|
GOST (block Cipher)
The GOST block cipher (Magma), defined in the standard GOST 28147-89 (RFC 5830), is a Soviet and Russian government standard symmetric key block cipher with a block size of 64 bits. The original standard, published in 1989, did not give the cipher any name, but the most recent revision of the standard, GOST R 34.12-2015 (RFC 7801, RFC 8891), specifies that it may be referred to as Magma. The GOST hash function is based on this cipher. The new standard also specifies a new 128-bit block cipher called Kuznyechik. Developed in the 1970s, the standard had been marked "Top Secret" and then downgraded to "Secret" in 1990. Shortly after the dissolution of the USSR, it was declassified and it was released to the public in 1994. GOST 28147 was a Soviet alternative to the United States standard algorithm, DES. Thus, the two are very similar in structure. The algorithm GOST has a 64-bit block size and a key length of 256 bits. Its S-boxes can be secret, and they contain about 354 (lo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Key Length
In cryptography, key size or key length refers to the number of bits in a key used by a cryptographic algorithm (such as a cipher). Key length defines the upper-bound on an algorithm's security (i.e. a logarithmic measure of the fastest known attack against an algorithm), because the security of all algorithms can be violated by brute-force attacks. Ideally, the lower-bound on an algorithm's security is by design equal to the key length (that is, the algorithm's design does not detract from the degree of security inherent in the key length). Most symmetric-key algorithms are designed to have security equal to their key length. However, after design, a new attack might be discovered. For instance, Triple DES was designed to have a 168-bit key, but an attack of complexity 2112 is now known (i.e. Triple DES now only has 112 bits of security, and of the 168 bits in the key the attack has rendered 56 'ineffective' towards security). Nevertheless, as long as the security (understood as ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Broken Block Ciphers
Broken may refer to: Literature * ''Broken'' (Armstrong novel), a 2006 novel by Kelley Armstrong in the ''Women of the Otherworld'' series * ''Broken'' (Slaughter novel), a 2010 novel by Karin Slaughter Music Albums * '' Broken (And Other Rogue States)'', a 2005 album by Luke Doucet * ''Broken'' (MBLAQ EP) (2014) * ''Broken'' (Nine Inch Nails EP), (1992) * ''Broken'' (Soulsavers album) (2009) * ''Broken'' (Straight Faced album) (1996) Songs * "Broken" (Jake Bugg song) (2013) * "Broken" (Sam Clark song) (2009) * "Broken" (Coldplay song) (2019) * "Broken" (Elisa song) (2003) * "Broken" (Lifehouse song) (2008) * "Broken" (lovelytheband song) (2017) * "Broken" (Kate Ryan song) (2011) * "Broken" (Seether song) (2004) * "Broken" (Slander and Kompany song) (2019) * "Broken", by 12 Stones from '' 12 Stones'' * "Broken", by All That Remains from ''Victim of the New Disease'' * "Broken", by David Archuleta from '' Begin'' * "Broken", by Bad Religion from '' The Pr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Bruges
Bruges ( , ; ; ) is the capital and largest city of the province of West Flanders, in the Flemish Region of Belgium. It is in the northwest of the country, and is the sixth most populous city in the country. The area of the whole city amounts to more than 14,099 hectares (140.99 km2; 54.44 sq. miles), including 1,075 hectares off the coast, at Zeebrugge (from , meaning 'Bruges by the Sea'). The historic city center is a prominent World Heritage Site of UNESCO. It is oval and about 430 hectares in size. The city's total population is 117,073 (1 January 2008),Statistics Belgium; ''Population de droit par commune au 1 janvier 2008'' (excel-file) Population of all municipalities in Belgium, as of 1 January 2008. Retrieved on 19 October 2008. of who ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
EUROCRYPT
EuroCrypt is a conditional access system for Multiplexed Analogue Components-encoded analogue satellite television Satellite television is a service that delivers television programming to viewers by relaying it from a communications satellite orbiting the Earth directly to the viewer's location.ITU Radio Regulations, Section IV. Radio Stations and Systems .... It had several versions (M, S and S2). It supported receivers with card slots and those with embedded keys. Its most widespread use was in Scandinavia, where the only EuroCrypt protected broadcasts remained until July 2006 (in France, they stopped in 1998). It was also hacked with pirate cards, which was popular in many countries in Europe, especially in order to watch English-language channels such as Filmnet Plus and TV1000. EuroCrypt evolved into the Viaccess system for digital television. SourcesFrequency List dated 1998.Denmark's Radio receiver info Digital television Digital rights management systems ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
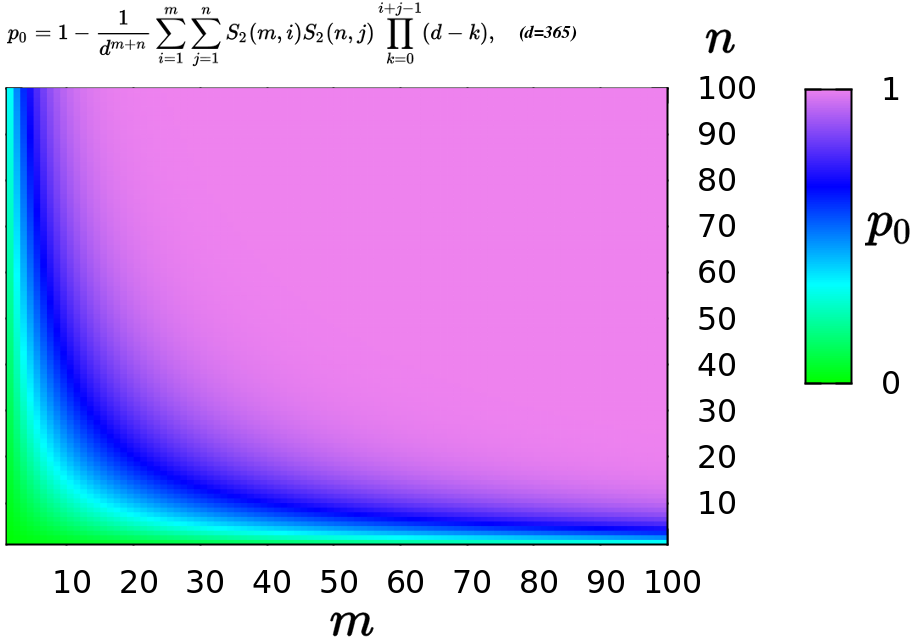
Birthday Paradox
In probability theory, the birthday problem asks for the probability that, in a set of randomly chosen people, at least two will share the same birthday. The birthday paradox is the counterintuitive fact that only 23 people are needed for that probability to exceed 50%. The birthday paradox is a veridical paradox: it seems wrong at first glance but is, in fact, true. While it may seem surprising that only 23 individuals are required to reach a 50% probability of a shared birthday, this result is made more intuitive by considering that the birthday comparisons will be made between every possible pair of individuals. With 23 individuals, there are = 253 pairs to consider. Real-world applications for the birthday problem include a cryptographic attack called the birthday attack, which uses this probabilistic model to reduce the complexity of finding a Collision attack, collision for a hash function, as well as calculating the approximate risk of a hash collision existi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Weak Key
In cryptography, a weak key is a key, which, used with a specific cipher, makes the cipher behave in some undesirable way. Weak keys usually represent a very small fraction of the overall keyspace, which usually means that, a cipher key made by random number generation is very unlikely to give rise to a security problem. Nevertheless, it is considered desirable for a cipher to have no weak keys. A cipher with no weak keys is said to have a ''flat'', or ''linear'', key space. Historical origins Virtually all rotor-based cipher machines (from 1925 onwards) have implementation flaws that lead to a substantial number of weak keys being created. Some rotor machines have more problems with weak keys than others, as modern block and stream ciphers do. The first stream cipher machines were also rotor machines and had some of the same problems of weak keys as the more traditional rotor machines. The T52 was one such stream cipher machine that had weak key problems. The British first ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Central Bank Of Russia
The Central Bank of the Russian Federation (), commonly known as the Bank of Russia (), also called the Central Bank of Russia (CBR), is the central bank of the Russia, Russian Federation. The bank was established on 13 July 1990. It traces its beginnings to the State Bank of the Russian Empire established in 1860. The bank is headquartered on Neglinnaya Street in Moscow. Its functions are described in the Constitution of Russia (Article 75), as well as in federal law. History Shortly after Declaration of State Sovereignty of the Russian Soviet Federative Socialist Republic, declaring sovereignty in June 1990, the Russian SFSR decreed the creation of a central bank under the leadership of . Matiukhin commandeered Russian branches of the State Bank of the USSR and brought them under the control of the Bank of the RSFSR. A comprehensive central bank statute was passed in December 1990 and the bank adopted a charter in June 1991. A remnant of the State Bank continued to operate ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Pseudorandom Number Generator
A pseudorandom number generator (PRNG), also known as a deterministic random bit generator (DRBG), is an algorithm for generating a sequence of numbers whose properties approximate the properties of sequences of random number generation, random numbers. The PRNG-generated sequence is not truly random, because it is completely determined by an initial value, called the PRNG's ''random seed, seed'' (which may include truly random values). Although sequences that are closer to truly random can be generated using hardware random number generators, ''pseudorandom number generators'' are important in practice for their speed in number generation and their reproducibility. PRNGs are central in applications such as simulations (e.g. for the Monte Carlo method), electronic games (e.g. for procedural generation), and cryptography. Cryptographic applications require the output not to be predictable from earlier outputs, and more cryptographically-secure pseudorandom number generator, elabora ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Modular Arithmetic
In mathematics, modular arithmetic is a system of arithmetic operations for integers, other than the usual ones from elementary arithmetic, where numbers "wrap around" when reaching a certain value, called the modulus. The modern approach to modular arithmetic was developed by Carl Friedrich Gauss in his book '' Disquisitiones Arithmeticae'', published in 1801. A familiar example of modular arithmetic is the hour hand on a 12-hour clock. If the hour hand points to 7 now, then 8 hours later it will point to 3. Ordinary addition would result in , but 15 reads as 3 on the clock face. This is because the hour hand makes one rotation every 12 hours and the hour number starts over when the hour hand passes 12. We say that 15 is ''congruent'' to 3 modulo 12, written 15 ≡ 3 (mod 12), so that 7 + 8 ≡ 3 (mod 12). Similarly, if one starts at 12 and waits 8 hours, the hour hand will be at 8. If one instead waited twice as long, 16 hours, the hour hand would be on 4. This ca ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
S-box
In cryptography, an S-box (substitution-box) is a basic component of symmetric key algorithms which performs substitution. In block ciphers, they are typically used to obscure the relationship between the key and the ciphertext, thus ensuring Claude Shannon, Shannon's property of confusion and diffusion, confusion. Mathematically, an S-box is a nonlinear vectorial Boolean function. In general, an S-box takes some number of input bits, ''m'', and transforms them into some number of output bits, ''n'', where ''n'' is not necessarily equal to ''m''. An ''m''×''n'' S-box can be implemented as a lookup table with 2''m'' words of ''n'' bits each. Fixed tables are normally used, as in the Data Encryption Standard (DES), but in some ciphers the tables are generated dynamically from the cryptographic key, key (e.g. the Blowfish (cipher), Blowfish and the Twofish encryption algorithms). Example One good example of a fixed table is the S-box from DES (S5), mapping 6-bit input into a 4-bi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Block Size (cryptography)
In modern cryptography, symmetric key ciphers are generally divided into stream ciphers and block ciphers. Block ciphers operate on a fixed length string of bits. The length of this bit string is the block size. Both the input ( plaintext) and output (ciphertext) are the same length; the output cannot be shorter than the input this follows logically from the pigeonhole principle and the fact that the cipher must be reversibleand it is undesirable for the output to be longer than the input. Until the announcement of NIST's AES contest, the majority of block ciphers followed the example of the DES in using a block size of 64 bits (8 bytes). However, the birthday paradox In probability theory, the birthday problem asks for the probability that, in a set of randomly chosen people, at least two will share the same birthday. The birthday paradox is the counterintuitive fact that only 23 people are needed for that ... indicates that after accumulating several blocks equal ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |