|
Authorization Server
Authorization or authorisation (see spelling differences) is the function of specifying access rights/privileges to resources, which is related to general information security and computer security, and to access control in particular. More formally, "to authorize" is to define an access policy. For example, human resources staff are normally authorized to access employee records and this policy is often formalized as access control rules in a computer system. During operation, the system uses the access control rules to decide whether access requests from (authenticated) consumers shall be approved (granted) or disapproved (rejected). Resources include individual files or an item's data, computer programs, computer devices and functionality provided by computer applications. Examples of consumers are computer users, computer software and other hardware on the computer. Overview Access control in computer systems and networks rely on access policies. The access control proce ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
American And British English Spelling Differences
Despite the various List of dialects of English, English dialects spoken from country to country and within different regions of the same country, there are only slight regional variations in English orthography, the two most notable variations being British and American spelling. Many of Comparison of American and British English, the differences between American English, American and British English date back to a time before spelling standards were developed. For instance, some spellings seen as "American" today were once commonly used in Britain, and some spellings seen as "British" were once commonly used in the United States. A "British standard" began to emerge following the 1755 publication of Samuel Johnson's ''A Dictionary of the English Language'', and an "American standard" started following the work of Noah Webster and, in particular, his ''Webster's Dictionary, An American Dictionary of the English Language'', first published in 1828. Webster's efforts at spellin ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Access Control List
In computer security, an access-control list (ACL) is a list of permissions associated with a system resource (object). An ACL specifies which users or system processes are granted access to objects, as well as what operations are allowed on given objects. Each entry in a typical ACL specifies a subject and an operation. For instance, if a file object has an ACL that contains , this would give Alice permission to read and write the file and give Bob permission only to read it. Implementations Many kinds of operating systems implement ACLs or have a historical implementation; the first implementation of ACLs was in the filesystem of Multics in 1965. Filesystem ACLs A filesystem ACL is a data structure (usually a table) containing entries that specify individual user or group rights to specific system objects such as programs, processes, or files. These entries are known as access-control entries (ACEs) in the Microsoft Windows NT, OpenVMS, and Unix-like operating systems s ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
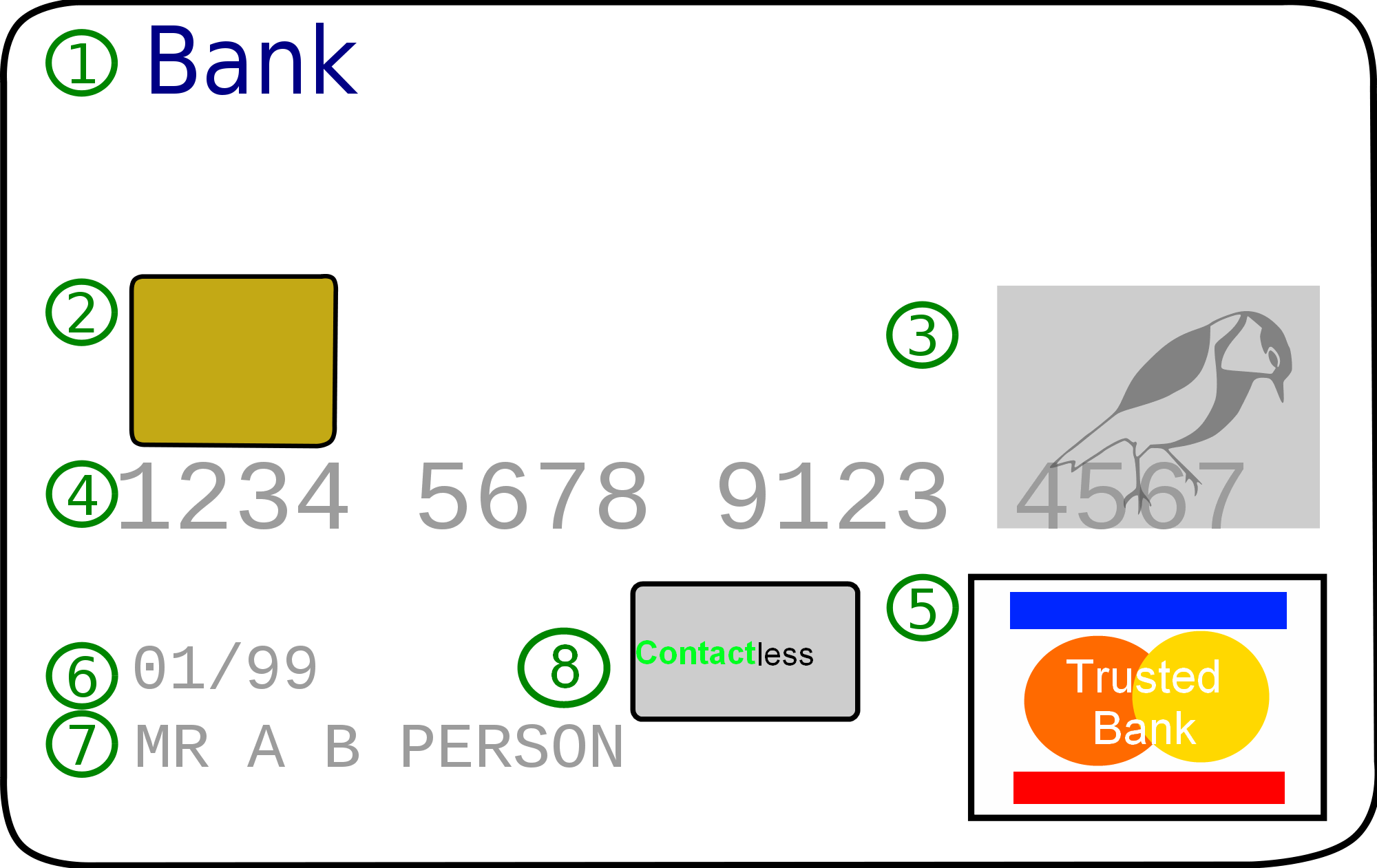
Credit Card
A credit card is a payment card issued to users (cardholders) to enable the cardholder to pay a merchant for goods and services based on the cardholder's accrued debt (i.e., promise to the card issuer to pay them for the amounts plus the other agreed charges). The card issuer (usually a bank or credit union) creates a revolving account and grants a line of credit to the cardholder, from which the cardholder can borrow money for payment to a merchant or as a cash advance. There are two credit card groups: consumer credit cards and business credit cards. Most cards are plastic, but some are metal cards (stainless steel, gold, palladium, titanium), and a few gemstone-encrusted metal cards. A regular credit card is different from a charge card, which requires the balance to be repaid in full each month or at the end of each statement cycle. In contrast, credit cards allow the consumers to build a continuing balance of debt, subject to interest being charged. A credit car ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Debit Card
A debit card, also known as a check card or bank card is a payment card that can be used in place of cash to make purchases. The term '' plastic card'' includes the above and as an identity document. These are similar to a credit card, but unlike a credit card, the money for the purchase must be in the cardholder's bank account at the time of a purchase and is immediately transferred directly from that account to the merchant's account to pay for the purchase. Some debit cards carry a stored value with which a payment is made (prepaid card), but most relay a message to the cardholder's bank to withdraw funds from the cardholder's designated bank account. In some cases, the payment card number is assigned exclusively for use on the Internet and there is no physical card. This is referred to as a virtual card. In many countries, the use of debit cards has become so widespread they have overtaken checks in volume, or have entirely replaced them; in some instances, debit cards ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Authorization Hold
Authorization hold (also card authorization, preauthorization, or preauth) is a service offered by credit and debit card providers whereby the provider puts a hold of the amount approved by the cardholder, reducing the balance of available funds until the merchant clears the transaction (also called settlement), after the transaction is completed or aborted, or because the hold expires. In the case of debit cards, authorization holds can fall off the account, thus rendering the balance available again, anywhere from one to eight business days after the transaction date, depending on the bank's policy. In the case of credit cards, holds may last as long as thirty days, depending on the issuing bank. Transactions may be withdrawn but in most cases, especially with smaller banks, will not show up as a deposit on your statement but will instead be directly added to your available balance automatically due to it only being a “temporary charge”. The usual reason for authorization hold ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Banking
A bank is a financial institution that accepts deposits from the public and creates a demand deposit while simultaneously making loans. Lending activities can be directly performed by the bank or indirectly through capital markets. Because banks play an important role in financial stability and the economy of a country, most jurisdictions exercise a high degree of regulation over banks. Most countries have institutionalized a system known as fractional reserve banking, under which banks hold liquid assets equal to only a portion of their current liabilities. In addition to other regulations intended to ensure liquidity, banks are generally subject to minimum capital requirements based on an international set of capital standards, the Basel Accords. Banking in its modern sense evolved in the fourteenth century in the prosperous cities of Renaissance Italy but in many ways functioned as a continuation of ideas and concepts of credit and lending that had their roots in the a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Security
Security is protection from, or resilience against, potential harm (or other unwanted coercive change) caused by others, by restraining the freedom of others to act. Beneficiaries (technically referents) of security may be of persons and social groups, objects and institutions, ecosystems or any other entity or phenomenon vulnerable to unwanted change. Security mostly refers to protection from hostile forces, but it has a wide range of other senses: for example, as the absence of harm (e.g. freedom from want); as the presence of an essential good (e.g. food security); as resilience against potential damage or harm (e.g. secure foundations); as secrecy (e.g. a secure telephone line); as containment (e.g. a secure room or cell); and as a state of mind (e.g. emotional security). The term is also used to refer to acts and systems whose purpose may be to provide security (security companies, security forces, security guard, cyber security systems, security cameras, remote guard ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Policy
Policy is a deliberate system of guidelines to guide decisions and achieve rational outcomes. A policy is a statement of intent and is implemented as a procedure or protocol. Policies are generally adopted by a governance body within an organization. Policies can assist in both ''subjective'' and ''objective'' decision making. Policies used in subjective decision-making usually assist senior management with decisions that must be based on the relative merits of a number of factors, and as a result, are often hard to test objectively, e.g. work–life balance policy... Moreover, Governments and other institutions have policies in the form of laws, regulations, procedures, administrative actions, incentives and voluntary practices. Frequently, resource allocations mirror policy decisions. Policy is a blueprint of the organizational activities which are repetitive/routine in nature. In contrast, policies to assist in objective decision-making are usually operational in nature an ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Trusted Third Party
In cryptography, a trusted third party (TTP) is an entity which facilitates interactions between two parties who both trust the third party; the Third Party reviews all critical transaction communications between the parties, based on the ease of creating fraudulent digital content. In TTP models, the relying parties use this trust to secure their own interactions. TTPs are common in any number of commercial transactions and in cryptographic digital transactions as well as cryptographic protocols, for example, a certificate authority (CA) would issue a digital certificate to one of the two parties in the next example. The CA then becomes the Trusted-Third-Party to that certificates issuance. Likewise transactions that need a third party recordation would also need a third-party repository service of some kind or another. 'Trusted' means that a system needs to be trusted to act in your interests, but it has the option (either at will or involuntarily) to act against your interests. ' ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Access Token
In computer systems, an access token contains the security credentials for a login session and identifies the user, the user's groups, the user's privileges, and, in some cases, a particular application. In some instances, one may be asked to enter an access token (e.g. 40 random characters) rather than the usual password (it therefore should be kept secret just like a password). Overview An ''access token'' is an object encapsulating the security identity of a process or thread. A token is used to make security decisions and to store tamper-proof information about some system entity. While a token is generally used to represent only security information, it is capable of holding additional free-form data that can be attached while the token is being created. Tokens can be duplicated without special privilege, for example to create a new token with lower levels of access rights to restrict the access of a launched application. An access token is used by Windows when a process or t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
.jpg)

