|
Correlation Attack
In cryptography, correlation attacks are a class of known-plaintext attacks for breaking stream ciphers whose keystream is generated by combining the output of several linear-feedback shift registers (LFSRs) using a Boolean function. Correlation attacks exploit a statistical weakness arising from certain choices of the Boolean function. The cipher is not inherently insecure if there is a choice of the Boolean function that avoids this weakness. Explanation Correlation attacks are possible when there is a significant correlation between the output state of an individual LFSR in the keystream generator and the output of the Boolean function that combines the output state of all of the LFSRs. In combination with partial knowledge of the keystream, which is derived from partial knowledge of the plaintext, the two are simply compared using an XOR logic gate. This allows an attacker to brute-force the key for the individual LFSR and the rest of the system separately. For instance, i ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptography
Cryptography, or cryptology (from grc, , translit=kryptós "hidden, secret"; and ''graphein'', "to write", or ''-logia'', "study", respectively), is the practice and study of techniques for secure communication in the presence of adversarial behavior. More generally, cryptography is about constructing and analyzing protocols that prevent third parties or the public from reading private messages. Modern cryptography exists at the intersection of the disciplines of mathematics, computer science, information security, electrical engineering, digital signal processing, physics, and others. Core concepts related to information security (data confidentiality, data integrity, authentication, and non-repudiation) are also central to cryptography. Practical applications of cryptography include electronic commerce, chip-based payment cards, digital currencies, computer passwords, and military communications. Cryptography prior to the modern age was effectively synony ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Kerckhoffs' Principle
Kerckhoffs's principle (also called Kerckhoffs's desideratum, assumption, axiom, doctrine or law) of cryptography was stated by Dutch-born cryptographer Auguste Kerckhoffs in the 19th century. The principle holds that a cryptosystem should be secure, even if everything about the system, except the key, is public knowledge. This concept is widely embraced by cryptographers, in contrast to security through obscurity, which is not. Kerckhoffs's principle was phrased by American mathematician Claude Shannon as "the enemy knows the system", i.e., "one ought to design systems under the assumption that the enemy will immediately gain full familiarity with them". In that form, it is called Shannon's maxim. Another formulation by American researcher and professor Steven M. Bellovin is: In other words — design your system assuming that your opponents know it in detail. (A former official at NSA's National Computer Security Center told me that the standard assumption there was that se ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Bruce Schneier
Bruce Schneier (; born January 15, 1963) is an American cryptographer, computer security professional, privacy specialist, and writer. Schneier is a Lecturer in Public Policy at the Harvard Kennedy School and a Fellow at the Berkman Klein Center for Internet & Society as of November, 2013. He is a board member of the Electronic Frontier Foundation, Access Now, and The Tor Project; and an advisory board member of Electronic Privacy Information Center and VerifiedVoting.org. He is the author of several books on general security topics, computer security and cryptography and is a squid enthusiast. In 2015, Schneier received the EPIC Lifetime Achievement Award from Electronic Privacy Information Center. Early life Bruce Schneier is the son of Martin Schneier, a Brooklyn Supreme Court judge. He grew up in the Flatbush neighborhood of Brooklyn, New York, attending P.S. 139 and Hunter College High School. After receiving a physics bachelor's degree from the University of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Topics In Cryptography
The following outline is provided as an overview of and topical guide to cryptography: Cryptography (or cryptology) – practice and study of hiding information. Modern cryptography intersects the disciplines of mathematics, computer science, and engineering. Applications of cryptography include ATM cards, computer passwords, and electronic commerce. Essence of cryptography * Cryptographer * Encryption/decryption * Cryptographic key * Cipher * Ciphertext * Plaintext * Code * Tabula recta * Alice and Bob Uses of cryptographic techniques * Commitment schemes * Secure multiparty computation * Electronic voting * Authentication * Digital signatures * Crypto systems * Dining cryptographers problem * Anonymous remailer * Pseudonymity * Onion routing * Digital currency * Secret sharing * Indistinguishability obfuscation Branches of cryptography * Multivariate cryptography * Post-quantum cryptography * Quantum cryptography * Steganography * Visual cryptograph ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
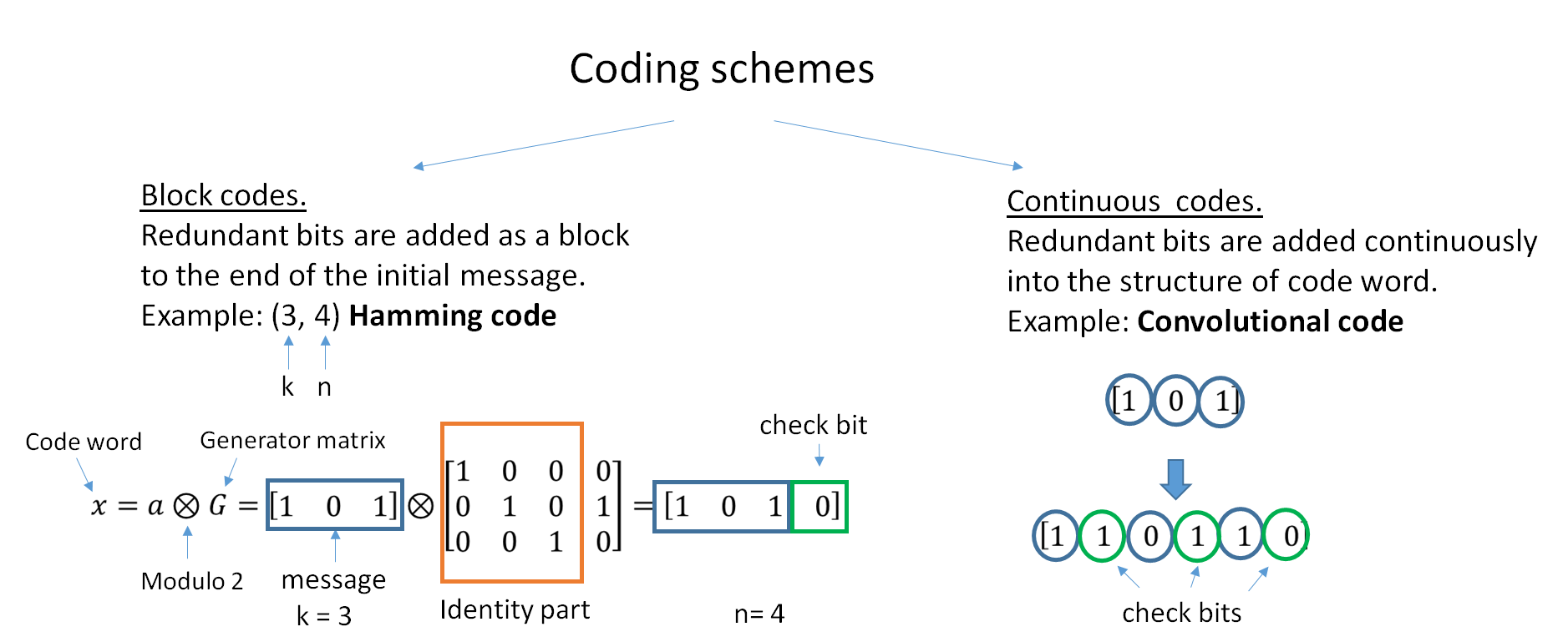
Error Correcting Code
In computing, telecommunication, information theory, and coding theory, an error correction code, sometimes error correcting code, (ECC) is used for controlling errors in data over unreliable or noisy communication channels. The central idea is the sender encodes the message with redundant information in the form of an ECC. The redundancy allows the receiver to detect a limited number of errors that may occur anywhere in the message, and often to correct these errors without retransmission. The American mathematician Richard Hamming pioneered this field in the 1940s and invented the first error-correcting code in 1950: the Hamming (7,4) code. ECC contrasts with error detection in that errors that are encountered can be corrected, not simply detected. The advantage is that a system using ECC does not require a reverse channel to request retransmission of data when an error occurs. The downside is that there is a fixed overhead that is added to the message, thereby requiring a hi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Balanced Boolean Function
In mathematics and computer science, a balanced boolean function is a boolean function whose output yields as many 0s as 1s over its input set. This means that for a uniformly random input string of bits, the probability of getting a 1 is 1/2. Examples of balanced boolean functions are the function that copies the first bit of its input to the output, and the function that produces the exclusive or of the input bits. Usage Balanced boolean functions are primarily used in cryptography. If a function is not balanced, it will have a statistical bias, making it subject to cryptanalysis such as the correlation attack. See also * Bent function In the mathematics, mathematical field of combinatorics, a bent function is a special type of Boolean function which is maximally non-linear; it is as different as possible from the set of all linear map, linear and affine functions when measure ... References Balanced boolean functions that can be evaluated so that every input bit i ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Correlation Immunity
In mathematics, the correlation immunity of a Boolean function is a measure of the degree to which its outputs are uncorrelated with some subset of its inputs. Specifically, a Boolean function is said to be correlation-immune ''of order m'' if every subset of ''m'' or fewer variables in x_1,x_2,\ldots,x_n is statistically independent of the value of f(x_1,x_2,\ldots,x_n). Definition A function f:\mathbb_2^n\rightarrow\mathbb_2 is k-th order correlation immune if for any independent n binary random variables X_0\ldots X_, the random variable Z=f(X_0,\ldots,X_) is independent from any random vector (X_\ldots X_) with 0\leq i_1<\ldots Results in cryptography When used in a as a combining function for |
Binomial Distribution
In probability theory and statistics, the binomial distribution with parameters ''n'' and ''p'' is the discrete probability distribution of the number of successes in a sequence of ''n'' independent experiments, each asking a yes–no question, and each with its own Boolean-valued outcome: ''success'' (with probability ''p'') or ''failure'' (with probability q=1-p). A single success/failure experiment is also called a Bernoulli trial or Bernoulli experiment, and a sequence of outcomes is called a Bernoulli process; for a single trial, i.e., ''n'' = 1, the binomial distribution is a Bernoulli distribution. The binomial distribution is the basis for the popular binomial test of statistical significance. The binomial distribution is frequently used to model the number of successes in a sample of size ''n'' drawn with replacement from a population of size ''N''. If the sampling is carried out without replacement, the draws are not independent and so the resultin ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Brute-force Search
In computer science, brute-force search or exhaustive search, also known as generate and test, is a very general problem-solving technique and algorithmic paradigm that consists of systematically enumerating all possible candidates for the solution and checking whether each candidate satisfies the problem's statement. A brute-force algorithm that finds the divisors of a natural number ''n'' would enumerate all integers from 1 to n, and check whether each of them divides ''n'' without remainder. A brute-force approach for the eight queens puzzle would examine all possible arrangements of 8 pieces on the 64-square chessboard and for each arrangement, check whether each (queen) piece can attack any other. While a brute-force search is simple to implement and will always find a solution if it exists, implementation costs are proportional to the number of candidate solutionswhich in many practical problems tends to grow very quickly as the size of the problem increases ( §Combinator ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Known-plaintext Attack
The known-plaintext attack (KPA) is an attack model for cryptanalysis where the attacker has access to both the plaintext (called a crib), and its encrypted version ( ciphertext). These can be used to reveal further secret information such as secret keys and code books. The term "crib" originated at Bletchley Park, the British World War II decryption operation, where it was defined as: History The usage "crib" was adapted from a slang term referring to cheating (e.g., "I cribbed my answer from your test paper"). A "crib" originally was a literal or interlinear translation of a foreign-language text—usually a Latin or Greek text—that students might be assigned to translate from the original language. The idea behind a crib is that cryptologists were looking at incomprehensible ciphertext, but if they had a clue about some word or phrase that might be expected to be in the ciphertext, they would have a "wedge," a test to break into it. If their otherwise random attacks on ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Divide-and-conquer Algorithm
In computer science, divide and conquer is an algorithm design paradigm. A divide-and-conquer algorithm recursively breaks down a problem into two or more sub-problems of the same or related type, until these become simple enough to be solved directly. The solutions to the sub-problems are then combined to give a solution to the original problem. The divide-and-conquer technique is the basis of efficient algorithms for many problems, such as sorting (e.g., quicksort, merge sort), multiplying large numbers (e.g., the Karatsuba algorithm), finding the closest pair of points, syntactic analysis (e.g., top-down parsers), and computing the discrete Fourier transform ( FFT). Designing efficient divide-and-conquer algorithms can be difficult. As in mathematical induction, it is often necessary to generalize the problem to make it amenable to a recursive solution. The correctness of a divide-and-conquer algorithm is usually proved by mathematical induction, and its computational cos ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Brute-force Attack
In cryptography, a brute-force attack consists of an attacker submitting many passwords or passphrases with the hope of eventually guessing correctly. The attacker systematically checks all possible passwords and passphrases until the correct one is found. Alternatively, the attacker can attempt to guess the key which is typically created from the password using a key derivation function. This is known as an exhaustive key search. A brute-force attack is a cryptanalytic attack that can, in theory, be used to attempt to decrypt any encrypted data (except for data encrypted in an information-theoretically secure manner). Such an attack might be used when it is not possible to take advantage of other weaknesses in an encryption system (if any exist) that would make the task easier. When password-guessing, this method is very fast when used to check all short passwords, but for longer passwords other methods such as the dictionary attack are used because a brute-force search ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |