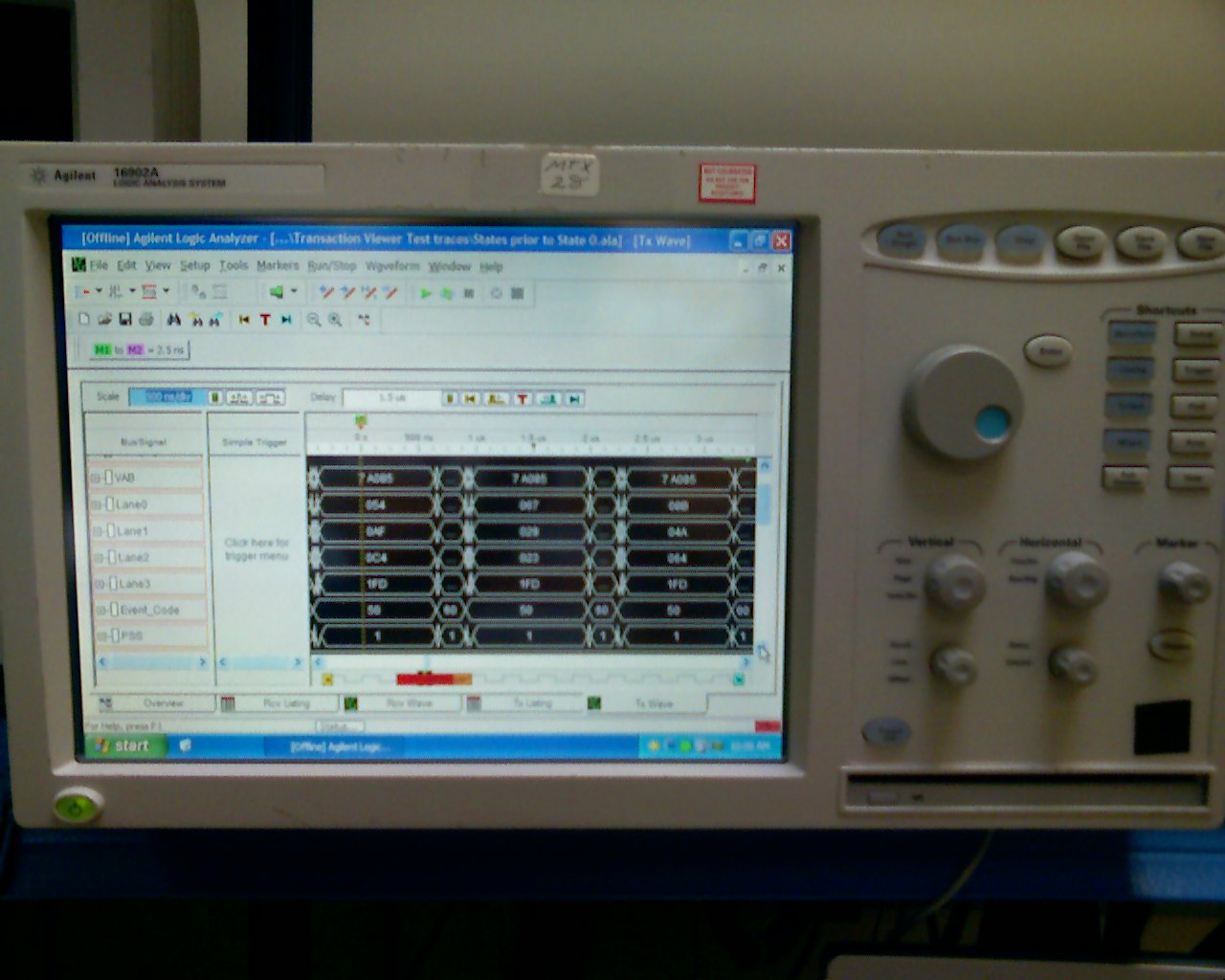
Logic Analyzer
A logic analyzer is an electronic instrument that captures and displays multiple logic signals from a digital system or digital circuit. A logic analyzer may convert the capture into timing diagrams, protocol decodes, state machine traces, opcodes, or may correlate opcodes with source-level software. Logic analyzers have advanced triggering capabilities, and are useful when a user needs to see the timing relationships between many signals in a digital system. Overview Presently, there are three distinct categories of logic analyzers available on the market: * Modular LAs, which consist of both a chassis or mainframe and logic analyzer modules. The mainframe/chassis contains the display, controls, control computer, and multiple slots into which the actual data-capturing hardware is installed. The modules each have a specific number of channels, and multiple modules may be combined to obtain a very high channel count. While modular logic analyzers are typically more expensive, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
INT3
INT is an assembly language instruction for x86 processors that generates a software interrupt. It takes the interrupt number formatted as a byte value. When written in assembly language, the instruction is written like this: :INT ''X'' where ''X'' is the ''software interrupt'' that should be generated (0-255). As is customary with machine binary arithmetic, interrupt numbers are often written in hexadecimal form, which can be indicated with a prefix ''0x'' or with the suffix ''h''. For example, INT 13H will generate the 20th ''software interrupt'' (0x13 is nineteen (19) in hexadecimal notation, and the count starts at 0), causing the function pointed to by the 20th vector in the interrupt table to be executed. INT is widely used in real mode. In protected mode, INT is a privileged instruction. Real mode When generating a ''software interrupt'', the processor calls one of the 256 functions pointed to by the interrupt address table, which is located in the first 1024 byt ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Non-disclosure Agreement
A non-disclosure agreement (NDA), also known as a confidentiality agreement (CA), confidential disclosure agreement (CDA), proprietary information agreement (PIA), or secrecy agreement (SA), is a legal contract or part of a contract between at least two parties that outlines confidential material, knowledge, or information that the parties wish to share with one another for certain purposes, but wish to restrict access to. Doctor–patient confidentiality (physician–patient privilege), attorney–client privilege, priest–penitent privilege and bank–client confidentiality agreements are examples of NDAs, which are often not enshrined in a written contract between the parties. It is a contract through which the parties agree not to disclose any information covered by the agreement. An NDA creates a confidential relationship between the parties, typically to protect any type of confidential and proprietary information or trade secrets. As such, an NDA protects non-public bu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Nexus (standard)
Nexus or IEEE-ISTO 5001-2003 is a standard debugging interface for embedded systems. Features The IEEE-ISTO 5001-2003 (Nexus) feature set is modeled on today's on-chip debug implementations, most of which are processor-specific. Its goal is to create a rich debug feature set while minimizing the required pin-count and die area, and being both processor- and architecture independent. It also supports multi-core and multi-processor designs. Accordingly, it is comparable to the ARM CoreSight debug architecture. Physically, IEEE-ISTO 5001-2003 defines a standard set of connectors for connecting the debug tool to the target or system under test. Logically, data is transferred using a packet-based protocol. This protocol can be JTAG (IEEE 1149.1); or, for high-speed systems, an auxiliary port can be used that supports full duplex, higher bandwidth transfers. Key Nexus functionality involves either JTAG-style request/response interactions, or packets transferred through the debug ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
CoreSight
ARM (stylised in lowercase as arm, formerly an acronym for Advanced RISC Machines and originally Acorn RISC Machine) is a family of RISC In electronics and computer science, a reduced instruction set computer (RISC) is a computer architecture designed to simplify the individual instructions given to the computer to accomplish tasks. Compared to the instructions given to a comp ... instruction set architectures (ISAs) for central processing unit, computer processors. Arm Holdings develops the ISAs and licenses them to other companies, who build the physical devices that use the instruction set. It also designs and licenses semiconductor intellectual property core, cores that implement these ISAs. Due to their low costs, low power consumption, and low heat generation, ARM processors are useful for light, portable, battery-powered devices, including smartphones, laptops, and tablet computers, as well as embedded systems. However, ARM processors are also used for desktop ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Debug
In engineering, debugging is the process of finding the root cause, workarounds, and possible fixes for bugs. For software, debugging tactics can involve interactive debugging, control flow analysis, log file analysis, monitoring at the application or system level, memory dumps, and profiling. Many programming languages and software development tools also offer programs to aid in debugging, known as debuggers. Etymology The term ''bug'', in the sense of defect, dates back at least to 1878 when Thomas Edison wrote "little faults and difficulties" in his inventions as "Bugs". A popular story from the 1940s is from Admiral Grace Hopper. While she was working on a Mark II computer at Harvard University, her associates discovered a moth stuck in a relay that impeded operation and wrote in a log book "First actual case of a bug being found". Although probably a joke, conflating the two meanings of bug (biological and defect), the story indicates that the term was used in t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
In-circuit Emulator
In-circuit emulation (ICE) is the use of a hardware device or in-circuit emulator used to debug the software of an embedded system. It operates by using a processor with the additional ability to support debugging operations, as well as to carry out the main function of the system. Particularly for older systems, with limited processors, this usually involved replacing the processor temporarily with a hardware emulator: a more powerful although more expensive version. It was historically in the form of bond-out processor which has many internal signals brought out for the purpose of debugging. These signals provide information about the state of the processor. More recently the term also covers JTAG-based hardware debuggers which provide equivalent access using on-chip debugging hardware with standard production chips. Using standard chips instead of custom bond-out versions makes the technology ubiquitous and low cost, and eliminates most differences between the development a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Booting
In computing, booting is the process of starting a computer as initiated via Computer hardware, hardware such as a physical button on the computer or by a software command. After it is switched on, a computer's central processing unit (CPU) has no software in its main memory, so some process must load software into memory before it can be executed. This may be done by hardware or firmware in the CPU, or by a separate processor in the computer system. On some systems a power-on reset (POR) does not initiate booting and the operator must initiate booting after POR completes. IBM uses the term Initial Program Load (IPL) on someE.g., System/360 through IBM Z, RS/6000 and System/38 through IBM Power Systems product lines. Restarting a computer also is called Reboot (computing), ''rebooting'', which can be "hard", e.g. after electrical power to the CPU is switched from off to on, or "soft", where the power is not cut. On some systems, a soft boot may optionally clear RAM to zero. Bo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |