|
HAMMER2
HAMMER2 is a successor to the HAMMER filesystem, redesigned from the ground up to support enhanced clustering. HAMMER2 supports online and batched deduplication, snapshots, directory entry indexing, multiple mountable filesystem roots, mountable snapshots, a low memory footprint, compression, encryption, zero-detection, data and metadata checksumming, and synchronization to other filesystems or nodes. History The HAMMER2 file system was conceived by Matthew Dillon, who initially planned to bring it up to minimal working state by July 2012 and ship the final version in 2013. During Google Summer of Code 2013 Daniel Flores implemented compression in HAMMER2 using LZ4 and zlib algorithms. On June 4, 2014, DragonFly 3.8.0 was released featuring support for HAMMER2, although the file system was said to be not ready for use. On October 16, 2017, DragonFly 5.0 was released with bootable support for HAMMER2, though file-system status was marked as experimental. HAMMER2 had a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
DragonFly BSD
DragonFly BSD is a free and open-source Unix-like operating system forked from FreeBSD 4.8. Matthew Dillon, an Amiga developer in the late 1980s and early 1990s and FreeBSD developer between 1994 and 2003, began working on DragonFly BSD in June 2003 and announced it on the FreeBSD mailing lists on 16 July 2003. Dillon started DragonFly in the belief that the techniques adopted for threading and symmetric multiprocessing in FreeBSD 5 would lead to poor performance and maintenance problems. He sought to correct these anticipated problems within the FreeBSD project. Due to conflicts with other FreeBSD developers over the implementation of his ideas, his ability to directly change the codebase was eventually revoked. Despite this, the DragonFly BSD and FreeBSD projects still work together, sharing bug fixes, driver updates, and other improvements. Intended as the logical continuation of the FreeBSD 4.x series, DragonFly has diverged significantly from FreeBSD, implementing l ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
HAMMER (file System)
HAMMER is a high-availability 64-bit file system developed by Matthew Dillon for DragonFly BSD using B+ trees. Its major features include infinite NFS-exportable snapshots, master–multislave operation, configurable history retention, fsckless-mount, and checksums to deal with data corruption. HAMMER also supports data block deduplication, meaning that identical data blocks will be stored only once on a file system. A successor, HAMMER2, was announced in 2011 and became the default in Dragonfly 5.2 (April 2018). Features HAMMER file system provides configurable fine-grained and coarse-grained filesystem histories with online snapshots availability. Up to 65536 '' master'' (read–write) and ''slave'' (read-only) pseudo file systems (PFSs), with independent individual retention parameters and inode numbering, may be created for each file system; PFS may be mirrored to multiple slaves both locally or over network connection with near real-time performance. No file system che ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
List Of File Systems
The following lists identify, characterize, and link to more thorough information on Computer file systems. Many older operating systems support only their one "native" file system, which does not bear any name apart from the name of the operating system itself. Disk file systems Disk file systems are usually block-oriented. Files in a block-oriented file system are sequences of blocks, often featuring fully random-access read, write, and modify operations. * ADFS – Acorn's Advanced Disc filing system, successor to DFS. * AdvFS – Advanced File System, designed by Digital Equipment Corporation for their Digital UNIX (now Tru64 UNIX) operating system. * APFS – Apple File System is a next-generation file system for Apple products. * AthFS – AtheOS File System, a 64-bit journaled filesystem now used by Syllable. Also called AFS. * BFS – the Boot File System used on System V release 4.0 and UnixWare. * BFS – the Be File System used on BeOS, occasionally misnamed ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Comparison Of File Systems
The following tables compare general and technical information for a number of file systems. General information Limits Metadata Features File capabilities Block capabilities Note that in addition to the below table, block capabilities can be implemented below the file system layer in Linux ( LVM, integritysetup, cryptsetup) or Windows ( Volume Shadow Copy Service, SECURITY), etc. Resize capabilities "online" and "offline" are synonymous with "mounted" and "not mounted". Allocation and layout policies OS support See also * List of file systems * Comparison of file archivers * List of archive formats * Comparison of archive formats Notes References External links A speed comparison of filesystems on Linux 2.4.5(archived) Filesystems (ext3, reiser, xfs, jfs) comparison on Debian Etch{{Webarchive, url=https://web.archive.org/web/20180304191727/https://debian-administration.org/article/388/Filesystems_ext3_reiser_xfs_jfs_compari ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Matthew Dillon (computer Scientist)
Matthew Dillon (born 1966) is an American software engineer known for Amiga software, contributions to FreeBSD and for starting and leading the DragonFly BSD project since 2003. Biography Dillon studied electronic engineering and computer science at the University of California, Berkeley, where he first became involved with BSD in 1985. He also became known for his Amiga programming, his C compiler DICE and his work on the Linux kernel. He founded and worked at Best Internet from 1994 until 1997, contributing to FreeBSD in that time. His "Diablo" internet news transit program was very popular with many ISPs. In 1997, Dillon gained commit access to the FreeBSD code and heavily contributed to the virtual memory subsystem, amongst other contributions. Concerned with problems he saw in the direction FreeBSD 5.x was headed in regards to concurrency, and coupled with the fact that Dillon's access to the FreeBSD source code repository was revoked due to a falling-out with other Fre ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Distributed File Systems
A clustered file system is a file system which is shared by being simultaneously mounted on multiple servers. There are several approaches to clustering, most of which do not employ a clustered file system (only direct attached storage for each node). Clustered file systems can provide features like location-independent addressing and redundancy which improve reliability or reduce the complexity of the other parts of the cluster. Parallel file systems are a type of clustered file system that spread data across multiple storage nodes, usually for redundancy or performance. Shared-disk file system A shared-disk file system uses a storage area network (SAN) to allow multiple computers to gain direct disk access at the block level. Access control and translation from file-level operations that applications use to block-level operations used by the SAN must take place on the client node. The most common type of clustered file system, the shared-disk file system —by ad ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Root Directory
In a computer file system, and primarily used in the Unix and Unix-like operating systems, the root directory is the first or top-most directory in a hierarchy. It can be likened to the trunk of a tree, as the starting point where all branches originate from. The root file system is the file system contained on the same disk partition on which the root directory is located; it is the filesystem on top of which all other file systems are mounted as the system boots up. Unix-like systems Unix abstracts the nature of this tree hierarchy entirely and in Unix and Unix-like systems the root directory is denoted by the / (slash) sign. Though the root directory is conventionally referred to as /, the directory entry itself has no name its path is the "empty" part before the initial directory separator character (/). All file system entries, including mounted file systems are "branches" of this root. chroot In UNIX-like operating systems, each process has its own idea of what the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data Compression
In information theory, data compression, source coding, or bit-rate reduction is the process of encoding information using fewer bits than the original representation. Any particular compression is either lossy or lossless. Lossless compression reduces bits by identifying and eliminating statistical redundancy. No information is lost in lossless compression. Lossy compression reduces bits by removing unnecessary or less important information. Typically, a device that performs data compression is referred to as an encoder, and one that performs the reversal of the process (decompression) as a decoder. The process of reducing the size of a data file is often referred to as data compression. In the context of data transmission, it is called source coding; encoding done at the source of the data before it is stored or transmitted. Source coding should not be confused with channel coding, for error detection and correction or line coding, the means for mapping data onto a signa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Filesystem-level Encryption
Filesystem-level encryption, often called file-based encryption, FBE, or file/folder encryption, is a form of disk encryption where individual files or directories are encrypted by the file system itself. This is in contrast to the full disk encryption where the entire partition or disk, in which the file system resides, is encrypted. Types of filesystem-level encryption include: * the use of a 'stackable' cryptographic filesystem layered on top of the main file system * a single ''general-purpose'' file system with encryption The advantages of filesystem-level encryption include: * flexible file-based key management, so that each file can be and usually is encrypted with a separate encryption key * individual management of encrypted files e.g. incremental backups of the individual changed files even in encrypted form, rather than backup of the entire encrypted volume * access control can be enforced through the use of public-key cryptography, and * the fact that cryptographic ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Checksum
A checksum is a small-sized block of data derived from another block of digital data for the purpose of detecting errors that may have been introduced during its transmission or storage. By themselves, checksums are often used to verify data integrity but are not relied upon to verify data authenticity. The procedure which generates this checksum is called a checksum function or checksum algorithm. Depending on its design goals, a good checksum algorithm usually outputs a significantly different value, even for small changes made to the input. This is especially true of cryptographic hash functions, which may be used to detect many data corruption errors and verify overall data integrity; if the computed checksum for the current data input matches the stored value of a previously computed checksum, there is a very high probability the data has not been accidentally altered or corrupted. Checksum functions are related to hash functions, fingerprints, randomization func ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Synchronization (computer Science)
In computer science Computer science is the study of computation, automation, and information. Computer science spans theoretical disciplines (such as algorithms, theory of computation, information theory, and automation) to practical disciplines (includin ..., synchronization refers to one of two distinct but related concepts: synchronization of Process (computer science), processes, and synchronization of Dataset, data. ''Process synchronization'' refers to the idea that multiple processes are to join up or Handshake (computing), handshake at a certain point, in order to reach an agreement or commit to a certain sequence of action. ''Data synchronization'' refers to the idea of keeping multiple copies of a dataset in coherence with one another, or to maintain data integrity. Process synchronization primitives are commonly used to implement data synchronization. The need for synchronization The need for synchronization does not arise merely in multi-processor systems ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
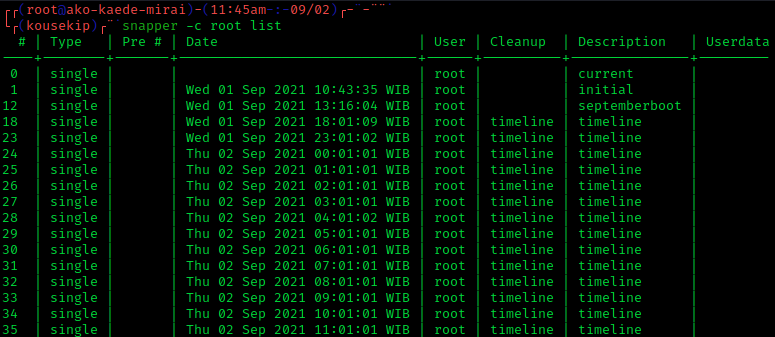
Snapshot (computer Storage)
In computer systems, a snapshot is the state of a system at a particular point in time. The term was coined as an analogy to that in photography. It can refer to an actual copy of the state of a system or to a capability provided by certain systems. Rationale A full backup of a large data set may take a long time to complete. On multi-tasking or multi-user systems, there may be writes to that data while it is being backed up. This prevents the backup from being atomic and introduces a version skew that may result in data corruption. For example, if a user moves a file into a directory that has already been backed up, then that file would be completely missing on the backup media, since the backup operation had already taken place before the addition of the file. Version skew may also cause corruption with files which change their size or contents underfoot while being read. One approach to safely backing up live data is to temporarily disable write access to data during th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |