|
DarkNET Conglomeration
A dark net or darknet is an overlay network within the Internet that can only be accessed with specific software, configurations, or authorization, and often uses a unique customized communication protocol. Two typical darknet types are social networks (usually used for file hosting with a peer-to-peer connection), and anonymity proxy networks such as Tor via an anonymized series of connections. The term "darknet" was popularized by major news outlets to associate with Tor Onion services, when the infamous drug bazaar Silk Road used it, despite the terminology being unofficial. Technology such as Tor, I2P, and Freenet was intended to defend digital rights by providing security, anonymity, or censorship resistance and is used for both illegal and legitimate reasons. Anonymous communication between whistle-blowers, activists, journalists and news organisations is also facilitated by darknets through use of applications such as SecureDrop. Terminology The term originally describe ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Overlay Network
An overlay network is a computer network that is layered on top of another network. Structure Nodes in the overlay network can be thought of as being connected by virtual or logical links, each of which corresponds to a path, perhaps through many physical links, in the underlying network. For example, distributed systems such as peer-to-peer networks and client–server applications are overlay networks because their nodes run on top of the Internet. The Internet was originally built as an overlay upon the telephone network, while today (through the advent of VoIP), the telephone network is increasingly turning into an overlay network built on top of the Internet. Uses Enterprise networks Enterprise private networks were first overlaid on telecommunication networks such as Frame Relay and Asynchronous Transfer Mode packet switching infrastructures but migration from these (now legacy) infrastructures to IP based MPLS networks and virtual private networks started (2001~ ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Surface Web
The Surface Web (also called the Visible Web, Indexed Web, Indexable Web or Lightnet) is the portion of the World Wide Web that is readily available to the general public and searchable with standard web search engines. It is the opposite of the deep web, the part of the web not indexed by a web search engine. The Surface Web only consists of 10 percent of the information that is on the internet. The Surface Web is made with a collection of public Web pages on a server accessible by any search engine. According to one source, , Google's Index of the Surface Web Contains about 14.8 billion pages. See also * Clearnet (networking) Clearnet is a term that typically refers to the publicly accessible Internet. Sometimes "clearnet" is used as a synonym for " surface web"—excluding both the darknet and the deep web. The World Wide Web is one of the most popular distributed se ... References {{Reflist Internet search engines Internet terminology Dark web ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Crypto-anarchism
Crypto-anarchism or cyberanarchism is a political ideology focusing on protection of privacy, political freedom, and economic freedom, the adherents of which use cryptographic software for confidentiality and security while sending and receiving information over computer networks. In his 1988 "Crypto Anarchist Manifesto", Timothy C. May introduced the basic principles of crypto-anarchism, encrypted exchanges ensuring total anonymity, total freedom of speech, and total freedom to trade. In 1992, he read the text at the founding meeting of the cypherpunk movement. Terminology "Crypto-" comes from the Ancient Greek ''κρυπτός'' kruptós, meaning "hidden" or "secret". This is a different use of the prefix than that employed in words like 'crypto-fascist' or 'crypto-Jew' where it indicates that the identity itself is concealed from the world; rather, many crypto-anarchists are open about their anarchism and promotion of tools based in cryptology. Motives One motive of cr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Camgirl
A webcam model (colloquially, camgirl, camboy, or cammodel) is a video performer who streams on the Internet with a live webcam broadcast. A webcam model often performs erotic acts online, such as stripping, masturbation, or sex acts in exchange for money, goods, or attention. They may also sell videos of their performances. Unlike other sex work, webcam models operate solely online. Once viewed as a small niche in the world of adult entertainment, camming became "the engine of the porn industry," according to Alec Helmy, the publisher of ''XBIZ'', a sex-trade industry journal. As many webcam models operate from their homes, they are free to choose the amount of sexual content for their broadcasts. While most display nudity and sexually provocative behavior, some choose to remain mostly clothed and merely talk about various topics, while still soliciting payment as tips from their fans. Webcam models are predominantly women, and also include noted performers of all genders and s ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Subculture
A subculture is a group of people within a culture that differentiates itself from the parent culture to which it belongs, often maintaining some of its founding principles. Subcultures develop their own norms and values regarding cultural, political, and sexual matters. Subcultures are part of society while keeping their specific characteristics intact. Examples of subcultures include BDSM, hippies, goths, bikers, punks, skinheads, hip-hoppers, metalheads, and cosplayers. The concept of subcultures was developed in sociology and cultural studies. Subcultures differ from countercultures. Definitions The ''Oxford English Dictionary'' defines subculture, in regards to sociological and cultural anthropology, as "an identifiable subgroup within a society or group of people, esp. one characterized by beliefs or interests at variance with those of the larger group; the distinctive ideas, practices, or way of life of such a subgroup." As early as 1950, David Riesman distinguished b ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Jamie Bartlett (journalist)
Jamie Bartlett is a British author and journalist, primarily for ''The Spectator'' and ''The Daily Telegraph''. He was a senior fellow at Demos and served as director of the Centre for the Analysis of Social Media at Demos until 2017. Education Bartlett was educated at a state comprehensive school in Chatham, Kent He won a scholarship to study at the University of Oxford and went on do a master's degree at the London School of Economics. Career In 2013, he covered the rise of Beppe Grillo's Five Star Movement in Italy for Demos, chronicling the new political force's emergence and use of social media. In 2014, Bartlett released his first full-length book, ''The Dark Net.'' The book discusses the darknet and dark web in broad terms, describing a range of underground and emergent subcultures, including social media racists, camgirls, self-harm communities, darknet drug markets, crypto-anarchists and transhumanists. Bartlett has frequently written about online extremism and free ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Copyright Infringement
Copyright infringement (at times referred to as piracy) is the use of works protected by copyright without permission for a usage where such permission is required, thereby infringing certain exclusive rights granted to the copyright holder, such as the right to reproduce, distribute, display or perform the protected work, or to make derivative works. The copyright holder is typically the work's creator, or a publisher or other business to whom copyright has been assigned. Copyright holders routinely invoke legal and technological measures to prevent and penalize copyright infringement. Copyright infringement disputes are usually resolved through direct negotiation, a notice and take down process, or litigation in civil court. Egregious or large-scale commercial infringement, especially when it involves counterfeiting, is sometimes prosecuted via the criminal justice system. Shifting public expectations, advances in digital technology and the increasing reach of the Internet ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Digital Rights Management
Digital rights management (DRM) is the management of legal access to digital content. Various tools or technological protection measures (TPM) such as access control technologies can restrict the use of proprietary hardware and copyrighted works. DRM technologies govern the use, modification, and distribution of copyrighted works (such as software and multimedia content), as well as systems that enforce these policies within devices. Laws in many countries criminalize the circumvention of DRM, communication about such circumvention, and the creation and distribution of tools used for such circumvention. Such laws are part of the United States' Digital Millennium Copyright Act (DMCA), and the European Union's Information Society Directive (the French DADVSI is an example of a member state of the European Union implementing the directive). DRM techniques include licensing agreements and encryption. The industry has expanded the usage of DRM to various hardware products, such as K ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Microsoft
Microsoft Corporation is an American multinational technology corporation producing computer software, consumer electronics, personal computers, and related services headquartered at the Microsoft Redmond campus located in Redmond, Washington, United States. Its best-known software products are the Windows line of operating systems, the Microsoft Office suite, and the Internet Explorer and Edge web browsers. Its flagship hardware products are the Xbox video game consoles and the Microsoft Surface lineup of touchscreen personal computers. Microsoft ranked No. 21 in the 2020 Fortune 500 rankings of the largest United States corporations by total revenue; it was the world's largest software maker by revenue as of 2019. It is one of the Big Five American information technology companies, alongside Alphabet, Amazon, Apple, and Meta. Microsoft was founded by Bill Gates and Paul Allen on April 4, 1975, to develop and sell BASIC interpreters for the Altair 8800. It rose to do ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Peter Biddle
Peter Nicholas Biddle (born December 22, 1966) is a software evangelist from the United States. His primary fields of interest include content distribution, secure computing, and encryption. Career Biddle joined Microsoft in 1990 as a Support Engineer. He was one of the first authors to describe the concept of darknet (networking), darknet,. an early participant in the Secure Digital Music Initiative (SDMI), Copy Protection Technical Working Group, and Trusted Computing Platform Alliance, an early technical evangelist for DVD and digital video recorder technology, the founding leader of Microsoft's Next-Generation Secure Computing Base (code named Palladium) initiative, and was responsible for starting Microsoft's Hypervisor development efforts. Biddle built and led the engineering team that shipped BitLocker Drive Encryption, a Trusted Platform Module-rooted disk encryption for Windows Vista. Bitlocker continues to be used by Microsoft today, having been shipped with certain ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Digital Distribution
Digital distribution, also referred to as content delivery, online distribution, or electronic software distribution, among others, is the delivery or distribution of digital media content (media), content such as Sound recording and reproduction, audio, motion graphics, video, e-books, video games, and other software. The term is generally used to describe distribution over an online delivery medium, such as the Internet, thus bypassing physical distribution methods, such as paper, optical discs, and VHS videocassettes. The term online distribution is typically applied to freestanding products; downloadable add-ons for other products are more commonly known as downloadable content. With the advancement of network bandwidth capabilities, online distribution became prominent in the 21st century, with prominent platforms such as Amazon (company), Amazon Video, and Netflix's Streaming media, streaming service starting in 2007. Content distributed online may be streamed or downloade ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
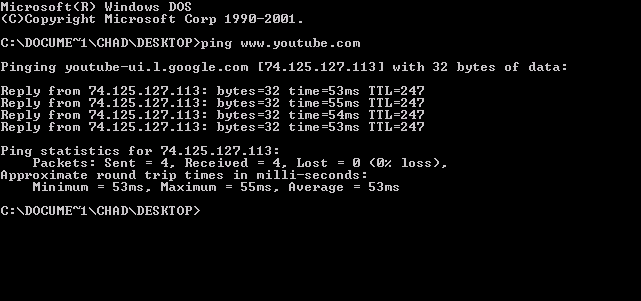
Ping (networking Utility)
ping is a computer network administration software utility used to test the reachability of a host on an Internet Protocol (IP) network. It is available for virtually all operating systems that have networking capability, including most embedded network administration software. Ping measures the round-trip time for messages sent from the originating host to a destination computer that are echoed back to the source. The name comes from active sonar terminology that sends a pulse of sound and listens for the echo to detect objects under water. Ping operates by means of Internet Control Message Protocol (ICMP) packets. ''Pinging'' involves sending an ICMP echo request to the target host and waiting for an ICMP echo reply. The program reports errors, packet loss, and a statistical summary of the results, typically including the minimum, maximum, the mean round-trip times, and standard deviation of the mean. The command-line options of the ping utility and its output vary between t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |

.jpg)

.jpg)