|
Command–query Separation
Command-query separation (CQS) is a principle of imperative computer programming. It was devised by Bertrand Meyer as part of his pioneering work on the Eiffel programming language. It states that every method should either be a ''command'' that performs an action, or a ''query'' that returns data to the caller, but not both. In other words, ''asking a question should not change the answer''. More formally, methods should return a value only if they are referentially transparent and hence possess no side effects. Connection with design by contract Command-query separation is particularly well suited to a design by contract (DbC) methodology, in which the design of a program is expressed as assertions embedded in the source code, describing the state of the program at certain critical times. In DbC, assertions are considered design annotations—not program logic—and as such, their execution should not affect the program state. CQS is beneficial to DbC because any value-retu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Imperative Programming
In computer science, imperative programming is a programming paradigm of software that uses Statement (computer science), statements that change a program's state (computer science), state. In much the same way that the imperative mood in natural languages expresses commands, an imperative program consists of command (computing), commands for the computer to perform. Imperative programming focuses on describing ''how'' a program operates step by step (with general order of the steps being determined in source code by the placement of statements one below the other), rather than on high-level descriptions of its expected results. The term is often used in contrast to declarative programming, which focuses on ''what'' the program should accomplish without specifying all the details of ''how'' the program should achieve the result. Procedural programming Procedural programming is a type of imperative programming in which the program is built from one or more procedures (also termed s ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Command Query Responsibility Segregation
In information technology, Command Query Responsibility Segregation (CQRS) is a system architecture A system architecture is the conceptual model that defines the structure, behavior, and views of a system. An architecture description is a formal description and representation of a system, organized in a way that supports reasoning about the s ... that extends the idea behind command–query separation (CQS) to the level of services. Such a system will have separate interfaces to send queries and to send commands. As in CQS, fulfilling a query request will only retrieve data and will not modify the state of the system (with some exceptions like logging access), while fulfilling a command request will modify the state of the system. Many systems push the segregation to the data models used by the system. The models used to process queries are usually called ''read models'' and the models used to process commands ''write models''. Although its origin is usually attributed to Gr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Create, Read, Update And Delete
In computer programming, create, read, update, and delete (CRUD) are the four basic operations (actions) of persistent storage. CRUD is also sometimes used to describe user interface conventions that facilitate viewing, searching, and changing information using computer-based forms and reports. History The term ''C.R.U.D'' was likely first popularized in 1983 by James Martin in his book ''Managing the data-base environment''. Conceptual Data can be put in a ''location/area'' of a storage mechanism. * The fundamental feature of a storage location is that its ''content'' is both ''readable'' and ''updatable''. * Before a storage location can be read or updated it needs to be ''created''; that is allocated and initialized with content. * At some later point, the storage location may need to be ''destructed''; that is finalized and deallocated. Together these four operations make up the basic operations of storage management known as CRUD: ''Create'', ''Read'', ''Update'' and ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Domain-driven Design
Domain-driven design (DDD) is a major software design approach, focusing on modeling software to match a domain according to input from that domain's experts. DDD is against the idea of having a single unified model; instead it divides a large system into bounded contexts, each of which have their own model. Under domain-driven design, the structure and language of software code (class names, class methods, class variables) should match the business domain. For example: if software processes loan applications, it might have classes like "loan application", "customers", and methods such as "accept offer" and "withdraw". Domain-driven design is predicated on the following goals: * placing the project's primary focus on the core domain and domain logic layer; * basing complex designs on a model of the domain; * initiating a creative collaboration between technical and domain experts to iteratively refine a conceptual model that addresses particular domain problems. Critics o ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Idempotence
Idempotence (, ) is the property of certain operations in mathematics and computer science whereby they can be applied multiple times without changing the result beyond the initial application. The concept of idempotence arises in a number of places in abstract algebra (in particular, in the theory of projectors and closure operators) and functional programming (in which it is connected to the property of referential transparency). The term was introduced by American mathematician Benjamin Peirce in 1870 in the context of elements of algebras that remain invariant when raised to a positive integer power, and literally means "(the quality of having) the same power", from + '' potence'' (same + power). Definition An element x of a set S equipped with a binary operator \cdot is said to be ''idempotent'' under \cdot if : . The ''binary operation'' \cdot is said to be ''idempotent'' if : . Examples * In the monoid (\mathbb, \times) of the natural numbers with multiplication, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
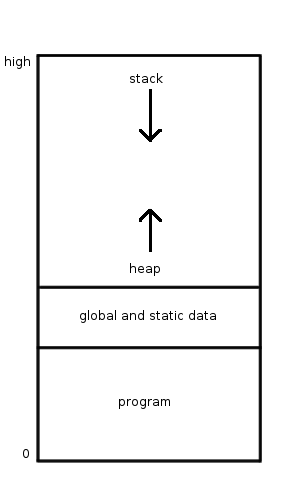
Stack (abstract Data Type)
In computer science, a stack is an abstract data type that serves as a collection (abstract data type), collection of elements with two main operations: * Push, which adds an element to the collection, and * Pop, which removes the most recently added element. Additionally, a peek (data type operation), peek operation can, without modifying the stack, return the value of the last element added. The name ''stack'' is an analogy to a set of physical items stacked one atop another, such as a stack of plates. The order in which an element added to or removed from a stack is described as last in, first out, referred to by the acronym LIFO. As with a stack of physical objects, this structure makes it easy to take an item off the top of the stack, but accessing a Data, datum deeper in the stack may require removing multiple other items first. Considered a sequential collection, a stack has one end which is the only position at which the push and pop operations may occur, the ''top'' ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Martin Fowler (software Engineer)
Martin Fowler (18 December 1963) is a British software developer, author and international public speaker on software development, specialising in object-oriented analysis and design, UML, patterns, and agile software development methodologies, including extreme programming. His 1999 book ''Refactoring'' popularised the practice of code refactoring. In 2004 he introduced a new architectural pattern, called Presentation Model (PM). Biography Fowler was born and grew up in Walsall, England, where he went to Queen Mary's Grammar School for his secondary education. He graduated at University College London in 1986. In 1994, he moved to the United States, where he lives near Boston, Massachusetts in the suburb of Melrose.Martin Fowler at martinfowler.com. Retrieved 2012-11-15. Fowler started working with software in the early 1980s. Out of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Multithreading (software)
In computer science, a thread of execution is the smallest sequence of programmed instructions that can be managed independently by a scheduler, which is typically a part of the operating system. In many cases, a thread is a component of a process. The multiple threads of a given process may be executed concurrently (via multithreading capabilities), sharing resources such as memory, while different processes do not share these resources. In particular, the threads of a process share its executable code and the values of its dynamically allocated variables and non- thread-local global variables at any given time. The implementation of threads and processes differs between operating systems. History Threads made an early appearance under the name of "tasks" in IBM's batch processing operating system, OS/360, in 1967. It provided users with three available configurations of the OS/360 control system, of which Multiprogramming with a Variable Number of Tasks (MVT) was ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Reentrant (subroutine)
Reentrancy is a programming concept where a function or subroutine can be interrupted and then resumed before it finishes executing. This means that the function can be called again before it completes its previous execution. Reentrant code is designed to be safe and predictable when multiple instances of the same function are called simultaneously or in quick succession. A computer program or subroutine is called reentrant if multiple invocations can safely run Concurrent computing, concurrently on Multiprocessing, multiple processors, or if on a Uniprocessor system, single-processor system its Execution (computing), execution can be interrupted and a new execution of it can be safely started (it can be "re-entered"). The interruption could be caused by an internal action such as a Branch (computer science), jump or call (which might be a Recursion (computer science), recursive call; reentering a function is a generalization of recursion), or by an external action such as an inter ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Domain-driven Design
Domain-driven design (DDD) is a major software design approach, focusing on modeling software to match a domain according to input from that domain's experts. DDD is against the idea of having a single unified model; instead it divides a large system into bounded contexts, each of which have their own model. Under domain-driven design, the structure and language of software code (class names, class methods, class variables) should match the business domain. For example: if software processes loan applications, it might have classes like "loan application", "customers", and methods such as "accept offer" and "withdraw". Domain-driven design is predicated on the following goals: * placing the project's primary focus on the core domain and domain logic layer; * basing complex designs on a model of the domain; * initiating a creative collaboration between technical and domain experts to iteratively refine a conceptual model that addresses particular domain problems. Critics o ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Event Driven Architecture
Event-driven architecture (EDA) is a software architecture paradigm concerning the production and detection of events. Event-driven architectures are evolutionary in nature and provide a high degree of fault tolerance, performance, and scalability. However, they are complex and inherently challenging to test. EDAs are good for complex and dynamic workloads. Overview An ''even'' can be defined as "a significant change in state". For example, when a consumer purchases a car, the car's state changes from "for sale" to "sold". A car dealer's system architecture may treat this state change as an event whose occurrence can be made known to other applications within the architecture. From a formal perspective, what is produced, published, propagated, detected or consumed is a (typically asynchronous) message called the event notification, and not the event itself, which is the state change that triggered the message emission. Events do not travel, they just occur. However, the term ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
CRUD
In computer programming, create, read, update, and delete (CRUD) are the four basic operations (actions) of persistent storage. CRUD is also sometimes used to describe user interface conventions that facilitate viewing, searching, and changing information using computer-based forms and reports. History The term ''C.R.U.D'' was likely first popularized in 1983 by James Martin in his book ''Managing the data-base environment''. Conceptual Data can be put in a ''location/area'' of a storage mechanism. * The fundamental feature of a storage location is that its ''content'' is both ''readable'' and ''updatable''. * Before a storage location can be read or updated it needs to be ''created''; that is allocated and initialized with content. * At some later point, the storage location may need to be ''destructed''; that is finalized and deallocated. Together these four operations make up the basic operations of storage management known as CRUD: ''Create'', ''Read'', ''Update'' and ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |