|
Cross-cutting Concern
In aspect-oriented software development, cross-cutting concerns are aspects of a program that affect several modules, without the possibility of being encapsulated in any of them. These concerns often cannot be cleanly decomposed from the rest of the system in both the design and implementation, and can result in either ''scattering'' (code duplication), ''tangling'' (significant dependencies between systems), or both. For instance, if writing an application software, application for handling Electronic health record, medical records, the indexing of such records is a core concern, while Data logging, logging a history of changes to the record database or user database, or an authentication system, would be cross-cutting concerns since they interact with more parts of the program. Background Cross-cutting concerns are parts of a program that rely on or must affect many other parts of the system. They form the basis for the development of aspect (computer science), aspects. Such ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Aspect-oriented Software Development
In computing, aspect-oriented programming (AOP) is a programming paradigm that aims to increase modularity by allowing the separation of cross-cutting concerns. It does so by adding behavior to existing code (an advice) ''without'' modifying the code itself, instead separately specifying which code is modified via a "pointcut" specification, such as "log all function calls when the function's name begins with 'set. This allows behaviors that are not central to the business logic (such as logging) to be added to a program without cluttering the code core to the functionality. AOP includes programming methods and tools that support the modularization of concerns at the level of the source code, while aspect-oriented software development refers to a whole engineering discipline. Aspect-oriented programming entails breaking down program logic into distinct parts (so-called ''concerns'', cohesive areas of functionality). Nearly all programming paradigms support some level of groupi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Aspect-oriented Programming
In computing, aspect-oriented programming (AOP) is a programming paradigm that aims to increase modularity by allowing the separation of cross-cutting concerns. It does so by adding behavior to existing code (an advice) ''without'' modifying the code itself, instead separately specifying which code is modified via a "pointcut" specification, such as "log all function calls when the function's name begins with 'set. This allows behaviors that are not central to the business logic (such as logging) to be added to a program without cluttering the code core to the functionality. AOP includes programming methods and tools that support the modularization of concerns at the level of the source code, while aspect-oriented software development refers to a whole engineering discipline. Aspect-oriented programming entails breaking down program logic into distinct parts (so-called ''concerns'', cohesive areas of functionality). Nearly all programming paradigms support some level of groupi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Log File
In computing, logging is the act of keeping a log of events that occur in a computer system, such as problems, errors or just information on current operations. These events may occur in the operating system or in other software. A message or log entry is recorded for each such event. These log messages can then be used to monitor and understand the operation of the system, to debug problems, or during an audit. Logging is particularly important in multi-user software, to have a central overview of the operation of the system. In the simplest case, messages are written to a file, called a log file. Alternatively, the messages may be written to a dedicated logging system or to a log management software, where it is stored in a database or on a different computer system. Specifically, a transaction log is a log of the communications between a system and the users of that system, or a data collection method that automatically captures the type, content, or time of transactions ma ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Information Security
Information security, sometimes shortened to InfoSec, is the practice of protecting information by mitigating information risks. It is part of information risk management. It typically involves preventing or reducing the probability of unauthorized/inappropriate access to data, or the unlawful use, disclosure, disruption, deletion, corruption, modification, inspection, recording, or devaluation of information. It also involves actions intended to reduce the adverse impacts of such incidents. Protected information may take any form, e.g. electronic or physical, tangible (e.g. paperwork) or intangible (e.g. knowledge). Information security's primary focus is the balanced protection of the confidentiality, integrity, and availability of data (also known as the CIA triad) while maintaining a focus on efficient policy implementation, all without hampering organization productivity. This is largely achieved through a structured risk management process that involves: * identifying inform ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
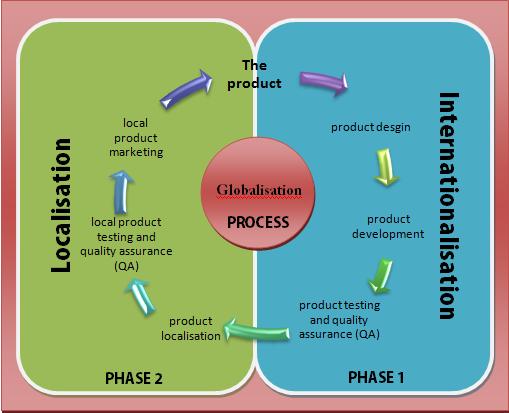
Language Localisation
Language localisation (or language localization) is the process of adapting a product's translation to a specific country or region. It is the second phase of a larger process of product translation and cultural adaptation (for specific countries, regions, cultures or groups) to account for differences in distinct markets, a process known as internationalization and localization, internationalisation and localisation. Language localisation differs from Translation, translation activity because it involves a comprehensive study of the target culture in order to correctly adapt the product to local needs. Localisation can be referred to by the numeronym L10N (as in: "L", followed by the number 10, and then "N"). The localisation process is most generally related to the cultural adaptation and translation of software localization, software, video game localization, video games, websites, and technical communication, as well as audio/voiceover, video, or other multimedia content, and ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Internationalization And Localization
In computing, internationalization and localization (American) or internationalisation and localisation (British English), often abbreviated i18n and L10n, are means of adapting computer software to different languages, regional peculiarities and technical requirements of a target locale. Internationalization is the process of designing a software application so that it can be adapted to various languages and regions without engineering changes. Localization is the process of adapting internationalized software for a specific region or language by translating text and adding locale-specific components. Localization (which is potentially performed multiple times, for different locales) uses the infrastructure or flexibility provided by internationalization (which is ideally performed only once before localization, or as an integral part of ongoing development). Naming The terms are frequently abbreviated to the numeronyms ''i18n'' (where ''18'' stands for the number of letters ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Error Detection And Correction
In information theory and coding theory with applications in computer science and telecommunication, error detection and correction (EDAC) or error control are techniques that enable reliable delivery of digital data over unreliable communication channels. Many communication channels are subject to channel noise, and thus errors may be introduced during transmission from the source to a receiver. Error detection techniques allow detecting such errors, while error correction enables reconstruction of the original data in many cases. Definitions ''Error detection'' is the detection of errors caused by noise or other impairments during transmission from the transmitter to the receiver. ''Error correction'' is the detection of errors and reconstruction of the original, error-free data. History In classical antiquity, copyists of the Hebrew Bible were paid for their work according to the number of stichs (lines of verse). As the prose books of the Bible were hardly ever ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Environment Variables
An environment variable is a dynamic-named value that can affect the way running processes will behave on a computer. They are part of the environment in which a process runs. For example, a running process can query the value of the TEMP environment variable to discover a suitable location to store temporary files, or the HOME or USERPROFILE variable to find the directory structure owned by the user running the process. They were introduced in their modern form in 1979 with Version 7 Unix, so are included in all Unix operating system flavors and variants from that point onward including Linux and macOS. From PC DOS 2.0 in 1982, all succeeding Microsoft operating systems, including Microsoft Windows, and OS/2 also have included them as a feature, although with somewhat different syntax, usage and standard variable names. Design In all Unix and Unix-like systems, as well as on Windows, each process has its own separate set of environment variables. By default, when a p ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Optimization (computer Science)
In computer science, program optimization, code optimization, or software optimization, is the process of modifying a software system to make some aspect of it work more efficiently or use fewer resources. In general, a computer program may be optimized so that it executes more rapidly, or to make it capable of operating with less memory storage or other resources, or draw less power. General Although the word "optimization" shares the same root as "optimal", it is rare for the process of optimization to produce a truly optimal system. A system can generally be made optimal not in absolute terms, but only with respect to a given quality metric, which may be in contrast with other possible metrics. As a result, the optimized system will typically only be optimal in one application or for one audience. One might reduce the amount of time that a program takes to perform some task at the price of making it consume more memory. In an application where memory space is at a premium, on ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data Validation
In computer science, data validation is the process of ensuring data has undergone data cleansing to ensure they have data quality, that is, that they are both correct and useful. It uses routines, often called "validation rules", "validation constraints", or "check routines", that check for correctness, meaningfulness, and security of data that are input to the system. The rules may be implemented through the automated facilities of a data dictionary, or by the inclusion of explicit application program validation logic of the computer and its application. This is distinct from formal verification, which attempts to prove or disprove the correctness of algorithms for implementing a specification or property. Overview Data validation is intended to provide certain well-defined guarantees for fitness and consistency of data in an application or automated system. Data validation rules can be defined and designed using various methodologies, and be deployed in various contexts. Thei ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Code Mobility
In distributed computing, code mobility is the ability for running programs, code or objects to be migrated (or moved) from one machine or application to another. This is the process of moving mobile code across the nodes of a network as opposed to distributed computation where the ''data'' is moved. It is common practice in distributed systems to require the movement of code or processes between parts of the system, instead of data. Examples of code mobility include scripts downloaded over a network (for example JavaScript, VBScript), Java applets, ActiveX controls, Flash animations, Shockwave movies (and Xtras), and macros embedded within Microsoft Office documents. Overview The purpose of code mobility is to support sophisticated operations. For example, an application can send an object to another machine, and the object can resume executing inside the application on the remote machine with the same state as it had in the originating application. According to a classificat ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cache (computing)
In computing, a cache ( ) is a hardware or software component that stores data so that future requests for that data can be served faster; the data stored in a cache might be the result of an earlier computation or a copy of data stored elsewhere. A ''cache hit'' occurs when the requested data can be found in a cache, while a ''cache miss'' occurs when it cannot. Cache hits are served by reading data from the cache, which is faster than recomputing a result or reading from a slower data store; thus, the more requests that can be served from the cache, the faster the system performs. To be cost-effective and to enable efficient use of data, caches must be relatively small. Nevertheless, caches have proven themselves in many areas of computing, because typical computer applications access data with a high degree of locality of reference. Such access patterns exhibit temporal locality, where data is requested that has been recently requested already, and spatial locality, where d ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |