|
.i2p
The Invisible Internet Project (I2P) is an anonymous network layer (implemented as a mix network) that allows for censorship-resistant, peer-to-peer communication. Anonymous connections are achieved by encrypting the user's traffic (by using end-to-end encryption), and sending it through a volunteer-run network of roughly 55,000 computers distributed around the world. Given the high number of possible paths the traffic can transit, a third party watching a full connection is unlikely. The software that implements this layer is called an "I2P router", and a computer running I2P is called an "I2P node". I2P is free and open source, and is published under multiple licenses. Technical design I2P started in 2003 as a fork of Freenet. The network is strictly message-based, like IP, but a library is available to allow reliable streaming communication on top of it (similar to Non-blocking IO-based TCP, although from version 0.6, a new ''Secure Semi-reliable'' UDP transport is us ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
I2P Logo
I, or i, is the ninth letter and the third vowel letter of the Latin alphabet, used in the modern English alphabet, the alphabets of other western European languages and others worldwide. Its name in English is ''i'' (pronounced ), plural ''ies''. Name In English, the name of the letter is the "long I" sound, pronounced . In most other languages, its name matches the letter's pronunciation in open syllables. History In the Phoenician alphabet, the letter may have originated in a hieroglyph for an arm that represented a voiced pharyngeal fricative () in Egyptian, but was reassigned to (as in English "yes") by Semites because their word for "arm" began with that sound. This letter could also be used to represent , the close front unrounded vowel, mainly in foreign words. The Greeks adopted a form of this Phoenician ''yodh'' as their letter ''iota'' () to represent , the same as in the Old Italic alphabet. In Latin (as in Modern Greek), it was also used to represent ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
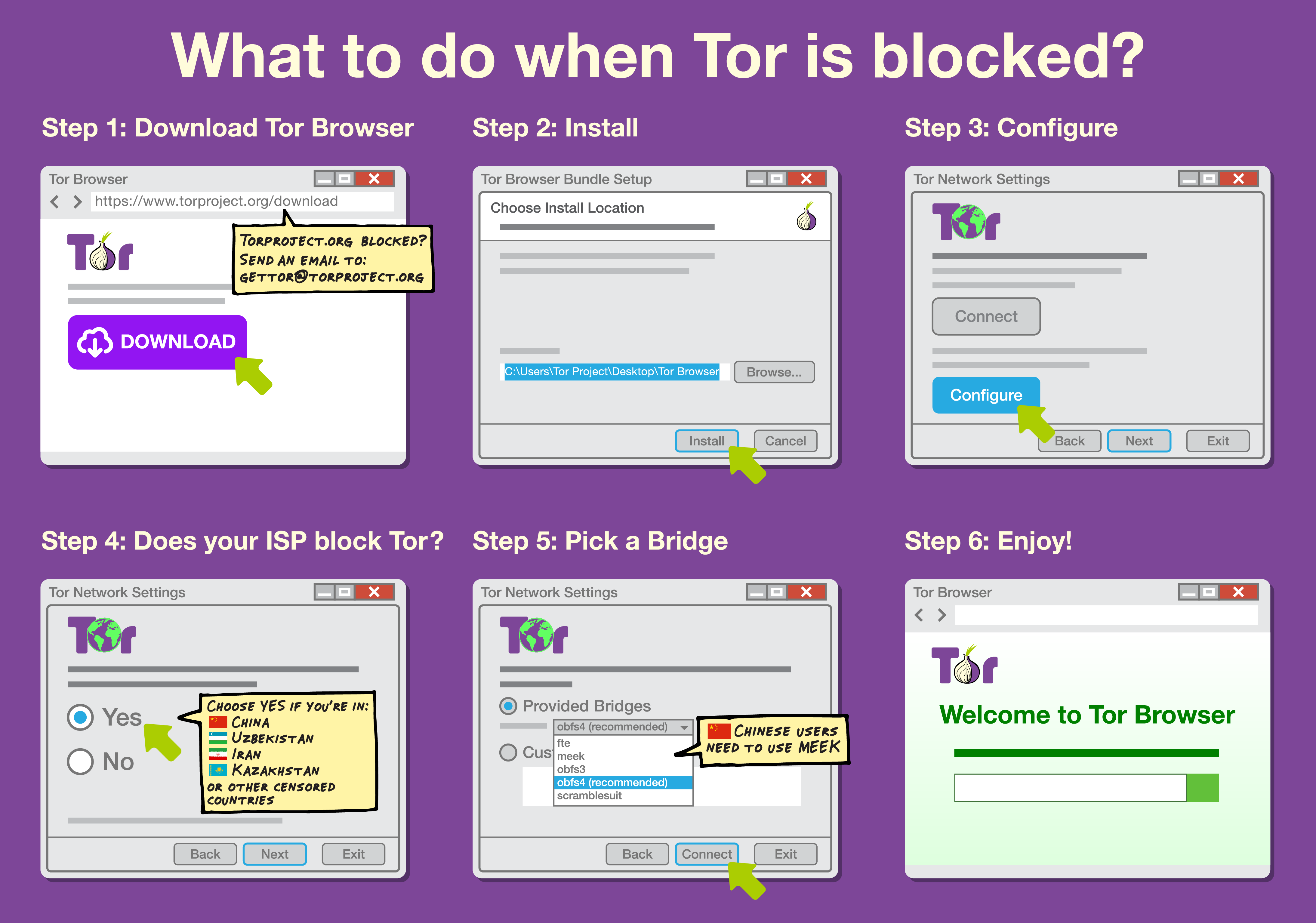
Internet Censorship Circumvention
Internet censorship circumvention is the use of various methods and tools to bypass internet censorship. Commonly used tools include Lantern and Psiphon, which bypass multiple safeguard types. Some methods use alternate DNS servers, false addresses or address lookup systems to evade less sophisticated blocking tools. However, such methods do not work if censors block the IP address of restricted domains in addition to DNS, rendering the bypass ineffective. Other tools tunnel network traffic to proxies in jurisdictions without censorship. Through pluggable transports, traffic obscuration, website mirrors, or archive sites, copies of sites can be accessed in areas under internet censorship. An arms race has developed between censors and developers of circumvention software, resulting in more sophisticated blocking techniques by censors and the development of harder-to-detect tools by tool developers. Estimates of adoption of circumvention tools are disputed, but are widely un ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
User Datagram Protocol
In computer networking, the User Datagram Protocol (UDP) is one of the core communication protocols of the Internet protocol suite used to send messages (transported as datagrams in Network packet, packets) to other hosts on an Internet Protocol (IP) network. Within an IP network, UDP does not require prior communication to set up communication channels or data paths. UDP is a connectionless protocol, meaning that messages are sent without negotiating a connection and that UDP does not keep track of what it has sent. UDP provides checksums for data integrity, and port numbers for addressing different functions at the source and destination of the datagram. It has no Handshake (computing), handshaking dialogues and thus exposes the user's program to any Reliability (computer networking), unreliability of the underlying network; there is no guarantee of delivery, ordering, or duplicate protection. If error-correction facilities are needed at the network interface level, an applica ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Transmission Control Protocol
The Transmission Control Protocol (TCP) is one of the main communications protocol, protocols of the Internet protocol suite. It originated in the initial network implementation in which it complemented the Internet Protocol (IP). Therefore, the entire suite is commonly referred to as TCP/IP. TCP provides reliability (computer networking), reliable, ordered, and error detection and correction, error-checked delivery of a reliable byte stream, stream of octet (computing), octets (bytes) between applications running on hosts communicating via an IP network. Major internet applications such as the World Wide Web, email, remote administration, and file transfer rely on TCP, which is part of the transport layer of the TCP/IP suite. Transport Layer Security, SSL/TLS often runs on top of TCP. TCP is Connection-oriented communication, connection-oriented, meaning that sender and receiver firstly need to establish a connection based on agreed parameters; they do this through three-way Ha ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Non-blocking IO
In computer science, asynchronous I/O (also non-sequential I/O) is a form of input/output processing that permits other processing to continue before the I/O operation has finished. A name used for asynchronous I/O in the Windows API is '' overlapped I/O''. Input and output (I/O) operations on a computer can be extremely slow compared to the processing of data. An I/O device can incorporate mechanical devices that must physically move, such as a hard drive seeking a track to read or write; this is often orders of magnitude slower than the switching of electric current. For example, during a disk operation that takes ten milliseconds to perform, a processor that is clocked at one gigahertz could have performed ten million instruction-processing cycles. A simple approach to I/O would be to start the access and then wait for it to complete. But such an approach, called synchronous I/O or blocking I/O, would block the progress of a program while the communication is in progress, le ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Streaming Algorithm
In computer science, streaming algorithms are algorithms for processing data streams in which the input is presented as a sequence of items and can be examined in only a few passes, typically one-pass algorithm, just one. These algorithms are designed to operate with limited memory, generally L (complexity), logarithmic in the size of the stream and/or in the maximum value in the stream, and may also have limited processing time per item. As a result of these constraints, streaming algorithms often produce approximate answers based on a summary or "sketch" of the data stream. History Though streaming algorithms had already been studied by Munro and Paterson as early as 1978, as well as Philippe Flajolet and G. Nigel Martin in 1982/83, the field of streaming algorithms was first formalized and popularized in a 1996 paper by Noga Alon, Yossi Matias, and Mario Szegedy. For this paper, the authors later won the Gödel Prize in 2005 "for their foundational contribution to streaming ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Library (computing)
In computing, a library is a collection of System resource, resources that can be leveraged during software development to implement a computer program. Commonly, a library consists of executable code such as compiled function (computer science), functions and Class (computer programming), classes, or a library can be a collection of source code. A resource library may contain data such as images and Text string, text. A library can be used by multiple, independent consumers (programs and other libraries). This differs from resources defined in a program which can usually only be used by that program. When a consumer uses a library resource, it gains the value of the library without having to implement it itself. Libraries encourage software reuse in a Modular programming, modular fashion. Libraries can use other libraries resulting in a hierarchy of libraries in a program. When writing code that uses a library, a programmer only needs to know how to use it not its internal d ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Internet Protocol
The Internet Protocol (IP) is the network layer communications protocol in the Internet protocol suite for relaying datagrams across network boundaries. Its routing function enables internetworking, and essentially establishes the Internet. IP has the task of delivering Packet (information technology), packets from the source Host (network), host to the destination host solely based on the IP addresses in the packet Header (computing), headers. For this purpose, IP defines packet structures that encapsulation (networking), encapsulate the data to be delivered. It also defines addressing methods that are used to label the datagram with source and destination information. IP was the connectionless datagram service in the original ''Transmission Control Program'' introduced by Vint Cerf and Bob Kahn in 1974, which was complemented by a connection-oriented service that became the basis for the Transmission Control Protocol (TCP). The Internet protocol suite is therefore often referre ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Freenet
Hyphanet (until mid-2023: Freenet) is a peer-to-peer platform for censorship-resistant, Anonymity application, anonymous communication. It uses a decentralized distributed data store to keep and deliver information, and has a suite of free software for publishing and communicating on the Web without fear of censorship.What is Freenet? , ''Freenet: The Free network official website''.Taylor, Ian J. ''From P2P to Web Services and Grids: Peers in a Client/Server World''. London: Springer, 2005. Both Freenet and some of its associated tools were originally designed by Ian Clarke (computer scientist), Ian Clarke, who defined Freenet's goal as providing freedom of speech on the Internet with strong anonymity protection. [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Ars Technica
''Ars Technica'' is a website covering news and opinions in technology, science, politics, and society, created by Ken Fisher and Jon Stokes in 1998. It publishes news, reviews, and guides on issues such as computer hardware and software, science, technology policy, and video games. ''Ars Technica'' was privately owned until May 2008, when it was sold to Condé Nast Digital, the online division of Condé Nast Publications. Condé Nast purchased the site, along with two others, for $25 million and added it to the company's ''Wired'' Digital group, which also includes '' Wired'' and, formerly, Reddit. The staff mostly works from home and has offices in Boston, Chicago, London, New York City, and San Francisco. The operations of ''Ars Technica'' are funded primarily by advertising, and it has offered a paid subscription service since 2001. History Ken Fisher, who serves as the website's current editor-in-chief, and Jon Stokes created ''Ars Technica'' in 1998. Its purpose was t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Software License
A software license is a legal instrument governing the use or redistribution of software. Since the 1970s, software copyright has been recognized in the United States. Despite the copyright being recognized, most companies prefer to sell licenses rather than copies of the software because it enables them to enforce stricter terms on redistribution. Very few purchasers read any part of the license, initially shrink-wrap contracts and now most commonly encountered as clickwrap or browsewrap. The enforceability of this kind of license is a matter of controversy and is limited in some jurisdictions. Service-level agreements are another type of software license where the vendor agrees to provide a level of service to the purchaser, often backed by financial penalties. Copyleft is a type of license that mandates derivative works to be licensed under the license's terms. Copyleft licenses exist for free and open-source software, but also for commercial applications like the Ser ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Open-source Software
Open-source software (OSS) is Software, computer software that is released under a Open-source license, license in which the copyright holder grants users the rights to use, study, change, and Software distribution, distribute the software and its source code to anyone and for any purpose. Open-source software may be developed in a collaborative, public manner. Open-source software is a prominent example of open collaboration, meaning any capable user is able to online collaboration, participate online in development, making the number of possible contributors indefinite. The ability to examine the code facilitates public trust in the software. Open-source software development can bring in diverse perspectives beyond those of a single company. A 2024 estimate of the value of open-source software to firms is $8.8 trillion, as firms would need to spend 3.5 times the amount they currently do without the use of open source software. Open-source code can be used for studying and a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |