|
AnoNet
anoNet is a decentralized friend-to-friend network built using VPNs and software BGP routers. anoNet works by making it difficult to learn the identities of others on the network allowing them to anonymously host IPv4 and IPv6 services. Motivation Implementing an anonymous network on a service by service basis has its drawbacks, and it is debatable if such work should be built at the application level. A simpler approach could be to design an IPv4/IPv6 network where its participants enjoyed strong anonymity. Doing so allows the use of any number of applications and services already written and available on the internet at large. IPv4 networks do not preclude anonymity by design; it is only necessary to decouple the identity of the owner of an IP address from the address itself. Commercial internet connectivity and its need of billing records makes this impossible, but private IPv4 networks do not share that requirement. Assuming that a router administrator on such a metane ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Darknet
A dark net or darknet is an overlay network within the Internet that can only be accessed with specific software, configurations, or authorization, and often uses a unique customized communication protocol. Two typical darknet types are social networks (usually used for file hosting with a peer-to-peer connection), and anonymity proxy networks such as Tor via an anonymized series of connections. The term "darknet" was popularized by major news outlets to associate with Tor Onion services, when the infamous drug bazaar Silk Road used it, despite the terminology being unofficial. Technology such as Tor, I2P, and Freenet was intended to defend digital rights by providing security, anonymity, or censorship resistance and is used for both illegal and legitimate reasons. Anonymous communication between whistle-blowers, activists, journalists and news organisations is also facilitated by darknets through use of applications such as SecureDrop. Terminology The term originally descri ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
DarkNET Conglomeration
A dark net or darknet is an overlay network within the Internet that can only be accessed with specific software, configurations, or authorization, and often uses a unique customized communication protocol. Two typical darknet types are social networks (usually used for file hosting with a peer-to-peer connection), and anonymity proxy networks such as Tor via an anonymized series of connections. The term "darknet" was popularized by major news outlets to associate with Tor Onion services, when the infamous drug bazaar Silk Road used it, despite the terminology being unofficial. Technology such as Tor, I2P, and Freenet was intended to defend digital rights by providing security, anonymity, or censorship resistance and is used for both illegal and legitimate reasons. Anonymous communication between whistle-blowers, activists, journalists and news organisations is also facilitated by darknets through use of applications such as SecureDrop. Terminology The term originally describe ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Anonymous P2P
An anonymous P2P communication system is a peer-to-peer distributed application in which the nodes, which are used to share resources, or participants are anonymous or pseudonymous. Anonymity of participants is usually achieved by special routing overlay networks that hide the physical location of each node from other participants. Interest in anonymous P2P systems has increased in recent years for many reasons, ranging from the desire to share files without revealing one's network identity and risking litigationElectronic Frontier Foundation (2005)RIAA v. The People: Five Years Later. Retrieved March 5, 2008. to distrust in governments, concerns over mass surveillance and data retention, and lawsuits against bloggers. Motivation for anonymity There are many reasons to use anonymous P2P technology; most of them are generic to all forms of online anonymity. P2P users who desire anonymity usually do so as they do not wish to be identified as a publisher (sender), or reader (r ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Anonymity
Anonymity describes situations where the acting person's identity is unknown. Some writers have argued that namelessness, though technically correct, does not capture what is more centrally at stake in contexts of anonymity. The important idea here is that a person be non-identifiable, unreachable, or untrackable. Anonymity is seen as a technique, or a way of realizing, a certain other values, such as privacy, or liberty. Over the past few years, anonymity tools used on the dark web by criminals and malicious users have drastically altered the ability of law enforcement to use conventional surveillance techniques. An important example for anonymity being not only protected, but enforced by law is the vote in free elections. In many other situations (like conversation between strangers, buying some product or service in a shop), anonymity is traditionally accepted as natural. There are also various situations in which a person might choose to withhold their identity. Acts of cha ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
OpenVPN
OpenVPN is a virtual private network (VPN) system that implements techniques to create secure point-to-point or site-to-site connections in routed or bridged configurations and remote access facilities. It implements both client and server applications. OpenVPN allows peers to authenticate each other using pre-shared secret keys, certificates or username/password. When used in a multiclient-server configuration, it allows the server to release an authentication certificate for every client, using signatures and certificate authority. It uses the OpenSSL encryption library extensively, as well as the TLS protocol, and contains many security and control features. It uses a custom security protocol that utilizes SSL/TLS for key exchange. It is capable of traversing network address translators (NATs) and firewalls. OpenVPN has been ported and embedded to several systems. For example, DD-WRT has the OpenVPN server function. SoftEther VPN, a multi-protocol VPN server, also has ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
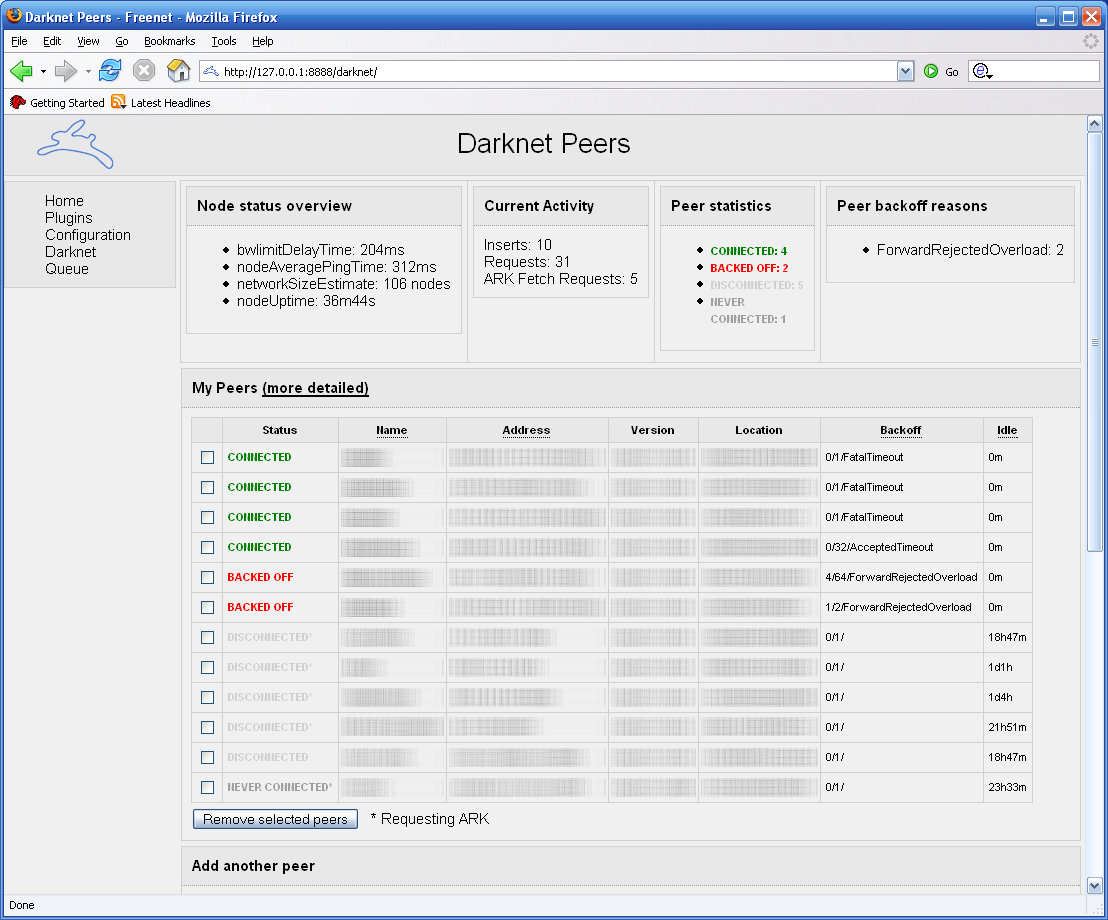
Freenet
Freenet is a peer-to-peer platform for censorship-resistant, anonymous communication. It uses a decentralized distributed data store to keep and deliver information, and has a suite of free software for publishing and communicating on the Web without fear of censorship.What is Freenet? , ''Freenet: The Free network official website''.Taylor, Ian J. ''From P2P to Web Services and Grids: Peers in a Client/Server World''. London: Springer, 2005. Both Freenet and some of its associated tools were originally designed by Ian Clarke, who defined Freenet's goal as providing |
Crypto-anarchism
Crypto-anarchism or cyberanarchism is a political ideology focusing on protection of privacy, political freedom, and economic freedom, the adherents of which use cryptographic software for confidentiality and security while sending and receiving information over computer networks. In his 1988 "Crypto Anarchist Manifesto", Timothy C. May introduced the basic principles of crypto-anarchism, encrypted exchanges ensuring total anonymity, total freedom of speech, and total freedom to trade. In 1992, he read the text at the founding meeting of the cypherpunk movement. Terminology "Crypto-" comes from the Ancient Greek ''κρυπτός'' kruptós, meaning "hidden" or "secret". This is a different use of the prefix than that employed in words like 'crypto-fascist' or 'crypto-Jew' where it indicates that the identity itself is concealed from the world; rather, many crypto-anarchists are open about their anarchism and promotion of tools based in cryptology. Motives One motive of cr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
OSPF
Open Shortest Path First (OSPF) is a routing protocol for Internet Protocol (IP) networks. It uses a link state routing (LSR) algorithm and falls into the group of interior gateway protocols (IGPs), operating within a single autonomous system (AS). OSPF gathers link state information from available routers and constructs a topology map of the network. The topology is presented as a routing table to the Internet Layer for routing packets by their destination IP address. OSPF supports Internet Protocol Version 4 (IPv4) and Internet Protocol Version 6 (IPv6) networks and supports the Classless Inter-Domain Routing (CIDR) addressing model. OSPF is widely used in large enterprise networks. IS-IS, another LSR-based protocol, is more common in large service provider networks. Originally designed in the 1980s, OSPF is defined for IPv4 in protocol version 2 by RFC 2328 (1998)., Updated by RFC 5709, RFC 6549, RFC 6845, RFC 6860, RFC 7474, RFC 8042. The updates for IPv6 are specifi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Anonymity
Anonymity describes situations where the acting person's identity is unknown. Some writers have argued that namelessness, though technically correct, does not capture what is more centrally at stake in contexts of anonymity. The important idea here is that a person be non-identifiable, unreachable, or untrackable. Anonymity is seen as a technique, or a way of realizing, a certain other values, such as privacy, or liberty. Over the past few years, anonymity tools used on the dark web by criminals and malicious users have drastically altered the ability of law enforcement to use conventional surveillance techniques. An important example for anonymity being not only protected, but enforced by law is the vote in free elections. In many other situations (like conversation between strangers, buying some product or service in a shop), anonymity is traditionally accepted as natural. There are also various situations in which a person might choose to withhold their identity. Acts of cha ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Song Of The South
''Song of the South'' is a 1946 American Live-action animated film, live-action/animated musical film, musical drama film directed by Harve Foster and Wilfred Jackson; produced by Walt Disney and released by RKO Pictures, RKO Radio Pictures. It is based on the Uncle Remus stories as adapted by Joel Chandler Harris, and stars James Baskett as Uncle Remus in his final film role. The film takes place in Georgia (U.S. state), Georgia during the Reconstruction era, a period of American history after the end of the American Civil War and the abolition of Slavery in the United States, slavery. The story follows seven-year-old Johnny (Bobby Driscoll) who is visiting his grandmother's Plantations in the American South, plantation for an extended stay. Johnny befriends Uncle Remus, an elderly worker on the plantation, and takes joy in hearing his tales about the adventures of Br'er Rabbit, Br'er Fox and Br'er Bear, Br'er Fox, and Br'er Bear. Johnny learns from the stories how to cope wit ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Bnetd
bnetd is a communication app that enables users of the online game StarCraft (and StarCraft: Brood War) released on March 31, 1998 to connect and chat together. Bnetd was released on April 28, 1998 under the name ''StarHack'' and provided near-complete emulation of the original online multiplayer gaming service network. This was accomplished through reverse engineering of the corporate Blizzard Entertainment's Battle.net. Due to a lawsuit in 2002, United States that Blizzard won against bnetd's original developers, they no longer maintain or host bnetd. Background The online game StarCraft was released on March 31, 1998, and required the online multiplayer gaming service network Battle.net. The near-complete emulation of this network was released with the first version of bnetd on April 28, 1998 by Mark Baysinger, who at the time was a student at UC San Diego, under the name ''StarHack'' because it was originally meant for StarCraft to connect and chat together. On April 2 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Premier Election Solutions
Premier Election Solutions, formerly Diebold Election Systems, Inc. (DESI), was a subsidiary of Diebold that made and sold voting machines. In 2009, it was sold to competitor ES&S. In 2010, Dominion Voting Systems purchased the primary assets of Premier, including all intellectual property, software, firmware and hardware for Premier's current and legacy optical scan, central scan, and touch screen voting systems, and all versions of the GEMS election management system from ES&S. At the time ES&S spun off the company due to monopoly charges its systems were in use in 1,400 jurisdictions in 33 states and serving nearly 28 million people. History DESI was run by Bob Urosevich, starting in 1976. In 1979, Bob Urosevich founded, and served as the President (through 1992) of, ''American Information Systems'', now known as Election Systems & Software, Inc. (ES&S), becoming a chief competitor to DESI. Todd Urosevich, Bob's brother, was Vice President, Aftermarket Sales, of Election ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |

.jpg)



