|
Hacker (video Game)
''Hacker'' is a 1985 video game by Activision. It was designed by Steve Cartwright and released for the Amiga, Amstrad CPC, Apple II, Atari 8-bit family, Atari ST, Commodore 64, Macintosh, DOS, MSX2, and ZX Spectrum. Plot Activision executive Jim Levy introduced ''Hacker'' to reporters by pretending that something had gone wrong during his attempt to connect on line to company headquarters to demonstrate a new game. After several attempts he logged into a mysterious non-Activision computer, before explaining, "That, ladies and gentlemen, is the game". The player assumes the role of a hacker, a person experienced in breaking into secure computer systems, who accidentally acquires access to a non-public system. The game was shipped with no information on how to play, thus building the concept that the player did hack into a system. BPL2020 The player must attempt to hack into the Magma Ltd. computer system at the beginning of the game by guessing the logon password. The pa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
ZX Spectrum
The ZX Spectrum () is an 8-bit computing, 8-bit home computer that was developed by Sinclair Research. It was released in the United Kingdom on 23 April 1982, and became Britain's best-selling microcomputer. Referred to during development as the ''ZX81 Colour'' and ''ZX82'', it was launched as the ''ZX Spectrum'' to highlight the machine's colour display, which differed from the black and white display of its predecessor, the ZX81. The Spectrum was released as six different models, ranging from the entry level with 16 Kilobyte, KB RAM released in 1982 to the ZX Spectrum +3 with 128 KB RAM and built in floppy disk drive in 1987; altogether they sold over 5 million units worldwide (not counting List of ZX Spectrum clones, unofficial clones). The Spectrum was among the first home computers in the United Kingdom aimed at a mainstream audience, and it thus had similar significance to the Commodore 64 in the US and the Thomson MO5 in France. The introduction of the ZX Spect ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Video Game
Video games, also known as computer games, are electronic games that involves interaction with a user interface or input device such as a joystick, controller, keyboard, or motion sensing device to generate visual feedback. This feedback mostly commonly is shown on a video display device, such as a TV set, monitor, touchscreen, or virtual reality headset. Some computer games do not always depend on a graphics display, for example text adventure games and computer chess can be played through teletype printers. Video games are often augmented with audio feedback delivered through speakers or headphones, and sometimes with other types of feedback, including haptic technology. Video games are defined based on their platform, which include arcade video games, console games, and personal computer (PC) games. More recently, the industry has expanded onto mobile gaming through smartphones and tablet computers, virtual and augmented reality systems, and remote c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Satellite
A satellite or artificial satellite is an object intentionally placed into orbit in outer space. Except for passive satellites, most satellites have an electricity generation system for equipment on board, such as solar panels or radioisotope thermoelectric generators (RTGs). Most satellites also have a method of communication to ground stations, called Transponder (satellite communications), transponders. Many satellites use a Satellite bus, standardized bus to save cost and work, the most popular of which is small CubeSats. Similar satellites can work together as a group, forming Satellite constellation, constellations. Because of the high launch cost to space, satellites are designed to be as lightweight and robust as possible. Most communication satellites are radio Broadcast relay station, relay stations in orbit and carry dozens of transponders, each with a bandwidth of tens of megahertz. Satellites are placed from the surface to orbit by launch vehicles, high enough to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Federal Government Of The United States
The federal government of the United States (U.S. federal government or U.S. government) is the national government of the United States, a federal republic located primarily in North America, composed of 50 states, a city within a federal district (the city of Washington in the District of Columbia, where most of the federal government is based), five major self-governing territories and several island possessions. The federal government, sometimes simply referred to as Washington, is composed of three distinct branches: legislative, executive, and judicial, whose powers are vested by the U.S. Constitution in the Congress, the president and the federal courts, respectively. The powers and duties of these branches are further defined by acts of Congress, including the creation of executive departments and courts inferior to the Supreme Court. Naming The full name of the republic is "United States of America". No other name appears in the Constitution, and this i ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Espionage
Espionage, spying, or intelligence gathering is the act of obtaining secret or confidential information (intelligence) from non-disclosed sources or divulging of the same without the permission of the holder of the information for a tangible benefit. A person who commits espionage is called an ''espionage agent'' or ''spy''. Any individual or spy ring (a cooperating group of spies), in the service of a government, company, criminal organization, or independent operation, can commit espionage. The practice is clandestine, as it is by definition unwelcome. In some circumstances, it may be a legal tool of law enforcement and in others, it may be illegal and punishable by law. Espionage is often part of an institutional effort by a government or commercial concern. However, the term tends to be associated with state spying on potential or actual enemies for military purposes. Spying involving corporations is known as industrial espionage. One of the most effective ways to gath ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Magma
Magma () is the molten or semi-molten natural material from which all igneous rocks are formed. Magma is found beneath the surface of the Earth, and evidence of magmatism has also been discovered on other terrestrial planets and some natural satellites. Besides molten rock, magma may also contain suspended crystals and gas bubbles. Magma is produced by melting of the mantle or the crust in various tectonic settings, which on Earth include subduction zones, continental rift zones, mid-ocean ridges and hotspots. Mantle and crustal melts migrate upwards through the crust where they are thought to be stored in magma chambers or trans-crustal crystal-rich mush zones. During magma's storage in the crust, its composition may be modified by fractional crystallization, contamination with crustal melts, magma mixing, and degassing. Following its ascent through the crust, magma may feed a volcano and be extruded as lava, or it may solidify underground to form an intrusion, such as a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Tunnel
A tunnel is an underground passageway, dug through surrounding soil, earth or rock, and enclosed except for the entrance and exit, commonly at each end. A pipeline is not a tunnel, though some recent tunnels have used immersed tube construction techniques rather than traditional tunnel boring methods. A tunnel may be for foot or vehicular road traffic, for rail traffic, or for a canal. The central portions of a rapid transit network are usually in the tunnel. Some tunnels are used as sewers or aqueducts to supply water for consumption or for hydroelectric stations. Utility tunnels are used for routing steam, chilled water, electrical power or telecommunication cables, as well as connecting buildings for convenient passage of people and equipment. Secret tunnels are built for military purposes, or by civilians for smuggling of weapons, contraband, or people. Special tunnels, such as wildlife crossings, are built to allow wildlife to cross human-made barriers safely. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
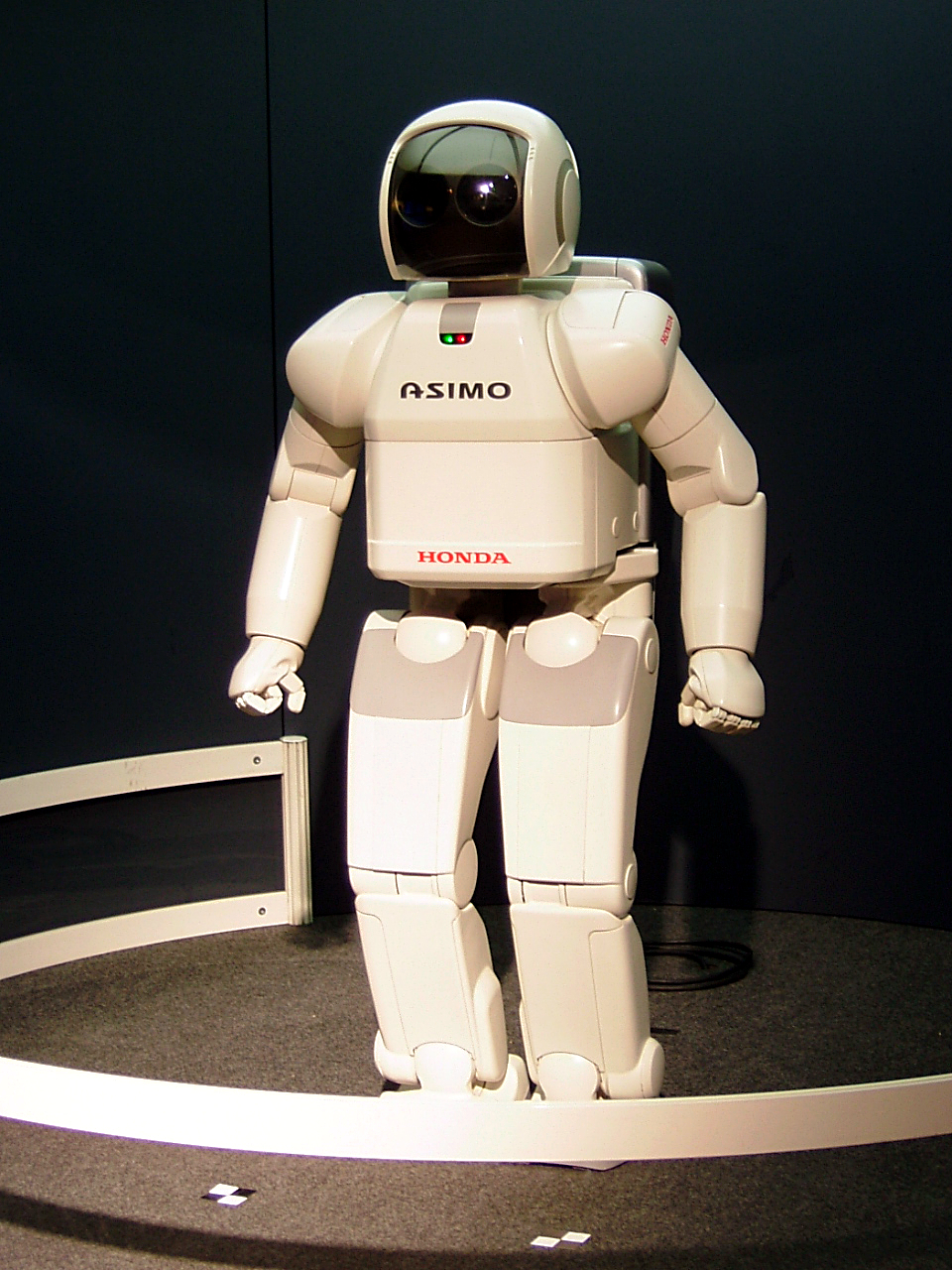
Robot
A robot is a machine—especially one programmable by a computer—capable of carrying out a complex series of actions automatically. A robot can be guided by an external control device, or the control may be embedded within. Robots may be constructed to evoke human form, but most robots are task-performing machines, designed with an emphasis on stark functionality, rather than expressive aesthetics. Robots can be autonomous or semi-autonomous and range from humanoids such as Honda's ''Advanced Step in Innovative Mobility'' ( ASIMO) and TOSY's ''TOSY Ping Pong Playing Robot'' (TOPIO) to industrial robots, medical operating robots, patient assist robots, dog therapy robots, collectively programmed ''swarm'' robots, UAV drones such as General Atomics MQ-1 Predator, and even microscopic nano robots. By mimicking a lifelike appearance or automating movements, a robot may convey a sense of intelligence or thought of its own. Autonomous things are expected to proliferate in ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Password
A password, sometimes called a passcode (for example in Apple devices), is secret data, typically a string of characters, usually used to confirm a user's identity. Traditionally, passwords were expected to be memorized, but the large number of password-protected services that a typical individual accesses can make memorization of unique passwords for each service impractical. Using the terminology of the NIST Digital Identity Guidelines, the secret is held by a party called the ''claimant'' while the party verifying the identity of the claimant is called the ''verifier''. When the claimant successfully demonstrates knowledge of the password to the verifier through an established authentication protocol, the verifier is able to infer the claimant's identity. In general, a password is an arbitrary string of characters including letters, digits, or other symbols. If the permissible characters are constrained to be numeric, the corresponding secret is sometimes called a personal i ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |