|
Electronic Privacy
Internet privacy involves the right or mandate of personal privacy concerning the storing, re-purposing, provision to third parties, and displaying of information pertaining to oneself via Internet. Internet privacy is a subset of data privacy. Privacy concerns have been articulated from the beginnings of large-scale computer sharing. Privacy can entail either personally identifiable information (PII) or non-PII information such as a site visitor's behavior on a website. PII refers to any information that can be used to identify an individual. For example, age and physical address alone could identify who an individual is without explicitly disclosing their name, as these two factors are unique enough to identify a specific person typically. Other forms of PII may soon include GPS tracking data used by apps, as the daily commute and routine information can be enough to identify an individual. It has been suggested that the "appeal of online services is to broadcast personal info ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Privacy
Privacy (, ) is the ability of an individual or group to seclude themselves or information about themselves, and thereby express themselves selectively. The domain of privacy partially overlaps with security, which can include the concepts of appropriate use and protection of information. Privacy may also take the form of bodily integrity. The right not to be subjected to unsanctioned invasions of privacy by the government, corporations, or individuals is part of many countries' privacy laws, and in some cases, constitutions. The concept of universal individual privacy is a modern concept primarily associated with Western culture, particularly British and North American, and remained virtually unknown in some cultures until recent times. Now, most cultures recognize the ability of individuals to withhold certain parts of personal information from wider society. With the rise of technology, the debate regarding privacy has shifted from a bodily sense to a digital sense. As the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Federal Trade Commission
The Federal Trade Commission (FTC) is an independent agency of the United States government whose principal mission is the enforcement of civil (non-criminal) antitrust law and the promotion of consumer protection. The FTC shares jurisdiction over federal civil antitrust enforcement with the Department of Justice Antitrust Division. The agency is headquartered in the Federal Trade Commission Building in Washington, DC. The FTC was established in 1914 with the passage of the Federal Trade Commission Act, signed in response to the 19th-century monopolistic trust crisis. Since its inception, the FTC has enforced the provisions of the Clayton Act, a key antitrust statute, as well as the provisions of the FTC Act, et seq. Over time, the FTC has been delegated with the enforcement of additional business regulation statutes and has promulgated a number of regulations (codified in Title 16 of the Code of Federal Regulations). The broad statutory authority granted to the FTC provide ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Email Scam
Email fraud (or email scam) is intentional deception for either personal gain or to damage another individual by means of email. Almost as soon as email became widely used, it began to be used as a means to defraud people. Email fraud can take the form of a "con game", or ''scam''. Confidence tricks tend to exploit the inherent greed and dishonesty of its victims. The prospect of a 'bargain' or 'something for nothing' can be very tempting. Email fraud, as with other ' bunco schemes,' usually targets naive individuals who put their confidence in schemes to get rich quickly. These include 'too good to be true' investments or offers to sell popular items at 'impossibly low' prices. Many people have lost their life savings due to fraud. Forms Spoofing Email sent from someone pretending to be someone else is known as spoofing. Spoofing may take place in a number of ways. Common to all of them is that the actual sender's name and the origin of the message are concealed or masked ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Adolescence
Adolescence () is a transitional stage of physical and psychological development that generally occurs during the period from puberty to adulthood (typically corresponding to the age of majority). Adolescence is usually associated with the teenage years, but its physical, psychological or cultural expressions may begin earlier and end later. Puberty now typically begins during preadolescence, particularly in females. Physical growth (particularly in males) and cognitive development can extend past the teens. Age provides only a rough marker of adolescence, and scholars have not agreed upon a precise definition. Some definitions start as early as 10 and end as late as 25 or 26. The World Health Organization definition officially designates an adolescent as someone between the ages of 10 and 19. Biological development Puberty in general Puberty is a period of several years in which rapid physical growth and psychological changes occur, culminating in sexual maturity. The aver ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Lane V
In road transport, a lane is part of a roadway that is designated to be used by a single line of vehicles to control and guide drivers and reduce traffic conflicts. Most public roads (highways) have at least two lanes, one for traffic in each direction, separated by lane markings. On multilane roadways and busier two-lane roads, lanes are designated with road surface markings. Major highways often have two multi-lane roadways separated by a median. Some roads and bridges that carry very low volumes of traffic are less than wide, and are only a single lane wide. Vehicles travelling in opposite directions must slow or stop to pass each other. In rural areas, these are often called country lanes. In urban areas, alleys are often only one lane wide. Urban and suburban one lane roads are often designated for one-way traffic. History For much of human history, roads did not need lane markings because most people walked or rode horses at relatively slow speeds. However, when ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Electronic Frontier Foundation
The Electronic Frontier Foundation (EFF) is an international non-profit digital rights group based in San Francisco, California. The foundation was formed on 10 July 1990 by John Gilmore, John Perry Barlow and Mitch Kapor to promote Internet civil liberties. The EFF provides funds for legal defense in court, presents '' amicus curiae'' briefs, defends individuals and new technologies from what it considers abusive legal threats, works to expose government malfeasance, provides guidance to the government and courts, organizes political action and mass mailings, supports some new technologies which it believes preserve personal freedoms and online civil liberties, maintains a database and web sites of related news and information, monitors and challenges potential legislation that it believes would infringe on personal liberties and fair use and solicits a list of what it considers abusive patents with intentions to defeat those that it considers without merit. History Fou ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Software Bug
A software bug is an error, flaw or fault in the design, development, or operation of computer software that causes it to produce an incorrect or unexpected result, or to behave in unintended ways. The process of finding and correcting bugs is termed " debugging" and often uses formal techniques or tools to pinpoint bugs. Since the 1950s, some computer systems have been designed to deter, detect or auto-correct various computer bugs during operations. Bugs in software can arise from mistakes and errors made in interpreting and extracting users' requirements, planning a program's design, writing its source code, and from interaction with humans, hardware and programs, such as operating systems or libraries. A program with many, or serious, bugs is often described as ''buggy''. Bugs can trigger errors that may have ripple effects. The effects of bugs may be subtle, such as unintended text formatting, through to more obvious effects such as causing a program to crash, freezing th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
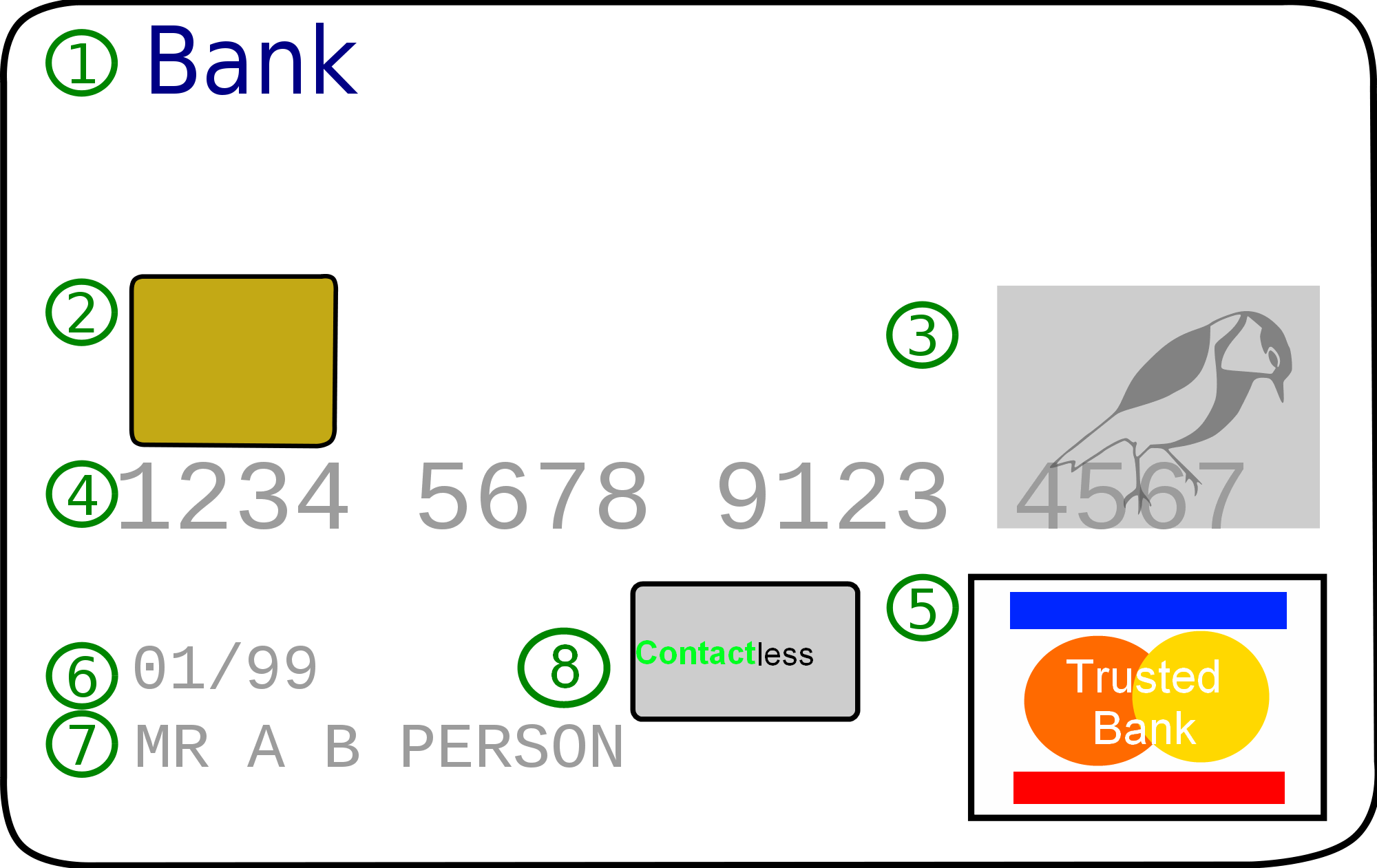
Credit Card
A credit card is a payment card issued to users (cardholders) to enable the cardholder to pay a merchant for goods and services based on the cardholder's accrued debt (i.e., promise to the card issuer to pay them for the amounts plus the other agreed charges). The card issuer (usually a bank or credit union) creates a revolving account and grants a line of credit to the cardholder, from which the cardholder can borrow money for payment to a merchant or as a cash advance. There are two credit card groups: consumer credit cards and business credit cards. Most cards are plastic, but some are metal cards (stainless steel, gold, palladium, titanium), and a few gemstone-encrusted metal cards. A regular credit card is different from a charge card, which requires the balance to be repaid in full each month or at the end of each statement cycle. In contrast, credit cards allow the consumers to build a continuing balance of debt, subject to interest being charged. A credit car ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Social Media
Social media are interactive media technologies that facilitate the creation and sharing of information, ideas, interests, and other forms of expression through virtual communities and networks. While challenges to the definition of ''social media'' arise due to the variety of stand-alone and built-in social media services currently available, there are some common features: # Social media are interactive Web 2.0 Internet-based applications. # User-generated content—such as text posts or comments, digital photos or videos, and data generated through all online interactions—is the lifeblood of social media. # Users create service-specific profiles for the website or app that are designed and maintained by the social media organization. # Social media helps the development of online social networks by connecting a user's profile with those of other individuals or groups. The term ''social'' in regard to media suggests that platforms are user-centric and enable communal ac ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Web Browsing History
Web browsing history refers to the list of web pages a user has visited, as well as associated metadata such as page title and time of visit. It is usually stored locally by web browsers in order to provide the user with a history list to go back to previously visited pages. It can reflect the user's interests, needs, and browsing habits.Du, Weidman, Zhenyu Cheryl Qian, Paul Parsons, Yingjie Victor Chen. 2018. “Personal Web Library: organizing and visualizing Web browsing history”. ''International Journal of Web Information Systems'' 14(2): 212-232. All major browsers have a private browsing mode in which browsing history is not recorded. This is to protect against browsing history being collected by third parties for targeted advertising or other purposes. Applications Local history Locally stored browsing history can facilitate rediscovering lost previously visited web pages of which one only has a vague memory in mind, or pages difficult to find due to being located w ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Twitter
Twitter is an online social media and social networking service owned and operated by American company Twitter, Inc., on which users post and interact with 280-character-long messages known as "tweets". Registered users can post, like, and 'Reblogging, retweet' tweets, while unregistered users only have the ability to read public tweets. Users interact with Twitter through browser or mobile Frontend and backend, frontend software, or programmatically via its APIs. Twitter was created by Jack Dorsey, Noah Glass, Biz Stone, and Evan Williams (Internet entrepreneur), Evan Williams in March 2006 and launched in July of that year. Twitter, Inc. is based in San Francisco, California and has more than 25 offices around the world. , more than 100 million users posted 340 million tweets a day, and the service handled an average of 1.6 billion Web search query, search queries per day. In 2013, it was one of the ten List of most popular websites, most-visited websites and has been de ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Facebook
Facebook is an online social media and social networking service owned by American company Meta Platforms. Founded in 2004 by Mark Zuckerberg with fellow Harvard College students and roommates Eduardo Saverin, Andrew McCollum, Dustin Moskovitz, and Chris Hughes, its name comes from the face book directories often given to American university students. Membership was initially limited to Harvard students, gradually expanding to other North American universities and, since 2006, anyone over 13 years old. As of July 2022, Facebook claimed 2.93 billion monthly active users, and ranked third worldwide among the most visited websites as of July 2022. It was the most downloaded mobile app of the 2010s. Facebook can be accessed from devices with Internet connectivity, such as personal computers, tablets and smartphones. After registering, users can create a profile revealing information about themselves. They can post text, photos and multimedia which are shared with any ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
.jpg)

.jpg)