|
Data Poisoning
Adversarial machine learning is the study of the attacks on machine learning algorithms, and of the defenses against such attacks. A survey from May 2020 revealed practitioners' common feeling for better protection of machine learning systems in industrial applications. Machine learning techniques are mostly designed to work on specific problem sets, under the assumption that the training and test data are generated from the same statistical distribution (Independent and identically distributed random variables, IID). However, this assumption is often dangerously violated in practical high-stake applications, where users may intentionally supply fabricated data that violates the statistical assumption. Most common attacks in adversarial machine learning include evasion attacks, data poisoning attacks, Byzantine attacks and model extraction. History At the MIT Spam Conference in January 2004, John Graham-Cumming showed that a machine-learning spam filter could be used to defeat ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Machine Learning
Machine learning (ML) is a field of study in artificial intelligence concerned with the development and study of Computational statistics, statistical algorithms that can learn from data and generalise to unseen data, and thus perform Task (computing), tasks without explicit Machine code, instructions. Within a subdiscipline in machine learning, advances in the field of deep learning have allowed Neural network (machine learning), neural networks, a class of statistical algorithms, to surpass many previous machine learning approaches in performance. ML finds application in many fields, including natural language processing, computer vision, speech recognition, email filtering, agriculture, and medicine. The application of ML to business problems is known as predictive analytics. Statistics and mathematical optimisation (mathematical programming) methods comprise the foundations of machine learning. Data mining is a related field of study, focusing on exploratory data analysi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Traffic Flow (computer Networking)
In packet switching networks, traffic flow, packet flow or ''network flow'' is a sequence of packets from a source computer to a destination, which may be another host, a multicast group, or a broadcast domain. RFC 2722 defines traffic flow as "an artificial logical equivalent to a call or connection." RFC 3697 defines traffic flow as "a sequence of packets sent from a particular source to a particular unicast, anycast, or multicast destination that the source desires to label as a flow. A flow could consist of all packets in a specific transport connection or a media stream. However, a flow is not necessarily 1:1 mapped to a transport connection." Flow is also defined in RFC 3917 as "a set of IP packets passing an observation point in the network during a certain time interval." Packet flow temporal efficiency can be affected by one-way delay (OWD) that is described as a combination of the following components: * Processing delay (the time taken to process a packet in a netw ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
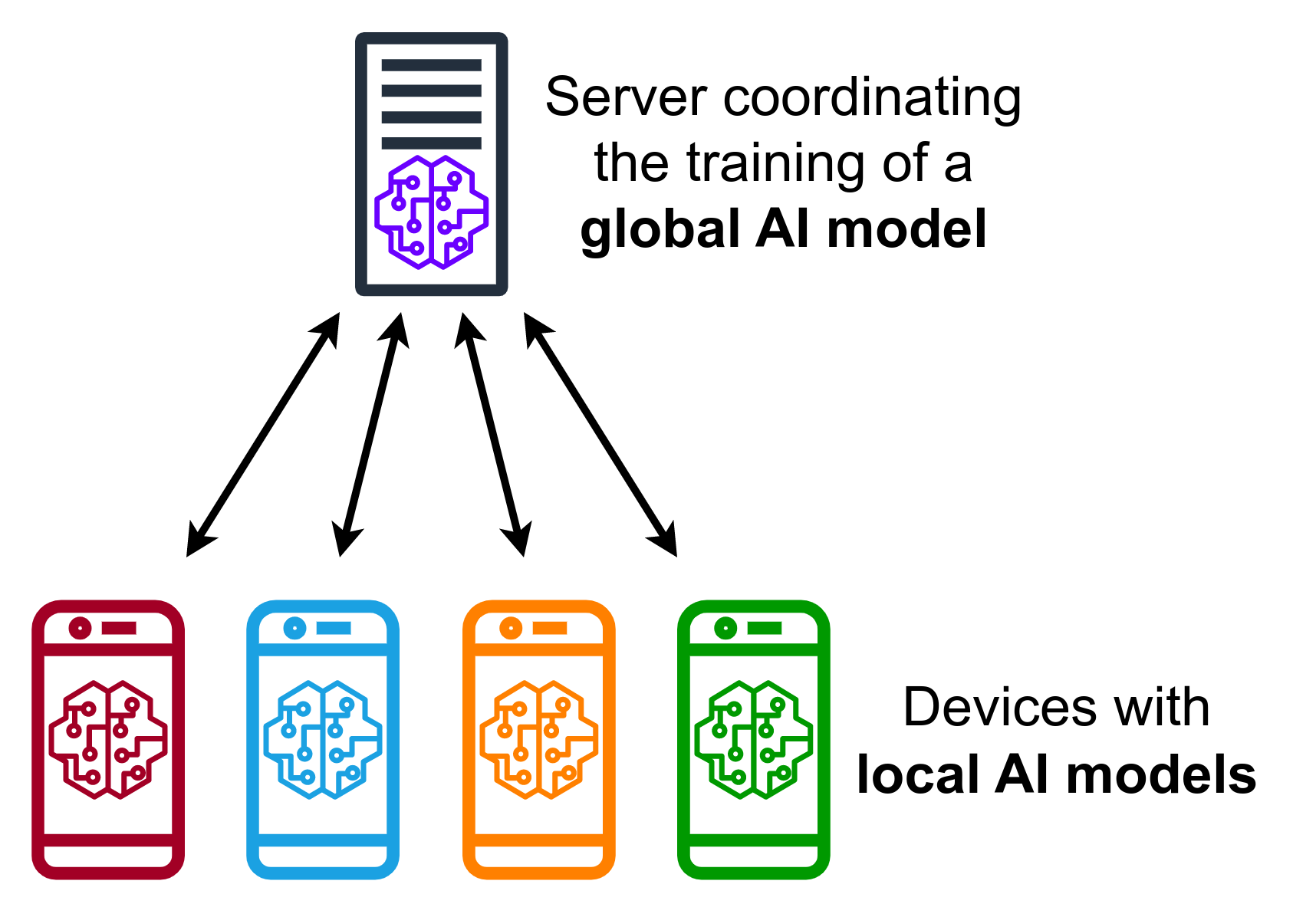
Federated Learning
Federated learning (also known as collaborative learning) is a machine learning technique in a setting where multiple entities (often called clients) collaboratively train a model while keeping their data Decentralized computing, decentralized, rather than centrally stored. A defining characteristic of federated learning is data Homogeneity and heterogeneity (statistics), heterogeneity. Because client data is decentralized, data samples held by each client may not be Independent and identically distributed random variables, independently and identically distributed. Federated learning is generally concerned with and motivated by issues such as Information Privacy, data privacy, data minimization, and data access rights. Its applications involve a variety of research areas including Arms industry, defence, telecommunications, the Internet of things, and Pharmaceutical industry, pharmaceuticals. Definition Federated learning aims at training a machine learning algorithm, for insta ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Model Collapse
Model collapse is a phenomenon where machine learning models gradually degrade due to errors coming from uncurated training on the outputs of another model, such as prior versions of itself. Such outputs are known as synthetic data. It is a possible mechanism for mode collapse. Shumailov et al. coined the term and described two specific stages to the degradation: ''early model collapse'' and ''late model collapse'': * In early model collapse, the model begins losing information about the tails of the distribution – mostly affecting minority data. Later work highlighted that early model collapse is hard to notice, since overall performance may appear to improve, while the model loses performance on minority data. * In late model collapse, the model loses a significant proportion of its performance, confusing concepts and losing most of its variance. Mechanism Using synthetic data as training data can lead to issues with the quality and reliability of the trained model. Model co ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Text-to-image Model
A text-to-image model is a machine learning model which takes an input natural language prompt and produces an image matching that description. Text-to-image models began to be developed in the mid-2010s during the beginnings of the AI boom, as a result of advances in deep neural networks. In 2022, the output of state-of-the-art text-to-image models—such as OpenAI's DALL-E 2, Google Brain's Imagen, Stability AI's Stable Diffusion, and Midjourney—began to be considered to approach the quality of real photographs and human-drawn art. Text-to-image models are generally latent diffusion models, which combine a language model, which transforms the input text into a latent representation, and a generative image model, which produces an image conditioned on that representation. The most effective models have generally been trained on massive amounts of image and text data scraped from the web. History Before the rise of deep learning, attempts to build text-to-image mo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Intrusion Detection System
An intrusion detection system (IDS) is a device or software application that monitors a network or systems for malicious activity or policy violations. Any intrusion activity or violation is typically either reported to an administrator or collected centrally using a security information and event management (SIEM) system. A SIEM system combines outputs from multiple sources and uses alarm filtering techniques to distinguish malicious activity from false alarms. IDS types range in scope from single computers to large networks. The most common classifications are network intrusion detection systems (NIDS) and host-based intrusion detection systems (HIDS). A system that monitors important operating system files is an example of an HIDS, while a system that analyzes incoming network traffic is an example of an NIDS. It is also possible to classify IDS by detection approach. The most well-known variants are signature-based detection (recognizing bad patterns, such as exploitatio ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
AI Training Data Poisoning Illustration (Nightshade)
AI most frequently refers to artificial intelligence, which is intelligence demonstrated by machines. Ai, AI or A.I. may also refer to: Animals * Ai (chimpanzee), an individual experimental subject in Japan * Ai (sloth) or the pale-throated sloth, a northern Amazonian mammal species Arts, entertainment and media Works * ''Ai'' (album), a 2004 release by Seraphim * "A.I." (song), by OneRepublic, 2016 * ''A.I. Artificial Intelligence'', a 2001 American film * '' A.I. Rising'', a 2018 Serbian film * '' AI: The Somnium Files'', a 2019 video game * ''American Idol'', a televised singing contest * ''The American Interest'', a bimonthly magazine (2005–2020) * ''I'' (2015 film), an Indian Tamil film (initial title: ''Ai'') Other uses in arts and media * A.i. (band), a Californian rock–electroclash group * All in (poker), wagering one's entire stake * Appreciation Index, a British measure of broadcast programme approval * Non-player character, in gaming (colloquially, ''an AI' ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Backdoor (computing)
A backdoor is a typically covert method of bypassing normal authentication or encryption in a computer, product, embedded device (e.g. a home router), or its embodiment (e.g. part of a cryptosystem, algorithm, chipset, or even a "homunculus computer"—a tiny computer-within-a-computer such as that found in Intel's AMT technology). Backdoors are most often used for securing remote access to a computer, or obtaining access to plaintext in cryptosystems. From there it may be used to gain access to privileged information like passwords, corrupt or delete data on hard drives, or transfer information within autoschediastic networks. In the United States, the 1994 Communications Assistance for Law Enforcement Act forces internet providers to provide backdoors for government authorities. In 2024, the U.S. government realized that China had been tapping communications in the U.S. using that infrastructure for months, or perhaps longer; China recorded presidential candidate campaign offi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Disinformation
Disinformation is misleading content deliberately spread to deceive people, or to secure economic or political gain and which may cause public harm. Disinformation is an orchestrated adversarial activity in which actors employ strategic deceptions and media manipulation tactics to advance political, military, or commercial goals. Disinformation is implemented through coordinated campaigns that "weaponize multiple rhetorical strategies and forms of knowing—including not only falsehoods but also truths, half-truths, and value judgements—to exploit and amplify culture wars and other identity-driven controversies." In contrast, ''misinformation'' refers to inaccuracies that stem from inadvertent error. Misinformation can be used to create disinformation when known misinformation is purposefully and intentionally disseminated. " Fake news" has sometimes been categorized as a type of disinformation, but scholars have advised not using these two terms interchangeably or us ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Viruses
A computer virus is a type of malware that, when executed, replicates itself by modifying other computer programs and inserting its own code into those programs. If this replication succeeds, the affected areas are then said to be "infected" with a computer virus, a metaphor derived from biological viruses. Computer viruses generally require a host program. The virus writes its own code into the host program. When the program runs, the written virus program is executed first, causing infection and damage. By contrast, a computer worm does not need a host program, as it is an independent program or code chunk. Therefore, it is not restricted by the host program, but can run independently and actively carry out attacks. Virus writers use social engineering deceptions and exploit detailed knowledge of security vulnerabilities to initially infect systems and to spread the virus. Viruses use complex anti-detection/stealth strategies to evade antivirus software. Motives for creati ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mobileye
Mobileye Global Inc. is a United States- domiciled, Israel-headquartered autonomous driving company. It is developing self-driving technologies and advanced driver-assistance systems (ADAS) including cameras, computer chips, and software. Mobileye was acquired by Intel in 2017 and went public again in 2022. History Mobileye was founded in 1999 by Hebrew University professor Amnon Shashua. He evolved his academic research into a vision system that could detect vehicles using a camera and software. It developed into a supplier of automotive safety technologies based on adding "intelligence" to inexpensive cameras for commercialization. Mobileye established its first research center in 2004. It launched the first generation EyeQ1 processor in 2008. The technology offered driver assistance including automatic emergency braking. One of the first vehicles to use this technology was the fifth-generation BMW 7 Series. Versions of the chip were released in 2010, 2014 and 2018. In ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Tesla, Inc
Tesla, Inc. ( or ) is an American multinational automotive and clean energy company. Headquartered in Austin, Texas, it designs, manufactures and sells battery electric vehicles (BEVs), stationary battery energy storage devices from home to grid-scale storage, grid-scale, solar panels and solar shingles, and related products and services. Tesla was incorporated in July 2003 by Martin Eberhard and Marc Tarpenning as Tesla Motors. Its name is a tribute to inventor and electrical engineer Nikola Tesla. In February 2004, Elon Musk led Tesla's first funding round and became the company's chairman; in 2008, he was named chief executive officer. In 2008, the company began production of its first car model, the Tesla Roadster (first generation), Roadster sports car, followed by the Tesla Model S, Model S sedan in 2012, the Tesla Model X, Model X SUV in 2015, the Tesla Model 3, Model 3 sedan in 2017, the Tesla Model Y, Model Y crossover in 2020, the Tesla Semi truck in 2022 and th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |