|
Echo Reply
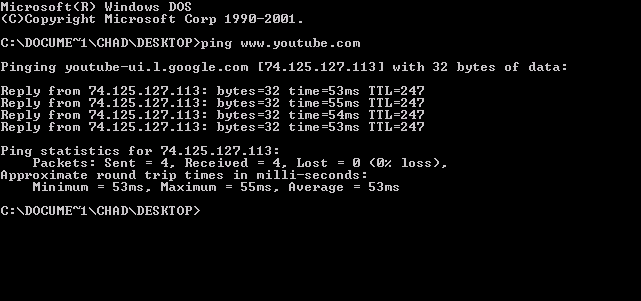
ping is a computer network administration software utility used to test the reachability of a host on an Internet Protocol (IP) network. It is available for virtually all operating systems that have networking capability, including most embedded network administration software. Ping measures the round-trip time for messages sent from the originating host to a destination computer that are echoed back to the source. The name comes from active sonar terminology that sends a pulse of sound and listens for the echo to detect objects under water. Ping operates by means of Internet Control Message Protocol (ICMP) packets. ''Pinging'' involves sending an ICMP echo request to the target host and waiting for an ICMP echo reply. The program reports errors, packet loss, and a statistical summary of the results, typically including the minimum, maximum, the mean round-trip times, and standard deviation of the mean. The command-line options of the ping utility and its output vary betwe ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mike Muuss
Michael John Muuss (October 16, 1958 – November 20, 2000) was the American author of the freeware network tool ping. Career A graduate of Johns Hopkins University, Muuss was a senior scientist specializing in geometric solid modeling, ray-tracing, MIMD architectures and digital computer networks at the United States Army Research Laboratory at Aberdeen Proving Ground, Maryland when he died. He wrote a number of software packages (including BRL-CAD) and network tools (including ttcp and the concept of the default route or "default gateway") and contributed to many others (including BIND). However, the thousand-line ping, which he wrote in December 1983 while working at the Ballistic Research Laboratory, is the program for which he is most remembered. Due to its usefulness, ping has been implemented on a large number of operating systems, initially Berkeley Software Distribution (BSD) and Unix, but later others including Windows and Mac OS X. In 1993, the USENIX Associatio ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Internet Control Message Protocol
The Internet Control Message Protocol (ICMP) is a supporting protocol in the Internet protocol suite. It is used by network devices, including routers, to send error messages and operational information indicating success or failure when communicating with another IP address, for example, an error is indicated when a requested service is not available or that a host or router could not be reached. ICMP differs from transport protocols such as TCP and UDP in that it is not typically used to exchange data between systems, nor is it regularly employed by end-user network applications (with the exception of some diagnostic tools like ping and traceroute). ICMP for IPv4 is defined in RFC 792. A separate ICMPv6, defined by RFC 4443, is used with IPv6. Technical details ICMP is part of the Internet protocol suite as defined in RFC 792. ICMP messages are typically used for diagnostic or control purposes or generated in response to errors in IP operations (as specified in RFC 1122 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Sonar
Sonar (sound navigation and ranging or sonic navigation and ranging) is a technique that uses sound propagation (usually underwater, as in submarine navigation) to navigation, navigate, measure distances (ranging), communicate with or detect objects on or under the surface of the water, such as other vessels. "Sonar" can refer to one of two types of technology: ''passive'' sonar means listening for the sound made by vessels; ''active'' sonar means emitting pulses of sounds and listening for echoes. Sonar may be used as a means of acoustic location and of measurement of the echo characteristics of "targets" in the water. Acoustic location in air was used before the introduction of radar. Sonar may also be used for robot navigation, and SODAR (an upward-looking in-air sonar) is used for atmospheric investigations. The term ''sonar'' is also used for the equipment used to generate and receive the sound. The acoustic frequencies used in sonar systems vary from very low (infrasonic ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
David L
David (; , "beloved one") (traditional spelling), , ''Dāwūd''; grc-koi, Δαυΐδ, Dauíd; la, Davidus, David; gez , ዳዊት, ''Dawit''; xcl, Դաւիթ, ''Dawitʿ''; cu, Давíдъ, ''Davidŭ''; possibly meaning "beloved one". was, according to the Hebrew Bible, the third king of the United Kingdom of Israel. In the Books of Samuel, he is described as a young shepherd and harpist who gains fame by slaying Goliath, a champion of the Philistines, in southern Canaan. David becomes a favourite of Saul, the first king of Israel; he also forges a notably close friendship with Jonathan, a son of Saul. However, under the paranoia that David is seeking to usurp the throne, Saul attempts to kill David, forcing the latter to go into hiding and effectively operate as a fugitive for several years. After Saul and Jonathan are both killed in battle against the Philistines, a 30-year-old David is anointed king over all of Israel and Judah. Following his rise to power, David ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
US Army Research Laboratory
The U.S. Army Combat Capabilities Development Command Army Research Laboratory (DEVCOM ARL) is the U.S. Army's foundational research laboratory. ARL is headquartered at the Adelphi Laboratory Center (ALC) in Adelphi, Maryland. Its largest single site is at Aberdeen Proving Ground, Maryland. Other major ARL locations include Research Triangle Park, North Carolina, White Sands Missile Range, New Mexico, Graces Quarters, Maryland, and NASA's Glenn Research Center, Ohio and Langley Research Center, Virginia. ARL also has regional sites in Playa Vista, California (ARL West), Chicago (ARL Central), Austin, TX (ARL South), and Boston (ARL Northeast). DEVCOM ARL has three directorates: *Army Research Office, located in Research Triangle Park *Army Research Directorate *Research Business Directorate History Before the forming of the ARL, the United States Army had research facilities dating back to 1820 when the laboratory at Watertown Arsenal, Massachusetts, studied pyrotechnics a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Ballistic Research Laboratory
The Ballistic Research Laboratory (BRL) was a leading U.S. Army research establishment situated at Aberdeen Proving Ground, Maryland that specialized in ballistics ( interior, exterior, and terminal) as well as vulnerability and lethality analysis. BRL served as a major Army center for research and development in technologies related to weapon phenomena, armor, electronic devices, and high-speed computing. In 1992, BRL's mission, personnel, and facilities were incorporated into the newly created Army Research Laboratory (ARL), and BRL was disestablished. BRL is perhaps best known for commissioning the creation of ENIAC, the first electronic general-purpose digital computer. History Formation The history of the Ballistic Research Laboratory dates back to World War I with the Office of the Chief of Ordnance (OCO) within the U.S. Army. During the first year of U.S. involvement in the war, the OCO was responsible for supervising ballistic firings at Sandy Hook Proving Ground in New J ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Internet Control Message Protocol Version 6
Internet Control Message Protocol version 6 (ICMPv6) is the implementation of the Internet Control Message Protocol (ICMP) for Internet Protocol version 6 (IPv6). ICMPv6 is an integral part of IPv6 and performs error reporting and diagnostic functions. ICMPv6 has a framework for extensions to implement new features. Several extensions have been published, defining new ICMPv6 message types as well as new options for existing ICMPv6 message types. For example, Neighbor Discovery Protocol (NDP) is a node discovery protocol based on ICMPv6 which replaces and enhances functions of ARP. Secure Neighbor Discovery (SEND) is an extension of NDP with extra security. Multicast Listener Discovery (MLD) is used by IPv6 routers for discovering multicast listeners on a directly attached link, much like Internet Group Management Protocol (IGMP) is used in IPv4. Multicast Router Discovery (MRD) allows the discovery of multicast routers. Message types and formats ICMPv6 messages may be classifie ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
IPv6
Internet Protocol version 6 (IPv6) is the most recent version of the Internet Protocol (IP), the communication protocol, communications protocol that provides an identification and location system for computers on networks and routes traffic across the Internet. IPv6 was developed by the Internet Engineering Task Force (IETF) to deal with the long-anticipated problem of IPv4 address exhaustion, and is intended to replace IPv4. In December 1998, IPv6 became a Draft Standard for the IETF, which subsequently ratified it as an Internet Standard on 14 July 2017. Devices on the Internet are assigned a unique IP address for identification and location definition. With the rapid growth of the Internet after commercialization in the 1990s, it became evident that far more addresses would be needed to connect devices than the IPv4 address space had available. By 1998, the IETF had formalized the successor protocol. IPv6 uses 128-bit addresses, theoretically allowing 2128, or approximatel ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Time To Live
Time to live (TTL) or hop limit is a mechanism which limits the lifespan or lifetime of data in a computer or network. TTL may be implemented as a counter or timestamp attached to or embedded in the data. Once the prescribed event count or timespan has elapsed, data is discarded or revalidated. In computer networking, TTL prevents a data packet from circulating indefinitely. In computing applications, TTL is commonly used to improve the performance and manage the caching of data. Description The original DARPA Internet Protocol's RFC document describes TTL as: IP packets Under the Internet Protocol, TTL is an 8-bit field. In the IPv4 header, TTL is the 9th octet of 20. In the IPv6 header, it is the 8th octet of 40. The maximum TTL value is 255, the maximum value of a single octet. A recommended initial value is 64. The time-to-live value can be thought of as an upper bound on the time that an IP datagram can exist in an Internet system. The TTL field is set by the sender ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Command-line Option
A command-line interpreter or command-line processor uses a command-line interface (CLI) to receive commands from a user in the form of lines of text. This provides a means of setting parameters for the environment, invoking executables and providing information to them as to what actions they are to perform. In some cases the invocation is conditional based on conditions established by the user or previous executables. Such access was first provided by computer terminals starting in the mid-1960s. This provided an interactive environment not available with punched cards or other input methods. Today, many users rely upon graphical user interfaces and menu-driven interactions. However, some programming and maintenance tasks may not have a graphical user interface and use a command line. Alternatives to the command-line interface include text-based user interface menus (for example, IBM AIX SMIT), keyboard shortcuts, and various desktop metaphors centered on the pointer (usual ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Standard Deviation
In statistics, the standard deviation is a measure of the amount of variation or dispersion of a set of values. A low standard deviation indicates that the values tend to be close to the mean (also called the expected value) of the set, while a high standard deviation indicates that the values are spread out over a wider range. Standard deviation may be abbreviated SD, and is most commonly represented in mathematical texts and equations by the lower case Greek letter σ (sigma), for the population standard deviation, or the Latin letter '' s'', for the sample standard deviation. The standard deviation of a random variable, sample, statistical population, data set, or probability distribution is the square root of its variance. It is algebraically simpler, though in practice less robust, than the average absolute deviation. A useful property of the standard deviation is that, unlike the variance, it is expressed in the same unit as the data. The standard deviation of a popu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |