|
Dragon1
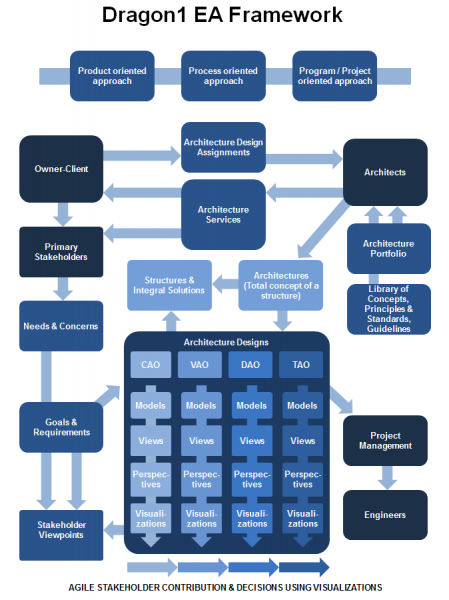
Dragon1 EA Method (Dragon1) is an The Open Group, open method for visual Enterprise Architecture, enterprise architecture and Enterprise Architecture Framework, enterprise architecture framework. Dragon1 covers the development of a variety of architectures, such as Business, enterprise, governance, business, information and Information technology architecture, technical architecture. It also covers solution architecture, reference architectures and Computer security, security architecture or Human Capital Architecture (HCA). Overview Dragon1, an open EA method for visual enterprise architecture, has been developed by Dragon1 Architecture Foundation, from the experience of practicing architecture on projects for clients across Europe. The first version was released in 2003 and was based on the ideas of Mark Paauwe about Enterprise Architecture, enterprise architecture, architecture visualization and architecture principles. Dragon1 EA Method is said to be the following: * A comp ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Enterprise Architecture Framework
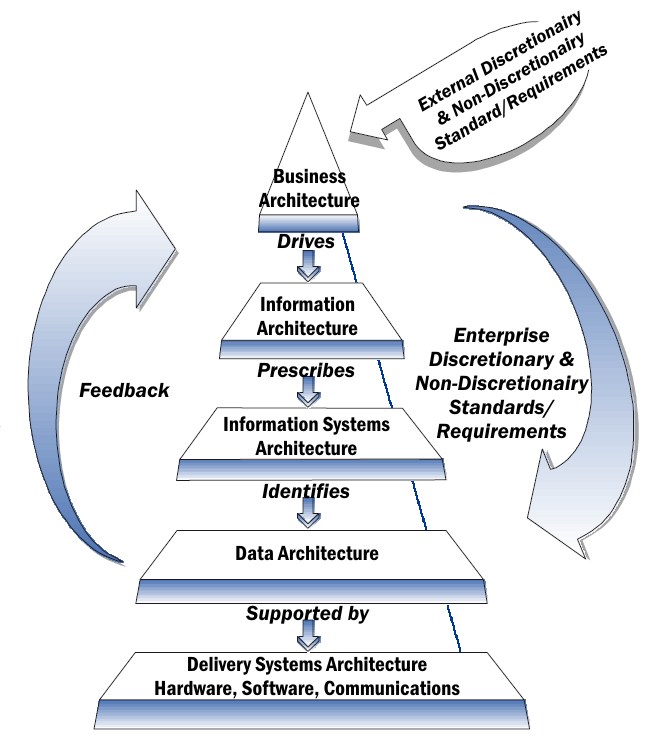
An enterprise architecture framework (EA framework) defines how to create and use an enterprise architecture. An architecture framework provides principles and practices for creating and using the architecture description of a system. It structures architects' thinking by dividing the architecture description into domains, layers, or views, and offers models - typically matrices and diagrams - for documenting each view. This allows for making systemic design decisions on all the components of the system and making long-term decisions around new design requirements, sustainability, and support. Overview Enterprise architecture regards the enterprise as a large and complex system or system of systems. To manage the scale and complexity of this system, an architectural framework provides tools and approaches that help architects abstract from the level of detail at which builders work, to bring enterprise design tasks into focus and produce valuable architecture description doc ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Security
Computer security, cybersecurity (cyber security), or information technology security (IT security) is the protection of computer systems and networks from attack by malicious actors that may result in unauthorized information disclosure, theft of, or damage to hardware, software, or data, as well as from the disruption or misdirection of the services they provide. The field has become of significance due to the expanded reliance on computer systems, the Internet, and wireless network standards such as Bluetooth and Wi-Fi, and due to the growth of smart devices, including smartphones, televisions, and the various devices that constitute the Internet of things (IoT). Cybersecurity is one of the most significant challenges of the contemporary world, due to both the complexity of information systems and the societies they support. Security is of especially high importance for systems that govern large-scale systems with far-reaching physical effects, such as power distribu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Request For Comments
A Request for Comments (RFC) is a publication in a series from the principal technical development and standards-setting bodies for the Internet, most prominently the Internet Engineering Task Force (IETF). An RFC is authored by individuals or groups of engineers and computer scientists in the form of a memorandum describing methods, behaviors, research, or innovations applicable to the working of the Internet and Internet-connected systems. It is submitted either for peer review or to convey new concepts, information, or, occasionally, engineering humor. The IETF adopts some of the proposals published as RFCs as Internet Standards. However, many RFCs are informational or experimental in nature and are not standards. The RFC system was invented by Steve Crocker in 1969 to help record unofficial notes on the development of ARPANET. RFCs have since become official documents of Internet specifications, communications protocols, procedures, and events. According to Crocker, t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Information Technology Architect Certification
The IT Architect Certification is an independent global certification program for qualifying the skills, knowledge and experience of IT, Business and Enterprise Architects. This program was developed by The Open Group members in response to the growing demand for experienced IT architects. The Open Group, a vendor- and technology-neutral industry consortium, offers IT Architect Certification to certify skills and experience in the IT architecture community. The Program The program is based on the proven best practices in the industry and sets an independent, industry-wide standard for IT Architects... Under the program, practicing IT Architects can achieve the certification based on demonstrating substantial skills, experience and success in designing solutions across the whole lifecycle. In addition to certifying individuals directly, the program also provides accreditation of third-party IT architect certification programs. The skill and experience requirements for both the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Stakeholder (corporate)
In a corporation, a stakeholder is a member of "groups without whose support the organization would cease to exist", as defined in the first usage of the word in a 1963 internal memorandum at the Stanford Research Institute. The theory was later developed and championed by R. Edward Freeman in the 1980s. Since then it has gained wide acceptance in business practice and in theorizing relating to strategic management, corporate governance, business purpose and corporate social responsibility (CSR). The definition of corporate responsibilities through a classification of stakeholders to consider has been criticized as creating a false dichotomy between the "shareholder model" and the "stakeholders model" or a false analogy of the obligations towards shareholders and other interested parties. Types Any action taken by any organization or any group might affect those people who are linked with them in the private sector. For examples these are parents, children, customers, owners, em ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Add-on Domain
Virtual hosting is a method for hosting multiple domain names (with separate handling of each name) on a single server (or pool of servers). This allows one server to share its resources, such as memory and processor cycles, without requiring all services provided to use the same host name. The term virtual hosting is usually used in reference to web servers but the principles do carry over to other Internet services. One widely used application is shared web hosting. The price for shared web hosting is lower than for a dedicated web server because many customers can be hosted on a single server. It is also very common for a single entity to want to use multiple names on the same machine so that the names can reflect services offered rather than where those services happen to be hosted. There are two main types of virtual hosting, name-based and IP-based. Name-based virtual hosting uses the host name presented by the client. This saves IP addresses and the associated administra ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Erik Proper
Henderik Alex (Erik) Proper (born 22 May 1967) is a Dutch computer scientist, aFNRPEARL Laureate, and a senior research manager within the Computer Science (ITIS) department of the Luxembourg Institute of Science and Technology (LIST). He is also adjunct professor in data and knowledge engineering at the University of Luxembourg. He is known for work on conceptual modeling, enterprise architecture and enterprise engineering. Biography Born in Rheden, Proper studied computer science at the Radboud University Nijmegen. In 1990 he received his MSc, and in 1994 his PhD with distinction with a thesis entitled "A Theory for Conceptual Modelling of Evolving Application Domains" under supervision of Eckhard D. Falkenberg. After graduation, Proper started his academic as computer science researcher at the University of Queensland in Australia, and lecturer at the Queensland University of Technology. Back in The Netherlands in 1997 Proper started working in the software industry as con ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Danny Greefhorst
Danny Greefhorst (born 31 December 1972) is a Dutch enterprise architect and consultant aArchiXL known for his work in the field of enterprise architecture. Biography Greefhorst obtained his master in computer science at Utrecht University in 1995 with the master thesis ""A Simulation Environment for Ariadne." Furthermore, he became IBM Certified Senior IT Architect in 2004. He is TOGAF 9 level 2 and ArchiMate 2.0 certified."Danny Greefhorst, Director at ArchiXL," at ''linkedin.com.'' Accessed 09.03.2015. After graduation Greefhorst started his career at the Software Engineering Research Centre in Utrecht in 1995. He worked in various roles from software researcher, designer, architect, developer, tester and webmaster to class instructor, coach, seminar organiser, and IT consultant, and published his first papers. In 2001 he moved to IBM, where he became Senior IT Architect for five years. After another year as Principal Consultant at the management consultancy firm Yellowtail, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Solution Architecture
Solution architecture, term used in information technology with various definitions such as; "A description of a discrete and focused business operation or activity and how IS/ IT supports that operation". Definitions The Open Group's definition of Solution Architecture, as provided above, is accompanied by the following three from Scaled Agile, Gartner and Greefhorst/Proper. It is worth noting that the Open Group does not recognize the role "Solution Architect" in its TOGAF skills framework whilst Glassdoor advertised 55,000 Solution Architect roles in August 2020. * Scaled agile (2020) ''Solution Architect/Engineering is responsible for defining and communicating a shared technical and architectural vision across a "Solution Train" to help ensure the system or Solution under development is fit for its intended purpose.'' * Gartner (2013) ''A solution architecture (SA) is an architectural description of a specific solution. SAs combine guidance from different enterprise archit ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Reference Architecture
A reference architecture in the field of software architecture or enterprise architecture provides a template solution for an architecture for a particular domain. It also provides a common vocabulary with which to discuss implementations, often with the aim to stress commonality. A software reference architecture is a software architecture where the structures and respective elements and relations provide templates for concrete architectures in a particular domain or in a family of software systems. A reference architecture often consists of a list of functions and some indication of their interfaces (or APIs) and interactions with each other and with functions located outside of the scope of the reference architecture. Reference architectures can be defined at different levels of abstraction. A highly abstract one might show different pieces of equipment on a communications network, each providing different functions. A lower level one might demonstrate the interactions of p ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
The Open Group
The Open Group is a global consortium that seeks to "enable the achievement of business objectives" by developing "open, vendor-neutral technology standards and certifications." It has over 840 member organizations and provides a number of services, including strategy, management, innovation and research, standards, certification, and test development. It was established in 1996 when X/Open merged with the Open Software Foundation. The Open Group is the certifying body for the UNIX trademark, and publishes the Single UNIX Specification technical standard, which extends the POSIX standards. The Open Group also develops and manages the TOGAF® standard, which is an industry standard enterprise architecture framework. Members The over 840 members include a range of technology vendors and buyers as well as government agencies, including, for example, Capgemini, Fujitsu, HPE, Orbus Software, IBM, Huawei, Philips, the U.S. Department of Defense, and NASA. There is no obligation ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |